The UNC4841 group, linked to China, is targeting Barracuda Email Security Gateway (ESG) appliances again, exploiting a new zero-day vulnerability identified as CVE-2023-7102.
Investigations revealed that attackers, using specially crafted Excel files attached to emails, targeted a limited number of Barracuda ESG devices to deploy new variants of SeaSpy and SaltWater malware.
It is important to note that there is a publicly available Proof-of-Concept (PoC) exploit for this vulnerability, raising concerns about potential widespread impact.
Background of UNC4841 Attacks Targeting Barracuda ESG
It was revealed in May 2023 that UNC4841 exploited a Barracuda ESG zero-day, tracked as CVE-2023-2868, as part of an extensive cyberespionage campaign ongoing since at least October 2022. The campaign, impacting organizations across 16 countries and various industries, involved malware delivery and data theft.
In June, Mandiant confidently attributed these attacks to UNC4841, a conclusion echoed by CISA, which issued a warning about the espionage campaign.
In the course of these attacks, hackers leveraged CVE-2023-2868 to gain initial access to Barracuda appliances by sending specially crafted emails to the targeted organizations. Subsequently, they deployed custom backdoors named SeaSpy, SaltWater, SeaSide, and Whirlpool, a rootkit named SandBar, and trojanized Barracuda modules.
Despite the availability of a patch for the vulnerability, attackers persisted in maintaining a presence on compromised systems. This ongoing threat prompted Barracuda to advise affected customers to replace infected systems to ensure security.
How Do Attackers Exploit the New Zero-Day? (CVE-2023-7102)
The new zero-day vulnerability, CVE-2023-7102, stems from the use of the third-party Perl module “Spreadsheet ParseExcel.”
 Vulnerability card for CVE-2023-7102 (SOCRadar Vulnerability Intelligence)
Vulnerability card for CVE-2023-7102 (SOCRadar Vulnerability Intelligence)
The module is employed by the Amavis virus scanner in Barracuda ESG devices for parsing Microsoft Excel files. The issue arises from the susceptibility of Spreadsheet ParseExcel to another vulnerability, which involves arbitrary code execution, identified as CVE-2023-7101, due to passing unvalidated input from a file into an evaluating string-type.
Upon the reception of a malicious Excel file, a remote attacker can run arbitrary code on a vulnerable Barracuda ESG appliance.
Barracuda recently deployed a patch to address compromised ESG appliances and reassured customers that no immediate action was required on their part as the investigation is ongoing. However, the vendor notes that there is no patch available for the vulnerability in the open-source Spreadsheet ParseExcel library, CVE-2023-7101. Barracuda recommends organizations utilizing the specific library in their products or services to promptly implement necessary remediation measures.
Visit Barracuda’s advisory for more information and new indicators of compromise (IoCs) associated with the malware variants deployed by UNC4841.
SOCRadar tracks the activities of threat actors and malware, offering pertinent information on its extensive XTI platform. You can access updates related to specific malware and threat actors through the Threat Actor/Malware tab within the Cyber Threat Intelligence module.
 SeaSpy Malware on SOCRadar platform
SeaSpy Malware on SOCRadar platform
Zero-Day Vulnerability in Apache OFBiz Could Lead to Authentication Bypass: CVE-2023-51467
Another recently discovered zero-day vulnerability, CVE-2023-51467, affects Apache OFBiz. Apache OFBiz is an open-source Enterprise Resource Planning (ERP) system that includes a collection of enterprise applications for automating business processes.
 Vulnerability card for CVE-2023-51467 (SOCRadar Vulnerability Intelligence)
Vulnerability card for CVE-2023-51467 (SOCRadar Vulnerability Intelligence)
CVE-2023-51467 resides in the login functionality and presents an avenue for attackers to bypass authentication protections, ultimately enabling a Server-Side Request Forgery (SSRF) attack.
Importantly, CVE-2023-51467 arose due to an incomplete patch; SonicWall reports that the security measures implemented to address a critical vulnerability, CVE-2023-49070, inadvertently left the root issue unresolved. CVE-2023-49070, on the other hand, represents a pre-authenticated Remote Code Execution (RCE) vulnerability, stemming from a deprecated XML-RPC component within Apache OFBiz. Successful exploitation of CVE-2023-49070 could grant threat actors full control over the server, enabling them to extract sensitive data.
Exploitation of the CVE-2023-51467 Vulnerability in Apache OFBiz
Researchers have successfully developed two test cases exploiting the CVE-2023-51467 vulnerability, involving either keeping the USERNAME and PASSWORD parameters in an HTTP request empty or using known invalid values. These test cases reveal that the presence of a certain string (requirePasswordChange=Y) allows for authentication bypass.
