International Authorities Strike Blow Against LockBit Ransomware: Operation Cronos
In a coordinated effort spanning 11 countries, law enforcement agencies have dealt a significant blow to the infamous LockBit ransomware operation through a joint initiative dubbed “Operation Cronos.”
Just recently, the LockBit group’s stronghold on their data leak website was wrested away by the United Kingdom’s National Crime Agency, in collaboration with the FBI and an international law enforcement task force.

Seizure announcement on LockBit’s leak site
A banner prominently displayed on the now-seized LockBit site bears the message: “This site is now under the control of The National Crime Agency of the UK, working in close cooperation with the FBI and the international law enforcement task force, ‘Operation Cronos’.
Operation Cronos
While access to LockBit’s leak site has been effectively cut off, displaying either a seizure banner or a connection error, some of the gang’s other dark web platforms remain operational.
Almost all LockBit’s leak site Onion links appear to be unreachable. However, currently, not all of them exhibit a seizure notice.
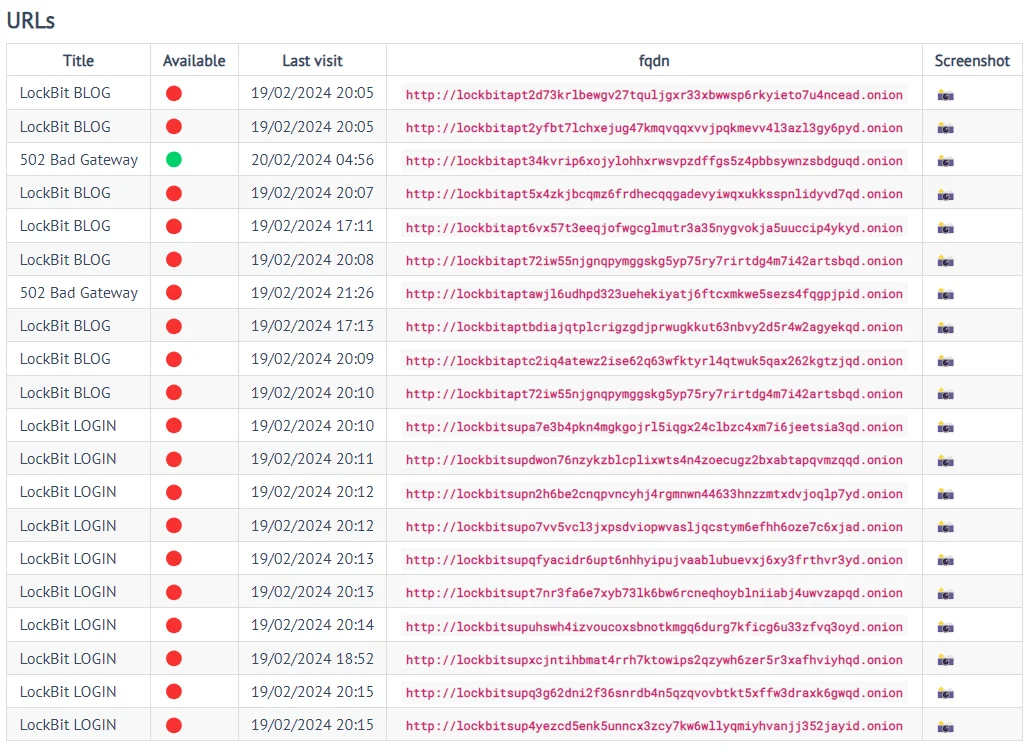
LockBit’s URLs by ransomware.live
Furthermore, the affiliate panel of LockBit has also been taken down by law enforcement, with a message indicating the seizure of LockBit’s source code, chats, and victim data.
