Kubernetes has emerged as the preferred platform for deploying and managing containerized applications in contemporary IT environments. As its adoption in production settings grows, ensuring the security of the cluster against potential threats becomes critically important. One of the most effective strategies for monitoring and detecting malicious activities within a Kubernetes cluster is through threat hunting utilizing API Server Audit Logs.
Introduction to Malware Binary Triage (IMBT) Course
Looking to level up your skills? Get 10% off using coupon code: MWNEWS10 for any flavor.
Enroll Now and Save 10%: Coupon Code MWNEWS10
Note: Affiliate link – your enrollment helps support this platform at no extra cost to you.
Audit logs offer a wealth of information, empowering security teams to identify and investigate suspicious activities. By providing a comprehensive history of interactions with the Kubernetes API server, these logs are essential tools for security teams to trace malicious actions, misconfigurations, and unauthorized access. This blog article will explore the significance of Kubernetes API Server Audit Logs in threat hunting, guide you on how to interpret them, and outline best practices for leveraging them to identify potential security threats.

Go To Section
Tags
Market Adoption and Trends
According to the 2021 CNCF Annual Survey, Kubernetes has transitioned from an emerging technology to a widely accepted global tool, with 66% of potential or current users deploying it in production and 18% actively assessing its implementation in 2023. This is an increase from 58% in 2021, highlighting Kubernetes' growing significance across industries as a fundamental asset for managing containerized applications.
The Red Hat Kubernetes Adoption, Security, and Market Trends Report 2024 reveals that 53% of respondents experienced project delays due to security or compliance issues related to Kubernetes, and 46% faced revenue loss or customer attrition from security incidents. Additionally, 26% reported employee terminations due to security breaches, and 30% were fined. Nearly 89% of organizations experienced at least one security incident involving containers or Kubernetes in the past year, emphasizing the urgent need for robust security measures.
Concerns regarding security challenges in Kubernetes environments are prevalent, with 60% of respondents expressing worries about vulnerabilities, misconfigurations, and exposures. Specifically, 33% reported anxiety over vulnerabilities, while 27% were concerned about misconfigurations that could lead to security risks.
Recent Kubernetes breaches and vulnerabilities
The Tesla Cloud Breach is recognized as one of the most significant Kubernetes breaches in history. In this incident, Tesla's Kubernetes console was compromised due to the lack of password protection. Attackers installed crypto-mining software, which was cleverly configured to utilize minimal CPU resources to avoid detection. They also implemented their own CPU throttling and concealed the mining pool behind CloudFlare to obscure the associated traffic. This sophisticated attack highlights how even prominent technology companies can be vulnerable to fundamental misconfigurations.
Furthermore, Shopify's bug bounty program uncovered a critical container escape vulnerability. This flaw allowed an attacker to potentially escape from a Kubernetes pod and gain access to the underlying host system. Fortunately, it was detected prior to any exploitation, underscoring the serious risks posed by container escape vulnerabilities, which could lead to a complete compromise of the cluster.
In early 2025, researchers from Wiz identified a vulnerability known as IngressNightmare, which received an alarming score of 9.8 on the CVSS v3.1 base score. This vulnerability enables attackers to execute unauthenticated remote code execution (RCE) on clusters by exploiting the admission controller component of the Ingress NGINX Controller for Kubernetes. According to Wiz's analysis, approximately 43% of cloud environments are vulnerable to such threats, with over 6,500 clusters—including those belonging to Fortune 500 companies—publicly exposing vulnerable Kubernetes ingress controllers’ admission controllers to the internet, thereby placing them at immediate critical risk.
What are Kubernetes Audit Logs?
Kubernetes Audit Logs are crucial for monitoring requests directed to the Kubernetes API server, offering comprehensive insights into activities within the cluster. They play a significant role in security monitoring, compliance, forensics, and troubleshooting.
The Kubernetes API facilitates interaction between users and components with the cluster's state via a robust HTTP API. The API Server serves as the central control point, rendering it a potential target for adversaries. If compromised, attackers can:
- Deploy malicious workloads or modify configurations.
- Disrupt services by altering or deleting critical resources.
- Gain unauthorized access to sensitive information, thereby jeopardizing data security.
- Result in substantial revenue loss, reputational damage, and business continuity challenges due to service disruptions.
Why Should We Monitor K8s Audit Logs?
- Security Monitoring: Audit logs meticulously track user and system activities, enabling the identification of unauthorized access or potential security threats, such as attempts to delete critical resources or escalate privileges.
- Compliance and Forensics: These logs create an essential trail for regulatory compliance (e.g., HIPAA, GDPR) and serve as vital evidence for forensic analysis in the event of a security breach.
- Troubleshooting and Debugging: Audit logs assist administrators in understanding the flow of requests and pinpointing issues, particularly when actions fail to execute as intended.
- Access Control: They provide visibility into which users or service accounts interact with Kubernetes resources, facilitating the refinement of access control policies.
- Accountability and Transparency: Audit logs maintain a historical record of all actions, fostering accountability within the organization by clearly documenting who performed each action and when.
- Detecting Misconfigurations: These logs are instrumental in identifying misconfigurations or changes that could introduce vulnerabilities, allowing for timely corrective measures.
- Change Tracking: Audit logs help monitor changes to Kubernetes resources, such as updates to deployments or modifications to network policies, which is crucial for understanding the evolving state of the cluster.
- Automated Security Alerts: They can be integrated with monitoring and alerting systems to automatically detect suspicious activities and generate security alerts.
- Risk Management: By capturing all actions within the cluster, audit logs empower organizations to assess and mitigate risks, ensuring adherence to proper user behavior and security practices.
In addition to the aforementioned points, monitoring K8s audit logs can significantly enhance the overall operational efficiency of a Kubernetes environment. By analyzing these logs, organizations can identify patterns and trends in resource usage, which can inform capacity planning and resource allocation strategies. This proactive approach not only aids in optimizing performance but also contributes to reducing costs associated with over-provisioning resources. Furthermore, regular audits of these logs can lead to improved incident response times, as teams can swiftly pinpoint the source of issues and implement corrective actions. Overall, the comprehensive monitoring of audit logs is a critical component of maintaining a secure, compliant, and efficient Kubernetes infrastructure.
