The SOCRadar Dark Web Team has meticulously documented a series of disturbing transactions within the obscured recesses of the dark web. These include the alarming sale of unauthorized shell access to a Japanese IT firm, the auctioning of 12,000 CPanel accesses, the exposure of sensitive credit card information from New Zealand, and a substantial LinkedIn database breach impacting millions. This intelligence highlights the increasingly sophisticated and perilous landscape of cyber threats where personal and corporate vulnerabilities are bartered with chilling efficiency.
Here are the latest dark web activities that have piqued our interest.
Get your free Dark Web Report and find out if your data has been compromised.Unauthorized Shell Access Leak is Detected for a Japanese Information Technology Company
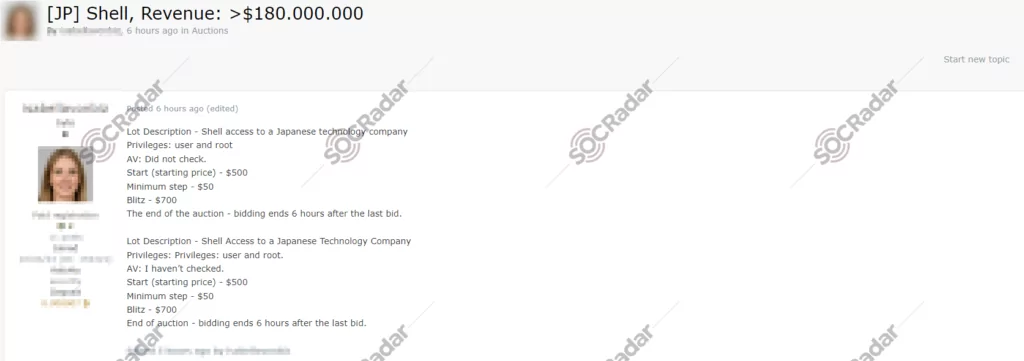
The SOCRadar Dark Web Team has detected a post on a hacker forum where a threat actor alleges they are selling unauthorized shell access to a Japanese information technology company. The offer includes user and root privileges, although it specifies that antivirus (AV) checks have not been performed. The starting price for this access is $500, with a minimum bid increment of $50 and a ‘Blitz’ buy-it-now option at $700. The auction is set to conclude 6 hours after the last bid is placed.
12K CPanel Accesses are on Sale
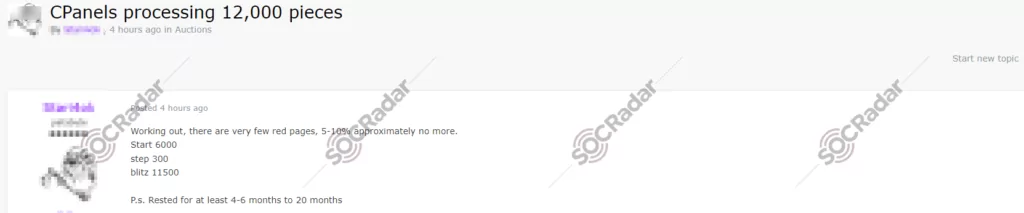
The SOCRadar Dark Web Team has detected a post on a hacker forum where a threat actor is offering for sale what they claim to be 12,000 CPanel accesses. According to the details mentioned in the post, the threat actor claims that most of these CPanels do not lead to ‘red pages,’ implying a low rate of compromised or alert-triggering sites, estimating this at about 5-10%. The sale is structured as an auction with the starting bid placed at 6,000, a minimum bid increment ‘Step’ of 300, and a ‘Blitz’ price of 11,500, presumably the amount to end the auction immediately. The post also notes that these CPanel accesses have supposedly been ‘rested’ or unused for a period ranging from 4 to 20 months, potentially to avoid detection.
