What is LOTL Attack?
Living Off the Land (LOTL), also known as lolbins, is a sophisticated cyberattack technique that leverages legitimate tools already present within a victim’s system to execute and sustain an attack. Contrary to the traditional malware attacks that rely on files deployed on the victim, LOTL attacks are fileless. In LOTL attacks, the attacker is not required to install any code or scripts within the target system. Instead, theyutilize tools, such as binaries, scripts, libraries, or drivers, that can be present in the system, such as CertUtil, Regsvr32, Schtasks, PowerShell and Windows Management Instrumentation (WMI).
It is incredibly challenging to detect LOTL attacks by relying on traditional security tools that search for known malware scripts or binaries because of it using native tools. This stealthy approach allows the attacker to dwell undetected within the victim’s environment for extended periods, sometimes even years. This increased stealth grants the attacker more time to escalate privileges, steal data, lateral movement, operate ransomware attacks, and set backdoors for future access. Because of these traits, LOTL attacks are becoming increasingly common. Which can be backed up by the CrowdStrike 2023 Global Threat Report. It is stated that malware-free activity accounted for 71% of all detections in 2022, up from 62% in 2021, indicating a shift away from malware use.
The reason for the shift towards LOTL techniques can be that many common LOTL attack vehicles, such as WMI and PowerShell, are often on the victim network’s “allow” list. This provides a perfect disguise for adversaries. Additionally, the lack of files or signatures makes it difficult to attribute LOTL attacks. It is also indicated in a report by Splunk that adversaries breaching a system are likely to start up the PowerShell command line utility 28.49% of the time, allowing them to move laterally throughout a network and gain persistence on the compromised machine.
How Can Attackers Leverage LOTL Techniques?
Living Off the Land (LOTL) attackers utilize several methods to gain access to a system and utilise its native tools for malicious purposes. One such method is the use of exploit kits, which are collections of code that take advantage of known vulnerabilities in an operating system or application. These kits can inject directly into memory, making them an efficient tool for launching a fileless malware attack, such as a LOTL attack.
Another common method involves hijacking legitimate tools already present in the system, such as File Transfer Protocol (FTP) clients, PowerShell, and Windows Management Instrumentation (WMI). These tools can be used to escalate privileges, access different systems and networks, steal or encrypt data, install malware, and set backdoor access points.
Other techniques include the use of registry resident malware, which installs itself in the Windows Registry to remain persistent while evading detection, and memory-only malware, which resides only in memory and is, therefore, difficult to detect. Fileless ransomware uses fileless techniques to embed malicious code in documents or write the malicious code directly into memory, then utilize native tools like PowerShell to encrypt files. Attackers may also use stolen credentials to access their target under the guise of a legitimate user and then use native tools such as WMI or PowerShell to conduct their attack.
To put it into a more practical context, in a post couple of months ago, Microsoft reported that The Volt Typhoonthreat actor, a state-sponsored group based in China, has been leveraging LOTL techniques to target critical infrastructure organizations in the United States. The group puts a strong emphasis on stealth in their campaign, using almost exclusively LOTL techniques and hands-on-keyboard activity. They issue commands via the command line to collect data, including credentials from local and network systems, put the data into an archive file to stage it for exfiltration, and then use the stolen valid credentials to maintain persistence.
To blend into normal network activity, Volt Typhoon routes traffic through compromised Small Office and Home Office (SOHO) network equipment, including routers, firewalls, and VPN hardware. They have also been observed using custom versions of open-source tools to establish a command and control (C2) channel over proxy to further stay under the radar.
The initial access to targeted organizations is achieved through internet-facing Fortinet FortiGuard devices. Once inside, Volt Typhoon begins conducting hands-on-keyboard activity via the command line, relying on Living-off-The-Land commands to find information on the system, discover additional devices on the network, and exfiltrate data. They also dump credentials through the Local Security Authority Subsystem Service (LSASS) and use the command-line tool Ntdsutil[.]exe to create installation media from domain controllers.