What does an audit log look like?
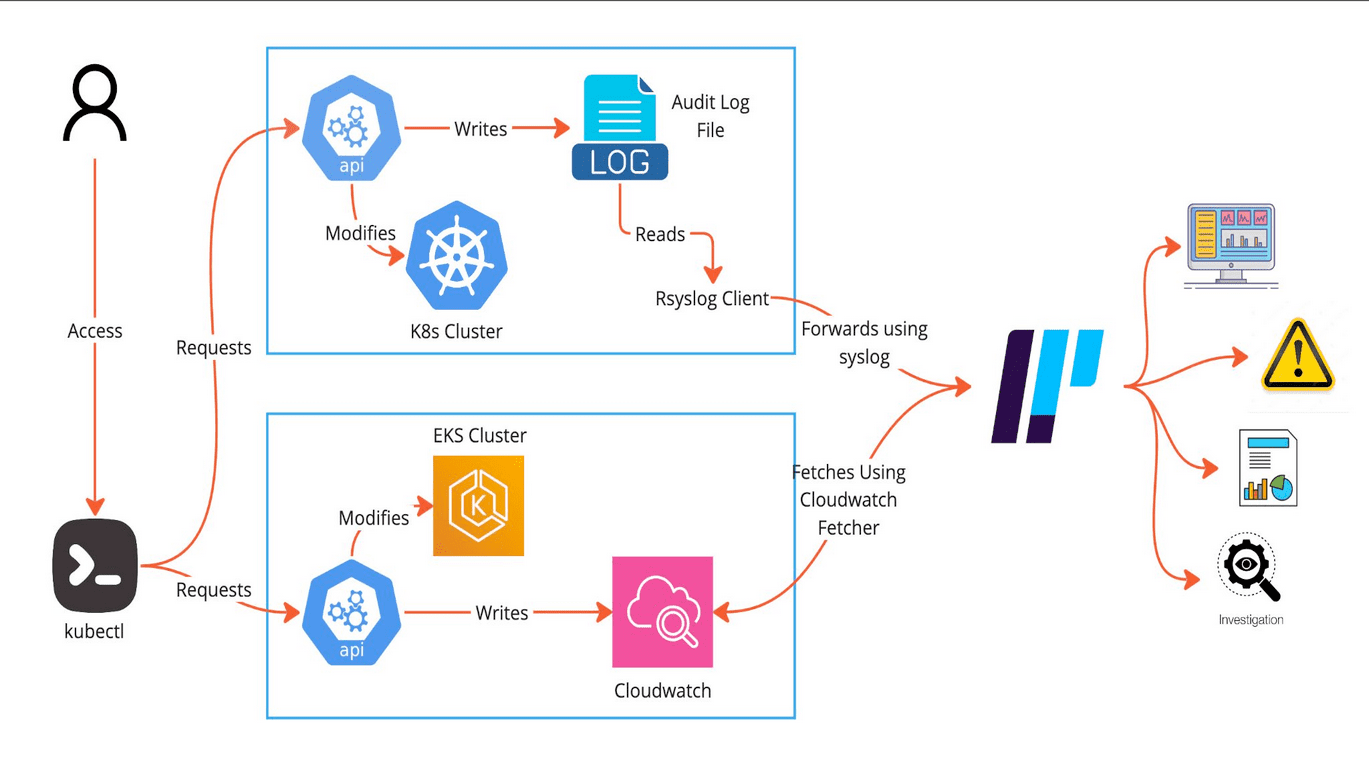
We are employing a Kubernetes Local Cluster to generate logs that are recorded in a file and retrieved through Rsyslog. Furthermore, we are collecting EKS Audit Logs, which are stored in CloudWatch and accessed via the CloudWatch Fetcher. Below is our architecture that illustrates the process of onboarding logs into Logpoint.
The log is represented in json format as :
Threat Matrix of K8s Infrastructure
The Threat Matrix for Kubernetes (K8s) Infrastructure shown below, released by the Microsoft, outlines potential threats and vulnerabilities in Kubernetes environments. As Kubernetes is increasingly adopted for its scalability and flexibility, understanding its security landscape is essential. The framework categorizes tactics and techniques that adversaries may use to exploit these environments, aiding security professionals in identifying and mitigating risks. This matrix is a valuable resource for security teams to assess their Kubernetes deployments, implement security measures, and enhance their overall security posture against potential threats.

Let's dive into a practical approach for threat hunting utilizing Kubernetes API Audit Logs:
Initial Access
| Mitre ATT&CK Technique Name | External Remote Service |
|---|---|
| Mitre ATT&CK Technique ID | T1133 |
Hypothesis
In this scenario, we assume that the attacker lacks prior knowledge of the Kubernetes clusters but successfully identifies the K8s API Endpoint through various methods. Once the API Endpoint is located, the attacker endeavors to infiltrate the cluster by gathering information about both the cluster and its resources.
To accomplish this, the attacker may employ several tactics, such as brute-forcing to uncover legitimate resources and users or attempting to circumvent the API Server's authentication mechanisms. Furthermore, the attacker might obfuscate their IP addresses and User Agents while experimenting with different combinations of request verbs to execute anonymous requests. By analyzing the response status codes from the K8s API Server, they can further identify resources within the cluster.
K8s User Agents Requests
Identifying User Agents that make requests to the K8s API Server is a critical initial step in threat hunting for API audit logs. For example, User Agents such as curl may suggest potential attacker requests, as they can be employed to conduct unauthorized inquiries aimed at gathering information regarding resources within K8s clusters. Understanding these patterns is essential for enhancing security measures and mitigating risks associated with API access.
The query shows us the top 10 user agents making requests to API Server.
