Static & Dynamic Analysis

Introduction
In this particular blog, i will walk you through the internals of Stop Ransomware where we will see the static as well as dynamic analysis of Stop Ransomware.
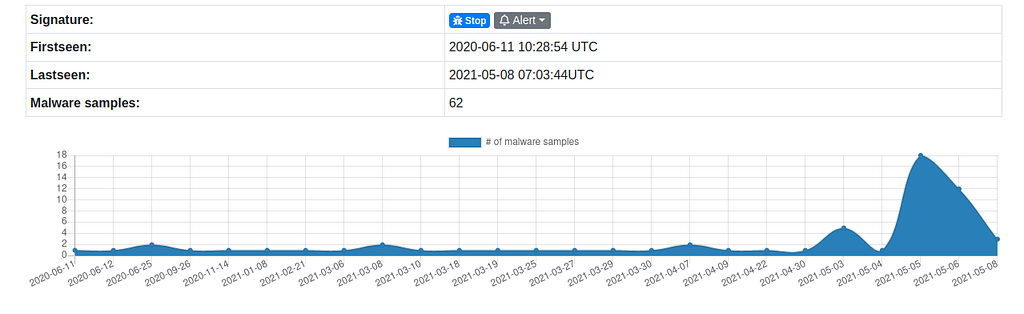 Graph of Stop Ransomware samples submitted in 2020–2021 on abuse.ch.
Graph of Stop Ransomware samples submitted in 2020–2021 on abuse.ch.Analysis
Static Analysis (Basic)
File Information
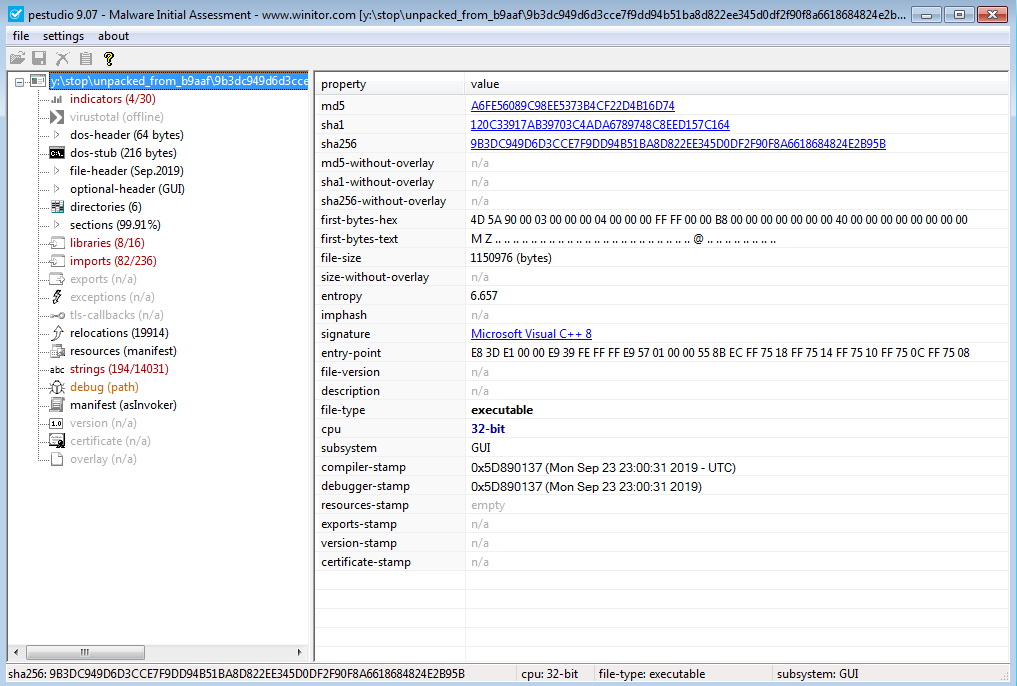 Information Gathering on Sample.
Information Gathering on Sample.Static Analysis (Advanced)
In this sample there is only one export which is start function.
start function
In this function there is calls to two functions is being made. One is “canary_cookie_calc___bof_mitigation” and other is “call_to_win_main” function.
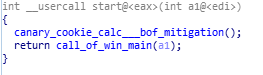
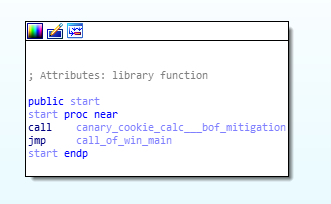 reversed code and disassembly call graph of start function.
reversed code and disassembly call graph of start function.canary_cookie_calc___bof_mitigation function
In this function calculation of canary cookies and buffer overflow mitigation is being done.
