We’re excited to share ANY.RUN‘s latest malware trends analysis for Q1 2024! Our quarterly update provides insights into the most widely deployed malware families, types, and TTPs we saw during the last 3 months of the year.
Summary
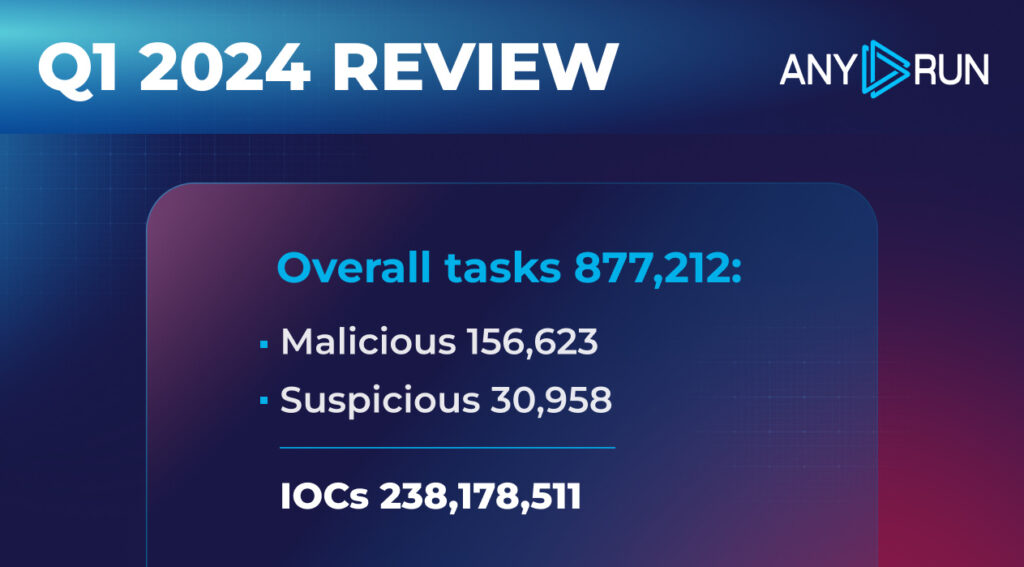
In Q1 2024, ANY.RUN users ran 877,212 public interactive analysis sessions, which is a 17.2% increase from Q4 2023. Out of these, our data marks 156,623 (17.8%) as malicious, and 30,958 (3.5%) — suspicious.
Compared to last quarter, the percentage of malicious tasks dropped slightly from 22.7% in Q4 2023 to 17.2% in Q1 2024. The share of suspicious tasks stayed about the same (4.5% to 3.5%).
As for Indicators of Compromise (IOCs), users collected a total of 238,178,511 IOCs this quarter, and 63,681,137 (26.7%) of them were unique.
In today’s report, we’ll:
- Explore the most common malware types and families in Q1 2024, using data from ANY.RUN
- Investigate the top MITRE ATT&CK TTPs employed during this quarter
Let’s dive in and see what we uncover!
Top Malware Types in Q4 2023
Let’s take a closer look at the most common malware types identified by ANY.RUN’s sandbox.
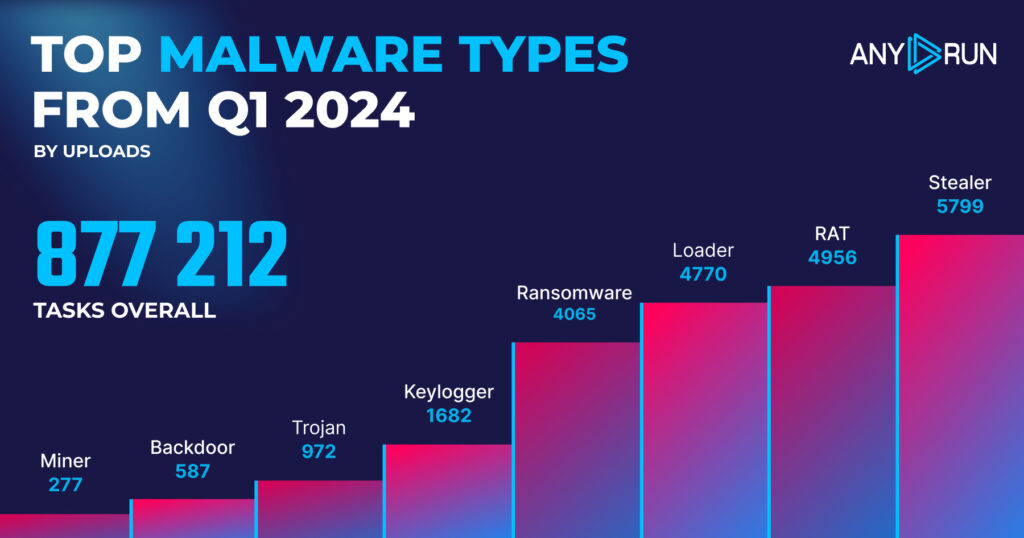
- Stealer: 5799
- RAT: 4956
- Loader: 4770
- Ransomware: 4065
- Keylogger: 1682
- Trojan: 972
- Backdoor: 587
- Miner: 277
Top malware types: highlights
In Q1 2024, Stealers remained the most widely detected category, with 5,799 detections. This is a slight decrease from the previous quarter’s 6,662 detections.
