Goal: Document presence of the new TrickBot Tor plugin server and deobfuscate the latest TrickBot Loader malware string template.
Trick Loader MD5: 6124c863c08f92732da180d4cf7cbf38
OutlineFake Danske Bank FW: Recent BACs delivers Trickbot https://t.co/1kcL0cPpoa pic.twitter.com/10kHnCuhFZ— My Online Security (@dvk01uk) July 12, 2018
I. Background
II. New Discovery: Tor Plugin Server in Config
III. TrickBot Loader Deobfuscation Walkthrough
IV. Analysis of Deobfuscated TrickBot Loader
A. Checks for the presence of the virtual machine processes and analysis DLLs
B. Injected process
C. Imported DLL
D. Command-line arguments via
cmd.exe & PowerShell -DisableRealtimeMonitoring
E. Checks for processes
F. Configuration storage
G. Directory name in %APPDATA%
H. Oddities
While analyzing one of the latest TrickBot samples from the impersonated Danske Bank sender (thanks to @dvk01uk for the sample), I decided to take a deeper dive into TrickBot Loader.
II. New Discovery: Tor Plugin Server in Config
The TrickBot crew recently implemented a plugin server communication via Tor .onion on port:448 to fetch malware modules.
It is a novel technique for TrickBot; it is likely they are experimenting with the Tor connector in order to improve and/or sustain first-layer module and proxy server resiliency. It is also possible that the Tor connector would be a new norm for the TrickBot crew to not only fetch modules but also for client-server communications similarly as it is performed in the other malware variants such as Gozi ISFB Botnet “4000”.7-11-2018: #TrickBot #banker group conf jmp+2— Vitali Kremez (@VK_Intel) July 11, 2018
1000224 -> 1000226 (skip /225)
Observation: It seems the group is experimenting with .onion nginx proxy module fetcher (–port 448) via lm3vzydqdw2orekm[.onion:448 | only via TOR
New blockist | Latest IOCs: https://t.co/AmHLEzoMTJ pic.twitter.com/h5LYbgkArv
III. TrickBot Loader Deobfuscation Walkthrough
A. Retrieve the first self-injected unpacked TrickBot payload in memory and dump as an executable and disk.
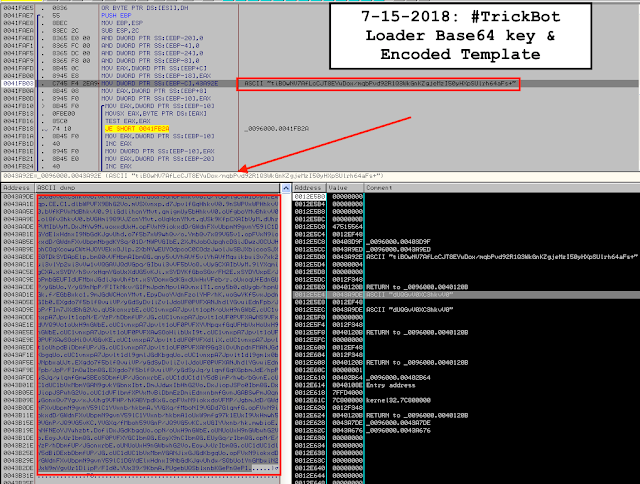
B. Locate the encoded string template in OllyDBG and set up a hardware breakpoint on access (DWORD), and run until you see the key and template execution.