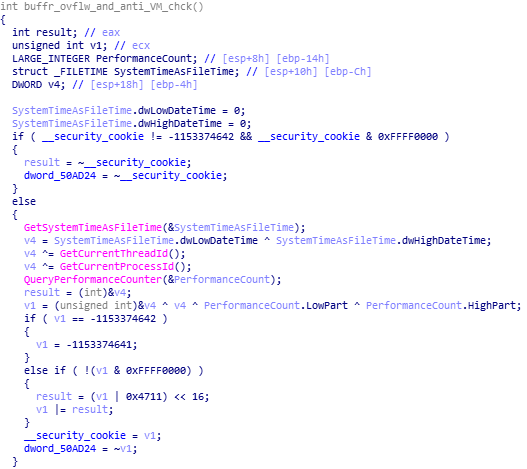
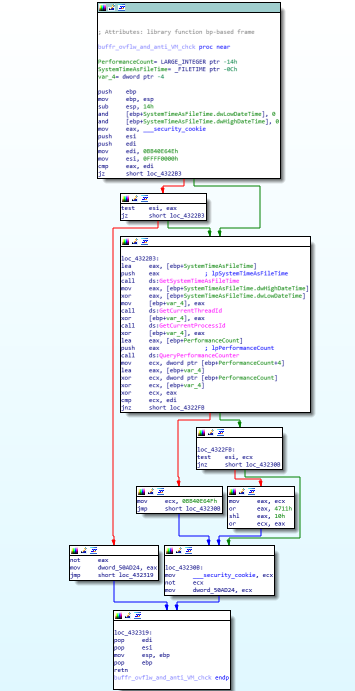 reversed code and disassembly of buffr_ovflw_and_anti_VM_chck function.
reversed code and disassembly of buffr_ovflw_and_anti_VM_chck function.call_to_win_main function
In this function firstly the “fetch_startup_info” is being called for fetching startup information of infected victim system ,after that what’s happening through out the whole function is that anti analysis and anti debugging techniques are being performed using different functions like
“anti_techqs_heap_access_ops” , “heap_thread_access_and_anti_analysis_dbg_ops”, “heap_anti_tech_access_ops_1”
are being performed along with the heap , modules, scrambling operations. And in the last “wWinMain” function is being called in this function which is the WinMain function.
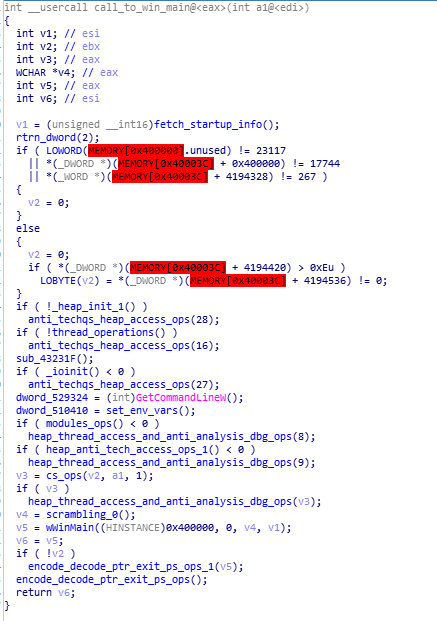
 reversed code and disassembly of call_to_win_main function.
reversed code and disassembly of call_to_win_main function.wWinMain function
Here is the call graph of wWinMain function is being given.
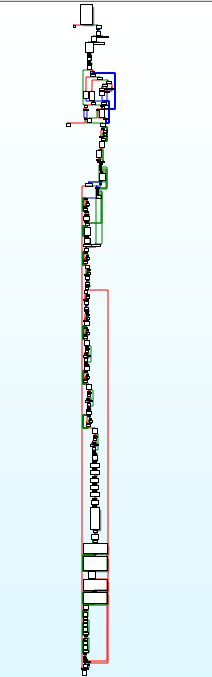 Disassembly call graph of wWinMain function.
Disassembly call graph of wWinMain function.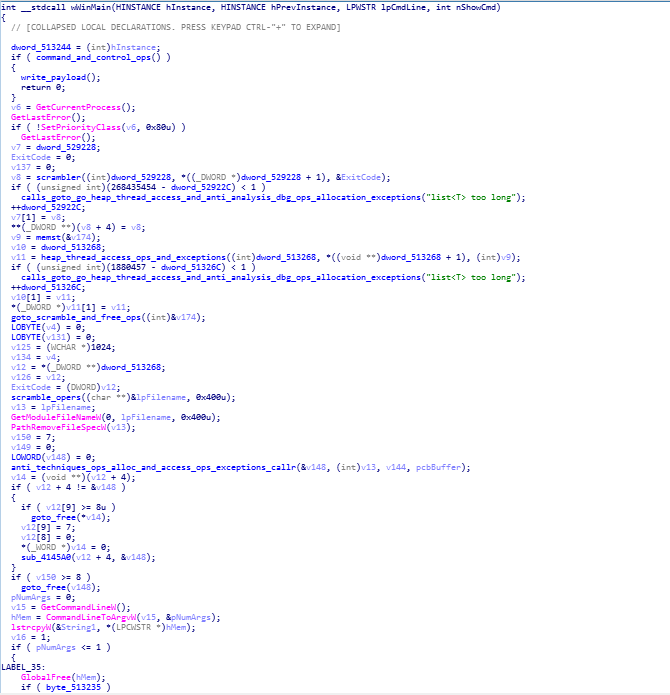 code of wWinMain function where call to command_and_control_ops is being made.
code of wWinMain function where call to command_and_control_ops is being made.In this wWinMain function,in starting conditional “if” statement call to “command_and_control_ops” function is being made where the operations for the command and control is being performed.
command_and_control_ops function
In this function , command and control(aka C2/C&C) server operations are being performed.
