As 2023 draws to a close, it’s time to look back on a remarkable year. It’s been quite a journey.
Our team has been hard at work this year, and we’re happy and excited to look back and see how far our interactive sandbox has come in just 12 short months.
- We’ve begun automating real-time malware interactions with the help of Machine Learning
- Released Threat intelligence feeds. They pull data from ANY.RUN’s repository of almost 50 Million unique quarterly IOCs, helping you expand threat coverage of SIEM systems.
- Added a Script tracer to analyze script execution step-by-step script
- And so much more
With that said, let’s go over every major update to ANY.RUN in 2023.
ANY.RUN: our biggest updates in 2023
Let’s cover the major improvements that took place in the ANY.RUN sandbox this year:
- Automated interactivity (ML). ANY.RUN can now intelligently detect and prioritize interactive elements. It can click on links, buttons, complete CAPTCHAs and perform other actions to detonate malware, capturing the resulting system behavior. This is especially useful for those who utilize our sandbox via API, since it dramatically increases detection rate of complex malware attacks.
- Residential proxy: You can now switch from a datacenter IP to a residential IP. Use Residential proxy to hide sandbox activity and mimic local traffic. This sidesteps malware’s anti-sandbox tricks, gets around geo-blocks, and helps you analyze C2 communication.
- ChatGPT reports. Get detailed and logical AI-generated summaries for process trees, command line data, Suricata rule triggers, HTTP connections, registry changes, and mutex patterns for links and files you submit. Learn more.
- Modular Static Discovering. Modules broaden the file types you can analyze in Static Discovering. The sandbox now auto-selects the best method for data extraction, even from complex nested structures. Current modules already cover MSG/Email, Office, OneNote, PDF, LNK, and ZIP.
- Threat Intelligence Feeds. ANY.RUN’s new service is our first step to better utilize our database of latest threats for Intelligence. It streams IOCs in STIX format, ready for modern SIEM systems. A wide range of threat data like malicious IPs, URLs, and domains is available. Plus, you can pull contextual metadata for IOCs to speed up incident investigations.
- QR code detector and extractor. Attackers began delivering malicious links in QR codes. We responded swiftly, adding a QR code module to Static Discovering. It auto-detects and extracts links from QR codes — even when they’re nested in other files — so you can rapidly submit QRs for further analysis in the system.
- Uploading addition files to active tasks. You can now bring your own set of tools to ANY.RUN, or augment tasks with files that the malware depends on to execute. All users can upload files to an active virtual session, up to 500 MB in total. Hunter and Enterprise subscribers also get Tool collections — a separate tab for quick access to favorites.
- Script tracer. Script-based malware has been on the rise in 2023. That’s why we added a tool that helps you trace and deobfuscate the execution flow of scripting programs. It works with JScript, VB Script, VBA and Macro 4.0 and is supported on all OS versions available in ANY.RUN, from Windows 7 to Windows 11.
- Expanded Suricata rules. ANY.RUN now shows more information about triggered Suricata rules. You’ll be able to see which specific rule was triggered, identify the traffic segment affected, the relevant fields, and often, even see the rule itself.
Even more exciting updates:
For our Enterprise-plan subscribers, Single Sign-On (SSO) authentication now offers seamless platform access. For in-depth malware analysis, security analysts can download and examine memory dumps of various processes.
Additionally, the platform has enhanced file authentication through digital signatures, allowing users to verify file authenticity and trustworthiness.
Simplifying data retrieval, users can export all sandbox analysis data in a single ZIP file. The service has improved its detection logic for IPs, URLs, and domains, ensuring better identification of malicious activities like phishing and QR code scams.
Finally, API request quotas have been restructured for team-wide sharing, allowing all team members to collectively use the total API requests available.
