Internals of DearCry Ransomware !
Ransomware used to target Microsoft Exchange Servers.

Recently attackers of APT groups started-off targeting Microsoft Exchange Servers after the flaw( 0day ) in the Microsoft exchange servers was published on github. As the 0day exploit is being published on github attackers of APT groups started hacking on MS-Exchange servers by scanning the servers for the 0day vulnerability and ransom’ing servers with the DearCry ransomware. In this blog i will be walking you through the reverse engineering of DearCry ransom where you will be seeing me reversing DearCry ransom for Static and Dynamic Analysis.
Static and Dynamic Analysis
Static Analysis (Basic)
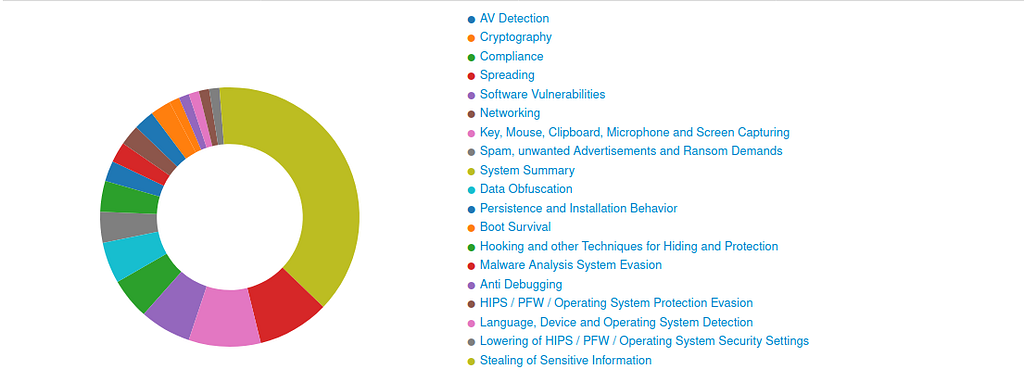 Signature Overview.
Signature Overview.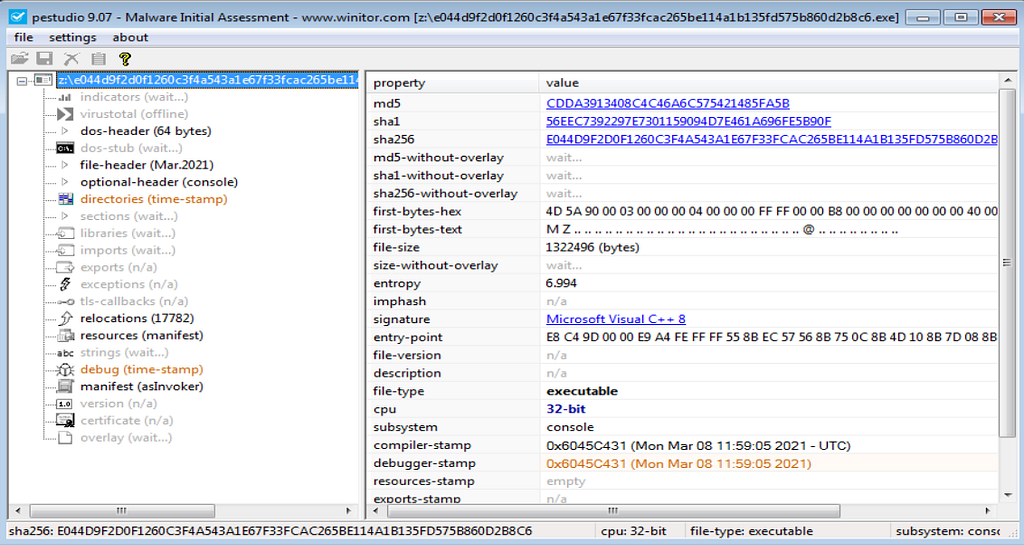 PE Studio View of DearCry Ransomware.
PE Studio View of DearCry Ransomware.Static Analysis (Advanced)
Starting off from exports in DearCry Ransomware which is only one.
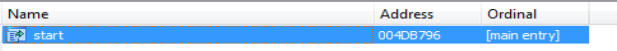 Start is the only export in DearCry Ransomware.
Start is the only export in DearCry Ransomware.start function
There are two function in the start function, one is “Anti_Analysis_and_anti_VM_checks” and another one is “main _app” function.
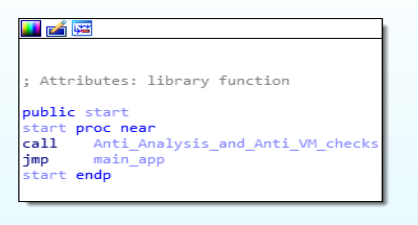
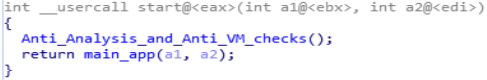 Disassembly Call Graph and code of start function.
Disassembly Call Graph and code of start function.Anti_Analysis_and_anti_VM_checks function
In this function, functions like GetSystemTimeAsFileTime, GetCurrentProcessId, GetCurrentThreadId are being used for anti analysis purpose.
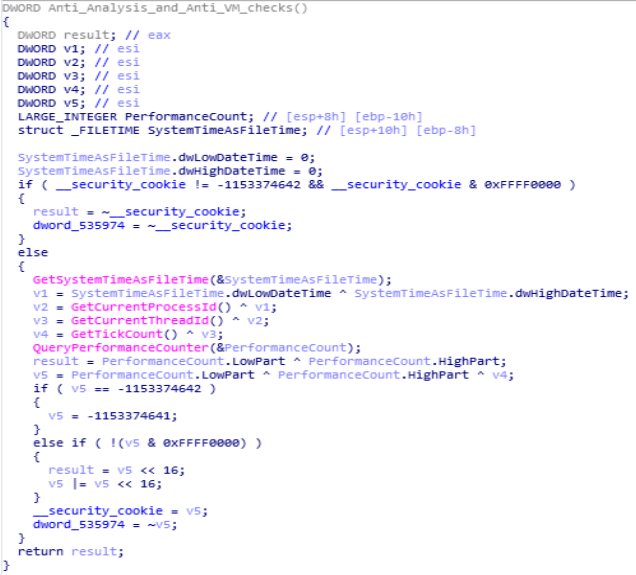
 Code and Call Graph of Anti_Analysis_and_anti_VM_checks function.
Code and Call Graph of Anti_Analysis_and_anti_VM_checks function.main_app function
It’s the main function, where firstly the heap is being created using “heap_create” , throughout this main module there is the functions like “anti_dbging_laoding_dlls_checks” & “anti_dbg_load_dlls_thread_ops” are being used as anti-debugging and for loading dlls and handling threads operations.