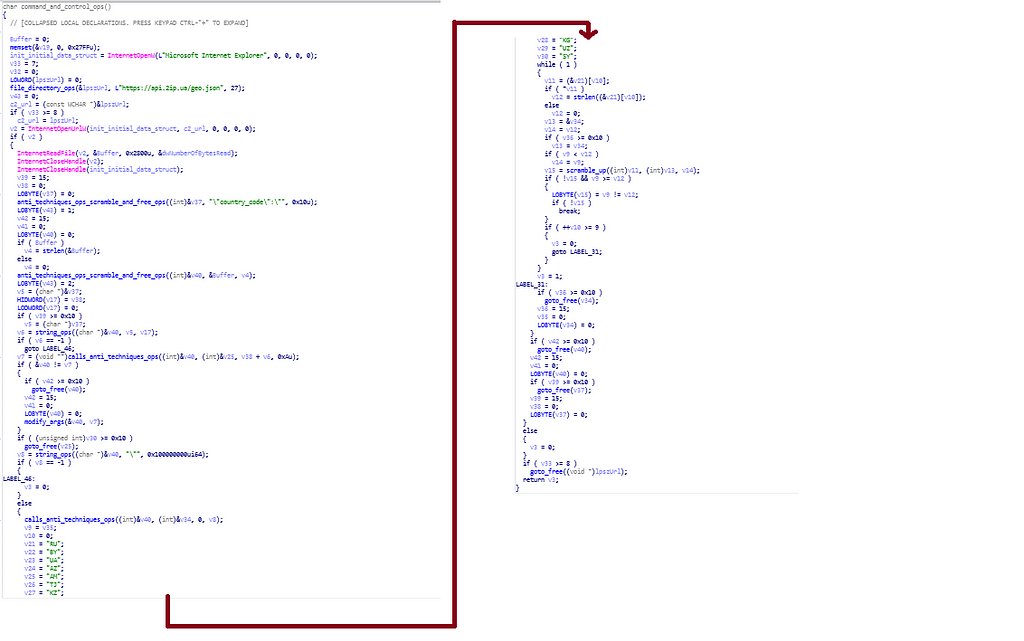
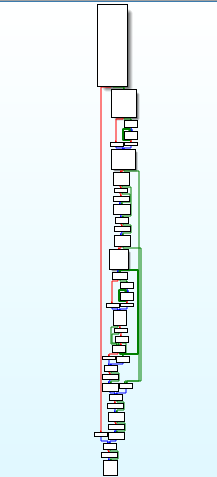 reversed code and disassembly call graph of command_and_control_ops function.
reversed code and disassembly call graph of command_and_control_ops function. calling of process_ops and registery_ops function in wWinMain function.
calling of process_ops and registery_ops function in wWinMain function.Here is the further code of wWinMain function is being given where the functions like “process_ops” and “registery_ops” are being called.
registery_ops function
In this function, all the registery key of system is being modified for further exploitation of infected victim system for establishing persistence across infected victim system.
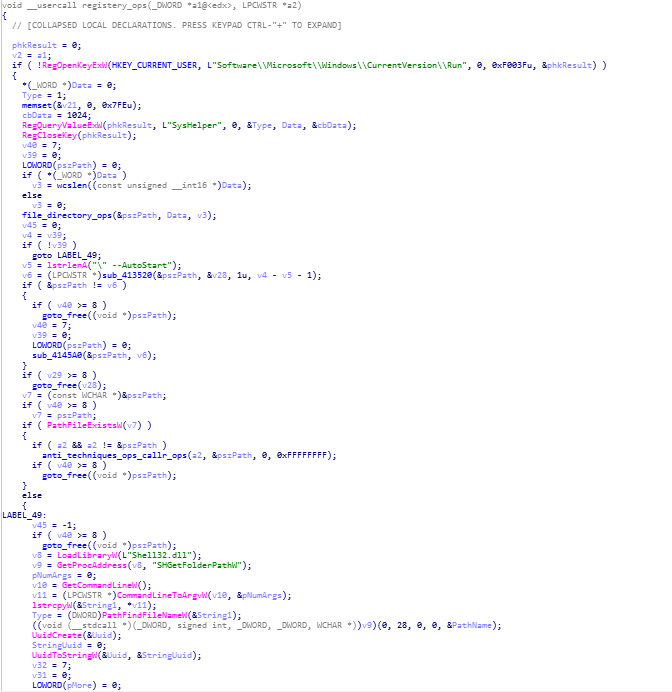
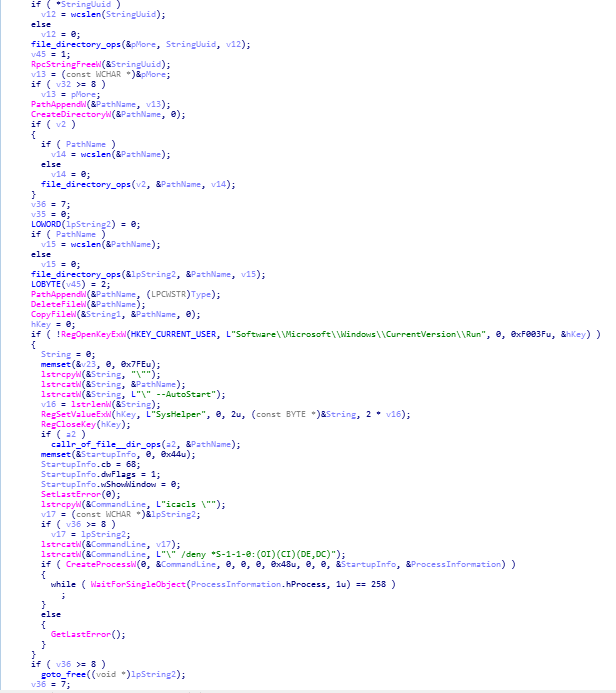
 reversed code of registery_ops function.