- In the first scenario, the USERNAME and PASSWORD parameters are intentionally left empty, with the inclusion of requirePasswordChange=Y in the URI. When passed through the login function, the system returns requirePasswordChange due to the empty username and password. Unexpectedly, the flow does not enter the conditional block despite both parameters being empty. Consequently, the checkLogin function returns success, facilitating the authentication bypass.
- In the second test case, known invalid values are assigned to the parameters, while requirePasswordChange=Y is retained in the URI. Similar to the first case, the login function returns requirePasswordChange. Again, the flow does not enter the conditional block, leading to authentication bypass.
To safeguard against potential threats, it is advised to promptly update to Apache OFBiz version 18.12.11 or later. This swift action will help mitigate the risks posed by CVE-2023-51467 and enhance the overall security posture of the system.
Patch Management Made Easy with SOCRadar
SOCRadar’s Vulnerability Intelligence offers insights into hacker trends and detailed information on vulnerabilities, providing the latest updates, mentions, exploitation activity, and available exploits. You can easily access updates about specific vulnerabilities and receive alerts by subscribing to CVEs through the module.
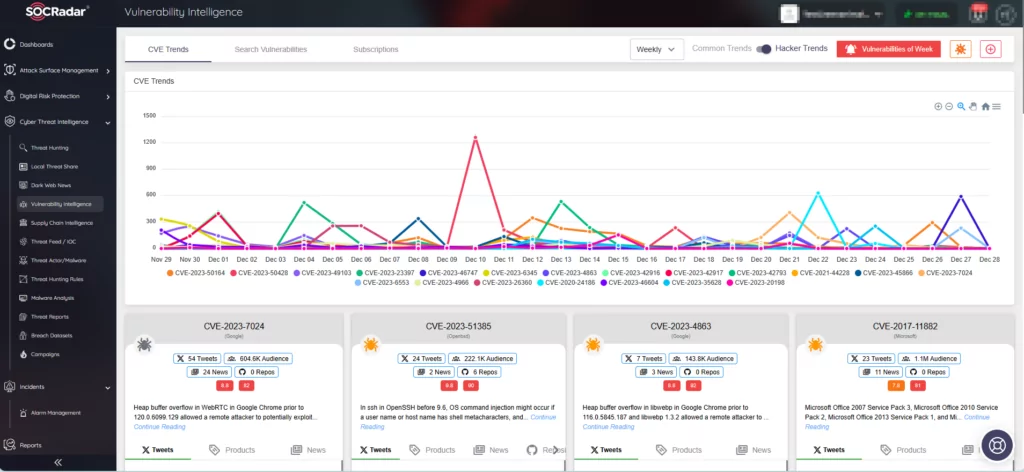 SOCRadar Vulnerability Intelligence
SOCRadar Vulnerability Intelligence
Additionally, the SOCRadar Attack Surface Management (ASM) module assists in identifying your digital assets and alerts you to emerging security issues and vulnerabilities. The platform enhances security measures and patch management by delivering actionable insights.
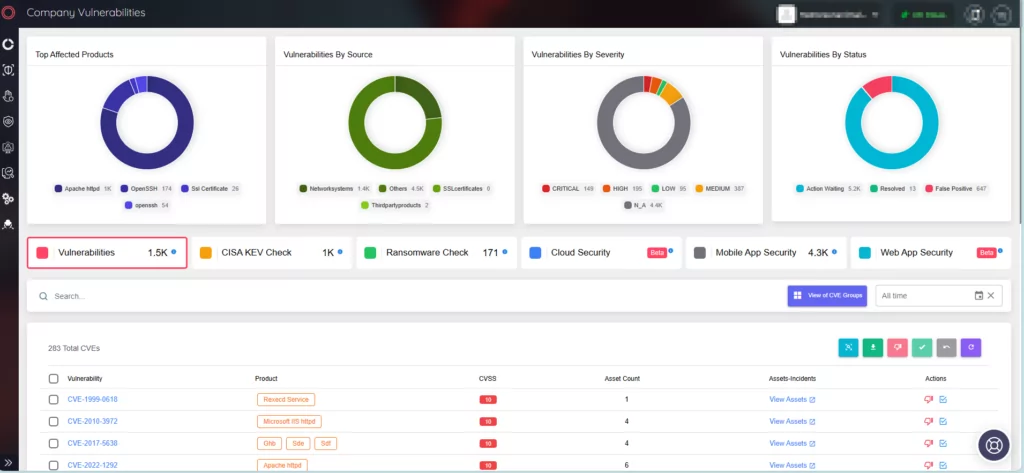 SOCRadar Attack Surface Management
SOCRadar Attack Surface Management
Sign up for a free edition of the SOCRadar platform to gain more knowledge and stay updated on the latest vulnerabilities.
The post Latest Zero-Day Vulnerabilities: UNC4841 Targets Barracuda ESG with CVE-2023-7102, Apache OFBiz Authentication Bypass (CVE-2023-51467) appeared first on SOCRadar® Cyber Intelligence Inc..
