For 7 years, ANY.RUN has been aiding cybersecurity experts in malware analysis through our interactive cloud sandbox. Our goal is to help enterprises, independent experts, and SMEs in understanding and defending against both persistent and emerging threats.
Today, we’re taking a big step forward in our effort to help businesses strengthen security with the introduction of Threat Intelligence Lookup — a streamlined platform that makes it easier to find relevant threat data from ANY.RUN sandbox tasks.
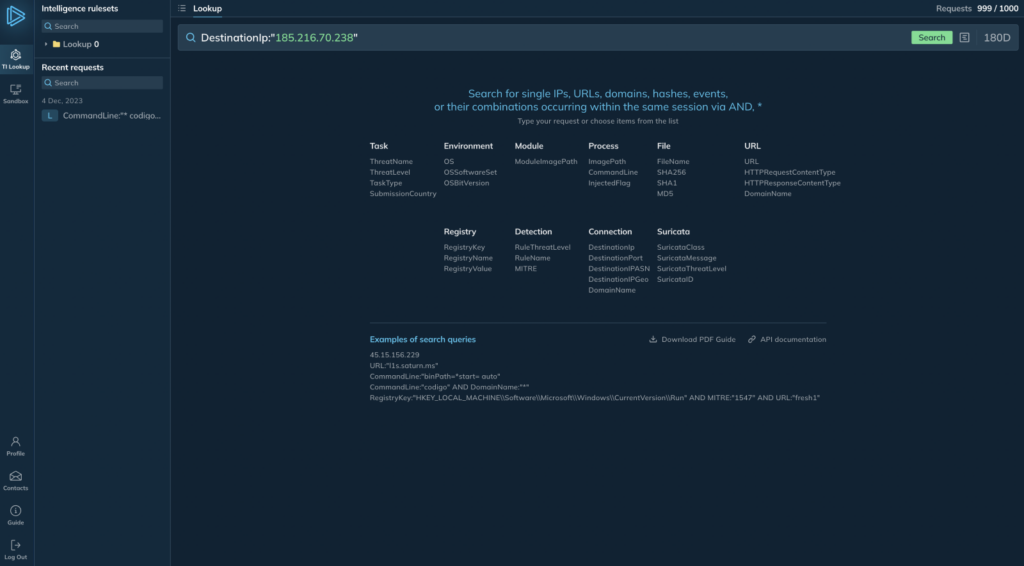 Homepage of ANY.RUN Threat Intelligence Lookup
Homepage of ANY.RUN Threat Intelligence Lookup What is Threat Intelligence Lookup?
Threat Intelligence Lookup centralized repository of millions of IOCs extracted from ANY.RUN’s extensive database of interactive malware analysis sessions (sandbox tasks). It turns isolated data into a holistic view of persistent and emerging threats.
By analyzing processes, modules, files, network traffic, and registry activities, you get detailed context and can fully understand an attack’s nature, scope, and impact.
Threat Intelligence Lookup is available through an intuitive web-interface as well as an API for integration with your existing security solutions.
Bolster your security
Try ANY.RUN’s Threat Intelligence Lookup platform
In ANY.RUN’s Threat Intelligence Lookup you can find linked threat data both through our Intuitive interface or via API access for integrations with security solutions. Regardless of your preferred interface, you will take advantage of:
- 1000 fresh entries per day
- 2-second request response time
- 30+ search parameters
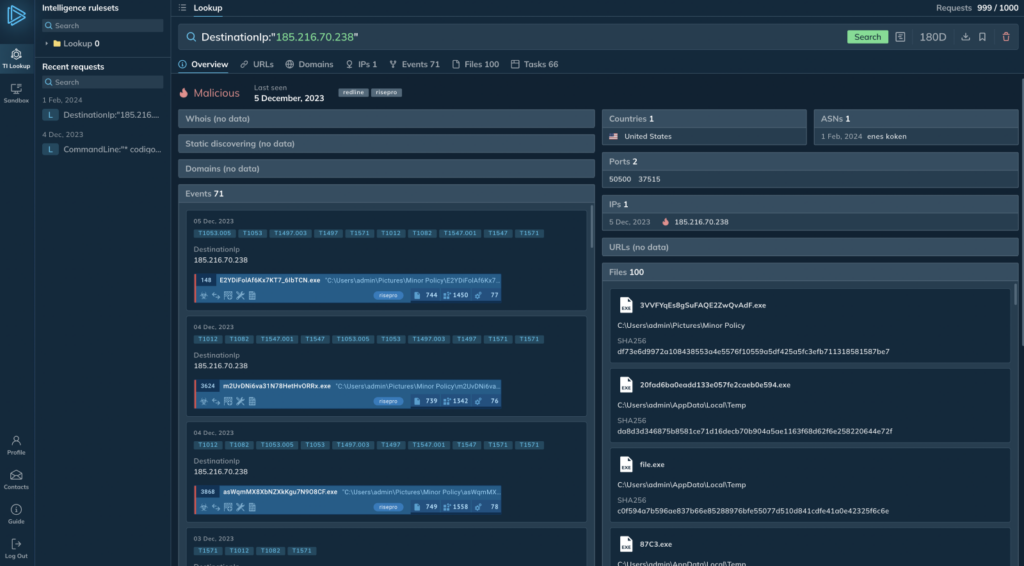 You can search for linked IOCs using 30+ search fields
You can search for linked IOCs using 30+ search fields A powerful search engine for contextual IOCs
You can investigate processes, modules, files, network, and registry activity logged by ANY.RUN sandbox using a variety of search parameters:
- Single IOC: Look for specific IOCs, including URLs, MD5, SHA1, SHA256 hashes, IP addresses, or domain names.
