Major Cyber Attacks in Review: March 2024
March 2024 witnessed a wave of cyber attacks targeting prominent organizations globally. From telecommunications giants to government pension funds, several high-profile entities encountered significant security incidents, underscoring the persistent threat of cybercrime.
Let’s explore these major cyber incidents that unfolded throughout the month to gain insights into the challenges faced by organizations in safeguarding their digital assets.
AT&T Confirms Data Breach Impacting 73 Million Customers
AT&T acknowledged a data breach affecting 73 million current and former customers, despite initial denials of the leaked data originating from their systems.
Initially disputed by AT&T, the breach was confirmed in late March, revealing that sensitive information of millions of customers, including names, addresses, phone numbers, and in some cases, social security numbers and birth dates, was compromised.
The breach, previously claimed by the threat actor group Shiny Hunters in 2021, resurfaced when another threat actor named “MajorNelson” leaked the same dataset on a hacking forum in 2024.
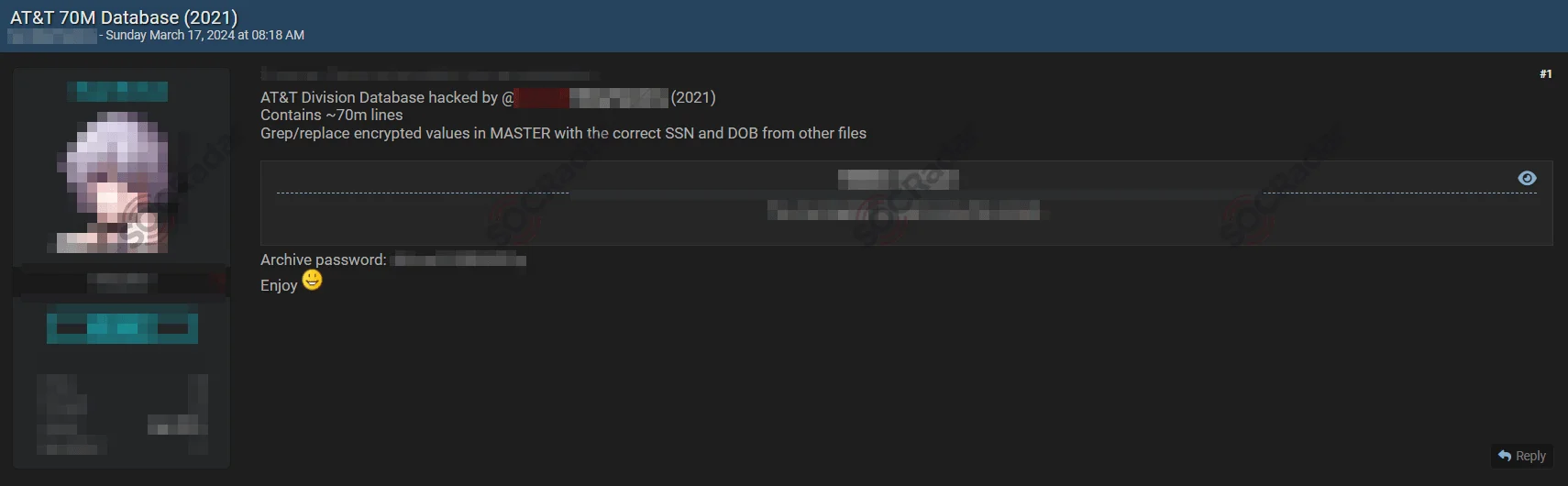
The new AT&T leak post (SOCRadar Dark Web News)
Evidence suggests that the leaked data originated from AT&T or DirectTV accounts, with numerous customers confirming unique email addresses used solely for their AT&T services.
Hot Topic Customer Data Exposed in Credential Stuffing Attacks
Hot Topic, a popular US retail chain, reported a potential data breach caused by a series of credential stuffing attacks in November 2023.

Hot Topic stands as a prominent American fast-fashion retail chain, boasting a widespread presence with over 600 locations.
The company discovered abnormal login activity on some of its customer rewards accounts, which was traced back to unauthorized entities using legitimate account credentials obtained from an undisclosed third-party source.
The potentially compromised data includes personal information such as names, email addresses, phone numbers, birth dates, mailing addresses, and purchase history.
In response to this incident, Hot Topic enlisted the help of third-party cybersecurity experts and took steps to improve its systems against future cyber attacks. Furthermore, the company has implemented a mandatory password reset for all account holders.
UnitedHealth Group Acknowledges Data Breach on Change Healthcare
UnitedHealth Group has confirmed a cyberattack on its Change Healthcare unit, revealing that sensitive data was accessed. The attack, which occurred in February, prompted the company to assess the potentially compromised personal, financial, and health information. Meanwhile, the U.S. Department of State was offering a reward of up to $10 million for information on the BlackCat/ALPHV ransomware group allegedly responsible for the incident.

