In July, Intezer Analyze community detections included GonnaCry ransomware, the HawkEye malware kit, and BXAQ, the spyware the Chinese authorities have been installing onto foreign travelers’ Android devices.
1) GonnaCry [Link to Analysis]
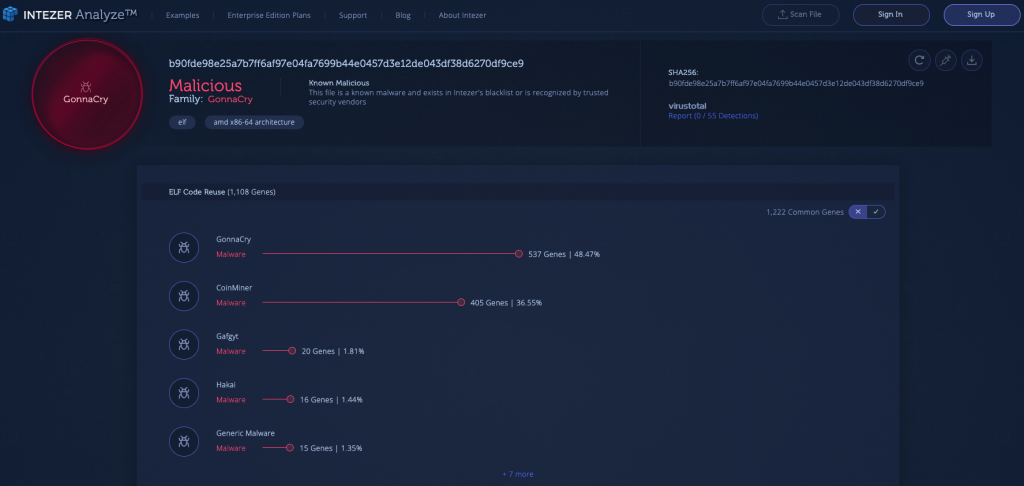
GonnaCry is an open-source ransomware designed for the Linux platform. GonnaCry’s source code is downloaded from GitHub and utilized by attackers to infect vulnerable Linux endpoints, by encrypting their file systems.
While it is not common to see ransomware targeting Linux users, the recent discovery of QNAPCrypt targeting Linux file storage servers is evidence that ransomware may become more prevalent on this operating system in the future.
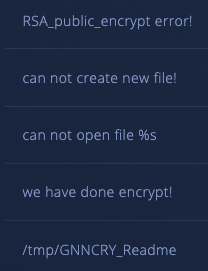
Despite having zero detections in VirusTotal, this Intezer Analyze community sample was immediately detected as malicious and classified as GonnaCry, based on code reuse. In fact, the file shares approximately 537 genes, or 48.47 percent of its code, with previously seen variants of GonnaCry. Even further, one of the malware’s strings, /tmp/GNNCRY_Readme, is further evidence that this sample is a type of GonnaCry ransomware.
2) HawkEye [Link to Analysis]
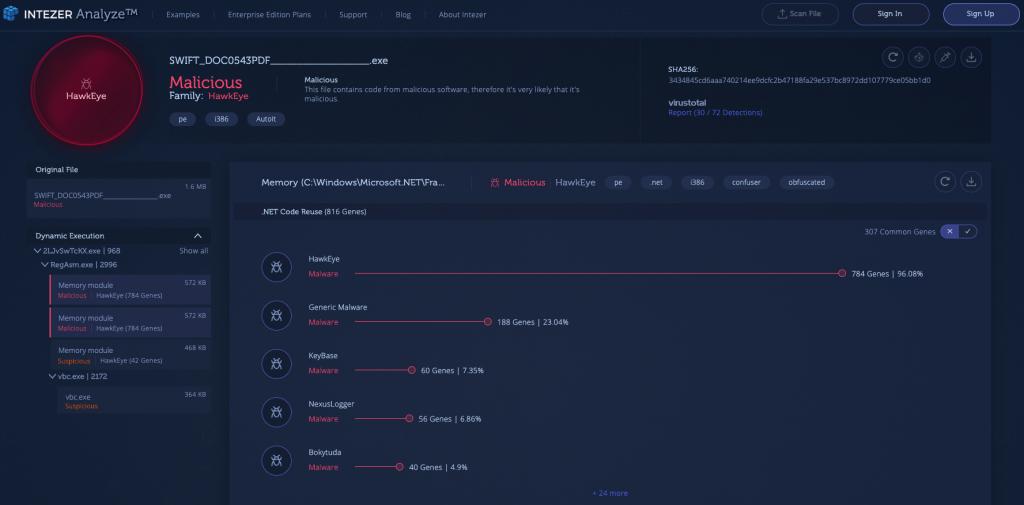
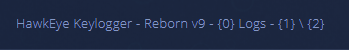
HawkEye is a malware kit used for stealing user credentials and other sensitive information. It is speculated by the infosec community that the malware has circulated since 2013. Since then, there have been continuous developments of HawkEye, and a new version of the malware, dubbed HawkEye Reborn v9, emerged in December 2018. HawkEye Reborn v9 can be seen within the strings of the community sample below.