- Logged event fields: Focus on key fields in logged events. Look for things like command lines, registry paths and values, and names of processes and modules.
- Detection details: Use MITRE techniques and detection names. Pay attention to Suricata class, message, and ID.
- Combined search: Search for occurrences of IOCs or event fields together in the same analysis session. This method helps understand the malware’s lifecycle and behavior at different infection stages.
- Wildcard queries: Use wildcard characters like asterisk (*), caret (^), and dollar sign ($) to expand or narrow your search. This is especially useful when you have limited or partial threat information.
Overall, ANY.RUN Threat Intelligence Lookup has 30+ search fields:
<tbody> <tr>
<td>
File Hash </td>
<td>
Task Type </td>
<td>
OS </td>
<td>
Registry Key </td>
<td>
File Hash </td>
</tr>
<tr>
<td>
Threat Name </td>
<td>
Image Path </td>
<td>
Destination IP </td>
<td>
Destination IP Geo </td>
<td>
Threat Name </td>
</tr>
<tr>
<td>
Rule Threat Level </td>
<td>
Submission Country </td>
<td>
HTTP Response Content </td>
<td>
Registry Name </td>
<td>
Rule Threat Level </td>
</tr>
<tr>
<td>
Rule Name </td>
<td>
Command Line </td>
<td>
Destination Port </td>
<td>
File Name </td>
<td>
Rule Name </td>
</tr>
<tr>
<td>
Threat Level </td>
<td>
Date </td>
<td>
URL </td>
<td>
Suricata Class </td>
<td>
Threat Level </td>
</tr>
<tr>
<td>
MITRE </td>
<td>
Injected Flag </td>
<td>
Domain Name </td>
<td>
Registry Value </td>
<td>
MITRE </td>
</tr>
</tbody></table>
What is the source of our Threat Intelligence data?
Our Threat Intelligence data is sourced from around 14,000 daily tasks that our community of over 300,000 researchers run in ANY.RUN malware sandbox.
The ANY.RUN sandbox is fully interactive. This means that it allows security teams to analyze malware in a cloud environment that is similar to a local computer setup. They can engage with malware directly (unlock password-protected archives, click through installers, and trigger downloads of secondary payloads) and identify samples that evade automated detection systems.
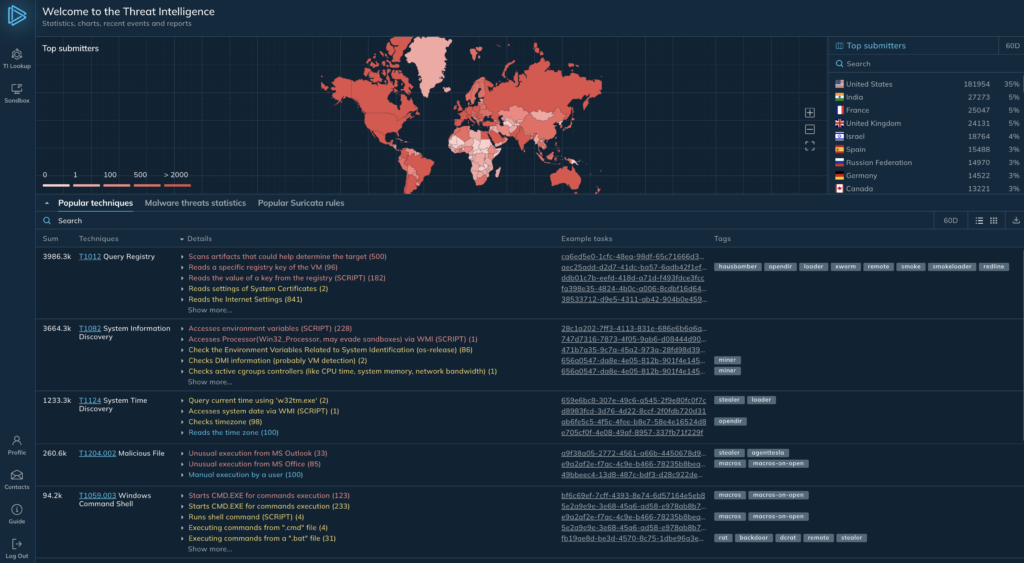 ANY.RUN IT Lookup gives access to the latest IOCs from millions of sandbox tasks
ANY.RUN IT Lookup gives access to the latest IOCs from millions of sandbox tasks Our sandbox enables analysts to examine malware for up to 20 minutes, handle files as large as 100MB, and configure environment settings: including custom VPN, MITM Proxy, and FakeNet — both for Windows and Linux operating systems. It provides real-time data to IOCs which makes our sandbox a go-to-tool among thousands of malware analysts — and every task they launch contributes to our Threat Intelligence Database.