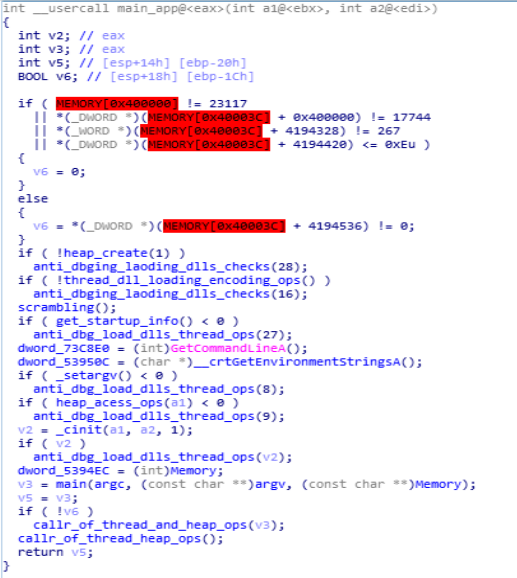 Disassembly Call Graph and code of main_app function.
Disassembly Call Graph and code of main_app function.anti_dbging_loading_dlls_checks function
This module makes calls to “callr_anti_debigging_checks_and_loading_dlls” & what this module does is that same kinda behaviour analysis on system environment on which the ransom is being debugged and the same function load dlls. & another function which is being called in this module is that “load_dlls_callr” which is the deployed for the loading dlls that loads dynamic linked library in the infected system.
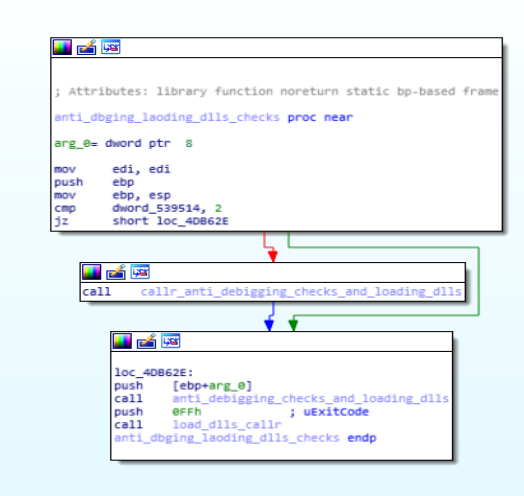
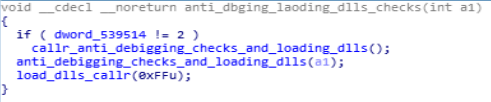 Disassembly Call Graph and code of anti_dbging_loading_dlls_checks function.
Disassembly Call Graph and code of anti_dbging_loading_dlls_checks function.scrambling function
what this module does is that it scramble up the data present in the infected system.
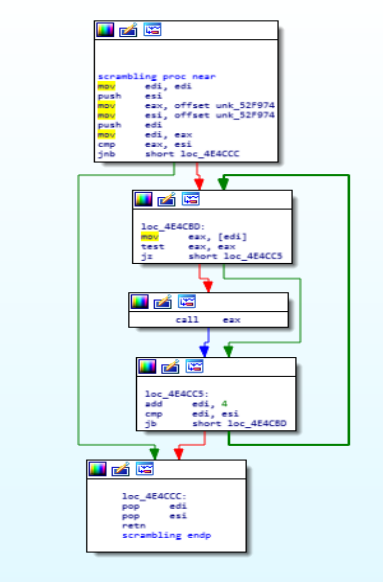
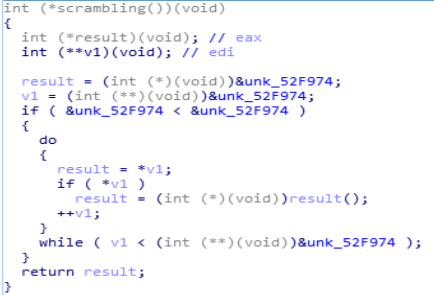 Disassembly Call Graph and code of scrambling function.
Disassembly Call Graph and code of scrambling function.anti_dbg_load_dlls_thread_ops function
In this module, mainly what happens in this is, it has three functions “callr_anti_debigging_checks_and_loading_dlls” , “anti_debigging_checks_and_loading_dlls” & “thread_ops”. Where first function in it is a function which calls a function “anti_debigging_checks_and_loading_dlls” in which the anti debugging checks & loading of dlls happens. Lastly, the function “thread_ops” is being deployed in this function where the thread operations happens.
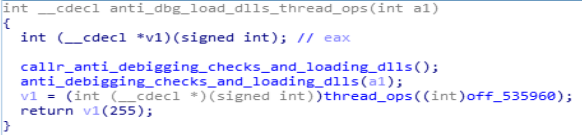 Disassembly Call Graph and code of anti_dbg_load_dlls_thread_ops function.
Disassembly Call Graph and code of anti_dbg_load_dlls_thread_ops function.anti_debugging_checks_and_loading_dlls function
In this function, using “anti_debugging_checks” the anti debugging happens whereas using the function “main_app_of_loading_dlls” dlls are being loaded.
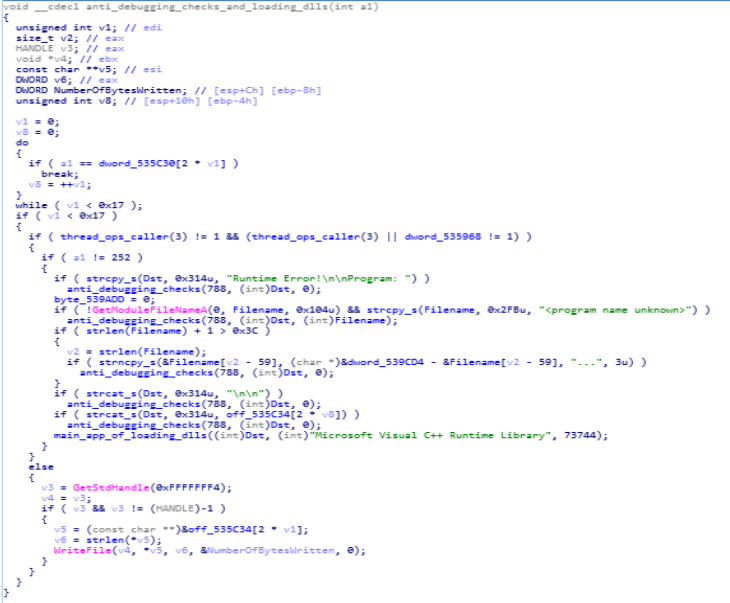 Disassembly Call Graph and code of anti_debugging_checks_and_loading_dlls function.
Disassembly Call Graph and code of anti_debugging_checks_and_loading_dlls function.thread_ops function
To get the thread value functions like TlsGetValue is being used whereas using the GetModuleHandleW function handle is being retrieved using this function & using “load_module_after_sleep” module is being loaded after execution of sleep.