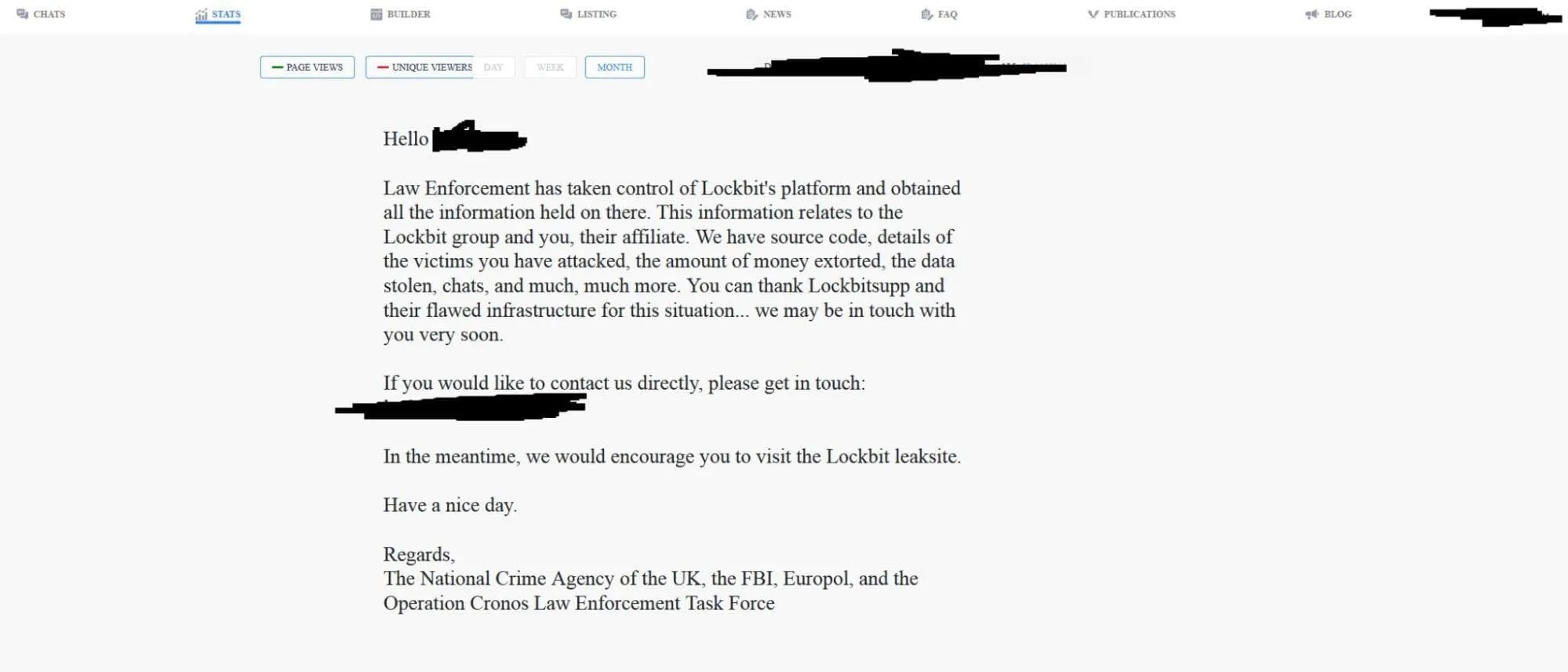
When a Lockbit affiliate tries to log into the LockBit panel, this is what they see. (vx-underground)
The message addressed to LockBit’s affiliates approximately reads: We have obtained all the information held on there, including details of the victims you have attacked, the amount of money extorted, the data stolen, chats, and much more.
In a revealing status update on the Tox messaging service, LockBitSupp, the operator behind the LockBit operation stated that the breach of their servers by the FBI via a PHP exploit.
“FBI f****d up servers via PHP, backup servers without PHP can’t be touched,” the translated message from LockBitSupp reads. As vx-underground shared in a tweet:
“ФБР уебали сервера через PHP, резервные сервера без PHP не тронуты”
Translated as: “The FBI f**** up servers using PHP, backup servers without PHP are not touched”
They also claim that the law enforcement agencies compromised them via exploiting a known vulnerability.
CVE-2023-3824 – Phar Directory Entries, Insufficient Length Check Leading to RCE
Allegedly, CVE-2023-3824 is used to take control of LockBit’s leak sites. The vulnerability occurs during the loading of a Phar (PHP Archive) file. Phar files are used in PHP for packaging entire applications or libraries into a single file for distribution. However, a flaw in specific PHP versions occurs while processing the directory entries within a Phar file.
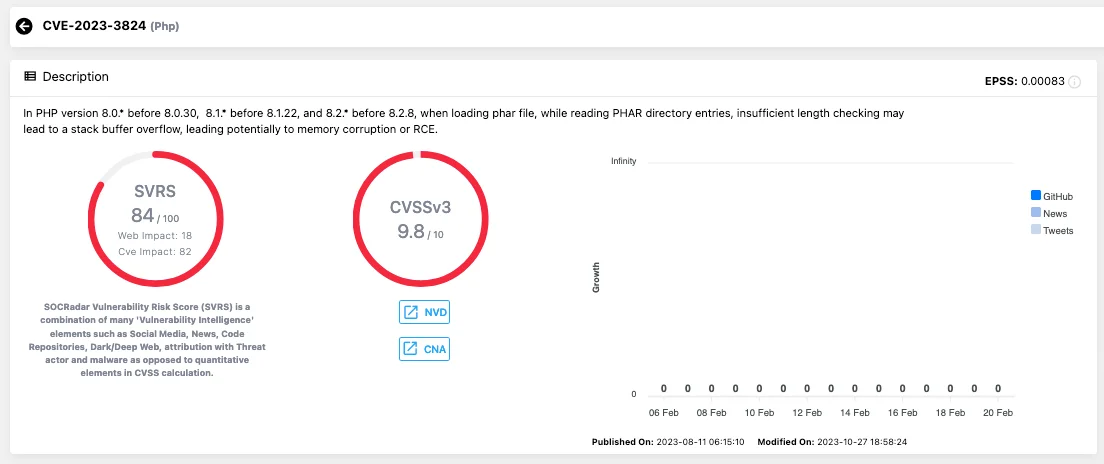
Vulnerability card of CVE-2023-3824, SOCRadar Vulnerability Intelligence
Insufficient length checking during this process can trigger a stack buffer overflow. A stack buffer overflow occurs when a program writes more data to a buffer, or memory space, than it can hold, leading to the corruption of adjacent memory locations. In the context of this vulnerability, the stack buffer overflow has the potential to cause memory corruption or allow for Remote Code Execution (RCE).