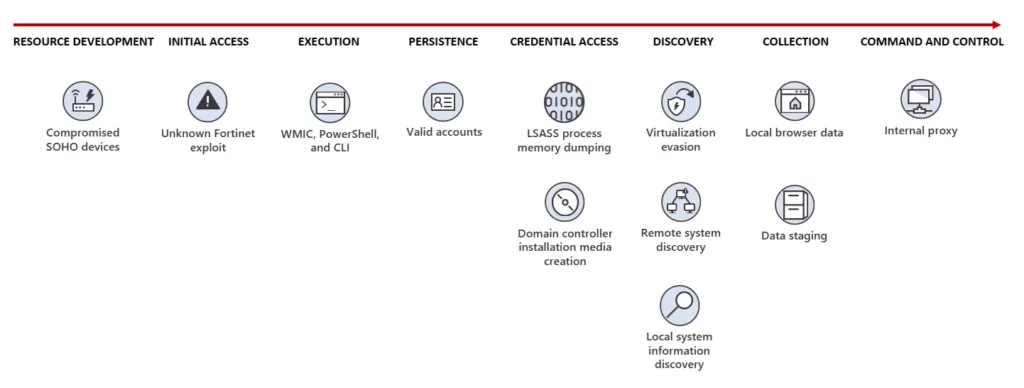 Figure 1: Attack diagram of Volt Typhoon (Source: Microsoft)
Figure 1: Attack diagram of Volt Typhoon (Source: Microsoft)
LOTL attacks leverage various tools that are native to the system being targeted.
Here are some commonly used tools:
- PowerShell: A versatile scripting language and shell framework for Windows systems, PowerShell is often used by attackers to execute malicious scripts and commands.
- Windows Management Instrumentation (WMI): An administrative feature for accessing and managing Windows system components, WMI can be exploited by attackers to perform various malicious activities, such as data theft and system manipulation.
- PsExec: A lightweight command-line tool for executing processes on remote systems, PsExec can be used by attackers to run malicious processes on compromised systems.
- Windows Sysinternals, NETSH, or SC tools: These are examples of dual-use tools which have been used for “living off the land” attacks.
- Windows Command Processor (CMD[.]exe), Windows-Based Script Host (WScript[.]exe), and Console-Based Script Host (CScript[.]exe): These native Windows tools can be used by attackers to execute malicious scripts and commands.
There are three projects dedicated to help guide against LOTL attacks. We will look at some examples of usage presented on the projects to see the potential LOTL usage.
 Figure 2: LOLBAS, GTFOBins, and LOLDrivers
Figure 2: LOLBAS, GTFOBins, and LOLDrivers
Living Off The Land Binaries and Scripts (LOLBAS) is a project that compiles a list of Windows executables that can be used to bypass security controls, execute code, and more. It’s a resource for understanding how these binaries can be potentially exploited in a system.
On the other hand, GTFOBins is a similar project but focused on Unix systems. It curates Unix binaries that can be used to bypass local security restrictions, providing insights into how these binaries can be misused in compromised systems.
The LOLDrivers is a project that catalogs legitimate Windows drivers that can be exploited by attackers to bypass security measures. It provides a list of these drivers, their capabilities, and potential risks to aid in threat understanding and mitigation.
The LOLBAS project page for WMI command-line provides information on how the WMIC utility can be used in LOTL attacks. WMIC provides a command-line interface for WMI and can be found in the System32 and SysWOW64 directories of a Windows system.
Several use cases for WMIC in an attack scenario, such as executing a binary file hidden in Alternate Data Streams, and executing a binary from WMIC to evade defensive countermeasures, are seen below. Each use case includes the command used, the privileges required, the applicable operating systems, and the corresponding MITRE ATT&CK® technique.
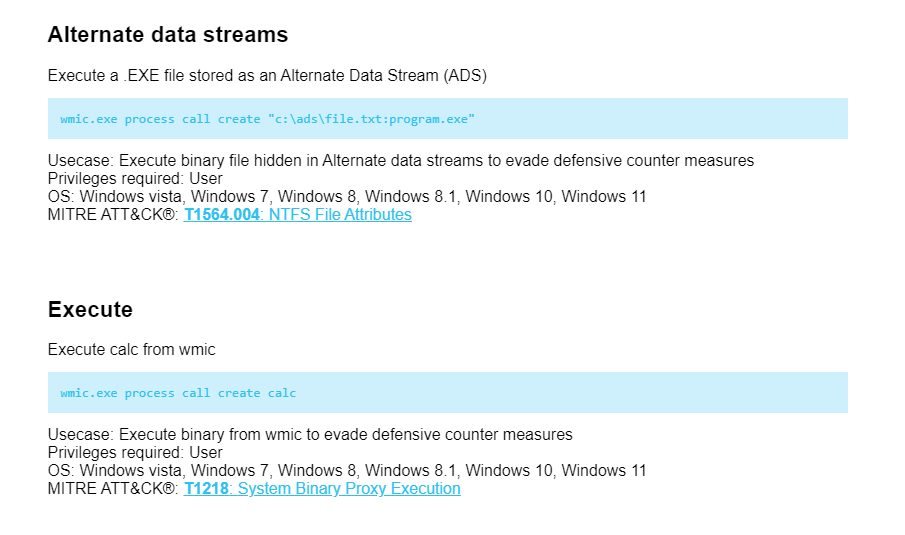 Figure 3: WMIC page on LOLBAS
Figure 3: WMIC page on LOLBAS
In another case, the LOLBAS project page for Netsh provides information on how the Windows network tool Netsh can be used in LOTL attacks.