C. Dump and save the encoded template ‘data’ with its ‘key’;
D. Decode the custom Base64 obfuscated string template (thanks to @sysopfb for the script) by entering the encoded template to ‘data’ and its key to ‘key’; and
import base64
data = ‘dUQGvV0XC3hkvV0\x00vKYkvV0IbVyM\x00dUQM9UN0PuhkvV0\x00q/YUqmigCXAIbVyM\x00EWqp\x00dlbWPVFX9BhG2Vo\x00mVSXvnxp\x00d7JpvlfGqHhkvV0\x009nSWPVxWPHhkvV0\x00bVfKPVxMdBhkvV0\x009liGdlihcnYMvt\x00qmigmUy5bHhkvV0\x00oUfgboYMvBhkvV0\x00olQfv3hkvV0\x00bVGHml9Q9VJZcnYMvt\x00oUqHcnYMvt\x00qUSk9KfpCXAIbVyM\x00dUhrPVMIbVyM\x00DxJNYw9N\x00uoxxdUxH\x00opFVxN9iokxdD/GWdnFXvUbpmN9gvnY59lC1DGYdElxHdnxI9NbGdKJgvUhd\x00o7f5b7xW9whQv/o\x00YmbQv7xQ9VG5v1\x00opFVxN9iokxdD/GWdnFXvUbpmNbgdKYSq/01D/NWPVGIbE\x002XJNJobOJpqhcDGiJDwzJOCUJHphCOqXcowyCWtHJOYVEkxOJlp\x002XbNYwEUYOdpcoC0COdzJwolJuSBJXbicooSJXE0TDkSYDApElp\x00bmQ0vVFHbmAIbmQG\x00qny5vUYhAVf5vlYhAVfMquikbui3v7xk2ui3vlYp2ui3vVw1vVQGAVJQdVGpq/GIbui3vVF5bVoQ\x00vUyGCXAIbVyM\x009lYXqmigCXA\x00xSYDY/hSv/xHqmYGoUxXdUG5vKJi\x00xSYDYKfGboSGv/FH2E\x00xSYDYUxpE/JpPmbGEUFIdUFMbxJGdlJgvUhfbt\x00xSYDomxGdKGxdUxHxVFeb/r\x00oUxoqUfEdnGUP/yGbUo\x00Y/yG9nNpP/FITkNkv/GIPmJpdnNpvlAQvnxlT1\x00cny5b0\x00qUygb/hpmUGk\x00f/EGbBxkc1\x009mJGdWCHcnYMvt\x00EpyDuoYVdnFzolYHP/hK\x00uoGwYKf5vxJpdnGIb0\x00EXgdo7f5blfQvuiVP/yGdSyDvliZvlJdoUF0PVFXANJhdlYGvuiEdnFpb/JpP/FIm7JXdBhG2Vo\x00qUSkcnxrbE\x00cUC1vnxpA7Jpvlt1opN/oUxH9nGWbE\x00cUC1vnxpA7Jpvlt1opN/E/YzP/hDbmfUP/JG\x00cUC1vnxpA7Jpvlt1oUF0PVFXAwNS9VFxdVYQ9Vo1oUxH9nGWbE\x00cUC1vnxpA7Jpvlt1oUF0PVFXYVNpqxfGqUFHbVxHoUxH9nGWbE\x00cUC1vnxpA7Jpvlt1oUF0PVFXAwSOoHiibUxI9t\x00cUC1vnxpA7Jpvlt1oUF0PVFXAwSOoHiOvVGGvKE\x00cUC1vnxpA7Jpvlt1dUF0PVFXdliX\x00cUC1vnxpA7Jpvlt1oUhpdBiDbmfUP/JG\x00cUC1vnxpA7Jpvlt1oUF0PVFXAN9Gq3iOvUhpdnFMANJGdKbgqUo\x00cUC1vnxpA7Jpvlt1dl9gmlJGdKbgqUo\x00cUC1vnxpA7Jpvlt1dl9gmlx0bVNpbxaUJt\x00EXgdo7f5blfQvuiVP/yGdSyDvliZvlJdoUF0PVFXANJhdlYGvuiEdnFpb/JpP/FImOwIbmQG\x00EXgdo7f5blfQvuiVP/yGdSyJq/ylqmfGqKGpbmJdE/hpPuSJq/ylqmfGmwSBEoSDbmfUP/JGcnxrbE\x00cUC1dUC1dlY5dBimP/hwb/bGvnE\x00cUC1dUC1bVxMbmYGAN9gvkYGbnxIbt\x00DmJJdwxIbHhG2Vo\x00DxJiopJSPo0IbmQG\x00DxJiopJSPuhG2Vo\x00cUC1dVFlbmfXPVxMvBiDbmEzDmiEdnxnbmfGvnJGABSwPmJQqnyGonxQv7Ygv/xJvUhg9VFHP/hKABYpdKxG\x00opFVxN9iokxdoVFMP/JgbmJdD/GWdnFXvUbpmN9gvnY59lC1YVxnb/hkbmA\x00YVGXq/fMboNI9VGDd7GlqmfG\x00opFVxN9iokxdD/GWdnFXvUbpmN9gvnY59lC1YVxnb/hkbmA1oUxW9mfg97k1EUxI9VxHmwh59VGnP/JQ9VG5vKC\x00YVGXq/fMboh59VGnP/JQ9VG5vKC\x00xUGIYVxnb/hk\x00mwbioE\x00mNfNEoYJYuhzbt\x00DofiDxJGdKbgqUo\x00opN/oUxH9nGWbE\x00oUNUoUxH9nGWbuhG2Vo\x00EoyJvUrIbmQG\x00oUF0PVFXYGCIbmQG\x00EoyX9nCIbmQG\x00EUyGq/rIbmQG\x00opN/E/YzP/hDbmfUP/JGcnxrbE\x00oUNUoUxH9nGWbuhG2Vo\x00EoyJvUrIbmQG\x00cUC1dUC1dlY5dBiDExbDbmfUP/JG\x00cUC1dUC1bVxMbmYGANJixGJGdKbgqUo\x00opFVxN9iokxdD/GWdnFXvUbpmN9gvnY59lC1DGYdElxHdnxI9NbGdKJgvUhdu/SQbUo1YnGMbuiN2VxW9mYgvUr1DlipP/FId0\x00YVx39/9KbmA\x00PUgebUQSblxnbKGePnQeP1\x00’
