Today, we’re excited to introduce our newest feature for our Autonomous SOC: AI Insights for Processes. Now, every alert from your endpoint security solutions — like CrowdStrike, SentinelOne, or Microsoft Defender — will be enriched with AI model insights (ChatGPT-like) directly on the Intezer Alert Report, based on different types of text-based evidence such as command lines and process trees.
Why AI Insights for Processes?
In today’s complex threat landscape, “Suspicious Activity” alerts can often be ambiguous, especially when they involve PowerShell, command line-based, or other fileless alerts. These types of alerts are particularly challenging to triage due to their elusive nature. AI Insights for Processes is our answer to this challenge, providing a human-like, natural language analysis of all textual-based information, ensuring that every piece of data is meticulously examined and understood.
Deciphering PowerShell and Fileless Alerts
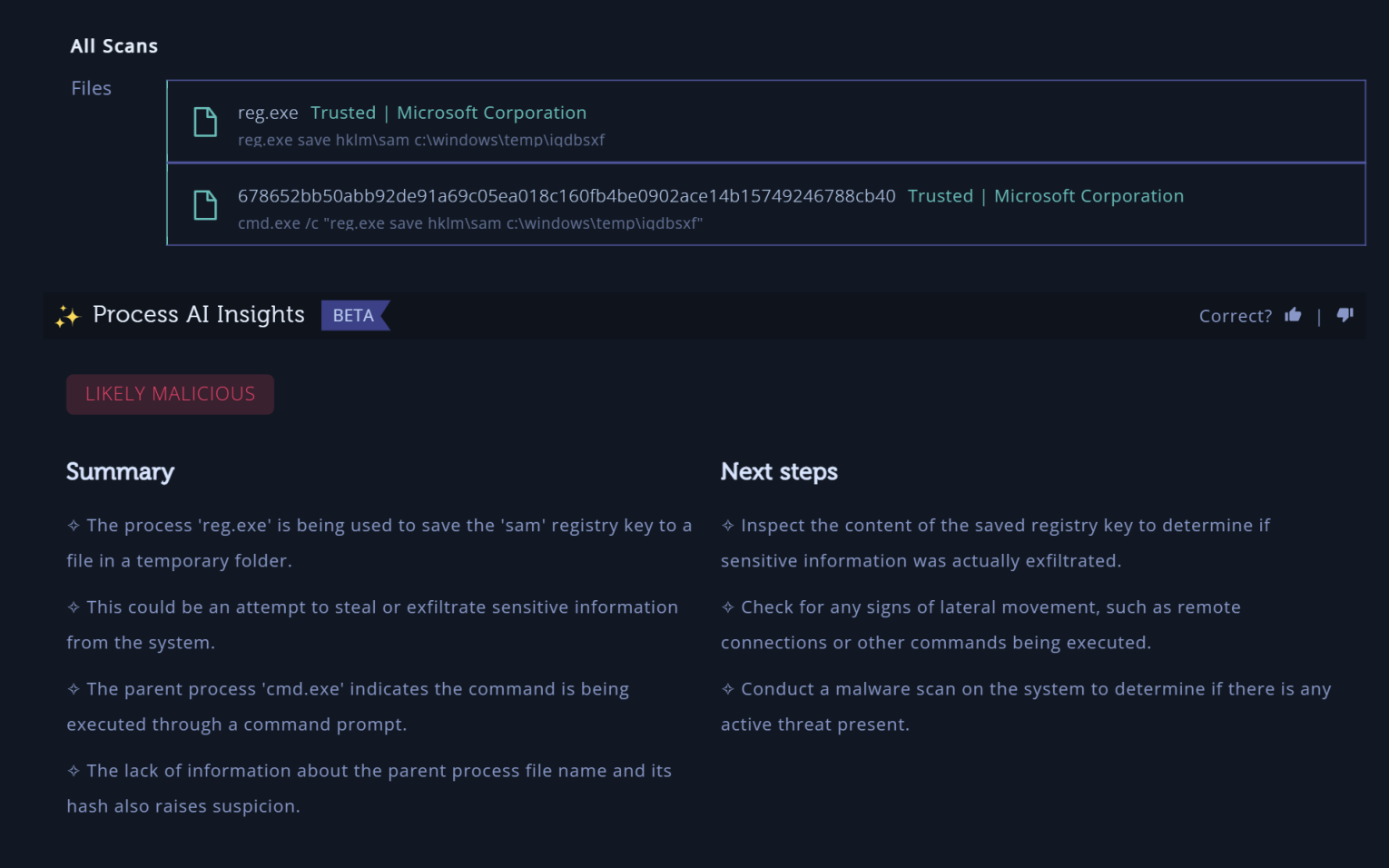
PowerShell and other command-line based alerts, often termed as fileless, are increasingly being used in sophisticated cyberattacks. Their ephemeral nature makes them hard to detect and even harder to analyze. With AI Insights for Processes, you can now get a clearer understanding of such alerts, ensuring that no threat, however stealthy, goes unnoticed. This adds to other existing analysis techniques we already use at Intezer to triage those alerts such as sandboxing, automated memory analysis, script analysis and more.