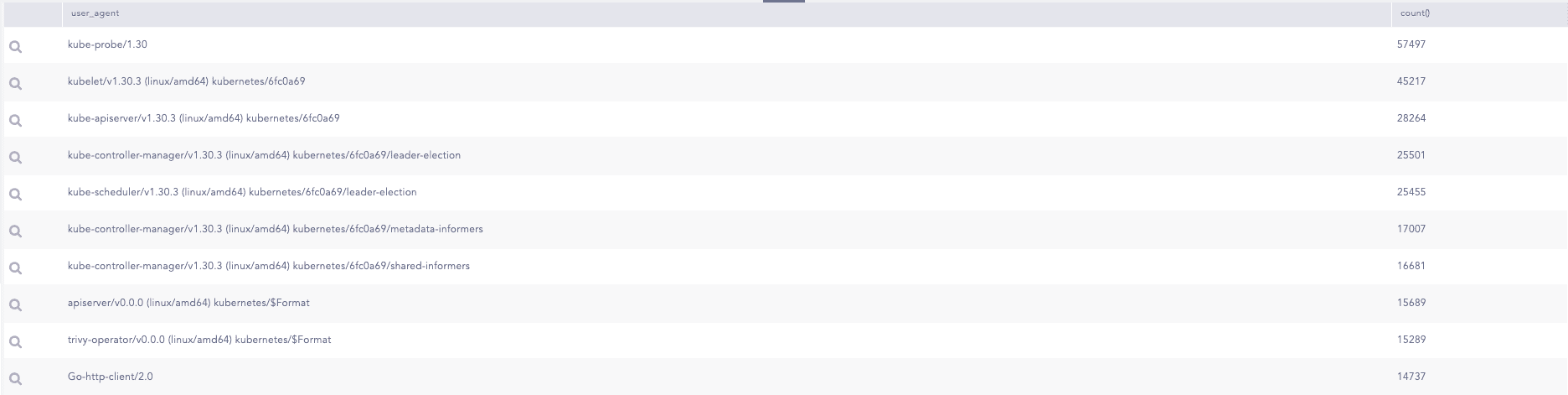
K8s API Request Status Code
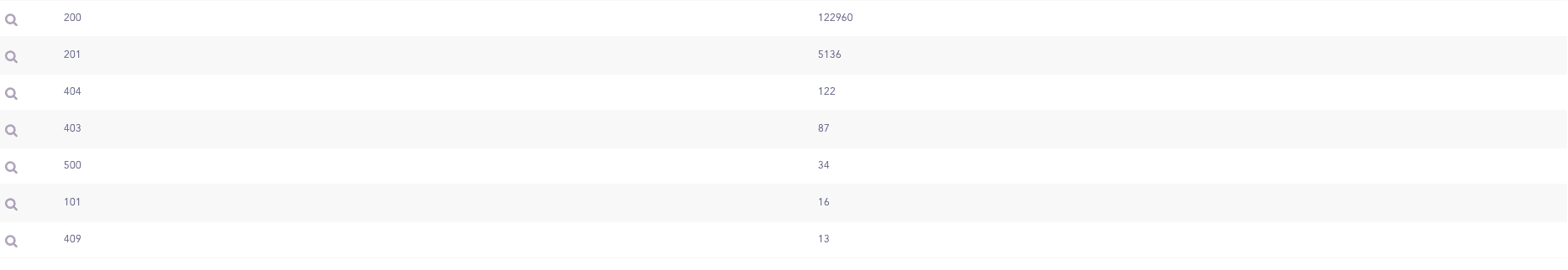
Status codes are crucial indicators of the success or failure of requests sent to and responses received from the API server. They play a significant role in identifying potential threats within API requests. For instance, a high volume of 404 responses may suggest that a user is attempting a brute-force attack to gather information about resources within the cluster. Conversely, a substantial number of 403 responses could indicate that a user is trying to access restricted resources within the cluster.
By analyzing these status codes, we can gain insights into the number of requests and responses handled by the API server, allowing for better threat detection and response management.
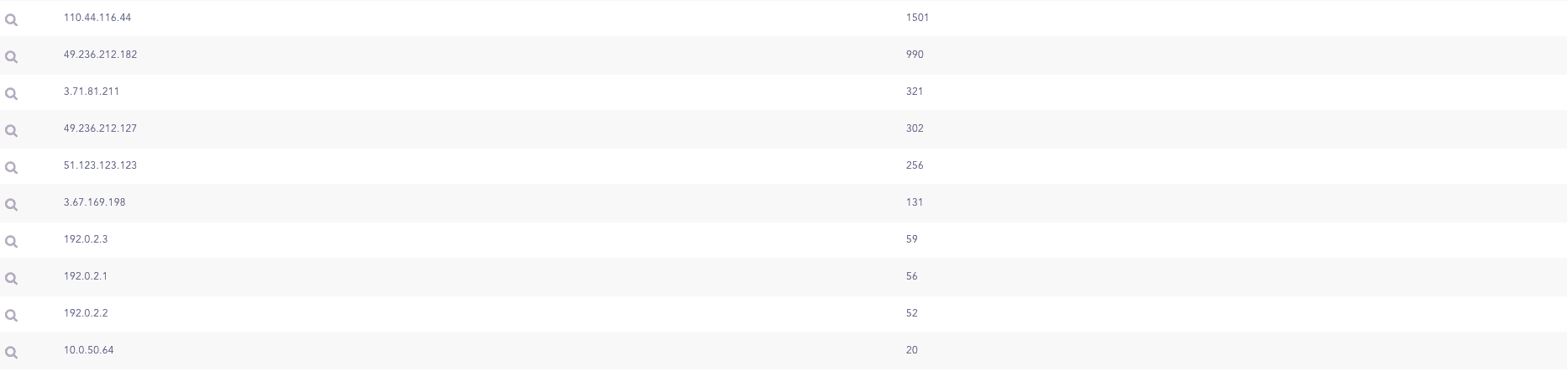
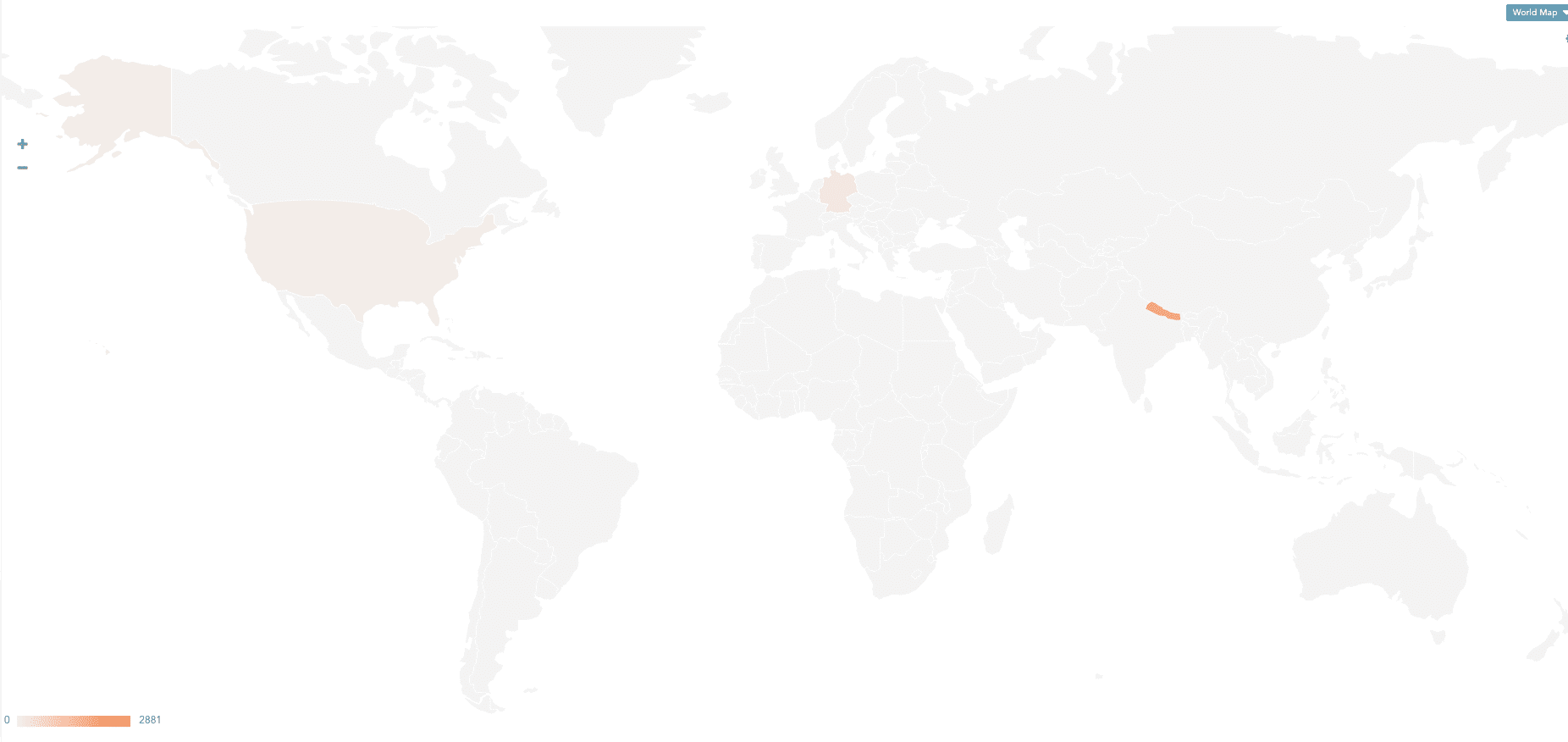
K8s API Request Source IPs