reversed code of registery_ops function.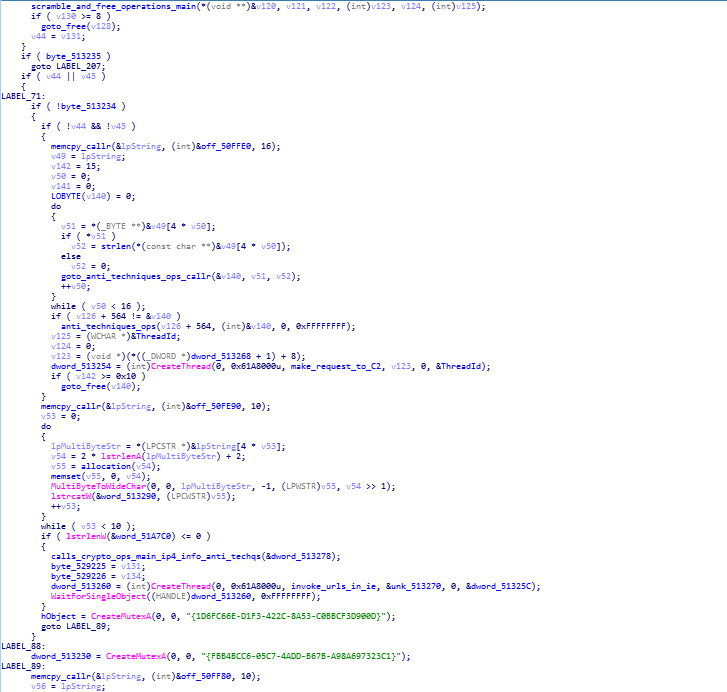 call to calls_crypto_ops_main_ip4_info_anti_techqs function is being made in wWinMain function.
call to calls_crypto_ops_main_ip4_info_anti_techqs function is being made in wWinMain function.moving further in the wWinMain function, what we encountered with is that here the call to the function “calls_crypto_ops_main_ip4_info_anti_techqs “ is being made where the encryption operations are being performed on infected victim system.
calls_crypto_ops_main_ip4_info_anti_techqs function
This is the function where the call to the “crypto_ops_main” function is being made.
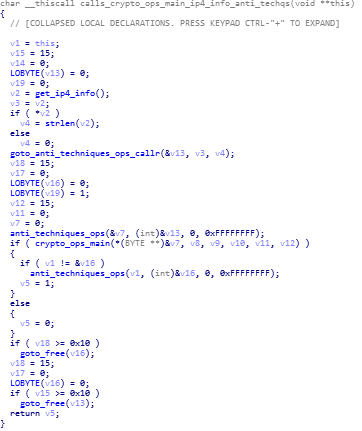
 reversed code and disassembly call graph of calls_crypto_ops_main_ip4_info_anti_techqs function.
reversed code and disassembly call graph of calls_crypto_ops_main_ip4_info_anti_techqs function.crypto_ops_main function
This is the crypto function main operational module developed by Stop ransomware developers in which they are using MD5 algorithm.