Loader detections remained stable, with 4,770 detections in Q1 2024 compared to 4,752 in Q3 2023. However, there appears to have been a vermin infestation in Q1 2024 cyberspace, as RAT detections doubled from 2,444 in Q3 2023 to 4,956 in Q1 2024, making it the second most prevalent threat type.
Ransomware moved into fourth place with 4,065 detections, up from 3,333 in the previous quarter, representing a 21.9% increase in detections. This indicates that ransomware is gaining popularity as a threat type. Keylogger detections also doubled, with 1,682 instances in Q1 2024 compared to 837 in Q3 2023.
The differences in miner and backdoor detections are negligible and can be attributed to statistical noise, indicating that the popularity of these threats has remained relatively unchanged.
Analyze malware and collect IOCs in ANY.RUN
Register for freeTop Malware Families in Q1 2024
Let’s now take a look at which malware families have been used the most in the first quarter of 2024.
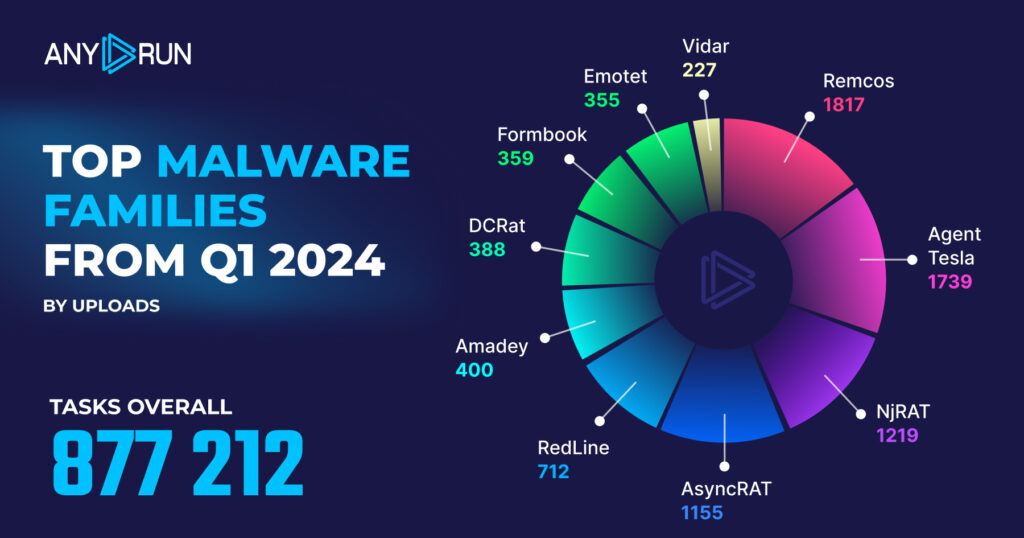
- Remcos: 1817
- Agent Tesla: 1739
- NjRAT: 1219
- AsyncRAT: 1155
- RedLine: 712
- Amadey: 400
- DCRat: 388
- Formbook: 359
- Emotet: 355
- Vidar: 227
Top malware families: highlights
In Q1 2024, Remcos took the lead, replacing Agent Tesla as the most prevalent malware, while NjRAT and AsyncRAT made significant jumps in the rankings.
- Remcos climbed to the top spot with 1817 instances, which is a 68.1% increase from 1081 in Q4 2023.
- RedLine dropped from second to fifth place with 712 instances, a decrease of 55.1% from 1586 in Q4 2023.