The page outlines a use case for Netsh in an attack scenario, where it is used to execute a .dll file and gain persistence every time the Netsh command is called. This can be achieved with the command “netsh[.]exe add helper C:\\Users\\User\\file.dll”. This use case requires admin privileges and can be applied to various Windows operating systems. The corresponding MITRE ATT&CK® technique is T1546.007: Netsh Helper DLL.
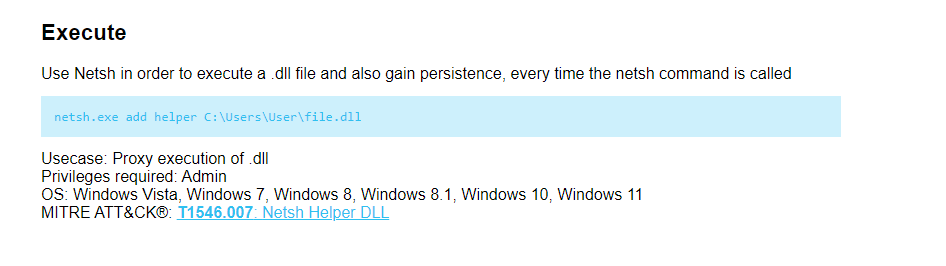 Figure 4: Netsh page on LOLBAS
Figure 4: Netsh page on LOLBAS
Who Leverages LOTL Attack Techniques?
As we already mentioned, LOTL techniques are increasingly being adopted by various threat actors. Both ransomware groups and nation-state actors are already using LOTL in their attacks. The primary reason for this trend is the stealth and efficiency that LOTL offers. By using legitimate tools and processes that are already present on the target system, these threat actors can blend in with normal network activity, making their malicious operations harder to detect. Furthermore, LOTL techniques allow them to bypass security measures that typically focus on detecting and blocking malware.
Vice Society, a notorious ransomware group, is one such actor that has been leveraging LOTL attack techniques to deploy its malicious payloads. According to a report by Unit 42, Vice Society has been observed using PowerShell, a legitimate scripting language and automation framework, to carry out their attacks. They use PowerShell to download and execute their ransomware directly in memory, thereby avoiding detection by traditional antivirus solutions. Below you can see the function diagram of the PowerShell script used. This is a clear example of how LOTL attack techniques can be used to effectively infiltrate and compromise systems.