Benefits of AI Insights for Processes
- Natural Language Response in Autonomous SOC: The strength of AI Insights for Processes lies in its ability to provide a natural language type of response. This not only makes the insights easily understandable but also integrates seamlessly with Autonomous SOC, enhancing the overall user experience.
- Harnessing the Power of LLMs: By leveraging Large Language Models (LLMs), AI Insights for Processes excels in dissecting textual evidence like process names, file paths, and command lines. This deep dive ensures every nuance is captured and analyzed. It also adds another critical angle to the very robust file-based and binary code centric evidence collection and analysis Intezer provides.
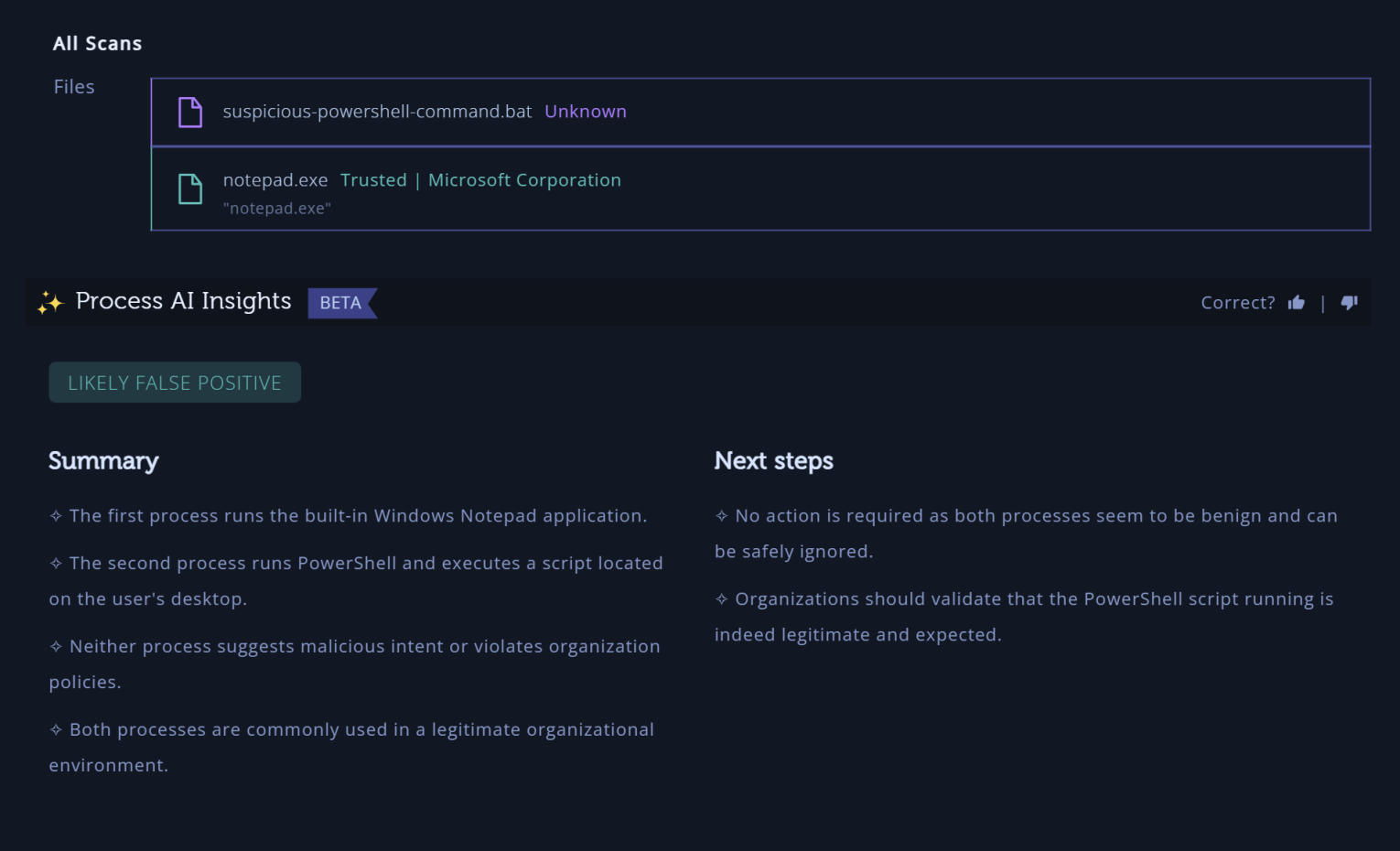
- Context-Rich Analysis: Drawing inspiration from real-world scenarios, AI Insights for Processes can, for instance, differentiate between a benign process like a Windows Notepad application and a potentially malicious one attempting to exfiltrate sensitive data. This depth of analysis ensures that security teams are equipped with actionable insights, from understanding the nature of the process to recommended next steps for mitigation.
How Does It Work?
The magic behind AI Insights for Processes lies in its integration of Large Language Models (LLMs). Here’s a step-by-step breakdown of its operation:
- Alert Ingestion: Once an alert is triggered from your endpoint security solution—be it Crowdstrike, SentinelOne, or Microsoft Defender—it’s immediately ingested into the Intezer system.
- Evidence Collection: In addition to the usual evidence Intezer is collecting from each alert, we also collect raw textual information from the endpoint security tool that triggered the original alert.