Source IPs in Kubernetes (K8s) audit logs represent the IP addresses of machines making requests to the API Server. These source IPs are essential for monitoring user requests based on their geographical locations. For instance, a request originating from an atypical IP address may indicate a potential threat attempting to access the K8s API Server and gather sensitive information about the cluster.
The following query illustrates the source IPs of machines making requests to the API Server.
Additionally, we can map source IP addresses using geolocation to display the machine's location by country.
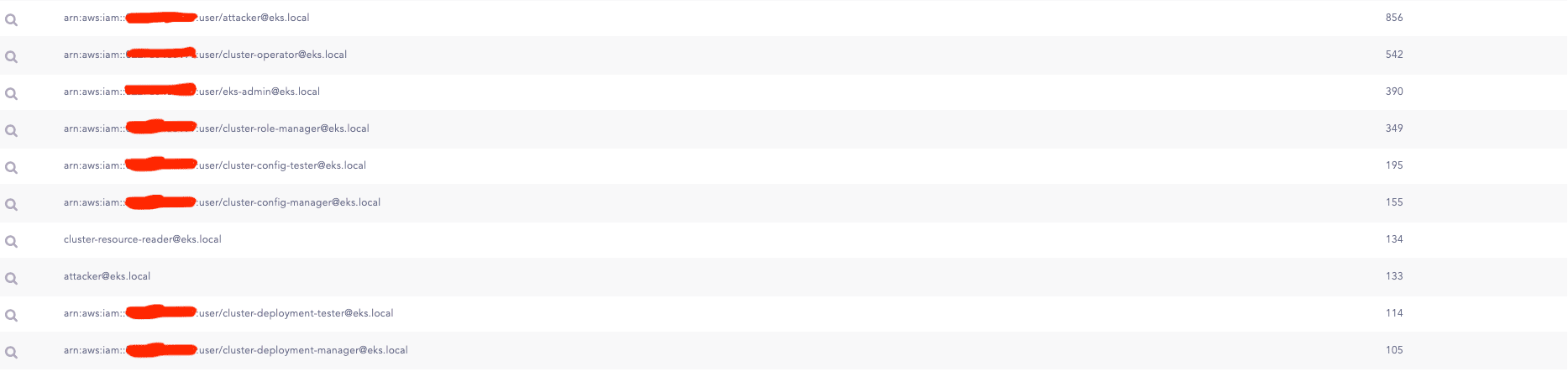
K8s API User Request
Users denote the usernames of individuals submitting requests to the API Server for resource access within the cluster. Comprehending user information is vital for identifying unauthorized users who may attempt to gain illegitimate access to resources. For example, a user not affiliated with the cluster could present a security threat, thereby necessitating close monitoring of such requests.
The query yields a list of users making requests to the API Server from diverse IP addresses, while intentionally excluding service accounts within the clusters.