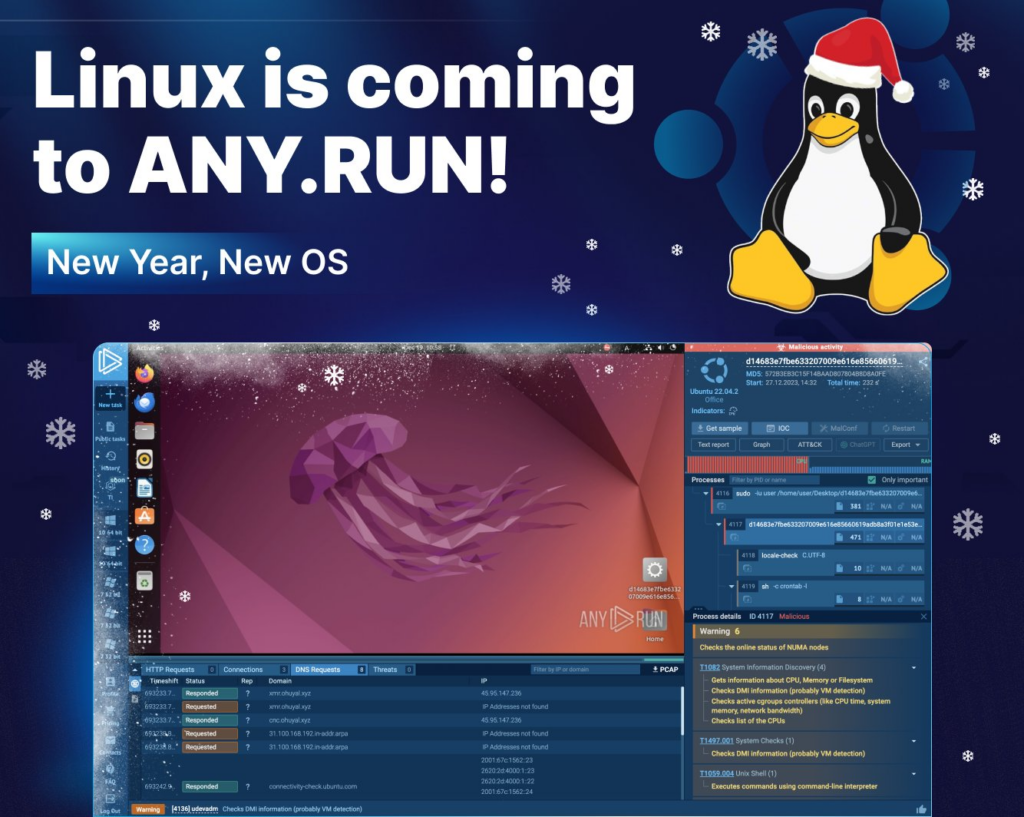
Linux is Coming to ANY.RUN
We’ve teased that starting 2024 ANY.RUN will support Ubuntu. You’ll be able to analyze samples, collect IOCs and streamline research of Linux malware with all of the advantages ANY.RUN brings, like interactivity and real-time results. Ubuntu 22.04.2 will be available at launch with more options to follow.
ANY.RUN’s community now has an official home
Another highlight of 2023 was the launch of our Discord server. We thought it’d be great to have a dedicated space where all ANY.RUN malware hunters can gather, share news and tips about malware analysis, and directly interact with our team.
We’re thrilled to announce that our ANY.RUN Discord community now boasts over 3,000 members and is expanding daily. If you haven’t joined us yet, we’d be delighted to welcome you aboard!
Become part of ANY.RUN’s growing community
Join our DiscordANY.RUN Top Awards in 2023
This year, our service collected many prestigious cybersecurity awards. We’re incredibly proud and humbled by this recognition. It’s a journey we couldn’t have made without you, our users. Here’s what you’ve helped us achieve:
- ANY.RUN won the Fortress Cyber Security Award in the Threat Detection category.
- Our sandbox was awarded the Malware Monitoring & Analysis Innovator of the Year 2023 by Innovation in Business.
- ANY.RUN was named the Most Innovative in Malware Analysis by The Cyber Defense Awards.
ANY.RUN was also a finalist at Innovation in Cyber 2023 by The National Cyber Awards and for the Most Innovative Cloud Product or Service by the Cloud Excellence Awards.
And, last but not least, on G2, ANY.RUN was recognized in 3 categories:

Most popular malware of 2023: ANY.RUN’s top five by uploads
Of course, since ANY.RUN is a tool designed for malware hunters, it’s only natural that we take a closer look at the top 5 most popular malware types and families in 2023. This is just a sneak peek — our more extensive yearly report will be released soon.