 reversed code and disassembly call graph of crypto_ops_main function.
reversed code and disassembly call graph of crypto_ops_main function.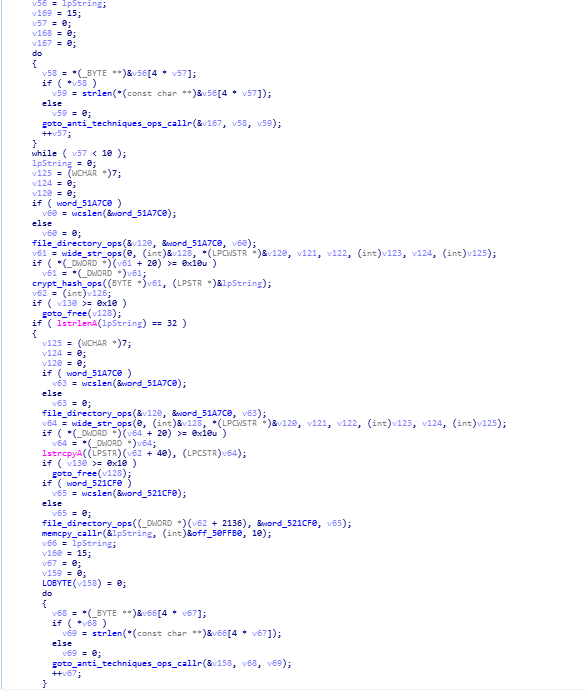 calling of file_directory_ops function in wWinMain function.
calling of file_directory_ops function in wWinMain function.On moving further in the reversed code of wWinMain function which we get encountered with is “file_directory_ops” function.
file_directory_ops function
in this function, is being use for loading dlls and carry out file directory operations

 reversed code and disassembly call graph of file_directory_ops function.
reversed code and disassembly call graph of file_directory_ops function. wWinMain function calling function responsible for anti-analysis and anti debugging.
wWinMain function calling function responsible for anti-analysis and anti debugging.following the reversed code of wWinMain of Stop ransomware we observe functions like carrying out anti analysis and anti debugging techniques throughout the mentioned reversed code of wWinMain function in here.
 wWinMain function calling scramble_and_free_operations function.
wWinMain function calling scramble_and_free_operations function.In here is the following reversed code of wWinMain function is being given. Here in here functions responsible for the scrambling the data on victim are being used.
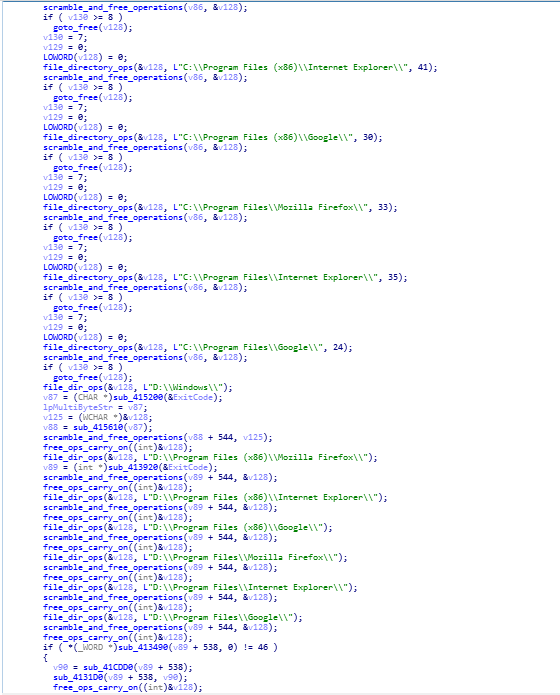 wWinMain function calling up freeing up space function.
wWinMain function calling up freeing up space function.In here reversed code of wWinMain function is being given where the freeing up space function are being used.
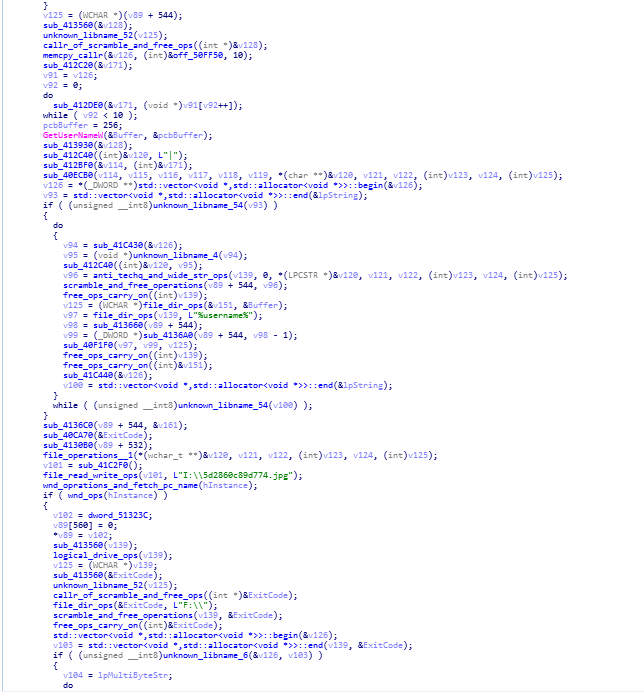 wWinMain function calling up file_read_and_write_ops function.
wWinMain function calling up file_read_and_write_ops function.In here further reversed code of Stop Ransomware is given, where file read and write operation is being carried out by “file_read_write_ops” function, also scrambling & freeing up memory space of victim system operations also carried out during section of reversed code.
file_read_and_write_ops function
This is the reversed code of file_read_and_write_ops function where the read and write operations are being carried out by the Stop Ransomware.