- Agent Tesla slipped to second place with 1739 instances, a slight decrease of 1.7% from 1769 in Q4 2023.
- NjRAT jumped to the third position with 1219 instances, an increase of 96.6% from 620 in Q4 2023.
- DCRat is a new addition to the top 10 list, claiming the seventh spot with 388 instances.
- AsyncRAT moved up to fourth place with 1155 instances, a significant increase of 116.7% from 533 in Q4 2023.
Top MITRE ATT&CK techniques in Q1 2024
The MITRE ATT&CK framework categorizes adversary behavior into tactics and techniques, helping malware analysts more efficiently identify, assess, and respond to threats.
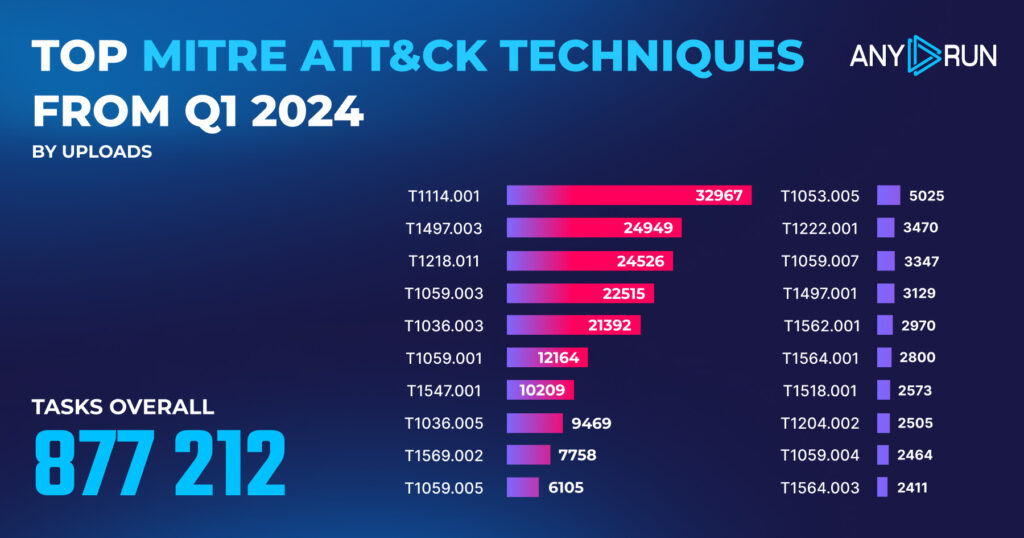
<thead> <tr>
<th>
# </th>
<th>
MITRE ATT&CK Technique </th>
<th>
№ of detections </th>
</tr>
</thead><tbody> <tr>
<td>
1 </td>
<td>
Email Collection: Local Email Collection, T1114.001 </td>
<td>
32,967 </td>
</tr>
<tr>
<td>
2 </td>
<td>
Virtualization/Sandbox Evasion: Time Based Evasion, T1497.003 </td>
<td>
24,949 </td>
</tr>
<tr>
<td>
3 </td>
<td>
System Binary Proxy Execution: Rundll32, Sub-technique, T1218.011 </td>
<td>
24,526 </td>
</tr>
<tr>
<td>
4 </td>
<td>
Command and Scripting Interpreter: Windows Command Shell, T1059.003 </td>
<td>
22,515 </td>
</tr>
<tr>
<td>
5 </td>
<td>
Masquerading: Rename System Utilities, T1036.003 </td>
<td>
21,392 </td>
</tr>
<tr>
<td>
6 </td>
<td>
Command and Scripting Interpreter: PowerShell, T1059.001 </td>
<td>
12,164 </td>
</tr>
<tr>
<td>
7 </td>
<td>
Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder, T1547.001 </td>
<td>
10,209 </td>
</tr>
<tr>
<td>
8 </td>
<td>
Masquerading: Match Legitimate Name or Location, T1036.005 </td>
<td>
9469 </td>
</tr>
<tr>
<td>
9 </td>
<td>
System Services: Service Execution, T1569.002 </td>
<td>
7758 </td>
</tr>
<tr>
<td>
10 </td>
<td>
Command and Scripting Interpreter: Visual Basic, T1059.005 </td>
<td>
6105 </td>
</tr>
<tr>
<td>
11 </td>
<td>
Scheduled Task/Job: Scheduled Task, T1053.005 </td>
<td>
5025 </td>
</tr>
<tr>
<td>
12 </td>
<td>
File and Directory Permissions Modification: Windows File and Directory Permissions Modification, T1222.001 </td>
<td>
3470 </td>
</tr>
<tr>
<td>
13 </td>
<td>
Command and Scripting Interpreter: JavaScript, T1059.007 </td>
<td>
3347 </td>
</tr>
<tr>
<td>
14 </td>
<td>
Virtualization/Sandbox Evasion: System Checks, T1497.001 </td>
<td>
3129 </td>
</tr>
<tr>
<td>
15 </td>
<td>
Impair Defenses: Disable or Modify Tools, T1562.001 </td>
<td>
2970 </td>
</tr>
<tr>
<td>
16 </td>
<td>
Hide Artifacts: Hidden Files and Directories, T1564.001 </td>
<td>
2800 </td>
</tr>
<tr>
<td>
17 </td>
<td>
Software Discovery: Security Software Discovery, T1518.001 </td>
<td>
2573 </td>
</tr>
<tr>
<td>
18 </td>
<td>
User Execution: Malicious File, T1204.002 </td>
<td>
2505 </td>
</tr>
<tr>
<td>
19 </td>
<td>
Command and Scripting Interpreter: Unix Shell, T1059.004 </td>
<td>
2464 </td>
</tr>
<tr>
<td>
20 </td>
<td>
Hide Artifacts: Hidden Window, Sub-technique T1564.003 </td>
<td>
2411 </td>
</tr>
</tbody></table>
Top TTPs: Q4 2023 vs Q1 2024 highlights