According to researchers at Cisco Talos, HawkEye Reborn v9 can be purchased as an advanced monitoring solution, which is then typically spread via email phishing campaigns. After running an infected Microsoft Excel document, an additional payload will be downloaded containing a heavily obfuscated AutoIT script. The script will commence the RegASM.exe process, and through the use of process hollowing the script will inject the final payload into the running process.
This entire process can be observed in the analysis below, beginning with an AutoIT file acting as a packer, and ending with a malicious payload being extracted through dynamic unpacking.
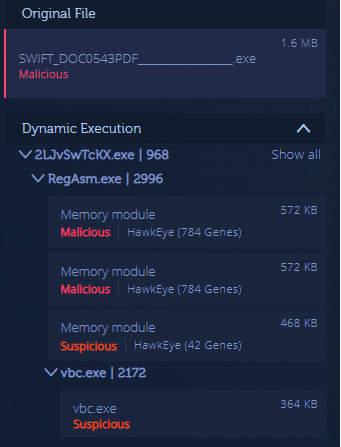
We can also see the use of the Nirsoft tool, WebBrowserPassView, as one of the information stealing tools deployed on the infected endpoint.
3) Sodinokibi [Link to Analysis]
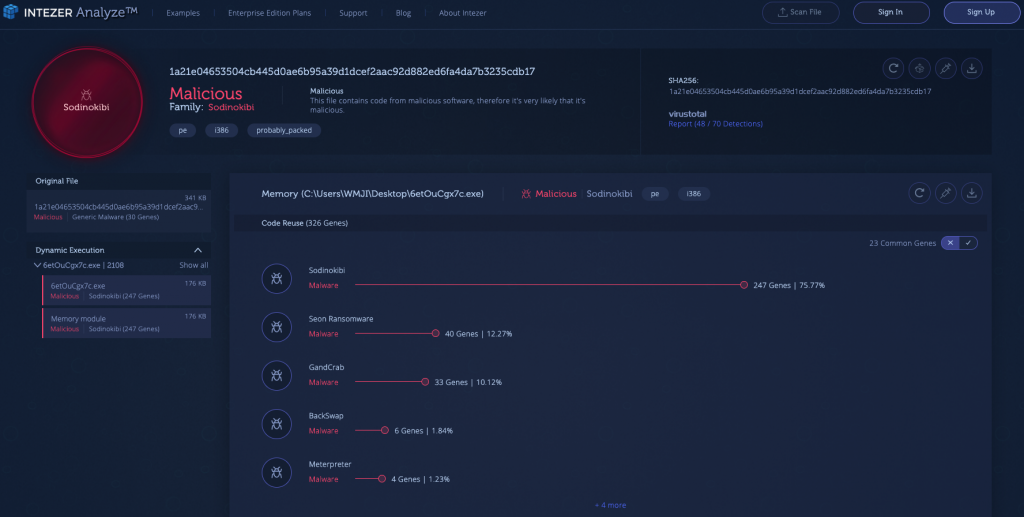
Immediately following the demise of the GandCrab operation in June, a new ransomware-as-a-service (RaaS) has emerged. Sodinokibi (aka Sodin and REvil) surfaced in April 2019, and has shown technical advancements over GandCrab. Still, many researchers have claimed that there might be a connection between the two ransomware families.
One small connection can be observed within the code similarities below. After automatic dynamic unpacking in Intezer Analyze, the file shares 33 genes, or approximately 10.12 percent of its code with GandCrab. Apart from spreading through phishing and malvertising, Sodinokibi also uses CVE-2018-8453 and CVE-2019-2725 to spread and elevate its privileges. The analysis below also proves that the malware uses a customized packer in order to evade detection and analysis.
Sodinokibi was one of the most common types of malware detected by the Intezer Analyze community in July. More about Sodinokibi and its relation to GandCrab in our recent blog post, titled Intezer Analyze Community: Mapping Code Connections Between Malware Samples.
