Authored by SangRyol Ryu
We live in a world where advertisements are everywhere, and it’s no surprise that users are becoming tired of them. On the other hand, developers are driven by profit and seek to incorporate more advertisements into their apps. However, there exist certain apps that manage to generate profit without subjecting users to the annoyance of ads. Is this really good?
Recently, McAfee’s Mobile Research Team discovered a concerning practice among some apps distributed through Google Play. These apps load ads while the device’s screen is off, which may initially seem convenient for users. However, it’s actually a clear violation of Google Play Developer policy on how ads should be displayed. This affects not only the advertisers who pay for invisible Ads, but also the users as it drains battery, consumes data and poses potential risks such as information leaks and disruption of user profiling caused by Clicker behavior.
The team has identified 43 apps that collectively downloaded 2.5 million times. Among the targeted apps are TV/DMB Player, Music Downloader, News, and Calendar applications. McAfee is a member of the App Defense Alliance focused on protecting users by preventing threats from reaching their devices and improving app quality across the ecosystem. We reported the discovered apps to Google, which took prompt action. Most apps are no longer available on Google Play while others are updated by the developer. McAfee Mobile Security detects this threat as Android/Clicker. For more information, and to get fully protected, visit McAfee Mobile Security.

Many affected apps
How does it work?
This ad fraud library utilizes specific tactics to avoid detection and inspection. It deliberately delays the initiation of its fraudulent activities, creating a latent period from the time of installation. What’s more, all the intricate configurations of this library can be remotely modified and pushed using Firebase Storage or Messaging service. These factors significantly add to the complexity of identifying and analyzing this fraudulent behavior. Notably, the latent period typically spans several weeks, which makes it challenging to detect.
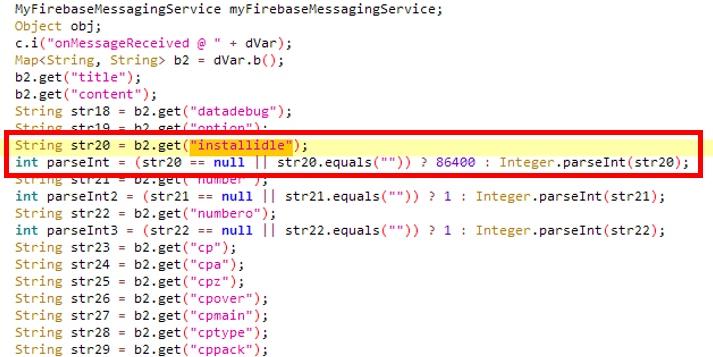
Getting latent period by using Firebase Messaging Service
It is important to be cautious about the implications of granting permissions, such as excluding ‘power saving’ and allowing ‘draw over other apps’. These permissions can enable certain activities to occur discreetly in the background, raising concerns about the intentions and behavior of the applications or libraries in question. Allowing these permissions can result in more malicious behavior, such as displaying phishing pages, also to displaying ads in the background.
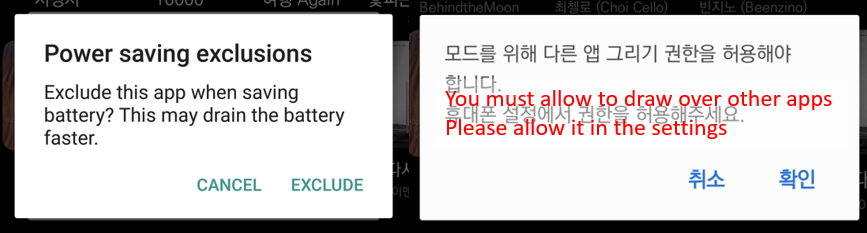
Asked permissions to run in the background and keep it hidden
When the device screen is turned off after the latent period, the fetching and loading of ads starts, resulting in users being unaware of the presence of running advertisements on their devices. This ad library registers device information by accessing the unique domain (ex: mppado.oooocooo.com) linked with the application. Then go to Firebase Storage to get the specific advertisement URL and show the ads. It is important to note that this process consumes power and mobile data resources.
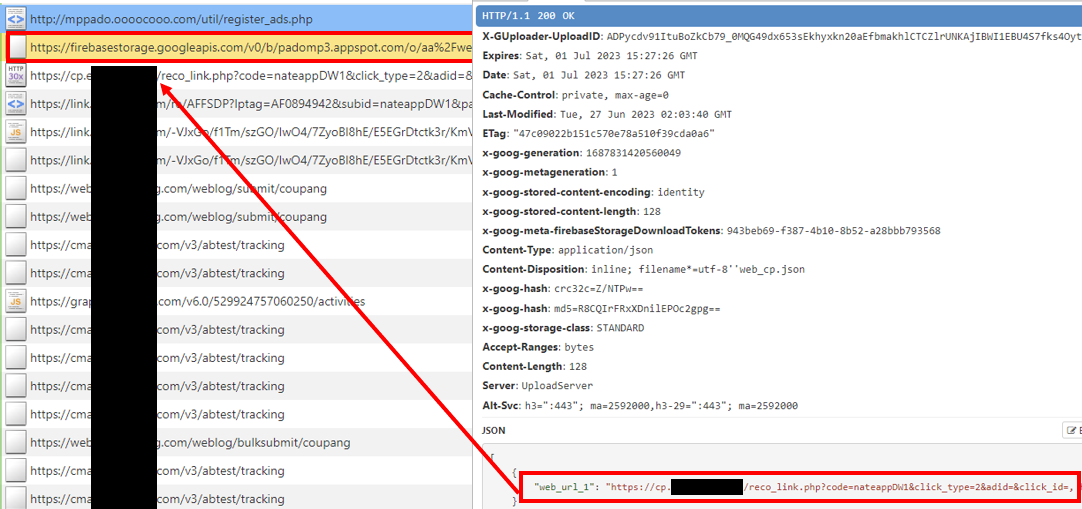
Observed traffic when the screen off
If users quickly turn on their screens at this point, they might catch a glimpse of the ad before it is automatically closed.
Example of an advertising site displayed when the screen is off
In conclusion, it is essential for users to exercise caution and carefully evaluate the necessity of granting permissions like power saving exclusion, or draw over other apps before allowing them. While these permissions might be required for certain legitimate functionalities for running in the background, it is important to consider the potential risks linked with them, such as enabling hidden behaviors or reducing the relevance of ads and contents displayed to users because the hidden Clicker behavior. By using McAfee Mobile Security products, users can further safeguard their devices and mitigate the risks linked with these kinds of malware, providing a safer and more secure experience. For more information, visit McAfee Mobile Security
The post Invisible Adware: Unveiling Ad Fraud Targeting Korean Android Users appeared first on McAfee Blog.
Article Link: Invisible Adware: Unveiling Ad Fraud Targeting Korean Android Users | McAfee Blog