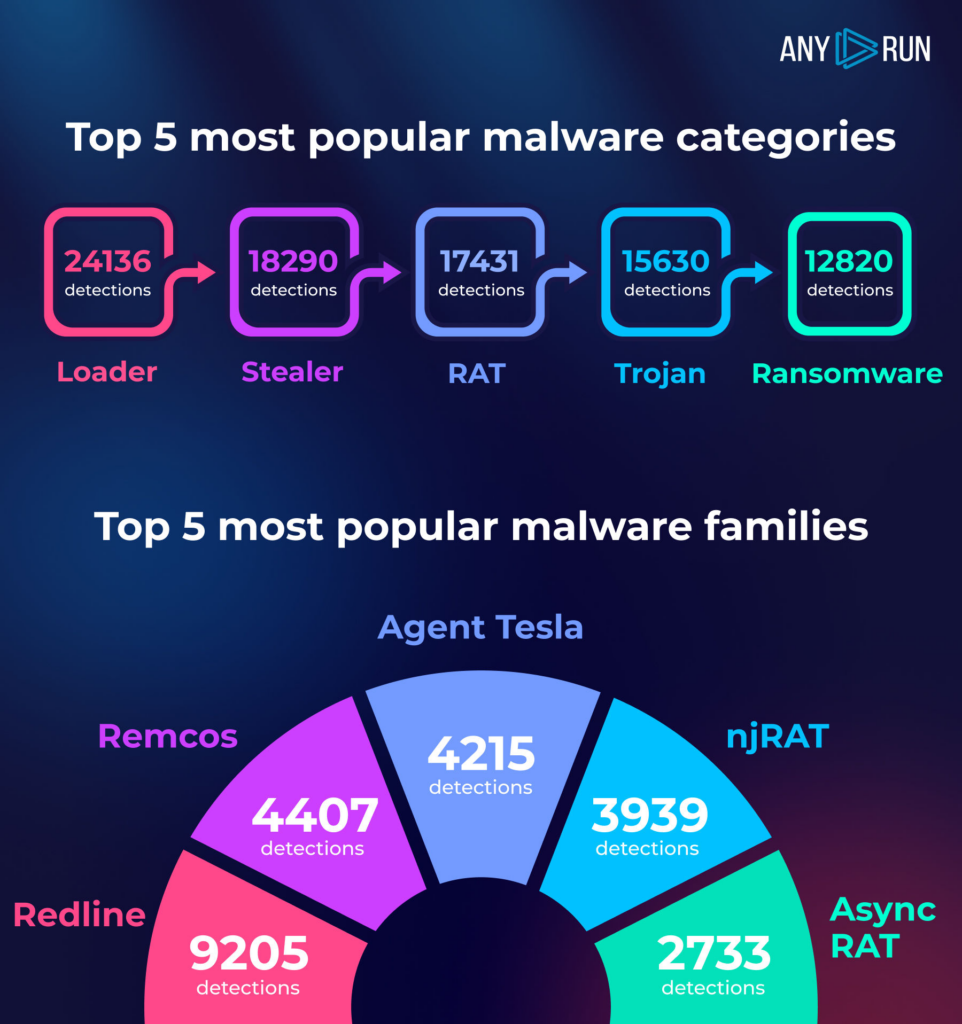
Top 5 most popular malware: categories
- Loader with 24,136 detections
- Stealer with 18,290 detections
- Remote Access Trojan (RAT) with 17,431 detections
- Trojan with 15,630 detections
- Ransomware with 12,820 detections
Top 5 most popular malware: families
- Redline with 9205 detections
- Remcos with 4407 detections
- Agent Tesla with 4215 detections
- njRAT with 3939 detections
- AsyncRAT with 2733 detections
Wrapping up
2023 has been a remarkable year for us at ANY.RUN, filled with both achievements and challenges. The cybersecurity landscape faced tough times, with global unrest unfortunately opening doors for increased cyber threats. The ease of creating and using malware has reached a point where practically anyone could be a potential threat.
Our goal is to combat these challenges by enhancing our sandbox’s capabilities and providing robust support to you, our dedicated community, in your malware research efforts. Together, we’re committed to making the online world a safer place, one step at a time.
We wish everyone a Happy New Year! Let it be the year of progress, security and thriving.
A few words about ANY.RUN
ANY.RUN is a cloud malware sandbox that handles the heavy lifting of malware analysis for SOC and DFIR teams. Every day, 300,000 professionals use our platform to investigate incidents and streamline threat analysis.
Request a demo today and enjoy 14 days of free access to our Enterprise plan.
The post Looking back at 2023 with ANY.RUN appeared first on ANY.RUN's Cybersecurity Blog.
Article Link: Looking back at 2023 with ANY.RUN - ANY.RUN's Cybersecurity Blog