- T1036.005, Masquerading: Match Legitimate Name or Location, saw a dramatic decrease, dropping from 98,578 detections in Q4 2023 to just 9,469 in Q1 2024 – a whopping 90.4% reduction.
- T1114.001, Email Collection: Local Email Collection, moved up to the top spot in Q1 2024 with 32,967 detections, a 21.0% increase from the previous quarter.
- T1497.003, Virtualization/Sandbox Evasion: Time Based Evasion, jumped from 8th place in Q4 2023 to 2nd place in Q1 2024, with detections nearly tripling from 8,943 to 24,949 (a 179.0% increase).
- T1218.011, System Binary Proxy Execution: Rundll32, moved up one spot to 3rd place, with detections increasing by 14.5% from 21,426 to 24,526.
Report methodology
For our report, we looked at data from 877,212 interactive analysis sessions. This information comes from researchers in our community who contributed by running public tasks in ANY.RUN.
About ANY.RUN
ANY.RUN is a trusted partner for more than 400,000 cybersecurity professionals around the world. Our interactive sandbox simplifies malware analysis of threats targeting both Windows and Linux systems, providing analysts with an advanced tool for investigations. Our threat intelligence products, Lookup and Feeds, offer refined indicators of compromise and context that lets users detect threats and respond to incidents faster.
Advantages of ANY.RUN
ANY.RUN helps you analyze threats faster while improving detection rates. The platform detects common malware families with YARA and Suricata rules and identifies malware behavior with signatures when detection by family is not possible.
With ANY.RUN you can:
- Detect malware in under 40s: ANY.RUN detects malware within about 40 seconds of a file upload. It identifies prevalent malware families using YARA and Suricata rules and uses behavioral signatures to detect malicious actions when you encounter a new threat.
- Interact with samples in real time: ANY.RUN is an interactive cloud sandbox powered by VNC, which means that you can do everything you could on a real system: browse webpages, click through installers, open password-protected archives.
- Save time and money on sandbox setup and maintenance: ANY.RUN’s cloud-based nature eliminates the need for setup or maintenance by your DevOps team, making it a cost-effective solution for businesses.
- Record and study all aspects of malware behavior: ANY.RUN provides a detailed analysis of malware behavior, including network traffic, system calls, and file system changes.
- Collaborate with your team: easily share analysis results, or, as a senior team member, check work of junior analysts by viewing recordings of their analysis sessions.
- Scale as you need: as a cloud service, you can easily scale your team, simply by adding more licenses.
We’ll show you in an interactive presentation how ANY.RUN can help your security team.
The post Malware Trends Report: Q1, 2024 appeared first on ANY.RUN's Cybersecurity Blog.
Article Link: Malware Trends Report: Q1, 2024 - ANY.RUN's Cybersecurity Blog