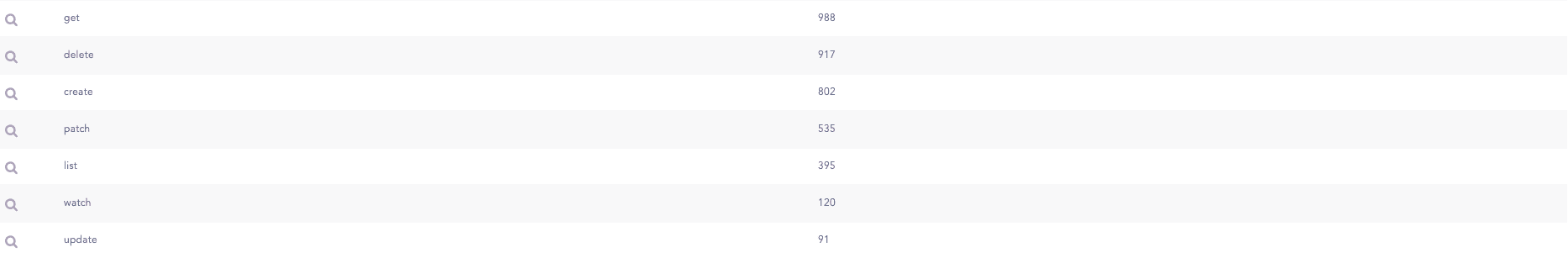
K8s API Requests methods
API request methods, commonly referred to as verbs, define the actions performed on specific resources governed by Kubernetes Role-Based Access Control (RBAC). These methods indicate the status of resources being created, updated, or deleted within a Kubernetes (k8s) cluster. The available request methods include Create, Update, Patch, Delete, Watch, Get, and DeleteCollection.
For instance, a high volume of Patch or Update requests suggests that a user is attempting to modify resources within the k8s cluster. Conversely, an elevated number of Delete requests indicates that resources within the k8s cluster are being removed.
The query provides insights into the request methods utilized by users to execute actions within the k8s cluster.
K8s API RBAC Request Decisions
Request Decisions outline user requests categorized as either Allowed or Forbid, as defined by Kubernetes RBAC (Role-Based Access Control). An Allowed Decision indicates that the user's request is permitted within the cluster, enabling them to make modifications to resources. Conversely, a Forbid Decision signifies that the user's request is denied due to the constraints established by RBAC Role bindings. For instance, a Forbid Decision may indicate that the user is attempting to access restricted resources within the K8s Cluster.
The query provides a count of decisions based on the audit logs related to RBAC, ensuring comprehensive tracking and analysis of user permissions and actions within the cluster environment.

Additionally, we can drill down for the forbid decision based on the user requests.
Mitigations
- Prevent public exposure of the Kubernetes (K8s) API by utilizing native cloud platform features to restrict the IP ranges permitted to access the API server.
- Block direct access to the K8s API Endpoint from public networks by routing traffic through network proxies, gateways, and firewalls.
- Conduct regular analyses of K8s API logs to identify potential unauthorized access attempts, and impose limits on requests to the K8s API Endpoint to enhance security measures.
Execution Phase
Hypothesis
We assume that an attacker has identified a cluster user or service account with the necessary permissions to create new resources, such as privileged pods. This access allows them to execute commands within existing pods and establish reverse shell connections through those pods.
K8s API Shell/Command inside the container
| Mitre ATT&CK Technique Name | Container Administration Command |
|---|---|
| Mitre ATT&CK Technique ID | T1609 |
Gaining shell or command access to a container represents a substantial opportunity for an attacker, enabling them to execute commands necessary for installing required packages. By utilizing package management commands such as apt, apk, yum, or dnf, an attacker can install tools like wget, curl, or network management utilities such as Netcat. Furthermore, attempts to read sensitive files like passwd or shadow, or to access environment variables associated with the Kubernetes API or Service Account Token, can facilitate further exploitation within a Kubernetes (K8s) cluster.
Additionally, legitimate users within the cluster are cognizant of the containers where they possess shell access and the commands they are authorized to execute. However, various restrictions enforced by Role-Based Access Control (RBAC) in the K8s API may expose potential threats within the cluster. To identify these threats, we can utilize the sub-resource exec, which is specifically designed for executing commands inside a container.
This query provides valuable insights into users executing commands within a container, thereby assisting in tracking and mitigating potential security risks.
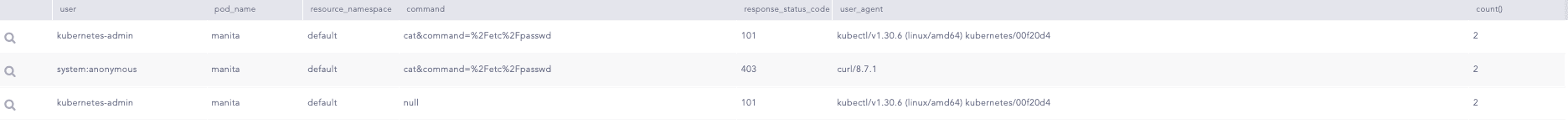
Moreover, we can dill down to look for specific command executed such as
- Package management commands
- File download commands
- Read service account token
- Read environment variables
- Read sensitive files
K8s API Side Car Injection
| Mitrea ATT&CK Technique Name | Deploy Container |
|---|---|
| Mitre ATT&CK Technique ID | T1610 |
A sidecar container refers to an auxiliary container that operates in conjunction with the primary container within a pod. For example, service mesh proxies serve as sidecars in application pods. Attackers may exploit this configuration by injecting a sidecar container into a legitimate pod within the cluster, thereby enabling them to execute their code and obscure their activities, rather than deploying a separate pod. One method to incorporate containers into running resources such as Deployments, DaemonSets, or StatefulSets is through a "kubectl patch" operation, which allows for seamless updates and modifications.
Mitigations
- Disabling the exec feature or restricting the list of shell commands that can be executed within the container by utilizing Open Policy Agent will assist in preventing the execution of malicious commands.
- Limiting access to core resources, such as deployments, stateful sets, and daemon sets, while confining the deployment of new pods to those originating solely from a Trusted Supply Chain will significantly enhance security.