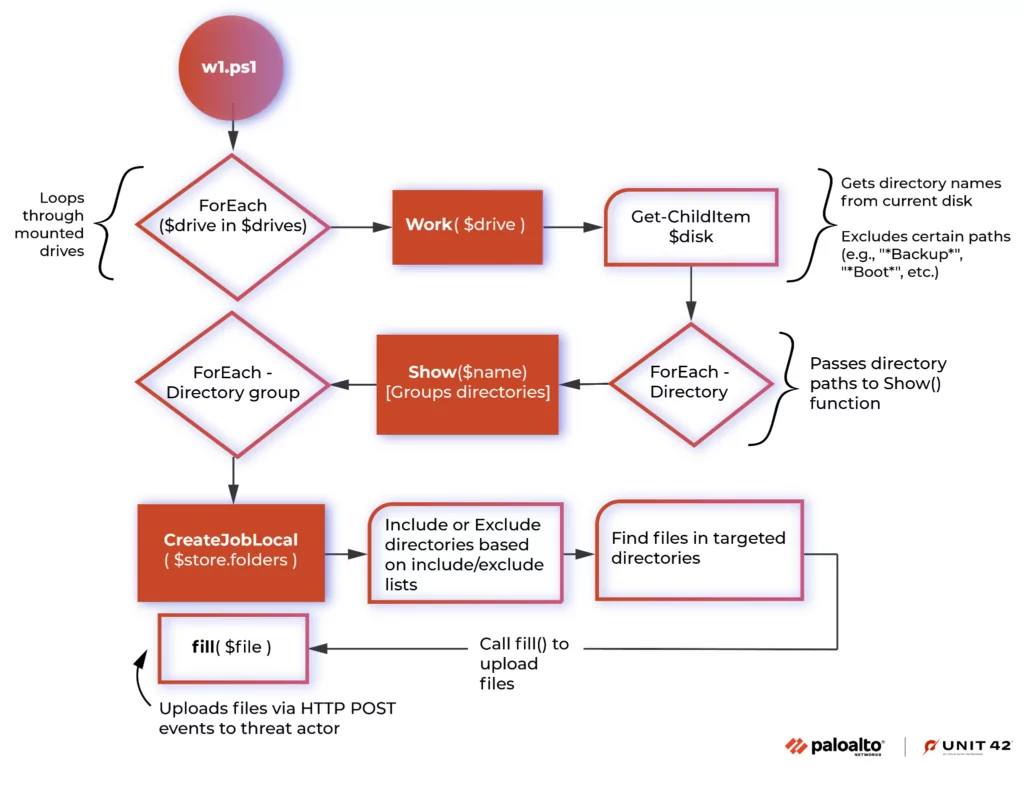 Figure 5: Function diagram of the PowerShell script (Source: Unit42)
Figure 5: Function diagram of the PowerShell script (Source: Unit42)
The Cybersecurity and Infrastructure Security Agency (CISA) has also issued the AA23-144a regarding the use of LOTL techniques by a China State-Sponsored Threat Actor, Volt Typhoon, which we already mentioned as Microsoft reported on their activities. The actor has been exploiting publicly known vulnerabilities to gain initial access, then leveraging LOTL attack techniques to move laterally within the network, escalate privileges, and evade detection. This includes the use of PowerShell for scripting, Certutil for downloading files, and WMIC for execution. The alert from CISA underscores the growing threat posed by LOTL attack techniques and the need for organizations to implement robust detection and mitigation strategies.
Mitigations and How Can SOCRadar Help?
-
Regularly update and patch systems: Keeping systems up-to-date can help prevent attackers from exploiting known vulnerabilities.
SOCRadar’s Attack Surface Management (ASM) module can significantly aid in this process. It continuously monitors your digital assets, identifying any outdated systems or applications that may pose a security risk. By providing real-time visibility into your attack surface, it enables you to proactively address vulnerabilities before they can be exploited, thereby enhancing your organization’s overall cybersecurity posture.
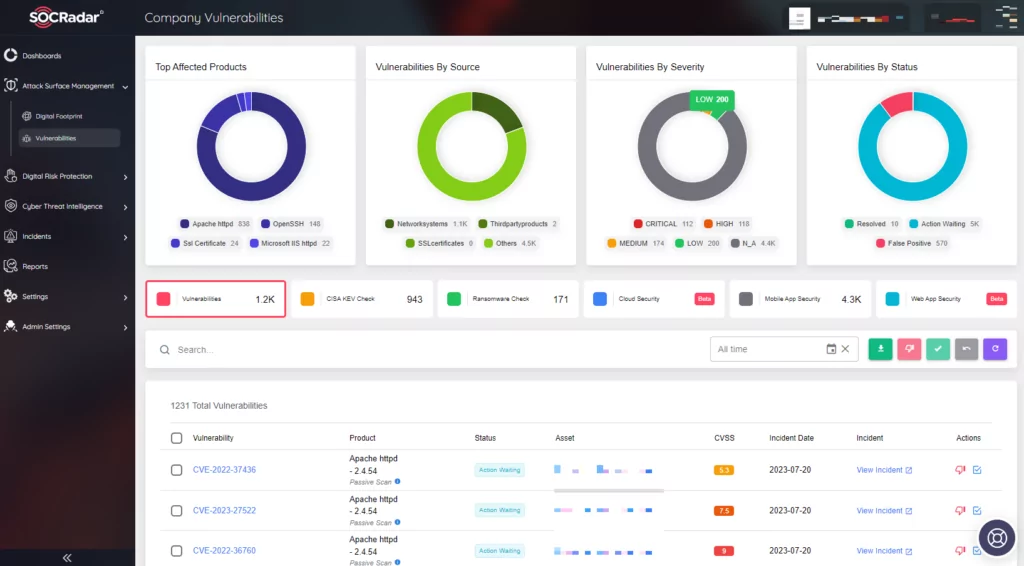 Figure 6: SOCRadar Company Vulnerabilities page
Figure 6: SOCRadar Company Vulnerabilities page
- Use Multi-Factor Authentication (MFA): MFA adds an additional layer of security, making it more difficult for attackers to gain access even if they have a user’s password.