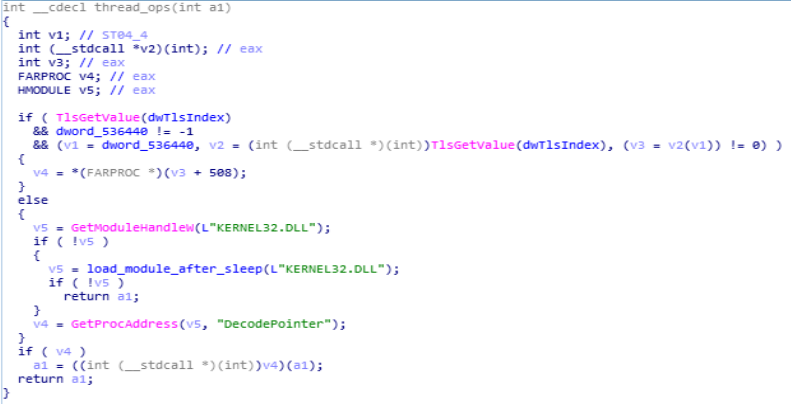
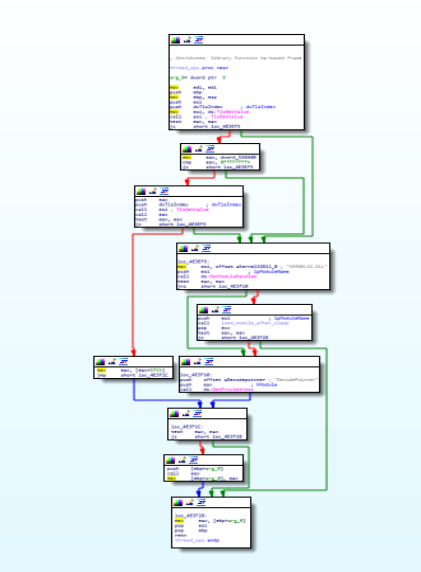 Disassembly Call Graph and code of thread_ops function.
Disassembly Call Graph and code of thread_ops function.main function
In the main function, fake “msupdate” service is being started whereas their are two functions in this module which are “RSA_encryption_ops” and “encryption_service_ops” are being used.
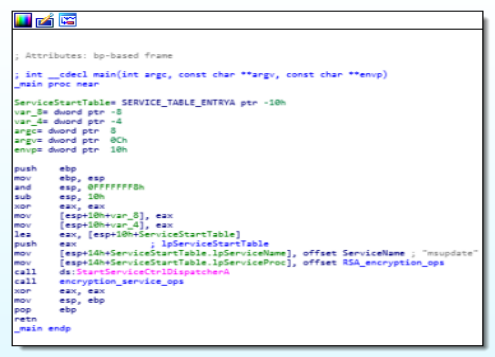
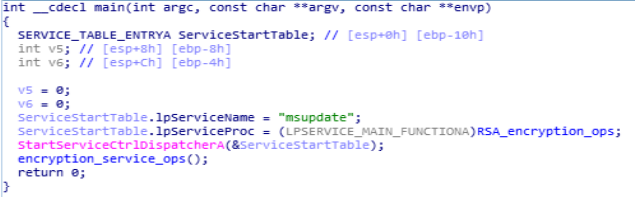 Disassembly Call Graph and code of main function.
Disassembly Call Graph and code of main function.RSA_encryption_ops function
In this function, “encryption_service_ops” is used for starting the service.
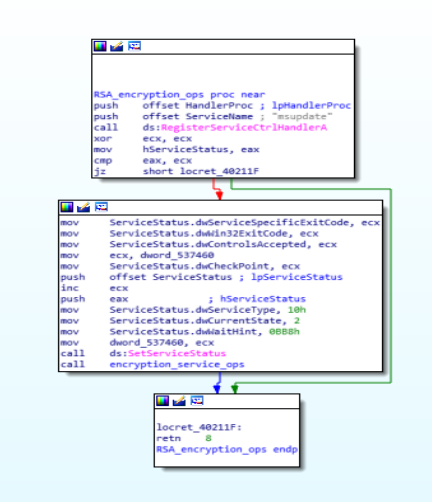
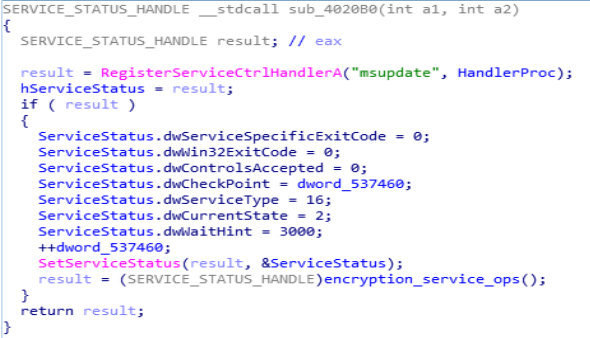 Disassembly Call Graph and code of RSA_encryption_ops function.
Disassembly Call Graph and code of RSA_encryption_ops function.encryption_service_ops function
This the function which is being used for starting the services for encrypting data on infected system.
<a href="https://medium.com/media/715dd2484cddef923c57eed66550bb3c/href">https://medium.com/media/715dd2484cddef923c57eed66550bb3c/href</a> Graph of encryption_service_ops function.
Graph of encryption_service_ops function.Some of the other interesting functions related to encryption/decryption keys operations , encryption/decryption operations.
exporting_key function
This function is used for exporting key for encryption key using CryptExportKey().
<a href="https://medium.com/media/5fd5757b658fdaa0eaa09951ad0516c9/href">https://medium.com/media/5fd5757b658fdaa0eaa09951ad0516c9/href</a>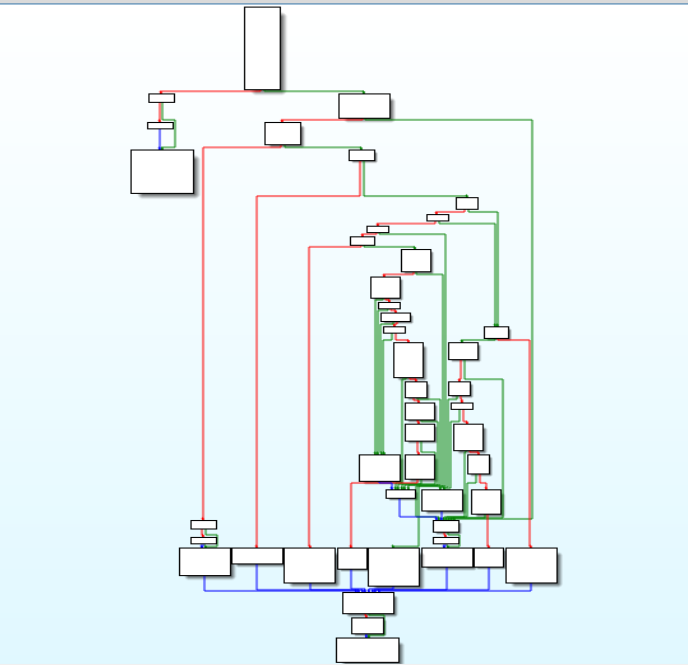 Disassembly Graph of exporting_key function.
Disassembly Graph of exporting_key function.encryption_decryption function
In this function, the encryption and decryption of data of victim infected system is being handled.
