Customers often ask us how to implement the suggestions provided in our blogs and threat advisories to better protect their environments. The goal of this blog is to do just that.
By showing you how to better use our products, you’ll be able to protect against Emotet and other malware. Emotet is a Trojan downloader spread by malicious spam campaigns using JavaScript, VBScript, and Microsoft Office macro functions. It downloads additional malware and persists on the machine as a service. Emotet has been observed to download ransomware, mass-mailing worms, W32/Pinkslipbot, W32/Expiro, W32/Dridex, and banking Trojans.
NOTE: Always test changes prior to implementing them in your environment.
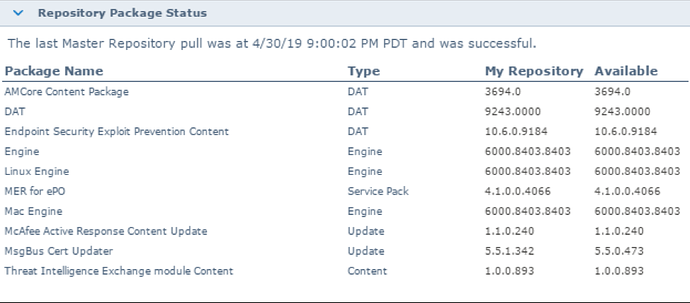
1. DATs and product updates
One of the most common issues seen while in Support was an outdated DAT.
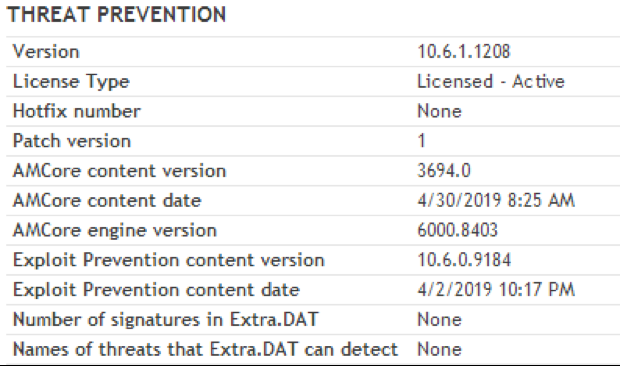
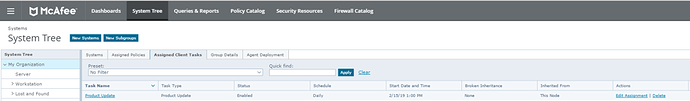
2. Make sure you have at least one scheduled product update task in McAfee ePO to run daily.
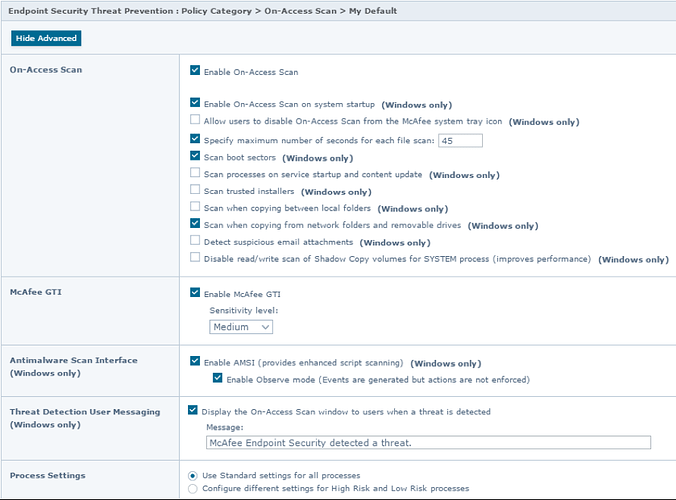
3. On-Access Scan (OAS) configuration for McAfee Endpoint Security and McAfee VirusScan Enterprise
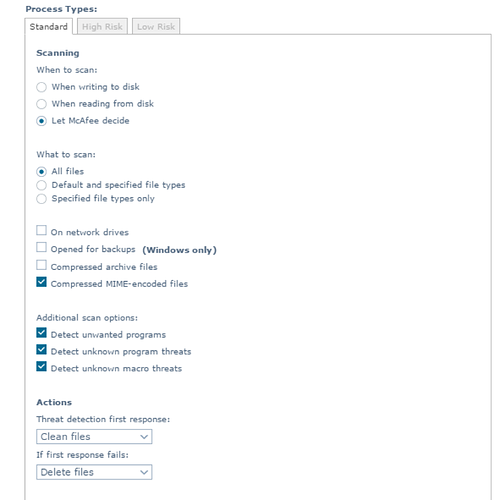
Ensure that On-Access Scan (OAS) is enabled and set to scan on read and write and that entire drives aren’t excluded from being scanned. McAfee Endpoint Security and McAfee VirusScan Enterprise allow you to configure different scan settings based on the process. You can enable “Configure different settings for High-Risk and Low-Risk processes” to improve performance and reduce the need for file/folder exclusions. See KB88205 for more information.
