The Latest 100 Threats Seen in Telecom Services
Lastline® sequences and indexes millions of submissions to our Global Threat Intelligence Network on a weekly basis. This snapshot explores the latest 100 malicious samples analyzed by Lastline that target the Telecom Services sector, additionally the snapshot also compares statistical data for all threats seen over the last 30 days in Telecom Services to the results in the Q4 2017 global Malscape® Monitor Report to highlight differences between threats targeting Telecom Services and the broader threat landscape.
The threat samples reflected in this report were submitted to Lastline for analysis after having been scrutinized and released by the upstream gateway, endpoint, and network security technologies. The findings provide insights into more advanced and sophisticated malware samples and threats that are able to evade conventional detection, and therefore don’t reflect the overall threat landscape. Lastline truly acts as The Last Line of Defense®, providing visibility into the advanced threats to organizations that evade detection by other defenses.
Key Findings In Contrast to Global Findings
Lastline analyzed all threats targeting Telecom Services companies over the past 30 days and compared them to global findings shared in the Malscape Monitor Report.
- Lastline found that the average number of malicious files that other security controls allow to infiltrate network traffic within the Telecom Services sector was one in every 370 submissions (see Figure 1). This is a higher malicious saturation level than the average of 1 in 500 seen across the global malscape. The reason for this could simply be that telco service providers experience a higher malicious encounter rate than other verticals or it could also be that higher levels of security in the Telecom Services sector that more effectively pre-filters files before submitting them to Lastline, and while this may appear in relative terms like a very small deviation, when one considers the total volume of email attachments received and webpages visited in any given day by Telecommunication Services companies, the volume of malicious samples escaping detection can become quite large.
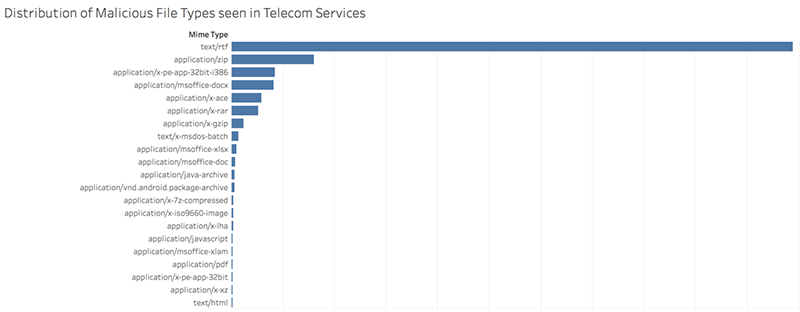
- Within the Telecom Services sector, only 15 file types were used to deliver malware, this is significantly lower than the global average of 40 file types. There is also a significant difference in the volume of various file types seen in Telecom Services as compared to the global landscape. Providing email services is one of the key business functions for this sector and email related file types such rich text format (RTF) documents dominate this sector’s encounter rate (see Figure 2). The threat in the Telecom Services sector is tailored to email as the vector of compromise.
- Around 90 percent of files had not been submitted previously to VirusTotal for analysis, (see Figure 3), which is a significant deviation from the global average of 65% and the polar opposite of the finance sector sitting at around 20%. This delta could be explained by the implementation of state of the art email security controls in Telecom Services companies that have necessitated that the threat actors, in order to penetrate defenses, constantly evolve their attacks creating a perpetual Day0 campaign of rotating file types, exploits, and social engineering schemas. The Telecom services vertical could well be patient zero for email-based attacks. We are using the term Day0 to describe a known threat, that has metamorphed its campaign attributes to include new file hashes, new lure documents, and new delivery and callback infrastructure. Essentially, at Day0 there will be no existing explicit threat intelligence to base detections for this campaign when it is released into the wild.
- Of the remaining payloads that had been submitted to VirusTotal the majority had only generic detections (such as “filerepmalware” and “trojan generic;” see Figure 3), with the occasional PowerShell, ransomware, or cryptominer payload, the generic labeling offers no ability to adapt incident response procedures to correctly remediate the threat. The typical incident response guidance from tools that identify files with these generic descriptions is to restore the device from a known good backup or simply perform a clean re-image. The issue with providing generic guidance is that it does not address the very significant threat posed by malware that is designed to steal credentials, for example. Without knowing what the malware is actually capable of doing, it’s impossible to effectively and completely remediate it and protect against subsequent attack using stolen credentials.
- Not all malware is created equal. The most dangerous of malware, in terms pertaining to the potential for significant loss of confidential or regulated data, has certain advanced characteristics and capabilities. It can:
- Navigate its way around static analysis with the use of “Packer” technology.
- Avoid detection by dynamic analysis systems with evasion behaviors.
- Compromise a host and remain undetected, by exhibiting stealth behaviors on the victim’s system by masquerading as, or injecting trusted system files.
- Stealing data such as credentials and surveilling user activity in order to gain further access to data and systems.
These capabilities put organizations at greater risk of a data breach because of both the poor detection of advanced persistent threats by their current tools, as well as the opportunity for secondary unauthorized access attacks from credential led campaigns.
In the Telecom Sector, one in ten malware threats displayed these advanced behaviors. This is a higher level of advanced threats than the global average, which is one in 12. The explanation could be that the Telecom Services sector’s more effective security requires a more sophisticated threat to successfully breach a company’s defenses. Additionally, stolen Telecom Sector credentials play a pivotal role in many forms of cybercrime activities and so threats with Steal behaviors play an increased role.