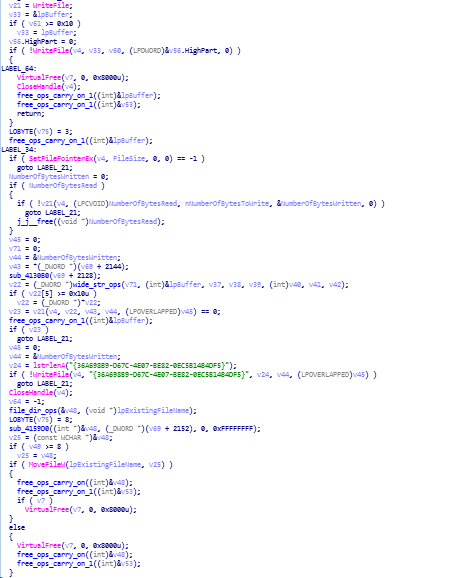
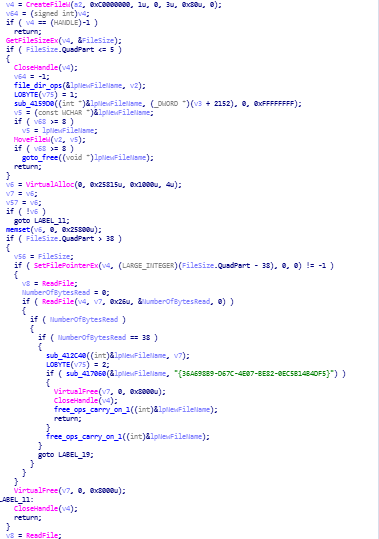 reversed code of file_read_and_write_ops function.
reversed code of file_read_and_write_ops function.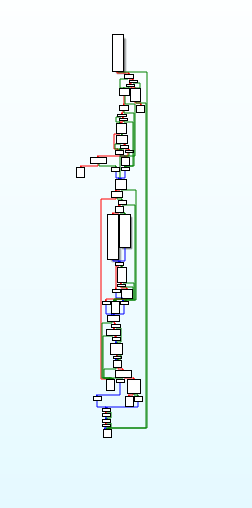 file_read_and_write_ops function disassembly call graph.
file_read_and_write_ops function disassembly call graph. wWinMain function carrying out messages operations.
wWinMain function carrying out messages operations.Further moving in the reverse code of Stop Ransomware there are the functions carrying out messages operations for this application which are highlighted in the pink.
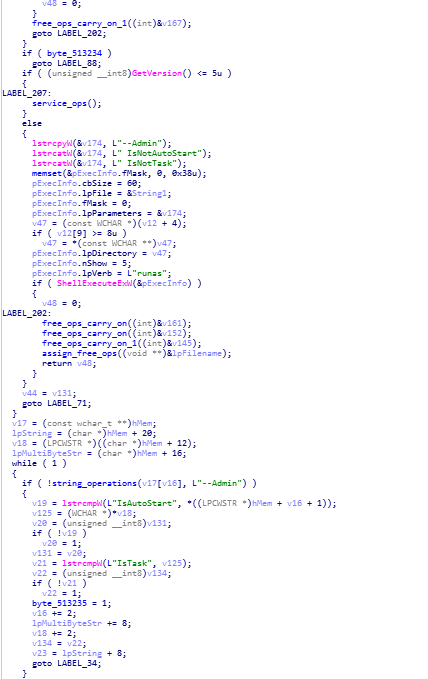 wWinMain function calls service_ops function.
wWinMain function calls service_ops function.In here further reversed code of Stop Ransomware is being mentioned , here service_ops function is being called , also shell execution and string_operations function being called for checking “Admin” privileges.
service_ops function
In this function, service “MYSQL” is being launched and operations related to that being carried out throughout this function.
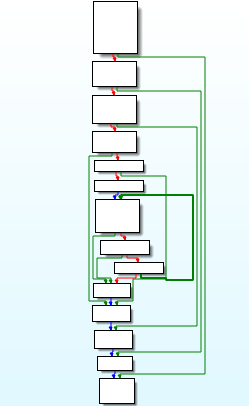
 disassembly call graph and reversed code of service_ops function.
disassembly call graph and reversed code of service_ops function.Moving further in the reversed code , what we observe that is operations related to processes is being carried out.