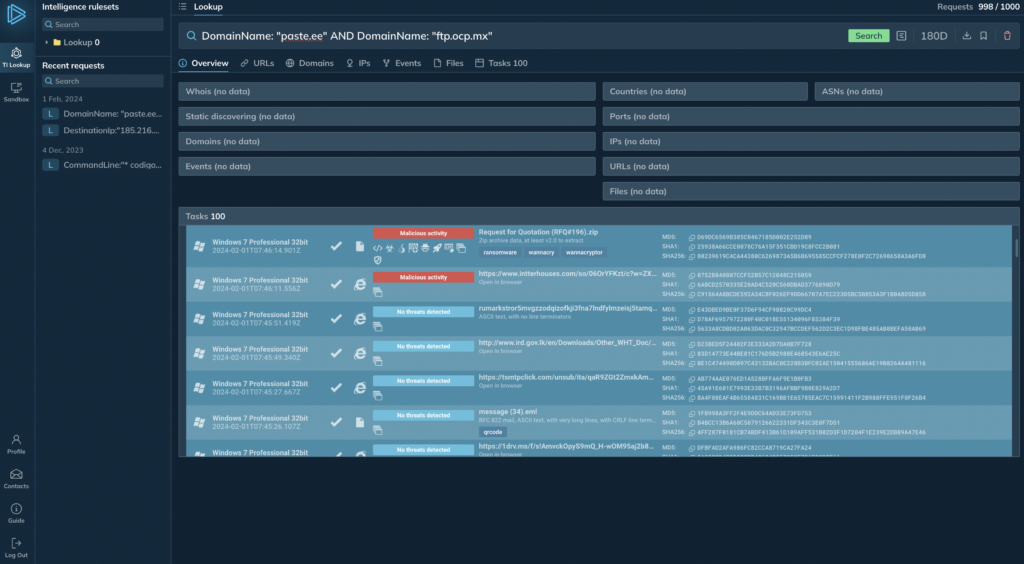 In TI Lookup you can directly access sandbox tasks where an IOC was recorded
In TI Lookup you can directly access sandbox tasks where an IOC was recordedBecause the ANY.RUN sandbox is closely integrated with the ANY.RUN Threat Intelligence Lookup, after identifying an indicator, you can directly access a recorded sandbox session where it was detected — this is crucial because you can get insights into malware behavior in real-life attack situations.
Get a demo of Threat Intelligence Lookup from our team
Get demoWhat are the benefits of ANY.RUN Threat Intelligence Lookup
ANY.RUN Threat Intelligence Lookup can help you meet compliance requirements by improving your cyberattack response capabilities. It also increases security ROI by reducing the time and effort needed to investigate and respond to threats.
- For security teams, using ANY.RUN TI Lookup means faster research, accurately and swiftly connecting isolated IOCs to specific threats or known malware campaigns, staying updated with emerging malware trends, and workflow flexibility — analysts can run searches using a web UI or our API.
- For organizations, ANY.RUN TI Lookup reduces risk by identifying threats as soon as they appear and proactively addressing them to prevent damage. TI Lookup also enables effective employee training—access to a comprehensive knowledge base with detailed insights into malware behavior helps to onboard new hires and junior researchers, growing their skills.
Interested in improving your security and incident response capabilities with ANY.RUN Threat Intelligence Lookup? We’re offering a trial with 20 search queries for existing ANY.RUN clients, who have purchased Searcher plan or above. We encourage all businesses to reach out to our sales team to gain access to the trial, find out more about the platform, or discuss pricing options.
The post Introducing ANY.RUN Threat Intelligence Lookup appeared first on ANY.RUN's Cybersecurity Blog.
Article Link: Introducing ANY.RUN Threat Intelligence Lookup - ANY.RUN's Cybersecurity Blog