Introduction
This article opens gates for one of the main sections of iOS application assessment i.e. assessment of the network traffic. Assessment of the network traffic of a mobile application is known as Traffic analysis. Let’s get started with this interesting and important part of iOS application assessment.Choosing a tool for Traffic Analysis
In order to help us carry out traffic analysis on mobile and web applications, many tools are publicly available for getting our job done. Some of the famous ones are Burp Suite, OWASP Zed Attack Proxy (ZAP), Fiddler proxy, Charles proxy and many more.



For carrying out traffic analysis, we would prefer a stable and reliable tool which can capture the application traffic for most of the communication protocols used by the applications today. Extensibility of the tool is also important as we would need the same tool to work with some tweaks implemented.
The most widely used client side proxy tool is Burp Suite. For getting it work, Java Runtime Environment (JRE) needs to be there on our computer. So, Burp Suite is platform independent too. It's community version is free of cost but has less features than its paid version i.e. Burp Suite Professional. The professional version is available for use by individuals or an organization. It is preferred to use the Professional version due to presence of the Scanner and other features in it.
Understanding use of Burp Suite tools
Let us get an understanding of Burp Suite’s in-built tools.- Target - This tool contains the site map, with detailed information about the target applications. It lets to define the target scope so that it can be used by other tools to recognize the in-scope items. It consists of two tabs:
- Site map
- Scope
- Proxy - This tools does the main task for Burp Suite i.e to intercept, view and modify all requests and responses passing between the iPhone device and destination web servers. It consists of four tabs namely:
- Intercept
- HTTP History
- WebSockets History
- Options
- Spider - This tool performs the task of spidering through the application i.e sending requests to all the URLs found in server’s responses recursively and lets us know some pages that we might miss out in manual assessment. It’s job is done by the two tabs:
- Control
- Options
- Scanner - This is the tool for which Burp Suite Professional is paid for. It consists of vulnerabilities and their definitions which keep updating with new versions of Burp Suite. The vulnerabilities are scanned automatically by their most common detection techniques and reported back to the user. It comprises of five tabs:
- Issue activity
- Scan queue
- Live Scanning
- Issue definitions
- Options
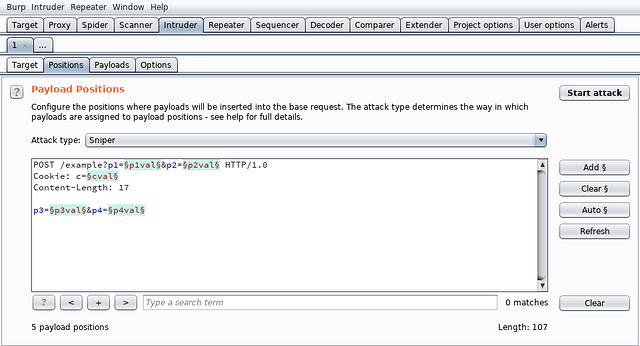
- Intruder - This tool is used for automated testing of attacks and payloads customized by us. The settings can be customized for testing all the requests and the required parameters. Its task is performed by the four tabs namely:
- Target
- Positions
- Payloads
- Options
There are four types of attacks offered by the Burp Suite Intruder:
- Sniper - This attack is used to test the response from the server against a single set of payloads on a particular parameter. It is mostly used to check possibility of Brute Force attacks, implementation of Rate Limiters and other Enumeration stuff.
- Battering ram - This attack is similar to Sniper but allowing multiple insertion points within a request. It is used for testing with the same payload in multiple insertion points.
- Pitchfork - This attack is used to test two or more insertion points with one payload from each set of lists providing them.
- Cluster bomb - This attack is used for testing with all possible permutations from the defined payload sets. It checks out the server’s response to all the possible combinations of applied payloads.
- Repeater - This tool helps in obtaining proof of concepts from manual assessment of the requests. The requests stored in this tool can be forwarded to the server at any instance of time and the response can be analysed using filtering mechanisms built in the tool.
- Sequencer - This tool is used for prediction purposes. It can capture the list of times either automatically or manually.The values can be analysed for randomness and checked for prediction of the next item in the list (if possible). It consists of three tabs:
- Live capture
- Manual load
- Analysis options
- Decoder - This tool consists of popular encoding and decoding algorithms. It is used for conversion of values from one form to the other.
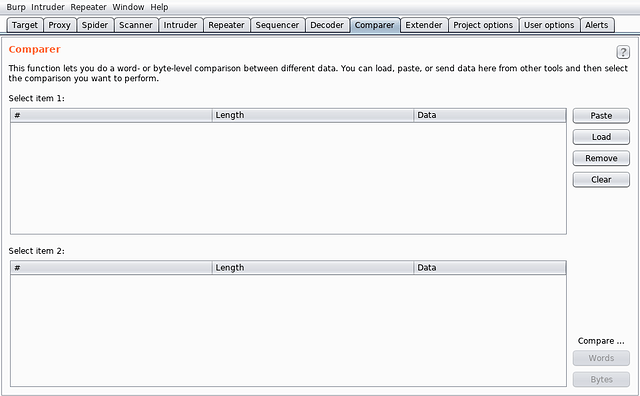
- Comparer - This tool is used to compare two pieces of information for addition, deletion or modification of data. For example, it might be used to check the difference in the server’s responses when the value of any of the parameter is changed in the request.