Remote Code Execution is a severe security risk where an attacker (FBI in this scenario) could exploit the vulnerability to execute arbitrary code on the affected system remotely. This could lead to various forms of malicious activity, such as installing malware, stealing sensitive data, or taking control of the affected system.
Another Blow to LockBit
Recently, LockBitSupp also found themselves banned from the XSS forum due to a breach of trust. Accusations arose suggesting that LockBit, having gained network access for encryption from another threat actor and collecting a ransom, failed to honor the agreed commission.
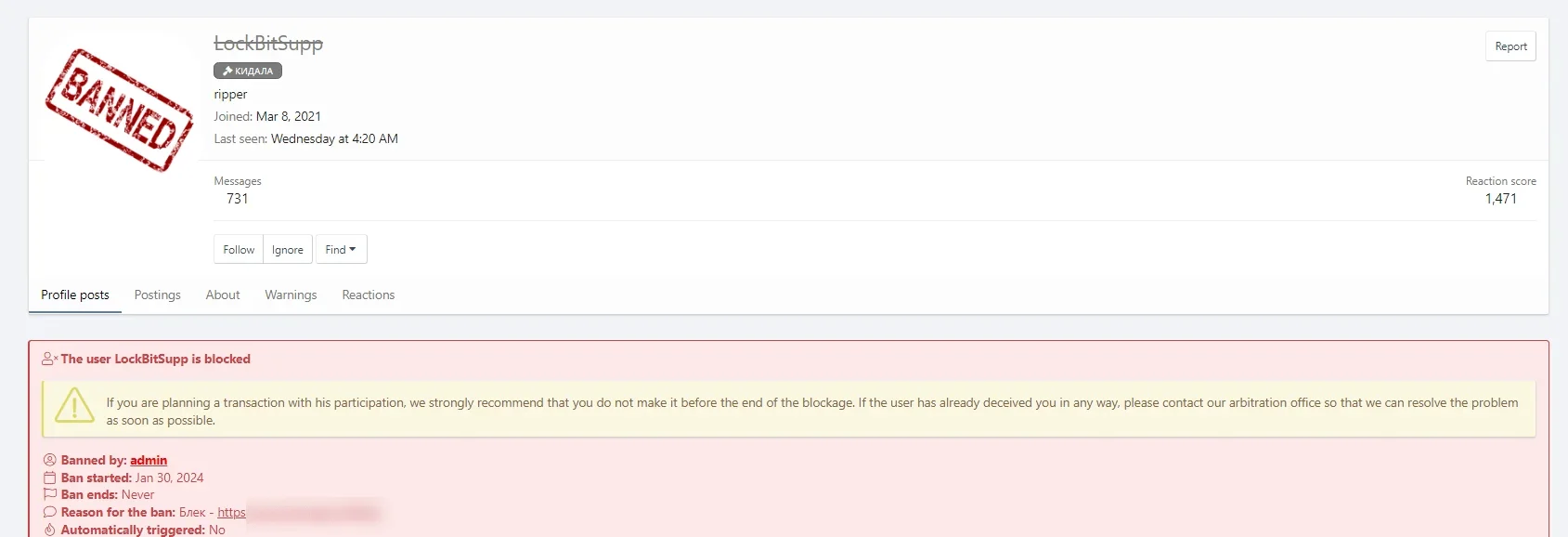
LockBit’s now banned account
Instead, they provided compensation solely for the network access. Subsequently, following the ban on the XSS forum, LockBit’s profile was also barred from Exploit. In other words, LockBit, which started to be ostracized within its own circles, now suffered another major blow. However, a question arises, did the escalation of this event also have an impact on the seizure of LockBit leak sites?
Conclusion
LockBit’s emergence as a Ransomware-as-a-Service (RaaS) group in 2019 signaled the onset of a campaign aimed at various prominent organizations globally. Throughout the past few years, LockBit has maintained its position as the preeminent and most prolific ransomware group, boasting the highest tally of victims.
Therefore, the takedown of LockBit signifies a significant victory in the ongoing battle against cybercrime, showcasing the effectiveness of international cooperation in combating such threats.
For more detailed information about the group, you can check out our relevant blog post.
Stay tuned for more updates on this evolving situation.
Article Link: https://socradar.io/international-authorities-strike-blow-against-lockbit-ransomware-operation-cronos/