107 Credit Cards are on Sale
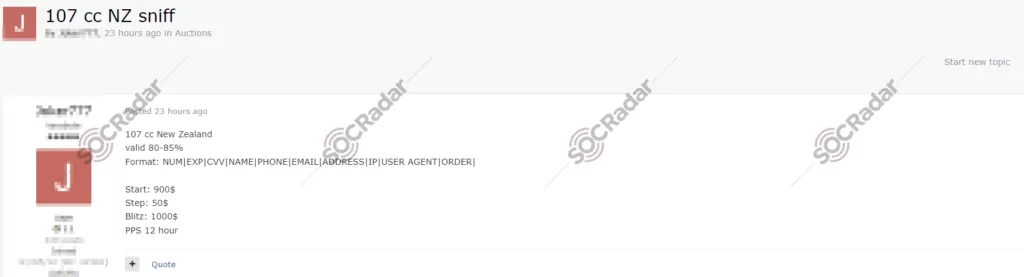
The SOCRadar Dark Web Team detected a post in a hacker forum where a threat actor offered a batch of 107 credit cards, allegedly from New Zealand, for sale. The threat actor advertises a validity rate of 80-85% for these cards. They present them in a format that includes numerous sensitive details such as the card number, expiration date, and CVV, along with personal information like the cardholder’s name, phone number, e-mail, and address, as well as associated IP and user agent data. The starting bid for this data set is $900 with increments of $50, and a “Blitz” buy-now option is priced at $1000. Additionally, a post-purchase service (PPS) is being offered, which presumably lasts 12 hours.
Database of LinkedIn is Leaked
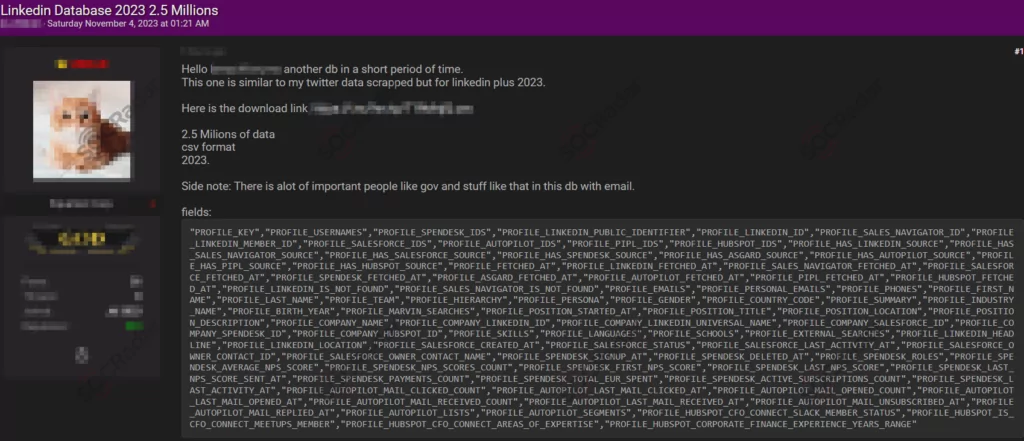
The SOCRadar Dark Web Team has identified a post on a hacker forum in which a threat actor alleges possession of a leaked database from LinkedIn. The post suggests that this database, claimed to be in CSV format and containing data from 2023, allegedly includes information on 2.5 million individuals, indicating that it features records of government officials and other significant entities.
Powered by DarkMirror
Gaining visibility into deep and dark web threats can be extremely useful from an actionable threat intelligence and digital risk protection perspective. However, monitoring all sources is simply not feasible, which can be time-consuming and challenging. One click-by-mistake can result in malware bot infection. To tackle these challenges, SOCRadar’s DarkMirror screen empowers your SOC team to follow up with the latest posts of threat actors and groups filtered by the targeted country or industry.
screen empowers your SOC team to follow up with the latest posts of threat actors and groups filtered by the targeted country or industry.
The post Japanese IT Breach, CPanel Auctions, LinkedIn Data Leak appeared first on SOCRadar® Cyber Intelligence Inc..
Article Link: Japanese IT Breach, CPanel Auctions, LinkedIn Data Leak