Persistence
Hypothesis
We assume that an attacker has gained access to a specific namespace. The service account may or may not possess the necessary permissions to view, create, or modify cron jobs, or to launch new pods from unauthorized private or public registries, thereby establishing a persistent foothold within the cluster. It is imperative to regularly review and audit service account permissions to mitigate such risks effectively.
K8s API Cronjobs
| Mitre ATT&CK Technique Name | Scheduled Task/Job |
|---|---|
| Mitrea ATT&CK Sub-Technique Name | Container Orchestration Job |
| Mitrea ATT&CK Technique ID | T1053.007 |
Suspicious activity may occur when a user or service account makes multiple attempts—regardless of whether these attempts are successful or denied—to create new cron jobs or modify existing ones to execute malicious applications. Such behavior raises concerns regarding the potential establishment of footholds within a cluster.
To effectively monitor these actions, the following query can be employed to track the creation, modification, and deletion of cron jobs, along with the corresponding Role-Based Access Control (RBAC) decisions made by a user.
K8s API Backdoor Container
| Mitre ATT&CK Technique Name | Implant Internal Image |
|---|---|
| Mitre ATT&CK Technique ID | T1525 |
When a container is created from an unknown private or public registry, it raises concerns regarding the potential for a user to establish a persistent foothold, which could enable an attacker to gain easy access to the cluster in the future.
This query reveals the pod that was created, along with the image name and the registry from which the image was sourced.
Mitigations
-
Regularly verify the integrity of images and containers utilized in cloud deployments to ensure they remain unaltered and free from malicious software.
-
Ensure that container images are sourced from authorized public container image registries and that the images intended for deployment are signed by trusted sources.
-
Implement Role-Based Access Control (RBAC) to restrict privileges, ensuring that only authorized Roles or ClusterRoles can create, view, and modify scheduled tasks on remote systems.
Privileged Escalation
Hypothesis
We assume that an attacker has established a persistent foothold within the cluster and is attempting to escalate their privileges. Privilege escalation in a cluster can occur when an unauthorized user or IP address creates, or tries to create, a Role or ClusterRole for a ServiceAccount or User, and subsequently binds these roles to the Cluster Admin role or another role with higher privileges. Additionally, an attempt to launch a privileged container within the cluster by mounting the Host Proc file system or bypassing security contexts can lead to container escape, granting root access to the host machine.
K8s API Creation or Modification of Roles and Roles Binding
| Mitre ATT&CK Technique Name | Account Manipulation |
|---|---|
| Mitre ATT&CK Sub-Technique Name | Additional Container Cluster Roles |
| Mitre ATT&CK Technique ID | T1098.006 |
In Kubernetes, Cluster Roles are employed to define roles that function across the entire cluster, enabling actions to be executed on various resources. These roles are regulated by the Role-Based Access Control (RBAC) of the API Server. If RBAC denies an unauthorized user the capability to bind their roles to Cluster Roles, it may indicate an attempted privilege escalation.
The following query can be used to track changes done in Roles and RoleBinding:
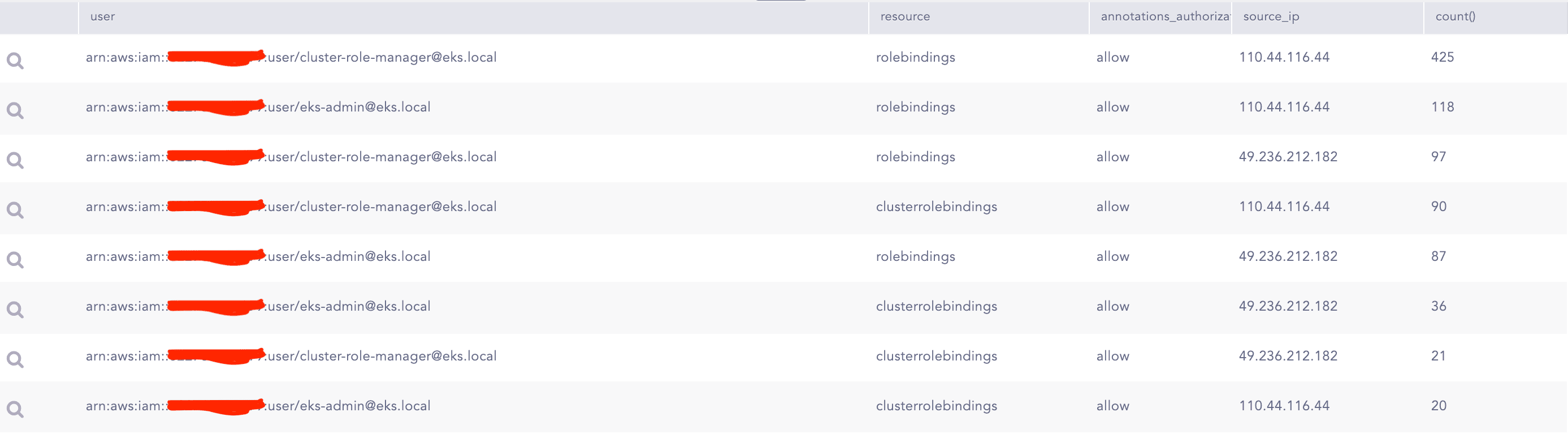
K8s API Creation of Privilege Container
| Mitre ATT&CK Technique Name | Escape to Host |
|---|---|
| Mitre ATT&CK Technique ID | T1611 |
In Kubernetes, a privileged container has unrestricted access to all host system resources, thereby circumventing container isolation mechanisms and granting root-level access to the host machine. If a user attempts to create a container with the privileged flag set to true, mounts the host's proc file inside the container, or shares the host namespace with other containers, it may indicate a potential privilege escalation risk, which could compromise the host network.
To detect users attempting to create containers with the privileged flag set to true, the following query can be utilized:

Defense Evasion
Hypothesis
Kubernetes “Events” are the resources that provide insights into the activities happening within a cluster which includes information about the change of state for resources. An attacker having privileged access can view the events being generated within a cluster by listing or watching Events resource and can coverup their tracks by deleting or clearing Events of a specific namespace or entire cluster.