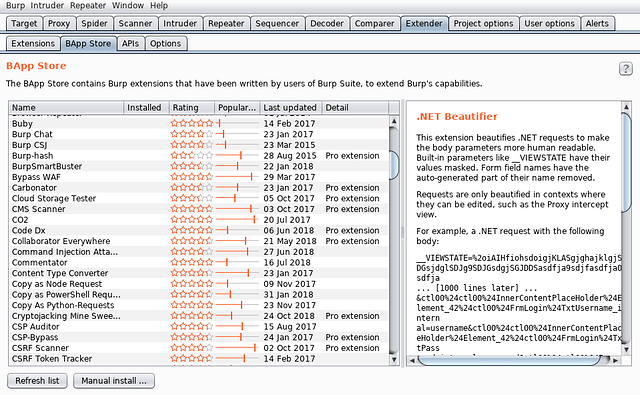
- Extender - This tool is used for extending the functionality of the Burp Suite inbuilt tools and tabs in order to quicken up testing. Burp Suite’s publicly available extensions can be downloaded from BApp Store and also extensions can be developed in Java, Python or Ruby. It is made up of four tabs:
- Extensions
- BApp Store
- APIs
- Options
- Project Options - This tool provides options for project related settings. The settings may be used to overwrite the user options or to specify rules for handling the server’s requests and responses for the current project. One useful and interesting tab is the Sessions tab which helps to carry out our assessment quickly smoothly by specifying macros for maintaining the user sessions of our target application. Other useful options include setting up Burp Collaborator server and scheduling tasks for Burp Suite. The tool comprises of four tabs:
- Connections
- HTTP
- SSL
- Sessions
- Misc
- User options - This tool is used to customize the interface of Burp Suite and also configure upstream server or platform authentication as required. It provides four tabs:
- Connections
- SSL
- Display
- Misc
- Alerts - This tool is used to log events and error messages from the Burp Suite tools and also the extensions. The alerts are very helpful in debugging tasks.
Installing the mobile assistant
Burp Suite offers a mobile assistant to facilitate testing of iOS apps. It supports the following key functions:- It can modify the system-wide proxy settings of iOS devices so that HTTP(S) traffic can be easily redirected to a running instance of Burp.
- It can make an attempt to circumvent SSL certificate pinning in selected apps, allowing Burp Suite to break their HTTPS connections and intercept, inspect and modify all traffic.
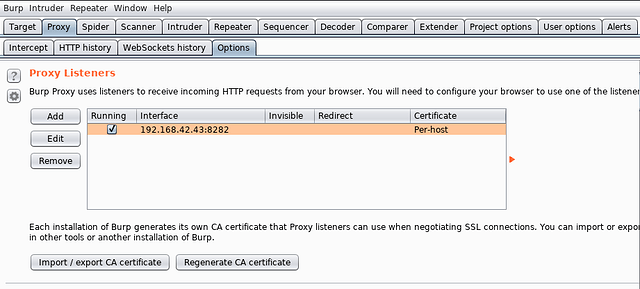
Installing the mobile assistant is easy. On the computer, start Burp Suite and configure to listen on any particular interface on a desired port. For example, in the screenshot, Burp Suite is configured to listen on 192.168.42.43 at port number 8282.
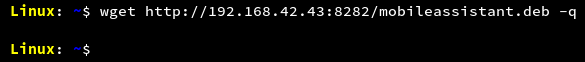
In the configured state, the mobile assistant can be downloaded using the URL http://192.168.42.43:8282/mobileassistant.deb in any browser or using terminal as shown in the screenshot.
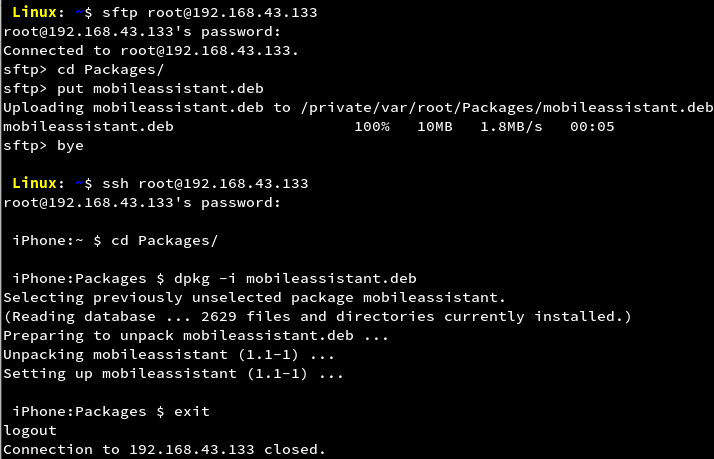
Installation to the device can be done as shown in the screenshot.
It can also be installed using Cydia. For help in installing, refer to https://support.portswigger.net/customer/portal/articles/2798916-installing-burp-suite-mobile-assistant.
Conclusion
In this article, we have learnt about proxy tools that we can use for performing traffic analysis on mobile applications. We have got a healthy introduction to the Burp’s in-built suite of tools. Good use of these tools comes from practice. With every application we determine to secure, we will learn more and more about the use of these tools. In the next part of this section, we will learn to capture the network traffic of an iOS application.Article Link: https://blog.lucideus.com/2019/04/ios-application-security-part-8-getting.html