<a href="https://medium.com/media/337d6ac0c4d1cf3b7a6274b9d750070d/href">https://medium.com/media/337d6ac0c4d1cf3b7a6274b9d750070d/href</a>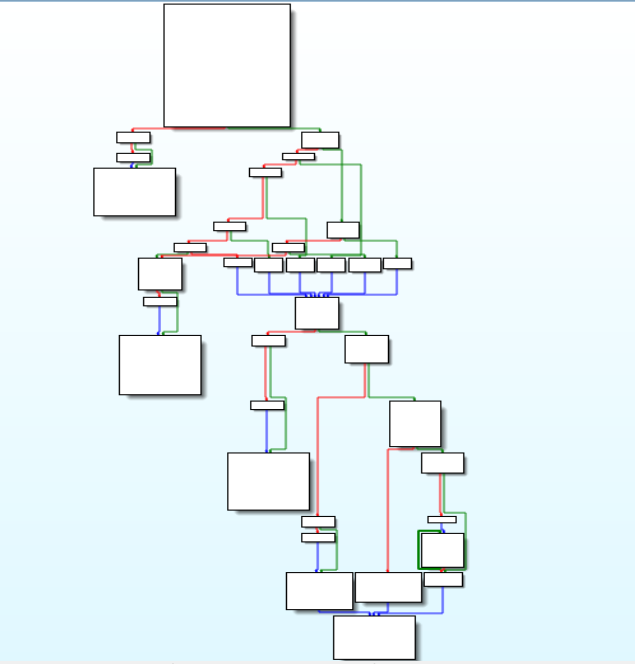 Disassembly Graph of encryption_decryption function.
Disassembly Graph of encryption_decryption function.key_ops function
This function is being used for carrying out key operation.
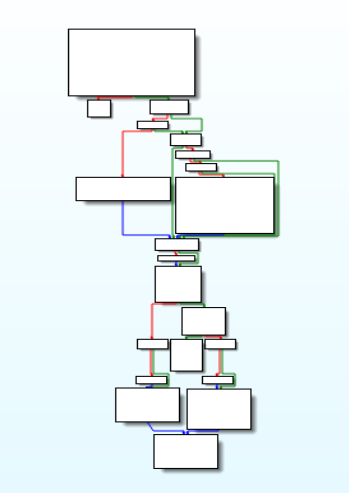
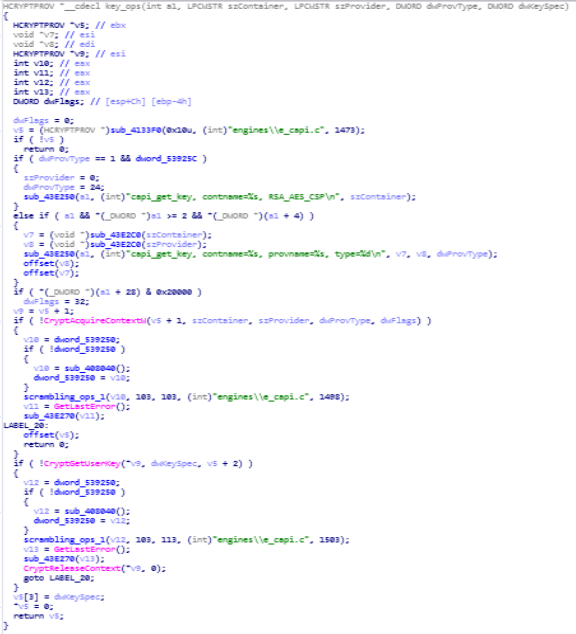 Disassembly Graph of key_ops function.
Disassembly Graph of key_ops function.private_key_generation function
This function is being deployed for generating private key.
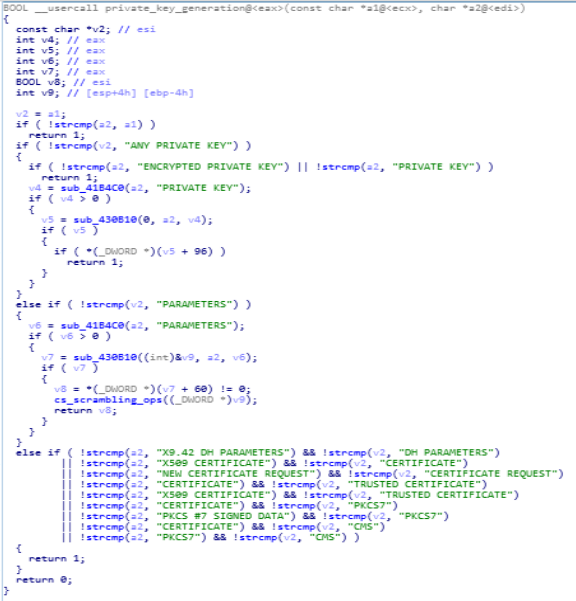 Disassembly Graph of private_key_generation function.
Disassembly Graph of private_key_generation function.Algorithms used for DearCry Ransomware are RSA and CALG_SHA1 .
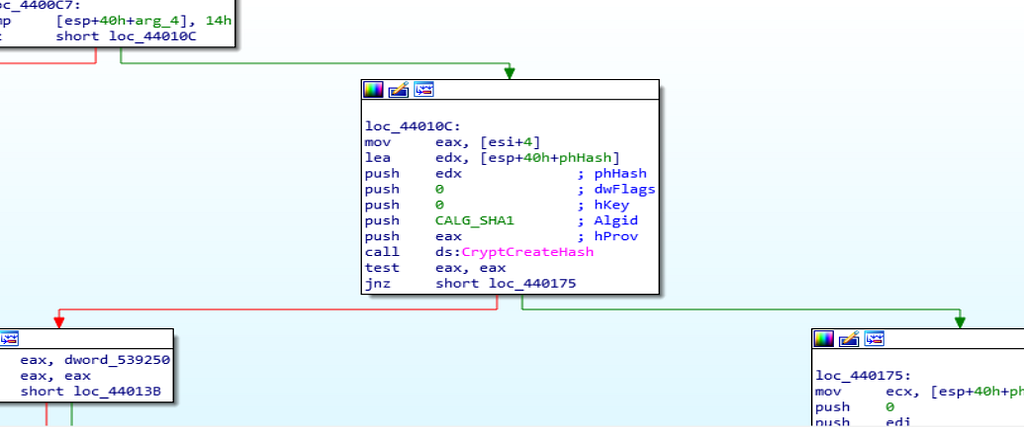 Use of CALG_SHA1 algorithm in DearCry Ransomware.
Use of CALG_SHA1 algorithm in DearCry Ransomware.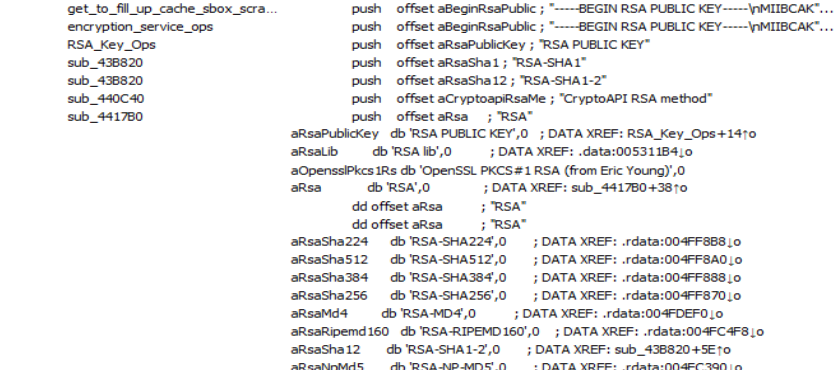 Use of RSA algorithm in DearCry Ransomware.