K8s API Events Viewed or Events Cleared
| Mitre ATT&CK Technique Name | Indicator Removal |
|---|---|
| Mitre ATT&CK Technique ID | T1070 |
Generally, Legitimate users almost never view or delete the events being generated during the change of state for resources unless they are required to do so. Any user viewing events might seems normal or such user deleting events for a specific resources or cluster wide indicates a illegitimate user trying to clear tracks for wrong doing done by him/her.
The query can be used to get information about the user listing resources inside a cluster
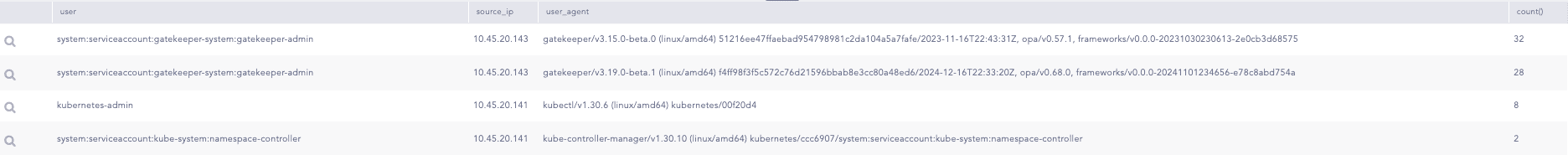
Furthermore, We can use below query to get information about the user who is responsible for clearing Resource Events

K8s API Creation of Pods in System Namespace
| Mitre ATT&CK Technique Name | Masquerading |
|---|---|
| Mitre ATT&CK Sub-Technique Name | Match Legitimate Name or Location |
| Mitre ATT&CK Technique ID | T1036 |
Detects deployments of pods within the kube-system namespace, which could be intended to imitate system pods. System pods, created by controllers such as Deployments or DaemonSets have random suffixes in their names. Attackers can use this fact and name their backdoor pods as if they were created by these controllers to avoid detection. Deployment of such a backdoor container e.g. named kube-proxy-1r4t, could be attempted in the kube-system namespace alongside the other administrative containers.
Mitigations
- Automatically forward events to a log server or data repository to prevent conditions in which the adversary can locate and manipulate data on the local system.
- Protect generated event files that are stored locally with proper permissions and authentication.
Credential Access
Hypothesis
Adversaries now possess privileged access to cluster or host machines, which allows them to extract sensitive information, such as credentials stored within Kubernetes resources like Secrets or tokens. This access can enable them to conduct further resource discovery, facilitate lateral movements, or manipulate credentials used by these resources, potentially leading to unexpected behavior.
K8s API List or Modify Secrets
| Mitre ATT&CK Technique Name | Unsecured Credentials |
|---|---|
| Mitre ATT&CK Sub-Technique Name | Container API |
| Mitre ATT&CK Technique ID | T1552.007 |
Kubernetes secrets are essential for the secure management of sensitive information, including passwords, API keys, and certificates. While these secrets are critical for maintaining security, they can also become targets for malicious actors seeking unauthorized access. Instances of prohibited actions detected by Kubernetes Role-Based Access Control (RBAC) may signify suspicious activities, such as attempts to read or modify existing secret resources. It is imperative to monitor these activities closely to ensure the integrity and confidentiality of sensitive data.
Access Container Service Accounts Tokens
| Mitre ATT&CK Technique Name | Steal Application Access Tokens |
|---|---|
| Mitre ATT&CK Technique ID | T1528 |
Processes operating within a container can interact with the Kubernetes API server by utilizing service account tokens. If a container is breached, a malicious actor could potentially steal the container's token, granting them unauthorized access to execute Kubernetes API commands.
The following query can be employed to identify token access via the Container Shell.
Additionally, you can generate a token for a service account using the kubectl command along with the Sub Resource Token. Any unauthorized attempts to create a token for a service account by illegitimate users should be regarded as suspicious.
Mitigations
- Apply the principle of Least Privilege for Service Accounts by restricting the automatic mounting of tokens when a pod does not need access to the Kubernetes API.
- Enhance security by integrating Kubernetes with external secret management systems such as HashiCorp Vault, AWS Secrets Manager, or Azure Key Vault, which provide advanced and secure handling of sensitive information.
- Establish automatic secret rotation to regularly update and change secrets, minimizing the risk of exposure in the event of a potential breach. Utilize tools like Kubernetes external secrets to streamline and automate this process.
Discovery
Hypothesis
If an adversary gains access to a Service Account Token within a Kubernetes cluster, they can leverage this access to interact with the Kubernetes API and other resources. This capability enables the attacker to collect information about the cluster, move laterally within the environment, escalate privileges, and potentially compromise more critical resources. Ultimately, this could lead to the complete takeover of the entire cluster.
K8s API Resource Discovery
| Mitre ATT&CK Technique Name | Container and Resource Discovery |
|---|---|
| Mitre ATT&CK Technique ID | T1613 |
An adversary possessing a Service Account Token may seek to uncover resources within a Kubernetes cluster by employing brute-force techniques on API resource names. The attacker typically utilizes a dictionary or a list of commonly used resource names to gain access to various Kubernetes resources, including Pods, Services, Deployments, Secrets, ConfigMaps, and others. A series of unsuccessful attempts that yield HTTP status codes such as 401 (Unauthorized), 403 (Forbidden), or 404 (Not Found) could signify an ongoing resource discovery effort.
