Goal: Reverse and document the latest module “network64/32Dll,” leveraged by the notorious Trickbot banking malware gang.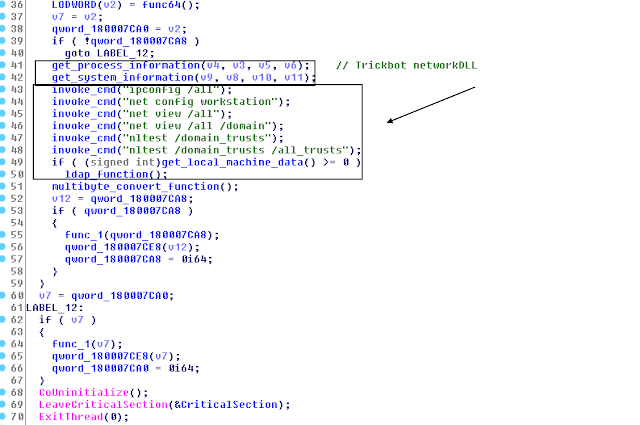
Decoded module hash “network64Dll”: aeb08b0651bc8a13dcf5e5f6c0d482f8
Decoded config in “network64Dll_configs:
<dpost>
<handler>http://85.143.209[.]180:8082</handler>
<handler>http://212.92.98[.]229:8082</handler>
</dpost>
AssessmentA few extractions from today’s trickbot 02/04/2018:gtag-tt0002https://t.co/PUQaOWa0CI - Confighttps://t.co/30Rep77aY3 - Dposthttps://t.co/T77F5kQyaf - Mailconf@executemalware @Ring0x0 @James_inthe_box @JAMESWT_MHT @VK_Intel @clucianomartins @MakFLwana @CryptoInsane pic.twitter.com/Ugr8B8bbgW— V0id_Hunt3r (@v0id_hunter) April 2, 2018
While reviewing Twitter posts related to Trickbot malware, I was alerted by a few researchers @Ring0x0 and @v0id_hunter to the new module dropped by the Trickbot gang “network64/32Dll.” This specific module appears to be one single harvester of all possible network victim information from running commands such as “ipconfig /all” and “nltest /domain_trusts /all_trusts” to WMI Query Language (WQL) queries such as “SELECT * FROM Win32_OperatingSystem” to lightweight directory access protocol (LDAP) queries. Notably, the gang leverages “nltest” commands to establish trust relationship between between a compromised workstation and its possible domain before quering LDAP. This is not the first time this gang leverages LDAP; it also developer a DomainGrabber module specifically to harvest sensitive domain controller information, as detailed earlier.
This tiny 24 KB module DLL, compiled on Friday March 30, 08:52:12 2018 UTC, is originally called “dll[.]dll.” The module itself consists of only 32 functions.
Possible Attack Methodology
The module is likely used by the gang to expand their access to victim networks possibly identifying high-value corporate domains that they can exploit further either via their “tab” module implementing its ETERNALROMANCE exploit implementation, paired with Mimikatz and/or establish deeper network persistence before they deploy additional malware.
The decoded Trickbot “network64Dll” module contains the usual Trickbot export functions:
- Control
- FreeBuffer
- Release
- Start
The module framework is as follows:
I. Network Collector Module
II. Network Communication
III. Yara rule
I. Network Collector Module
A. PROCESS LIST
A. PROCESS LIST
Collects all processes via CreatoolHelp32Snapshot iterating through running processes.
B. . SYSTEMINFO
The list of queried WMQ is based from this expression:
- SELECT * FROM Win32_OperatingSystem
C. CMD-based calls
The list of all simple command leveraged by the gang:
- ipconfig /all
- net config workstation
- net view /all
- net view /all /domain
- nltest /domain_trusts
- nltest /domain_trusts /all_trusts
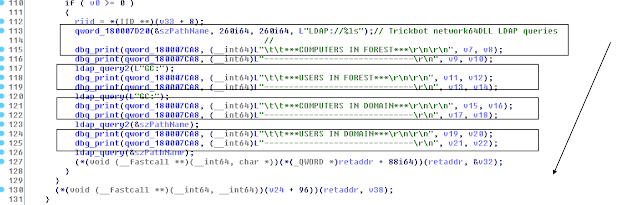
The list of some of the grouped LDAP queries:
a. LOCAL MACHINE DATA
- User name
- Computer name
- Site name
- Domain shortname
- Domain name
- Forest name
- Domain controller
- Forest trees
b. COMPUTERS IN FOREST
- Name
- Full name
- Description
- Operating System
- IP-addres
c. USERS IN FOREST
- Comment
- Description
- Name
d. COMPUTERS IN DOMAIN
- Name
- Full name
- Description
- Operating System
- IP-addres
e. USERS IN DOMAIN
- Comment
- Description
- Name
II. Network Communication
Part of the export “Control” function, the module forms and communicates to the next-layer network via the module network path ending in …/<GROUP ID>/<CLIENT ID>/90. The /90 ending is leveraged for POST requests with its content in the following three unique formats:
A. Content-Disposition: form-data; name=”proclist“
B. Content-Disposition: form-data; name=”sysinfo"
C. Content-Type: multipart/form-data; boundary=Arasfjasu7
The unique value “Arasfjasu7” appears to be a marker/separator specifically for the LDAP query collection upload to split the harvested information. Thanks to @Ring0x0 for the share.
III. YARA RULE
rule crime_trickbot_network_module_in_memory {
meta:
description = “Detects Trickbot network module in memory”
author = “@VK_Intel”
reference = “Detects unpacked Trickbot network64Dll”
date = “2018-04-02”
hash = “0df586aa0334dcbe047d24ce859d00e537fdb5e0ca41886dab27479b6fc61ba6”
strings:
$s0 = “PROCESS LIST” fullword wide
$s1 = “(&(objectCategory=computer)(userAccountControl:1.2.840.113556.1.4.803:=8192))” fullword wide
$s2 = “USERS IN DOMAIN” fullword wide
$s3 = “Operating System: %ls” fullword wide
$s4 = “<moduleconfig><autostart>yes</autostart><sys>yes</sys><needinfo name="id"/><needinfo name="ip"/><autoconf><conf ctl="SetCon” ascii
$s5 = “Content-Length: %lu” fullword wide
$s6 = “Boot Device - %ls” fullword wide
$s7 = “Serial Number - %ls” fullword wide
$s8 = “Content-Disposition: form-data; name="proclist"” fullword ascii
$s9 = “Content-Disposition: form-data; name="sysinfo"” fullword ascii
$s10 = “Product Type - Server” fullword wide
$s11 = “SYSTEMINFO” fullword wide
$s12 = “OS Version - %ls” fullword wide
$s13 = "(&(objectcategory=person)(samaccountname=))" fullword wide
$s14 = “Product Type - Domain Controller” fullword wide
condition:
uint16(0) == 0x5a4d and filesize < 70KB and 12 of ($s)
}
Article Link: http://www.vkremez.com/2018/04/lets-learn-trickbot-implements-network.html