Use of RSA algorithm in DearCry Ransomware.Dynamic Analysis (Advanced)
For the DearCry Ransom i had set the following breakpoints:-
…..:- start
……:- main_app
……:- exporting_key_function
……:- fill_up_cache and other following breakpoints are shown below
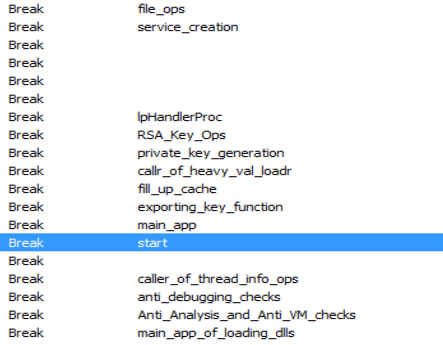 Breakpoints set for dynamic analysis of DearCry Ransom.
Breakpoints set for dynamic analysis of DearCry Ransom.First off the debugger hits at the function in the start module which is “Anti_Analysis_and_Anti_VM_checks”.
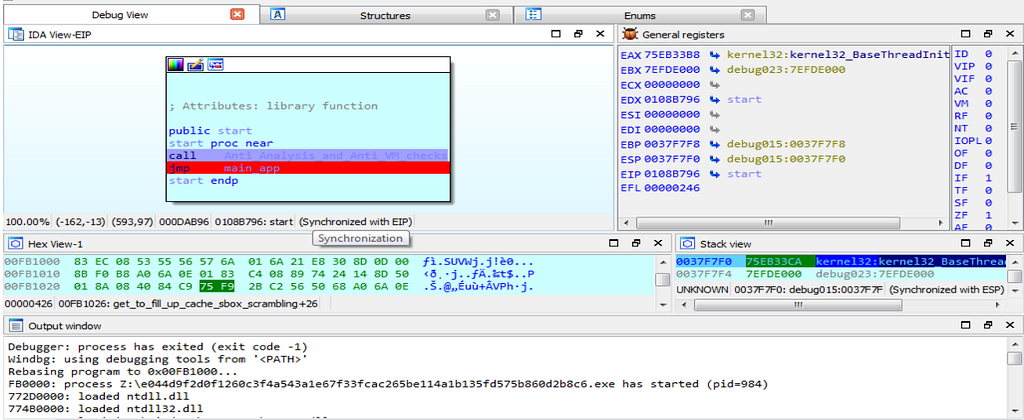
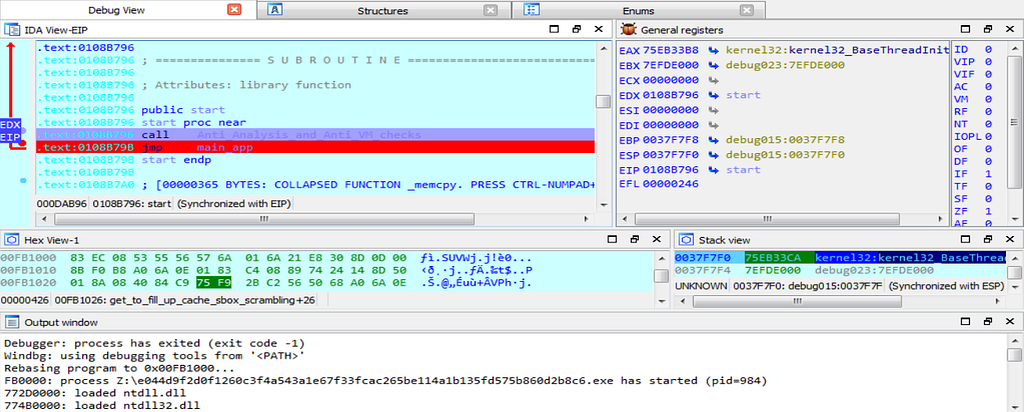 Graph and Text view of Debug View during dynamic analysis of DearCry Ransomware.
Graph and Text view of Debug View during dynamic analysis of DearCry Ransomware.As we debug the DearCry Ransom further we will see it falling in the “Anti_Analysis_and_Anti_VM_checks” function.
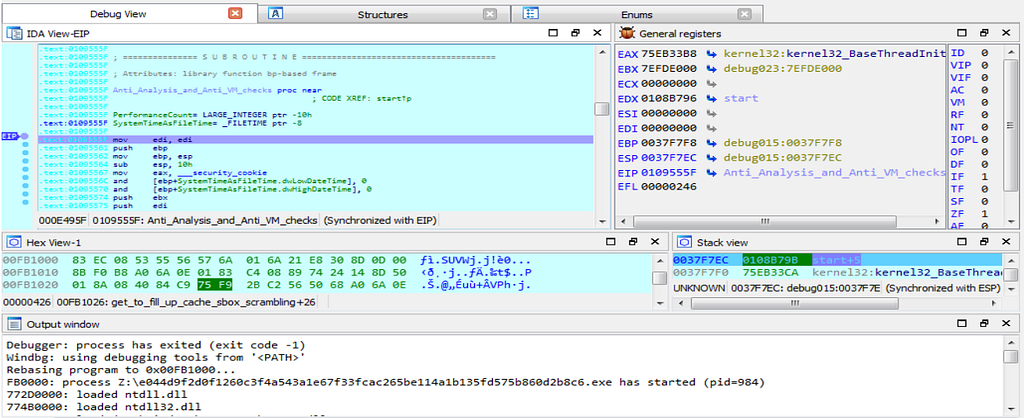
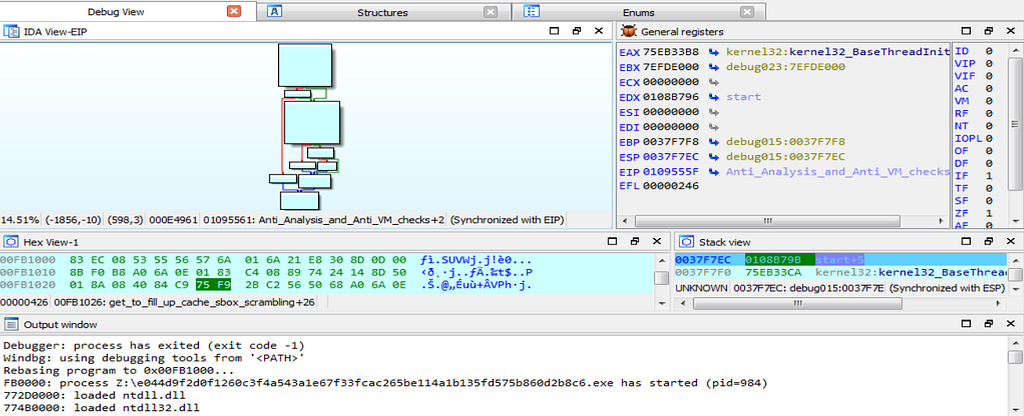
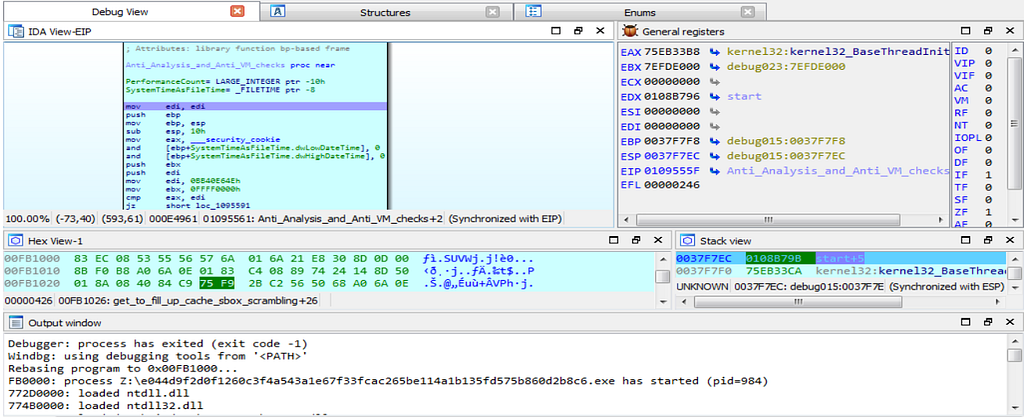 Here is the Text and Graph View of Debugger falling inside the Anti_Analysis_and_Anti_VM_checks function is shown.
