We are thrilled to announce an exciting enhancement to Intezer’s Autonomous SOC solution: the automated execution of our Endpoint Scanner as part of the alert triage process. Making memory analysis and advanced endpoint forensics easily accessible to security teams of all skill levels, our solution empowers organizations to enhance their security operations and incident response to unprecedented levels.
Automated Endpoint Scanning: Streamlining Alert Triage with Intezer
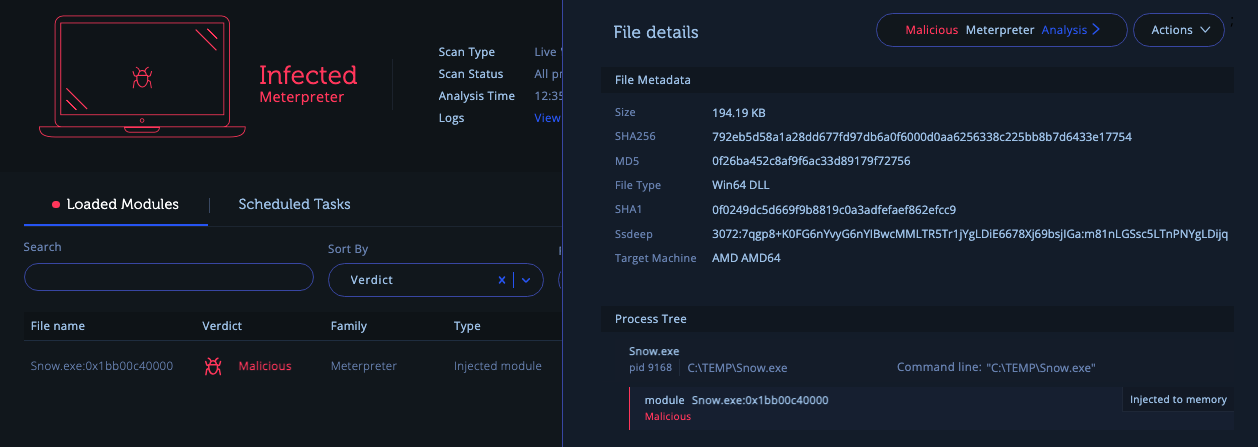
In the realm of cybersecurity, efficient alert triage is crucial to identify and prioritize potential risks. Intezer’s endpoint scan will perform a live memory that will find any traces of advanced in-memory threats such as malicious code injections, packed and fileless malware, or any unrecognized code. Organizations can now benefit from the following unique process:
Smart Triage Optimization: Intezer’s automated triage process intelligently analyzes incoming alerts, determining whether an endpoint scan is required. For example: Suspicious behavior, code injection or exploitation attempt alerts. By focusing solely on relevant alerts based on their type and attributes, unnecessary resource usage is minimized.
Seamless Integration: Leveraging the API provided by the Endpoint Detection and Response (EDR) vendor, Intezer seamlessly integrates with the existing infrastructure. This integration enables the automated execution of scanning operations, eliminating the need for manual intervention.
Automated Endpoint Scan: Intezer’s Endpoint Scanner is initiating a comprehensive scan of the targeted endpoint. This powerful forensic tool specializes in detecting advanced threats within the memory, including malicious code injections, packed and fileless malware, and unidentified code.
 Learn more about Live Endpoint Analysis
Learn more about Live Endpoint Analysis
Efficient Data Collection: During the scanning process, Intezer’s Endpoint Scanner collects an array of relevant information from the endpoint. This includes executables, memory modules, shellcodes, and other valuable forensic data. By examining these data points, Intezer distinguishes between benign software, generic malware, and sophisticated threat actors.
The Benefits of Automated Endpoint Scanning
Automating the endpoint scanning process offers several significant advantages for organizations:
Improved Efficiency: By seamlessly integrating automated scanning into the triage workflow, organizations can save valuable time and resources. This streamlines the overall alert handling process, allowing security teams to focus their efforts on investigating and mitigating real threats.
Enhanced Threat Detection: The automated execution of Intezer’s Endpoint Scanner ensures a consistent and comprehensive approach to detecting advanced in-memory threats. By leveraging the scanner’s powerful forensic capabilities, organizations can effectively identify and mitigate potential risks before they escalate. Additionally, this advanced scanning capability enables security teams to cover triage and response for alerts that are fileless or behavior-based.
Bridging skill gaps: Intezer provides security teams of all skill levels with access to all types of analysis, such as memory analysis and endpoint forensics. This ensures that regardless of the team’s expertise, they can leverage advanced techniques to analyze memory and investigate endpoints for potential threats.
Intezer’s Advanced Evidence Collection: Going Beyond Sandboxing
While sandboxing has traditionally been a go-to method for analyzing suspicious activities, it’s important to recognize its limitations in today’s complex threat landscape. Simply sending evidence collected by the Endpoint Detection and Response (EDR) system to a sandbox solution may not provide the comprehensive insights needed to identify sophisticated threats. That’s where Intezer’s advanced evidence collection capabilities come into play.
Looking Beyond Structured Fields: The evidence collected by the EDR system is typically structured and focuses on known indicators of compromise. However, sophisticated attackers often employ advanced techniques that go unnoticed in structured fields. Intezer takes a different approach by analyzing unstructured fields, such as the command line, where relevant evidence might be hidden. By examining these unstructured fields, our solution uncovers critical details that may be crucial in detecting malicious activities.
Unleashing the Power of Live Endpoint Scans: Many threats today involve in-memory and fileless techniques, which can evade traditional detection methods. Intezer understands the importance of thoroughly examining these areas, which is why we incorporate live endpoint scans into our automated triage process. By performing real-time scans of endpoints, we can uncover hidden in-memory and fileless threats that may otherwise go undetected.
Easy to set up
We have streamlined a simple and transparent setup process, ensuring it’s a one-time task, saving you precious time and resources. Once set up in your environment, Intezer will scan and analyze endpoints when needed, granting you peace of mind and confidence in your cybersecurity defenses.
Learn more about the setup process (Crowdstrike, SentinelOne and Microsoft Defender for Endpoint).
Take Your Alert Triage to the Next Level with Intezer’s Automated Endpoint Scanning
With the introduction of automated endpoint scanning, Intezer continues to empower organizations. By seamlessly integrating memory analysis and endpoint forensics into the alert triage process, we provide a streamlined and efficient approach to security operations. To learn more about how Intezer’s automated endpoint scanning can enhance your organization’s security posture, read the documentation or reach out to our team today.
The post 🚀 Launching Automated Endpoint Scanning: Advanced Triage for Fileless Threats appeared first on Intezer.
Article Link: Automated Endpoint Scanning Advanced Triage for Fileless Threats