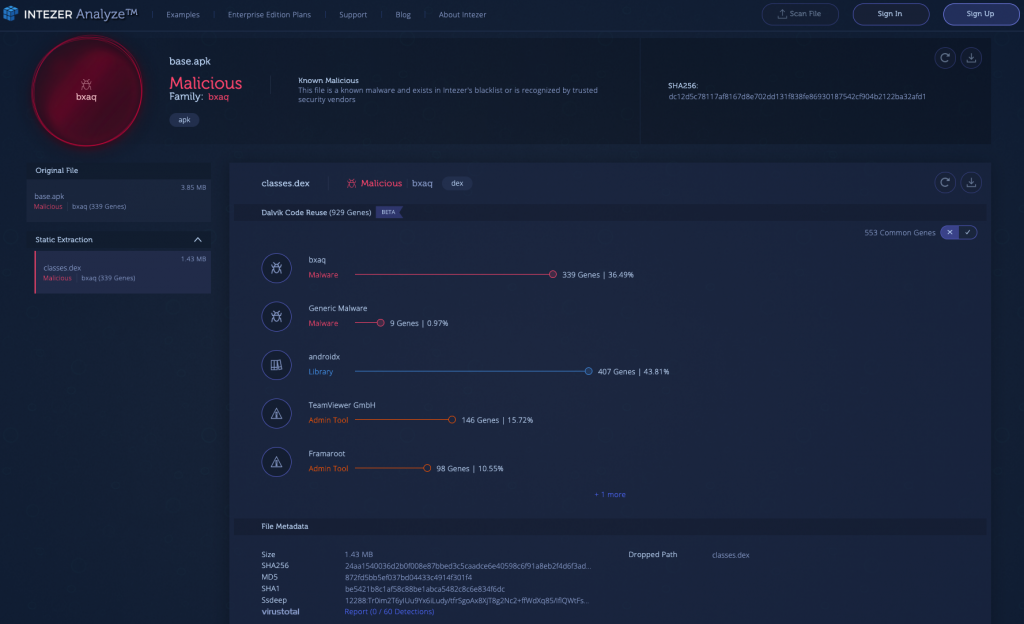
4) BXAQ [Link to Analysis]
The New York Times recently reported that the Chinese authorities have been installing malware onto foreign travelers’ Android devices at a border crossing in Xinjiang, an autonomous region in Northwestern China.
Once installed, the malware—or android package kit (APK)—named BXAQ, gains access to files, text messages, calendar entries, phone logs and more, and then uploads the data to a central server. Based on the type of content BXAQ searches for on a device, it can be discerned that the malware’s goal is to target people who oppose the Chinese government.
The analysis below shows an APK file which was classified as BXAQ, based on clear code connections (339 shared genes).
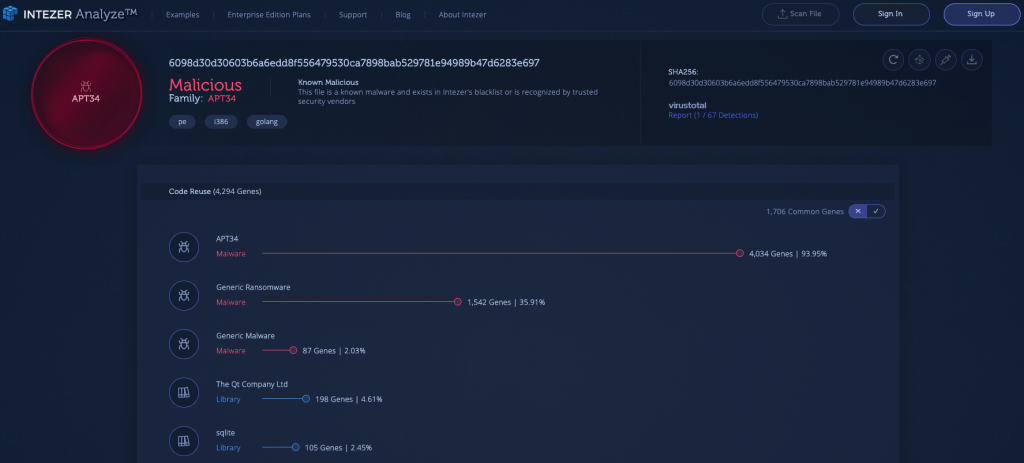
5) APT34 [Link to Analysis]
APT34 (aka OilRig and HelixKitten) is an Iranian threat actor who has targeted a variety of industries, including chemical, energy, financial services, government and telecommunications, since 2014. The group has largely focused its operations within the Middle East.
The sample below, which was uploaded to the Intezer Analyze community, was used in a recent phishing attack identified by FireEye. The malware was responsible for credential stealing.
The post Intezer Analyze Community: GonnaCry, HawkEye, BXAQ and More appeared first on Intezer.
Article Link: https://www.intezer.com/blog-intezer-analyze-community-july-2019/