key = ‘tiBOwNV7AfLcCJT8EYuDox/mqbPvd92R1Q3WkGnKZgjeMzI50yHXpSUlrh64aFs+’
std_b64 = “ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/”
for s in data.split(‘\x00’):
s = s.translate(str.maketrans(key,std_b64))
if len(s)%4 != 0:
s += ‘=’*(4 - len(s)%4)
print(base64.b64decode(s))
b’shell32.dll’
b’ntdll.dll’
b’shlwapi.dll’
b’advapi32.dll’
b’B64’
b’svchost.exe’
b’\msnet’
b’pstorec.dll’
b’vmcheck.dll’
b’dbghelp.dll’
b’wpespy.dll’
b’api_log.dll’
b’SbieDll.dll’
b’SxIn.dll’
b’dir_watch.dll’
b’Sf2.dll’
b’cmdvrt32.dll’
b’snxhk.dll’
b’MSEDGE’
b’IEUser’
b’SOFTWARE\Microsoft\Windows NT\CurrentVersion\‘
b’ProductName’
b’Evaluation’
b’SOFTWARE\Microsoft\Virtual Machine’
b’{3E5FC7F9-9A51-4367-9063-A120244FBEC7}‘
b’{6EDD6D74-C007-4E75-B76A-E5740995E24C}‘
b’explorer.exe’
b’bloody booty bla de bludy botty bla lhe capitaine bloode!‘
b’ole32.dll’
b’wtsapi32’
b’WTSEnumerateSessionsA’
b’WTSFreeMemory’
b’WTSGetActiveConsoleSessionId’
b’WTSQueryUserToken’
b’SeTcbPrivilege’
b’Elevation:Administrator!new:‘
b’.log’
b’client_id’
b’%d%d%d.‘
b’user32.dll’
b’CLSIDFromString’
b’IIDFromString’
b’C:\Program Files\Sophos\Sophos System Protection\ssp.exe’
b’cmd.exe’
b’/c net stop SAVService’
b’/c net stop SAVAdminService’
b’/c net stop Sophos AutoUpdate Service’
b’/c net stop SophosDataRecorderService’
b’/c net stop Sophos MCS Agent’
b’/c net stop Sophos MCS Client’
b’/c net stop sophossps’
b’/c net stop Sntp Service’
b’/c net stop Sophos Web Control Service’
b’/c net stop swi_service’
b’/c net stop swi_update_64’
b’C:\Program Files\Sophos\Sophos System Protection\1.exe’
b’C:\Program Files\Malwarebytes\Anti-Malware\MBAMService.exe’
b’/c sc stop WinDefend’
b’/c sc delete WinDefend’
b’MsMpEng.exe’
b’MSASCuiL.exe’
b’MSASCui.exe’
b’/c powershell Set-MpPreference -DisableRealtimeMonitoring $true’
b’SOFTWARE\Policies\Microsoft\Windows Defender’
b’DisableAntiSpyware’
b’SOFTWARE\Microsoft\Windows Defender Security Center\Notifications’
b’DisableNotifications’
b’WinDefend’
b’\FAQ’
b’\README.md’
b’MBAMService’
b’SAVService’
b’SavService.exe’
b’ALMon.exe’
b’SophosFS.exe’
b’ALsvc.exe’
b’Clean.exe’
b’SAVAdminService.exe’
b’SavService.exe’
b’ALMon.exe’
b’/c sc stop SAVService’