- Principle of least privilege: By restricting user privileges, organizations can limit the potential damage an attacker can do.
- Regularly back up data: Regular backups can help organizations recover more quickly if an attack does occur. Especially in the case of a ransomware attack, regular offline backups can save the organization from devastating damage.
- Implement network segmentation: By separating networks into different segments, organizations can limit the attackers’ hand in spreading.
- Employ User Behavior Analytics (UBA): UBA can significantly aid in detecting LOTL attacks by identifying anomalies, detecting insider threats, spotting privilege misuse, or uncovering data exfiltration.
- Employ or Hire Threat Hunters: Threat hunting can help in detecting LOTL attacks by proactively searching for Indicators of Compromise (IoCs) within a network. This includes unusual usage of legitimate tools, abnormal user behavior, and unexpected network connections. By actively seeking out these signs, threat hunters can identify and mitigate LOTL attacks before they cause significant damage.
- Employee Training: Training employees on safe practices and cybersecurity awareness can help in recognizing unusual system behavior, unexpected alerts or messages, or changes in the system.
- Leverage threat intelligence: Leveraging threat intelligence is crucial in staying informed about new attack techniques, Indicators of Compromise (IoCs), and other relevant threat data such as Supply Chain Intelligence. SOCRadar can provide detailed insights about emerging threats. This information can help organizations to proactively update their security measures, thereby preventing potential breaches and minimizing the impact of any attacks that do occur.
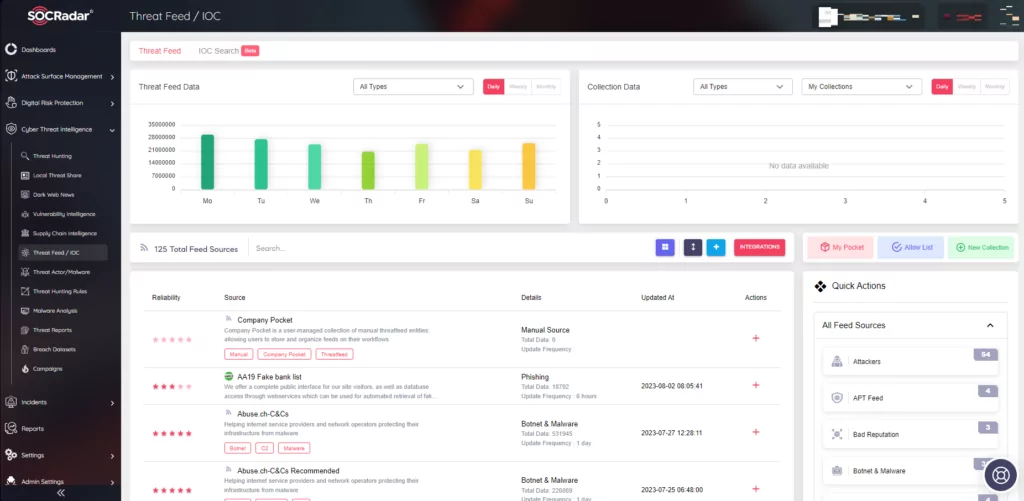 Figure 7: SOCRadar Threat Feed/IOC
Figure 7: SOCRadar Threat Feed/IOC
LOTL attacks present a significant challenge in the cybersecurity landscape. By leveraging legitimate tools and processes already present in the target system, these attacks can evade traditional security measures and cause significant damage. Various threat actors, ranging from ransomware groups to nation-state actors, are increasingly leveraging LOTL attack techniques due to their stealth and efficiency. These underscore the growing threat posed by LOTL techniques and the need for robust detection and mitigation strategies.
However, understanding the nature of LOTL attacks and the tools used can equip us with the knowledge to detect and mitigate them. The use of advanced security measures such as User Behavior Analytics, threat hunting, and threat intelligence can significantly enhance an organization’s ability to combat LOTL attacks.
In conclusion, as LOTL attacks continue to evolve, staying informed and proactive is key. By understanding the nature of these attacks and implementing robust security measures, organizations can effectively safeguard their digital assets against this growing threat.
The post Living Off the Land (LOTL): The Invisible Cyber Threat Lurking in Your System appeared first on SOCRadar® Cyber Intelligence Inc..
Article Link: Living Off the Land (LOTL): The Invisible Cyber Threat Lurking in Your System