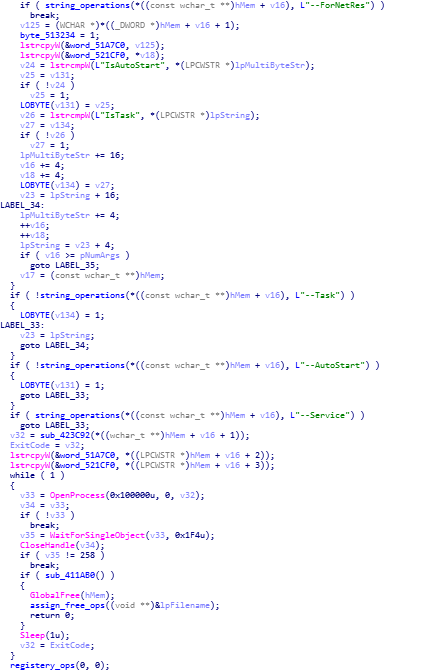
Dynamic Analysis ( Advanced )
For dynamic analysis, i had set breakpoints at the following functions in the Ida :-
….:- canary_cookie_calc___bof_mitigation()
….:- call_of_win_main()
….:- fetch_startup_info()
……:- thread_operations()
& inside thread_operations function i had set breakpoint at
…..:- heap_alloc_and_sleep()
…:- GetCurrent_thread_id()
Moving out of thread_operations function, coming back to the call_of_win_main function. further breakpoints are as follows :-
….:- 3 breakpoints in “call_of_win_main” function for heap_thread_access_and_anti_analysis_dbg_ops()
Moving to the Main function breakpoint are as follows:-
In call_of_win_Main
…..:- wWinMain()
Inside wWinMain():-
….:- few breakpoints in command_and_control_ops()
…:- write_payload()
…:- offset aAdmin
…:- OpenProcess() after loc_41A395
….:- registery_ops()
…..:- offset admin
….:- ShellExecuteW()
….:- allocation()
….:- calls_crypto_ops_main_ip4_info_anti_techqs()
…..:- file_dir_ops()
…..:- offset aI5d2860c89d774
……:- assign_free_ops()
Let’s dig in , as we start debugging “Stop Ransomware” first breakpoint gets hit at “canary_cookie_calc___bof_mitigation()” where the canary cookies calculation is being done and bof mitigation occurs.
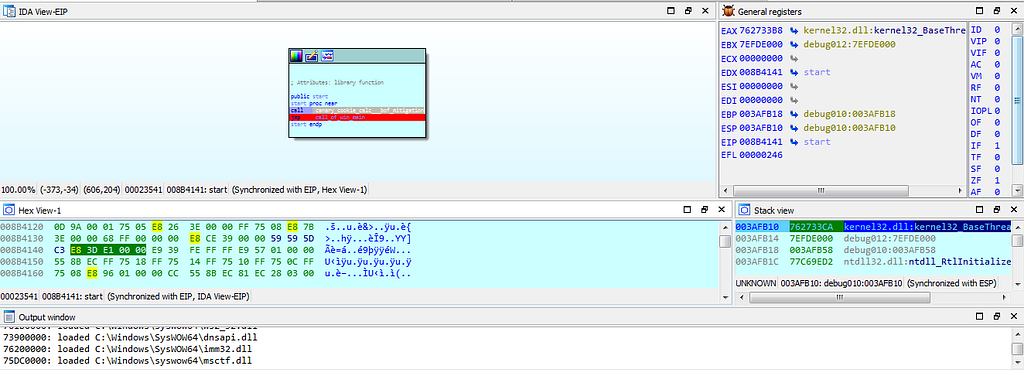 dbg hitting at canary_cookie_calc___bof_mitigation() function.
dbg hitting at canary_cookie_calc___bof_mitigation() function.Second breakpoint gets hit just after the first one, which is at the “call_of_win_main()” function where the call to wWinMain() function is being made.
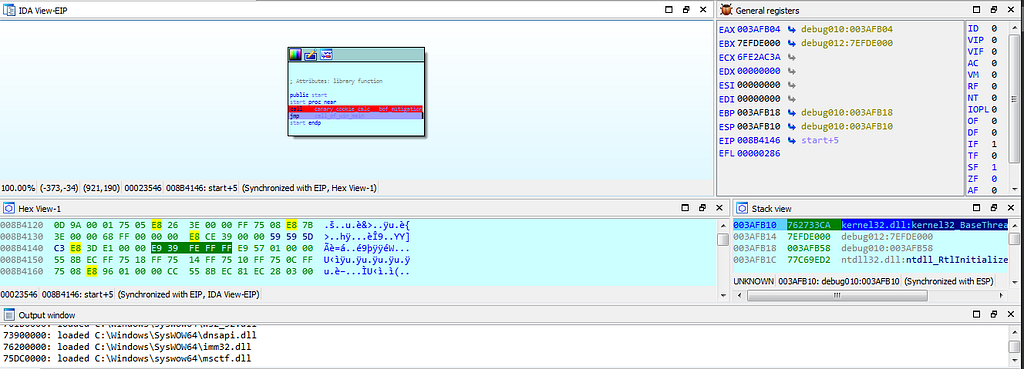 dbg hitting at call_of_win_main() function.
dbg hitting at call_of_win_main() function.As we proceed further in debugging “Stop Ransom” sample we come across debugger hitting at “fetch_startup_info” where the startup information of victim system is being fetched by the “Stop_Ransom”.