- Deep Dive Analysis: The system then begins its deep analysis, including all textual-based information associated with the alert. This includes process names, file paths, command lines, and more.
- Leveraging LLMs: Our proprietary integration of LLMs comes into play, dissecting the textual evidence with unparalleled precision. This ensures that every nuance, every subtle hint within the alert is captured.
- Natural Language Synthesis: Post-analysis, the insights are synthesized into a natural language format. This is where the human-like analysis shines, offering users a clear, easily understandable breakdown of the alert.
- Contextual Insights Generation: Drawing from a vast database of cybersecurity knowledge and real-world scenarios, the system provides context-rich insights. Whether it’s differentiating between a benign operation and a potential threat or offering actionable next steps, AI Insights for Processes ensures you have a comprehensive understanding of the alert.
- Integration with Intezer Alert Report: Finally, these detailed insights are seamlessly integrated into the Intezer Alert Report, ready for security teams to review, act upon, and archive.
The result? A transformative alert analysis experience that not only informs but empowers security teams to act swiftly and decisively.
Get Started
If you’re an existing Intezer Autonomous SOC customer, you’re all set! AI Insights will automatically enrich your Alert Report for vague alerts like “suspicious activity.”
New to Intezer?
- Book a demo to see AI Insights in action.
- Or, sign up for a trial and explore firsthand.
The post Introducing AI Insights for Processes: Triaging Command Lines and Other Text-Based Evidence appeared first on Intezer.
Article Link: AI Insights for Processes: Triaging Command Lines And More