Be sure that Artemis/GTI is enabled and that the first scanner action is “Clean” and the second action is “Delete”.
NOTE: Setting Artemis/GTI to High or Very High should be done gradually and with testing to reduce the risk of false positives. See KB53735 for more information.
4. On-Demand Scan (ODS)
A weekly On-Demand Scan (ODS) is suggested to ensure that your systems don’t have malware or PUPs. Do not run an ODS during peak business hours, as users may complain about system performance.
5. Access Protection (AP)
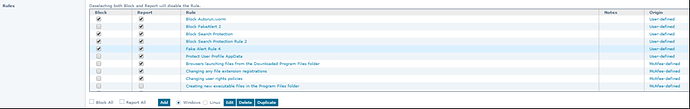
While the default Access Protection (AP) rules provide decent coverage, both McAfee Endpoint Security and McAfee VirusScan Enterprise allow for the creation of user-defined rules to prevent infection and the spread of worms or viruses. Below are some pre-created ones that should be tested and enabled in your environment to provide additional protection.
Pre-Defined Rule:
- Disabling Registry Editor and Task Manager — Certain malware may attempt to disable the Task Manager to prevent the user from terminating the malicious process. Enable this AP rule to prevent the Task Manager from being disabled.
6. Access Protection (AP) rules for virus and worm outbreaks
These rules should only be enabled during a virus outbreak and for workstations only. Implementing the last two shown below may cause issues with file servers running McAfee VirusScan Enterprise or McAfee Endpoint Security. Always test these rules before you enable them:
- Remotely Creating Autorun Files
- Remotely Creating or Modifying Files or Folders
- Remotely Accessing Local Files or Folders
NOTE: Only create a separate AP policy for workstations if you wish to continue using the AP rules below. Remotely creating files between workstations is unusual behavior.
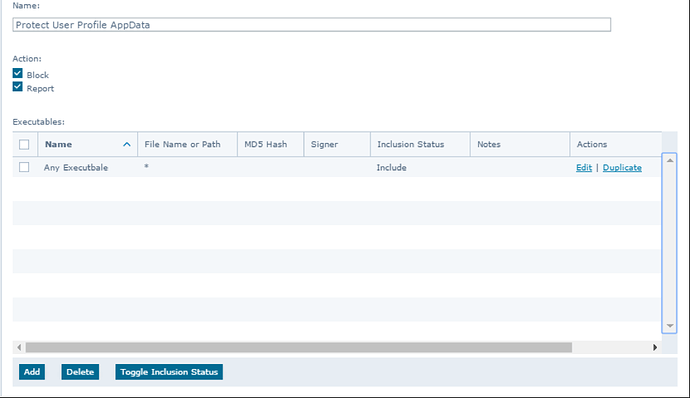
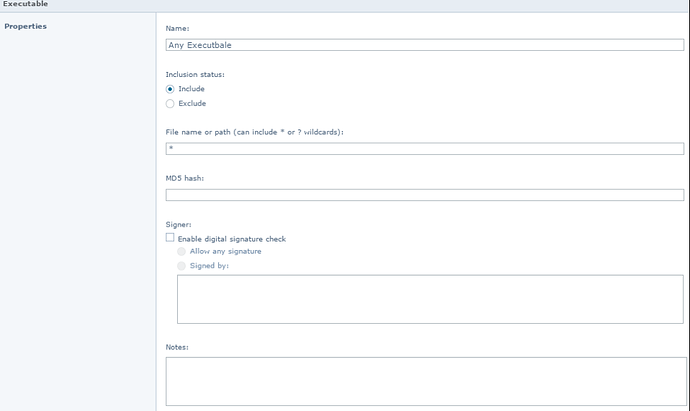
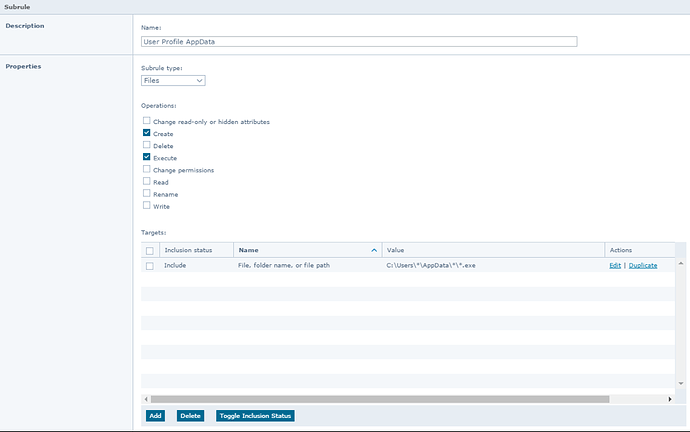
7. User-defined AP file/folder patch locations
The user-defined rule below is one common location for malware.