Here is the Text and Graph View of Debugger falling inside the Anti_Analysis_and_Anti_VM_checks function is shown.In further debugging we will see that the debugger hits at the function “main_app” present in the start function.
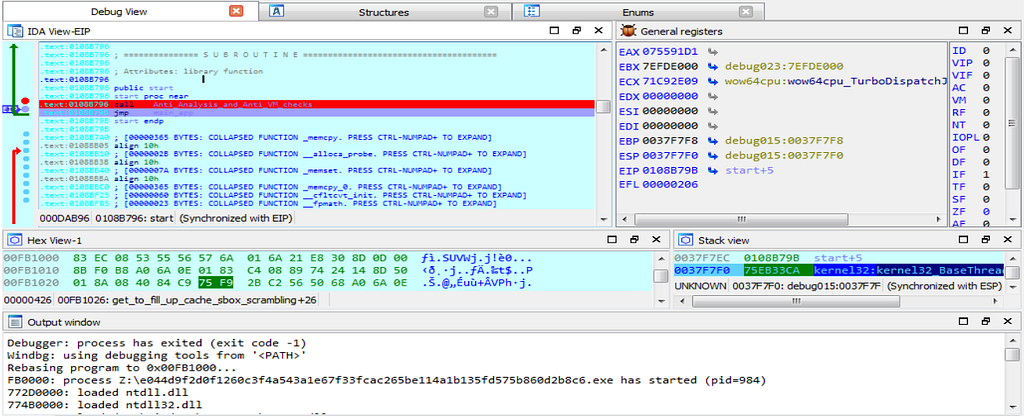
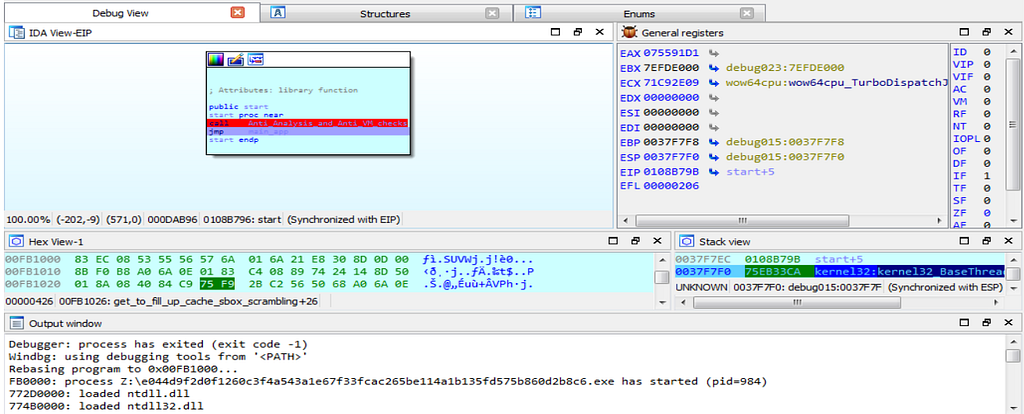 Here is the Text and Graph view of debugger hitting at the main_app function is shown.
Here is the Text and Graph view of debugger hitting at the main_app function is shown.As debugging further DearCry Ransom, we see that debugger jumps inside the main_app function.
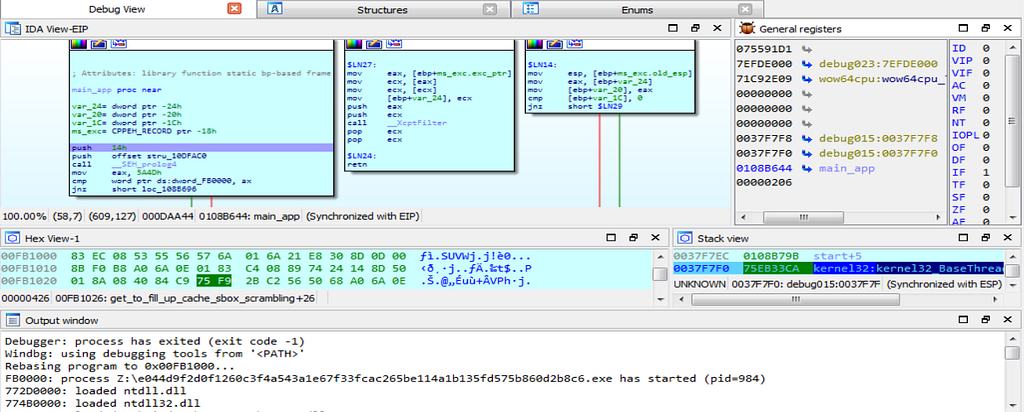
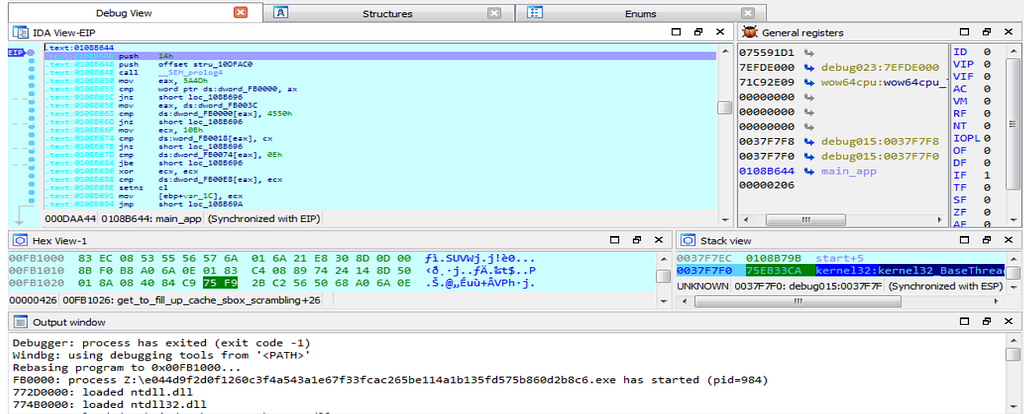 Here is the Text and Graph view of debugger jumping inside the main_app function.
Here is the Text and Graph view of debugger jumping inside the main_app function.on further debugging an exception is raised as shown.