Change Healthcare was listed as a victim by ALPHV (SOCRadar Dark Web News)
The attack targeted Change Healthcare’s payment systems, with details emerging about the extent of the breach and ongoing investigations.
In the latest news, following BlackCat’s shutdown, its affiliate ‘Notchy’ has joined forces with the RansomHub ransomware gang to target Change Healthcare again, despite allegedly receiving a ransom payment.
In a notice posted on RansomHub‘s data leak site, the threat actors threatened to release all data unless Change Healthcare and United Health negotiated with them. Screenshots that are already leaked appear to contain sensitive patient information and financial records.
The threat actors have given Change Healthcare a five-day deadline to meet their extortion demands, after which they intend to auction off the data.
INC Ransom Ransomware Attack on NHS Scotland
The ransomware group INC Ransom has claimed to be behind a recent attack on NHS Scotland, threatening to release 3TB of stolen data, including sensitive patient information. The group published several medical records as proof of the attack, including names, addresses, and sensitive medical information.

NHS Scotland, part of the National Health Service in the United Kingdom, is the publicly funded healthcare system serving Scotland.
NHS Dumfries and Galloway, one of the 14 NHS Scotland’s regions, previously reported a cyber incident in mid-March and issued a warning about the potential data breach. They also underscored the significance of the situation, stating that they are collaborating with partner agencies to ensure system security and assess potential risks.
Pro-Palestinian Hackers Breached 740GB of Viber’s Data
The messaging service Viber could be dealing with a data breach after a pro-Palestinian hacktivist group, Handala Hack, claims to have accessed its servers and stolen a significant amount of data. The group claims to have stolen over 740GB of data, including Viber’s source code, and is demanding 8 bitcoins, which is equivalent to roughly $540,000-$590,000.

Viber provides multi-platform support for instant messaging and internet-based voice calls.
Despite the claims, Viber has discovered no evidence of an intrusion into their systems or the compromise of user data. However, the company is looking into the allegations. If the breach is confirmed, it has the potential to expose Viber users’ personal messages, call logs, contact information, and financial information.
In the meantime, Viber users are advised to change their passwords, be cautious of phishing attempts, and stay informed about any updates.
France Travail Data Breach: 43 Million Job Seekers’ Data Compromised
In the last month, France Travail disclosed a significant breach, potentially compromising the data of 43 million job seekers.
The breach, affecting individuals registered over the past two decades, exposed sensitive information such as full names, social security numbers, and contact details. Although the breach occurred between February 6 and March 5, no specific threat actors have claimed responsibility.
Possible causes of the France Travail breach include account compromises, security vulnerabilities, or a service provider hack.
In response to the incident, heightened awareness against phishing and identity theft attempts is recommended.
SOCRadar monitors the clear and dark web, alerting you to such breaches and leaks of organizational, employee, or customer data. You can try our Labs’ free Account Breach feature to check if your information has been exposed online.
LockBit Ransomware Strikes South Africa’s Government Workers Pension Fund
GEPF, managing the pensions of 1.7 million government employees and pensioners, fell victim to LockBit’s cyber onslaught.
Last month, the LockBit ransomware gang claimed an attack on South Africa’s Government Employees Pension Fund (GEPF), causing operational disruptions and pension payment delays. Despite initial reassurances from the Government Pensions Administration Agency (GPAA) of no breach, subsequent investigations revealed compromised systems.
While no pension payments were affected, the incident led to office closures and service interruptions. Though regional offices have since resumed operations, the attack underscores South Africa’s vulnerability to cyber threats, with previous hits on state-owned institutions.
Although LockBit’s infrastructure was dismantled in February in Operation Cronos, the gang’s claim of the GPAA attack suggests ongoing challenges in combating cybercrime.
Ivanti Vulnerabilities Exploited in CISA Attack
It was revealed that threat actors breached the U.S. Cybersecurity and Infrastructure Security Agency (CISA) systems in February. In the attack, the attackers exploited vulnerabilities in Ivanti products, disrupting operations.

Read about the Ivanti zero-day vulnerabilities in SOCRadar blog post
CISA detected suspicious activities related to Ivanti product vulnerabilities a month earlier and promptly deactivated two affected systems to mitigate the breach. While specifics about the attack’s perpetrators remain undisclosed, sources identified compromised systems as repositories of critical infrastructure and sensitive industrial data.
CISA urged organizations to heed its advisory highlighting exploits targeting Ivanti gateways. The incident raises concerns about Ivanti’s susceptibility to cyber threats, underscoring the need for heightened vigilance and robust security measures.
This breach adds to previous warnings about Ivanti vulnerabilities, emphasizing the critical importance of proactive cybersecurity measures in safeguarding against sophisticated cyber threats.
American Express Third-Party Data Breach
Following a data breach at a third-party merchant processor, American Express has notified its customers that their credit card information may have been exposed. The processor, which handled card member data for American Express, was the true target of the breach.
The scope of the breach, including the number of customers affected, the identity of the merchant processor, and the time of the attack, is still unknown.

American Express is a global financial services company that issues prepaid, credit, and charge cards to individuals, small businesses, and corporate consumers worldwide.
In response to the breach, American Express has notified the appropriate regulatory authorities and is in the process of notifying affected customers. The company has also advised its customers to periodically review their account statements for any suspicious activity over the next 1 to 2 years and to enable instant notifications via the American Express mobile app for real-time fraud alerts and purchase notifications.
Article Link: https://socradar.io/major-cyber-attacks-in-review-march-2024/