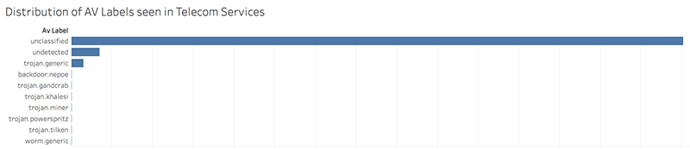
Figure 4 shows the AV labeling for files exhibiting packer, evasion, stealth and steal behaviors. In this timeframe, 100% of this type of threat were either unclassified or undetected on VirusTotal. At Day0 this category of threat has very low levels of detection.
The Latest 100 Threats Seen in Telecom Services: Analyzed
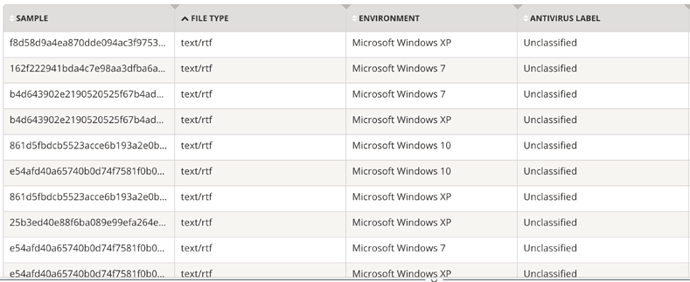
Moving to the latest 100 threat reports captured attacking the Telecom Services industry, we can see that we have captured a Rich Text Format (RTF) document campaign that is using CVE 2107-11882 or CVE 2018-0802 exploits to then download a Loki password stealer payload. At the time of submission, 100% of the RTF exploit docs were Unclassified in VirusTotal, meaning that they had not been submitted to VT for inspection. After re-submitting the 100 samples one month later only 29% had been cataloged by VT, indicating that the samples were either disposable or targeted, and that poor detection rates at time of encounter are the reason that the victims did not instigate a threat intelligence gathering action by having their security mechanisms submit the samples to VirusTotal.
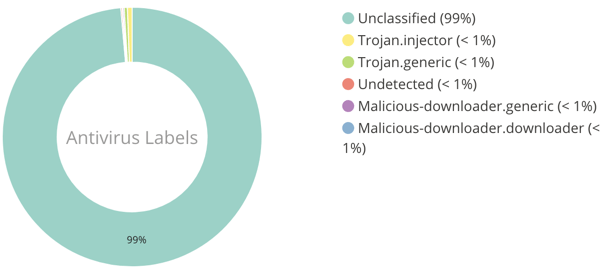
Figure 6: The latest 100 threats by Av Label detected.
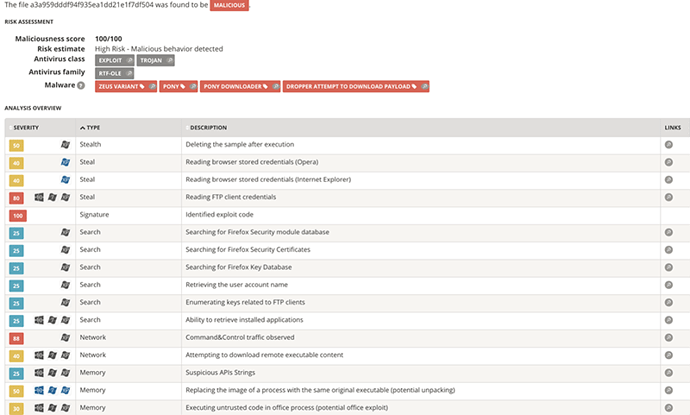
The captured RTF lure documents all look exactly the same, an example of which is shown in Figure 7, and rely on the user interacting with the document to exploit Windows equation editor program which then is used to download the Loki/Pony payload. The telltale behaviors of the RTF lure document and Loki payload are shown in Figure 8.
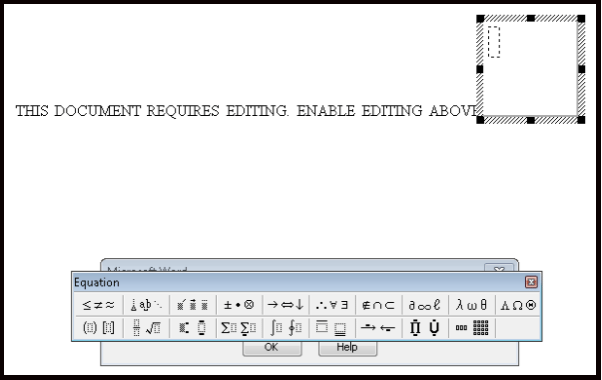
Figure 7: Example of a rich text format document lure.
Loki is primarily a password stealer, and given the already stated importance and role of email credentials in cybercrime, it is of no surprise that the threat actors are choosing to install Loki on the victim systems. Figure 9 shows a darkmarket advert for Loki.
Conclusion
The threats described in this snapshot are the result of our analysis of all threats seen the Telecom Services industry over the past 30 days, plus the 100 latest malware samples submitted by Lastline customers specifically in this vertical. There were significant differences in the trends seen in Telecom Services compared to the global trend: Threats arriving in Telecom Services organizations are ahead of the curve, essentially a Day0 attack, with very few prior submissions of samples being evidenced on VirusTotal. These malspam attacks represent the tip of emerging campaigns and reflect the inherent criminal value in stolen email credentials.
To read about the global trends against which we compared our findings in Telecom Services in this report, please download our Q4 2017 Malscape Monitor Report.
The post Malscape Snapshot: Telecom Services appeared first on Lastline.
Article Link: https://www.lastline.com/blog/malscape-snapshot-threats-seen-in-telecom-services/