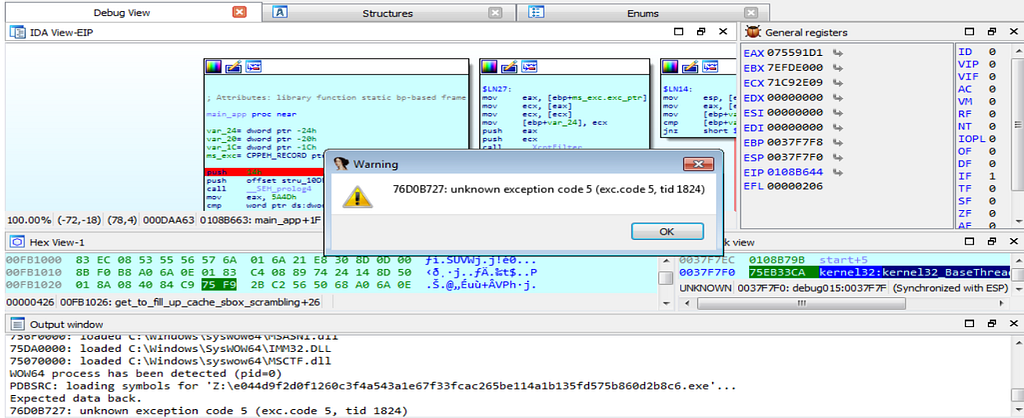 Exception Raised during debugging.
Exception Raised during debugging.On the further debugging, debugger hits inside the following database as shown below.
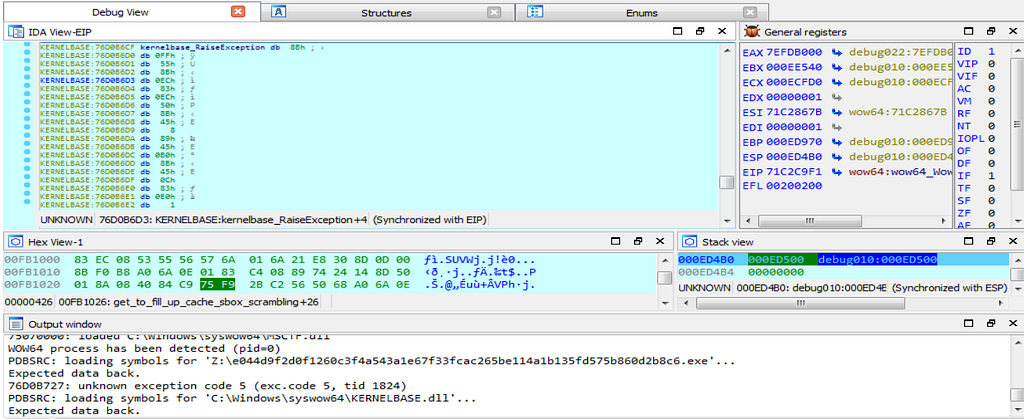 Debugger hitting inside the database.
Debugger hitting inside the database.Then after that, debugger hits at the function “fill_up_cache”.
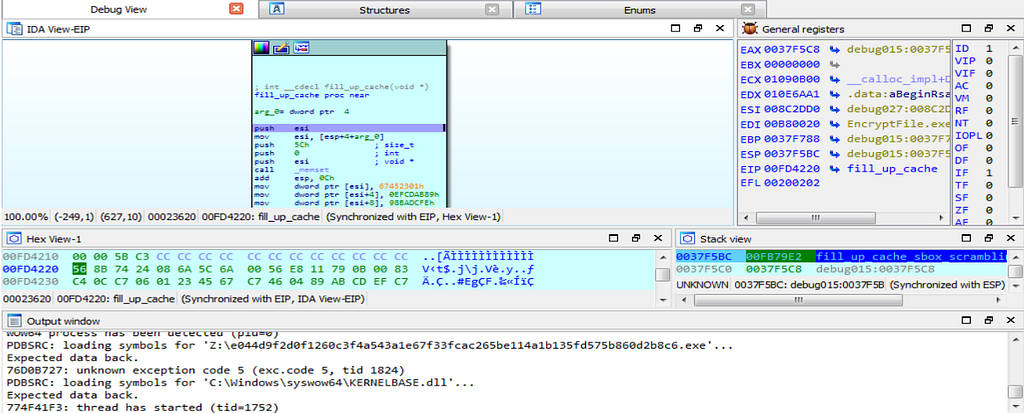 Debugger hits at the function “fill_up_the_cache”.
Debugger hits at the function “fill_up_the_cache”.Then soon after that the debugger hits at the function “callr_of_heavy_val_loader” who function is to load heavy bits in the cache of infected victim system.
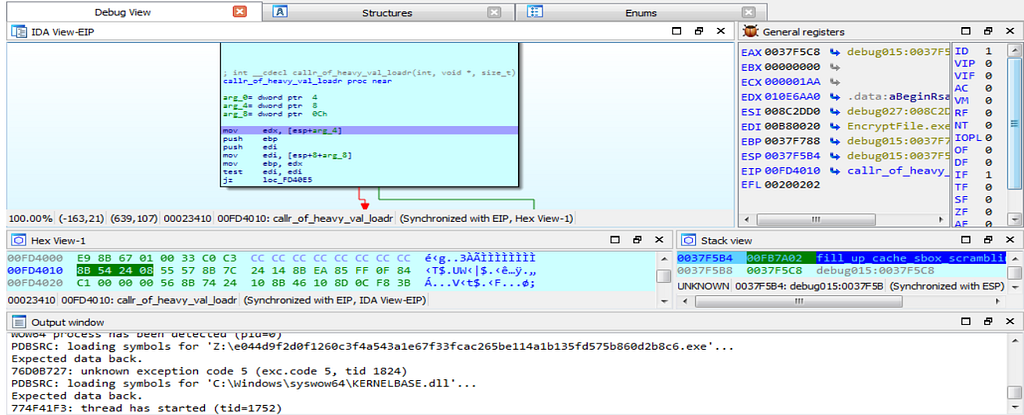 Debugger hitting at the callr_of_heavy_vals_loader” function.
Debugger hitting at the callr_of_heavy_vals_loader” function.Then after that the debugger hits at the function “RSA_Key_Ops” in which the encryption/decryption key operations happens on the system using RSA algorithm.
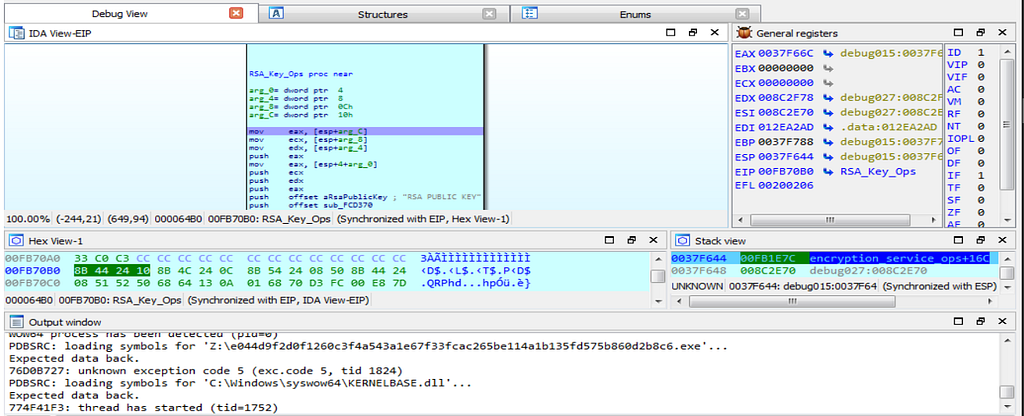 Debugger jumping into the RSA_Key_Ops function.