b’/c sc delete SAVService’
b’SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options’
b’Debugger’
b’kjkghuguffykjhkj’
The TrickBot Loader contains various logic targeting and “relaxing” various security measures on the host machine including stopping a plethora of Sophos and Windows Defender anti-virus services. Additionally, TrickBot Loader executes a Powershell script disabling real-time monitoring via “powershell Set-MpPreference -DisableRealtimeMonitoring $true”. Based on the analysis of the Loader, the crew is primarily concerned about Sophos, Windows Defender, and MalwareBytes anti-virus engines. Currently, this Loader installs itself and creates a directory “msnet” in $APPDATA$.
The oddities of the TrickBot loader include ever-present string ‘bloody booty bla de bludy botty bla lhe capitaine bloode!’ as well as a random ‘kjkghuguffykjhkj’ ones.
It is notable that the group consistently improves its loader since its rather crude GetModuleHandle anti-analysis DLL check implementation in late 2017.
A. Checks for the presence of the virtual machine processes and analysis DLL;
b’pstorec.dll’
b’vmcheck.dll’
b’dbghelp.dll’
b’wpespy.dll’
b’api_log.dll’
b’SbieDll.dll’
b’SxIn.dll’
b’dir_watch.dll’
b’Sf2.dll’
b’cmdvrt32.dll’
b’snxhk.dll
B. Injected process;
b’svchost.exe’
C. Imported DLLs;
b’shell32.dll’
b’ntdll.dll’
b’shlwapi.dll’
b’advapi32.dll’
b’ole32.dll’
b’user32.dll’
D. Command-line arguments via cmd.exe;
/c powershell Set-MpPreference -DisableRealtimeMonitoring $true’
b’/c net stop SAVService’
b’/c net stop SAVAdminService’
b’/c net stop Sophos AutoUpdate Service’
b’/c net stop SophosDataRecorderService’
b’/c net stop Sophos MCS Agent’
b’/c net stop Sophos MCS Client’
b’/c net stop sophossps’
b’/c net stop Sntp Service’
b’/c net stop Sophos Web Control Service’
b’/c net stop swi_service’
b’/c net stop swi_update_64’
b’/c sc stop SAVService’
b’/c sc delete SAVService’
E. Checks for processes and services;
b’MBAMService’
b’SAVService’
b’SavService.exe’
b’ALMon.exe’
b’SophosFS.exe’
b’ALsvc.exe’
b’Clean.exe’
b’SAVAdminService.exe’
b’SavService.exe’
b’ALMon.exe’
b’MsMpEng.exe’
b’MSASCuiL.exe’
b’MSASCui.exe’
b’C:\Program Files\Sophos\Sophos System Protection\1.exe’
b’C:\Program Files\Malwarebytes\Anti-Malware\MBAMService.exe’
b’C:\Program Files\Sophos\Sophos System Protection\ssp.exe’
b’\FAQ’
b’\README.md’
b’\msnet’
b’bloody booty bla de bludy botty bla lhe capitaine bloode!‘
b’kjkghuguffykjhkj’
Article Link: http://www.vkremez.com/2018/07/lets-learn-trickbot-new-tor-plugin.html