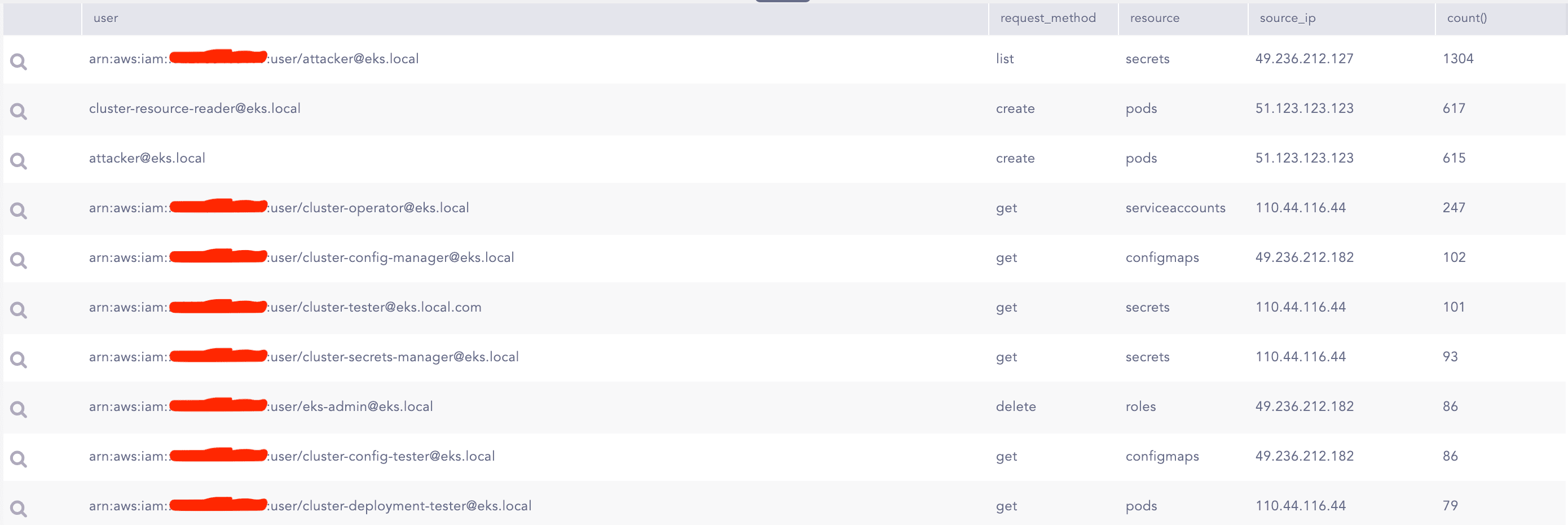
Mitigations:
- Implement Network Policies to limit communication between services, ensuring that only authorized services can discover or interact with specific Kubernetes resources.
- Implement RBAC policies to control access to resources based on user roles, guaranteeing that only individuals with the appropriate permissions can discover or engage with certain resources.
Lateral Movement
Hypothesis
If an adversary successfully infiltrates a Kubernetes cluster through a compromised user account, service account, or a vulnerable component, they will likely engage in lateral movement within the cluster. This can be accomplished by exploiting misconfigurations, vulnerable services, and excessive permissions. Such actions may lead to privilege escalation and expanded access to critical resources, ultimately resulting in a cluster-wide compromise and potential service disruption. It is essential to implement robust security measures to mitigate these risks effectively.
K8s API CoreDNS Poisioning
| Mitre ATT&CK Technique Name | Adversary-in-the-Middle |
|---|---|
| Mitre ATT&CK Technique ID | T1557 |
| Microsoft Threat Matrix for Kubernetes ID | MS-TA9035 |
CoreDNS is a flexible Domain Name System (DNS) server developed in Go and maintained by the Cloud Native Computing Foundation (CNCF). It serves as the primary DNS service utilized within Kubernetes environments. The configuration for CoreDNS can be adjusted through a file known as the corefile, which is stored in a ConfigMap object within the kube-system namespace in Kubernetes. If attackers gain permissions to modify this ConfigMap—potentially through the container’s service account—they could alter the cluster’s DNS behavior, leading to DNS poisoning and the potential hijacking of the network identities of other services.
This query can be used to track modification of CoreDNS configmaps
Mitigations:
- Enforce rigorous Role-Based Access Control (RBAC) policies to guarantee that users, service accounts, and workloads possess only the minimum necessary access to resources. This approach significantly mitigates the risk of unauthorized access and lateral movement within the cluster.
- Implement Kubernetes Network Policies to manage and restrict traffic between pods and namespaces. This strategy effectively prevents unauthorized communication among components and limits attackers' capacity to navigate laterally across the network.
Impact
Hypothesis
Failure to effectively detect and mitigate lateral movement within a Kubernetes cluster can expose organizations to significant risks. Attackers may escalate their privileges, compromise critical resources, and disrupt services, resulting in severe business consequences, including data breaches, financial losses, and reputational damage. For example, modifying or deleting essential Kubernetes resources, such as deployments, can result in considerable disruptions to service availability.
K8s API Resources Modification or Deletion
| Mitre ATT&CK Technique Name | Data Destruction |
|---|---|
| Mitre ATT&CK Technique ID | T1485 |
Modifying or deleting Kubernetes (K8s) API resources—such as Deployments, Services, Storage, or ConfigMaps—can lead to significant disruptions in application performance and service availability. The removal of critical resources may result in downtime, data loss, or compromised functionality, all of which can negatively impact business operations and customer experience. Similarly, altering these resources without proper validation can introduce configuration errors or security vulnerabilities, potentially leading to unexpected behavior or system breaches. It is essential to approach such modifications with caution and thorough assessment to mitigate risks effectively.
The query can be utilized to monitor the deletion of any resources within the cluster.

Mitigations
- Enforce stringent RBAC policies to limit permissions for data modification or deletion, ensuring that only authorized users can access or alter sensitive resources.
- Establish automated monitoring for Kubernetes (K8s) resources to detect unauthorized data and resource destruction, along with auditing processes to track changes and identify potential risks.
- To address these risks, implement rigorous change management practices, version control, and thorough testing, complemented by appropriate access controls and rollback strategies.
Conclusion
In conclusion, as Kubernetes continues to gain traction as the preferred platform for managing containerized applications, the importance of robust security measures cannot be overstated. The insights provided by Kubernetes API Server Audit Logs are invaluable for threat hunting, enabling organizations to proactively identify and mitigate potential security threats. With a significant percentage of organizations experiencing security incidents, it is imperative to prioritize the monitoring of audit logs to ensure compliance, enhance accountability, and improve overall operational efficiency. By leveraging these logs effectively, organizations can not only safeguard their Kubernetes environments but also foster a culture of security awareness and resilience, ultimately supporting their business objectives in an increasingly complex digital landscape.
The post Kubernetes Threat Hunting using API Server Audit Logs appeared first on Logpoint.
Article Link: https://www.logpoint.com/en/blog/emerging-threats/kubernetes-threat-hunting-using-api-server-audit-logs/