Debugger jumping into the RSA_Key_Ops function.As debugging continues, the debugger hits at the “private_key_generation” function in which the private key is being generated.
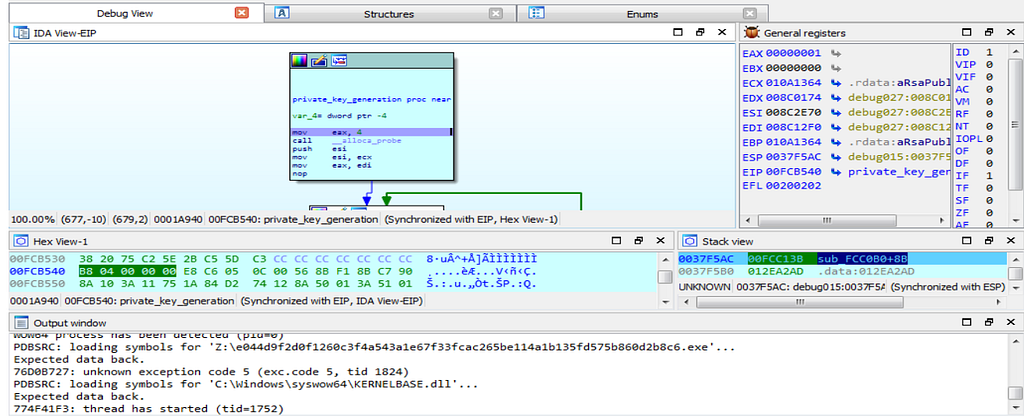 Debugger hits at the function “private_key_generation”.
Debugger hits at the function “private_key_generation”.As the move in further debugging , we encounter with debugger hitting at the “file_ops” function.
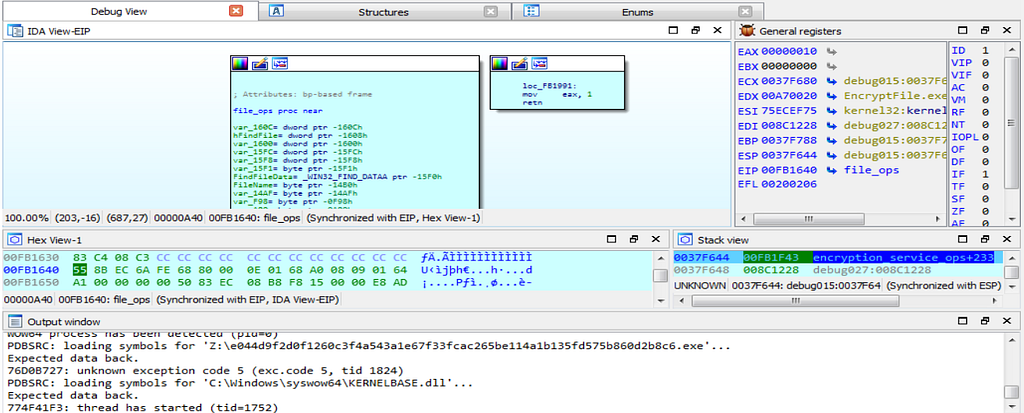 Debugger hits at the “file_ops” function.
Debugger hits at the “file_ops” function.Indicators of Compromise (IOCs) & Detection
Att&ck IDs
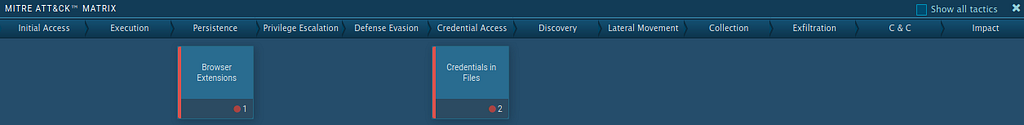 Att&ck IDs detected by Any Run Sandbox.
Att&ck IDs detected by Any Run Sandbox.Att&ck Techniques
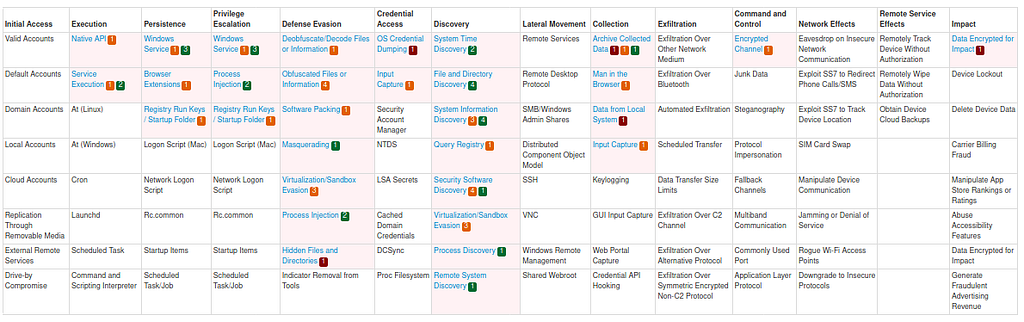 Att&ck Mitre Techniques produced by Joe Sandbox.
Att&ck Mitre Techniques produced by Joe Sandbox.Samples from Report
MD5: cdda3913408c4c46a6c575421485fa5b .
SHA-1: 56eec7392297e7301159094d7e461a696fe5b90f
SHA-256:
e044d9f2d0f1260c3f4a543a1e67f33fcac265be114a1b135fd575b860d2b8c6
YARA Signature
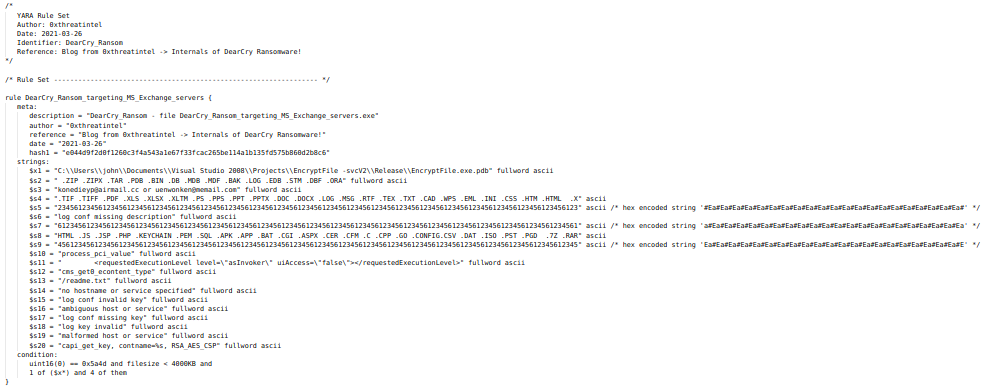 Yara Signature for DearCry Ransomware.
Yara Signature for DearCry Ransomware.Thanks for reading.
Article Link: https://0xthreatintel.medium.com/internals-of-dearcry-ransomware-507b84ae9ba8?source=rss-a15183055fd6------2