AhnLab Security Emergency response Center(ASEC) has confirmed the distribution of the LokiLocker ransomware in Korea. This ransomware is almost identical to the BlackBit ransomware and their common traits have been mentioned before in a previous blog post. A summary of these similarities is as follows.
Similarities Between LokiLocker and BlackBit
- Disguised as svchost.exe
- Same obfuscation tool used (.NET Reactor)
- Registered to the task scheduler and registry (persistence of malware)
- Ransom note and the new file icon image set after encryption
Disguised as svchost.exe
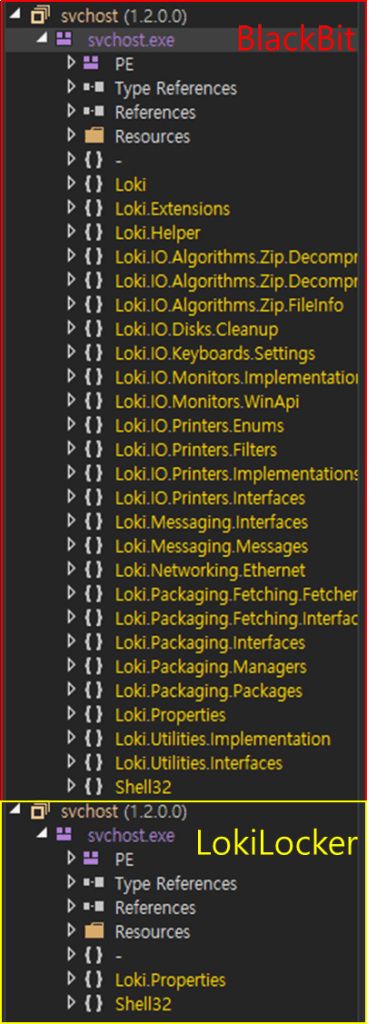
The BlackBit ransomware, which was covered in a previous post, disguised itself as a svchost.exe file. Similarly, the recently discovered LokiLocker ransomware was also found disguised as a svchost.exe file.

Same packer used (.NET Reactor)
A .NET Reactor was used to obfuscate the code and deter analysis. By looking at the unpacked BlackBit ransomware, it becomes clear that the malware was derived from the LokiLocker ransomware.
Registered to the task scheduler and registry (persistence of malware)
Similarities have also been found in their behavioral aspects. The following figure shows that the LokiLocker ransomware registers itself to the task scheduler and registry under the name”Loki” before it starts its encryption process. The ransomware also generates its ransom note before it begins encrypting. Afterward, it carries out actions such as deleting volume shadows to prevent recovery, as well as behaviors aimed at obstructing detection and leaking information.


Ransom note and the new file icon image set after encryption
After successfully infecting a system, LokiLocker creates a ransom note named Restore-My-Files.txt in each infected folder path, containing the message below. The ransom note and the icon of the infected files that have been confirmed were also found to be very similar to those of the BlackBit ransomware.


AhnLab’s anti-malware software, V3, detects and responds to LokiLocker ransomware with a variety of detection points, including file detection and behavior-based detection. To prevent ransomware infection, users must be cautious of running files from unknown sources and make sure to scan suspicious files with an anti-malware program while also keeping the program updated to the latest version. AhnLab’s anti-malware software, V3, detects and blocks the malware using the following aliases:
[File Detection]
Ransomware/Win.Loki.C5421356 (2023.05.03.00)
[Behavior Detection]
Ransom/MDP.Delete.M2117
[IOC]
d03823a205919b6927f3fa3164be5ac5
Subscribe to AhnLab’s next-generation threat intelligence platform ‘AhnLab TIP’ to check related IOC and detailed analysis information.
The post LokiLocker, a Ransomware Similar to BlackBit Being Distributed in Korea appeared first on ASEC BLOG.
Article Link: LokiLocker, a Ransomware Similar to BlackBit Being Distributed in Korea - ASEC BLOG