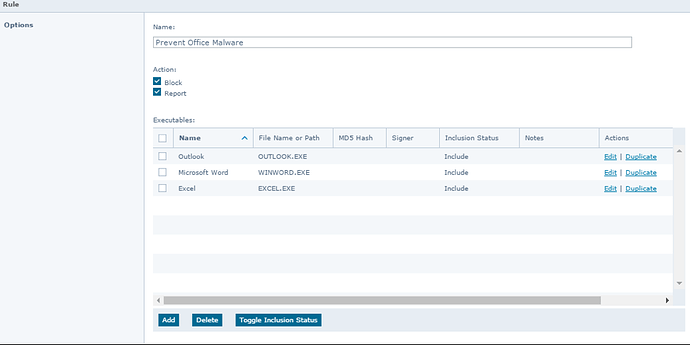
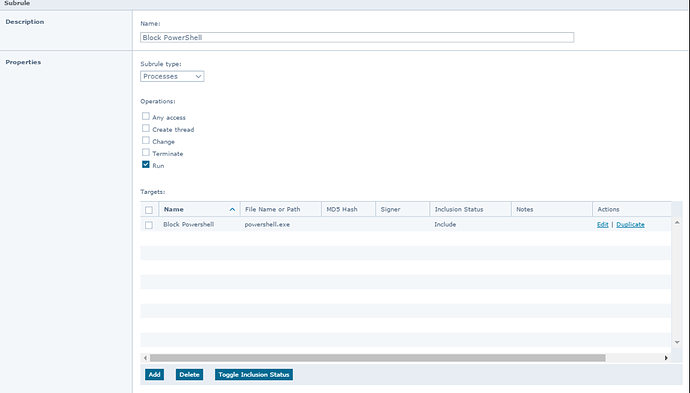
8. Microsoft Office malware
Most threats come through email and are often downloaders for other malware. The AP rule below is intended to prevent Microsoft Office applications from executing PowerShell. You can include CScript.exe and WScript.exe as well.
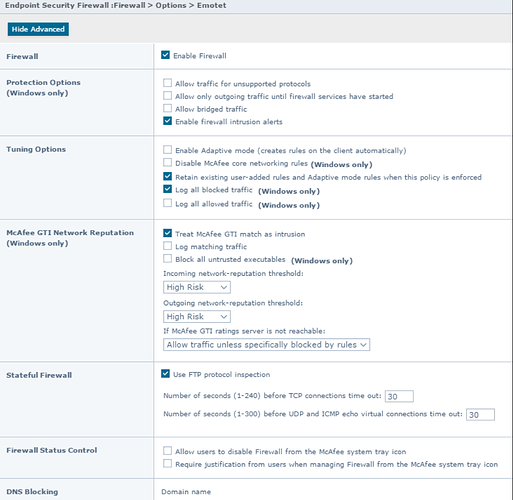
9. McAfee Endpoint Security firewall
Almost all organizations have a firewall at the perimeter level. Some may opt to disable the built-in firewall on workstations and servers. The McAfee Endpoint Security Firewall is more comprehensive than the Windows firewall and can be used to prevent communication to malicious IPs and domains.
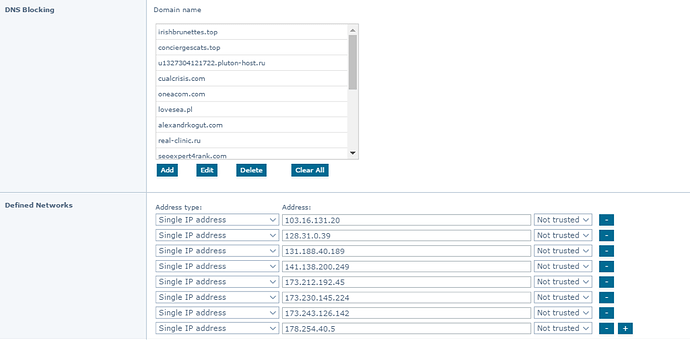
10. Blocking malicious traffic with the firewall
Blocking malicious network traffic prevents new variants from being downloaded and can minimize the impact on the environment. Environments that don’t block malicious traffic as one of the first steps often take longer to clean up.
The post Leveraging McAfee Endpoint Security to Protect Against Emotet and Other Malware appeared first on McAfee Blogs.
Article Link: https://securingtomorrow.mcafee.com/business/leveraging-mcafee-endpoint-security-to-protect-against-emotet-and-other-malware/