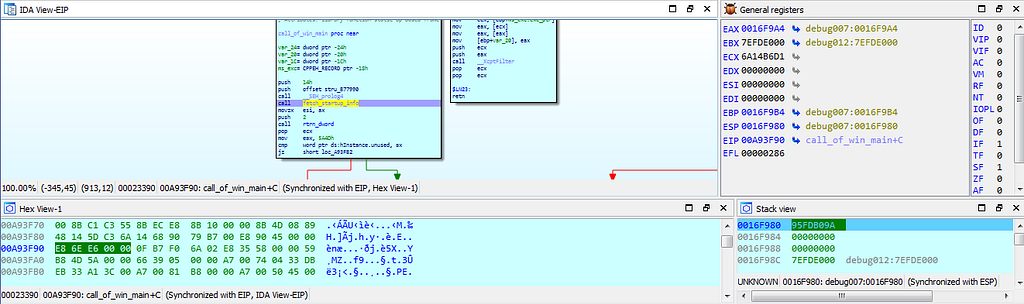
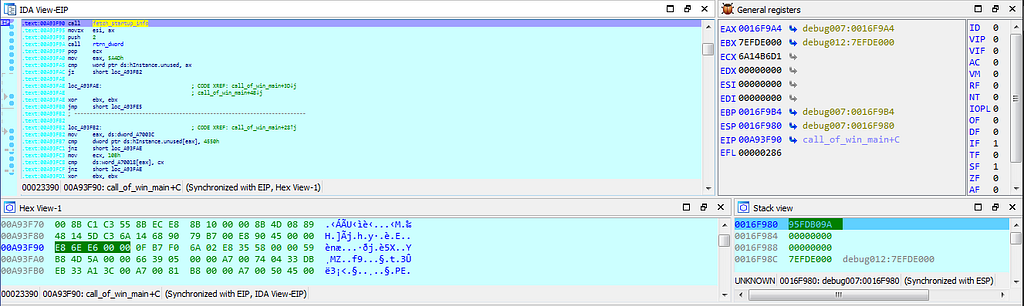 Graph and Text view of dbg hitting at fetch_startup_info() function.
Graph and Text view of dbg hitting at fetch_startup_info() function.Debugging further “Stop Ransom” , debugger gets to it’s next stop “thread_operations” where the operations like creating thread are being performed.
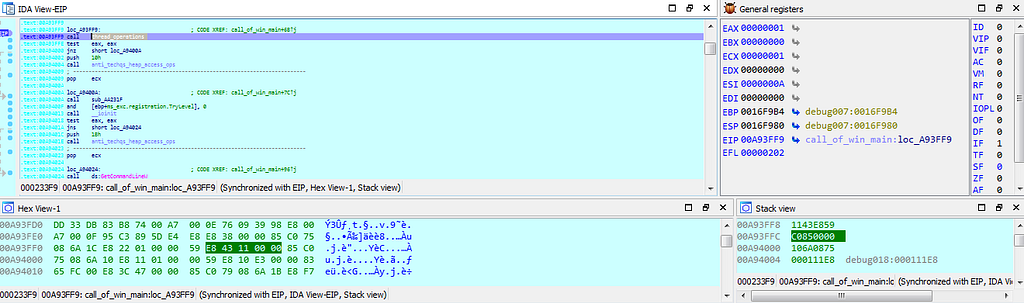
 Text and Graph view of dbg hitting at “thread_operations()” function.
Text and Graph view of dbg hitting at “thread_operations()” function.Next up the debugger gets hits at the “heap_alloc_and_goto_sleep” function where the allocation of data into the heap is being done.

 Graph & Text View of dbg hitting at the heap_alloc_and_goto_sleep() function.
Graph & Text View of dbg hitting at the heap_alloc_and_goto_sleep() function.Now the debugger hits at the wWinMain function, which is main function of the “Stop Ransom”.
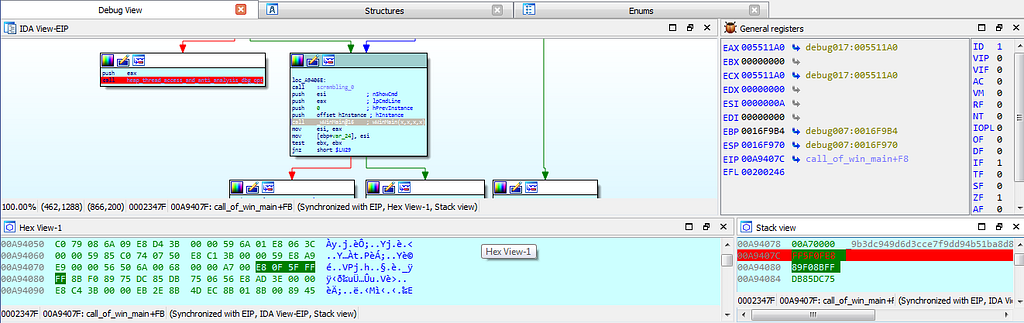
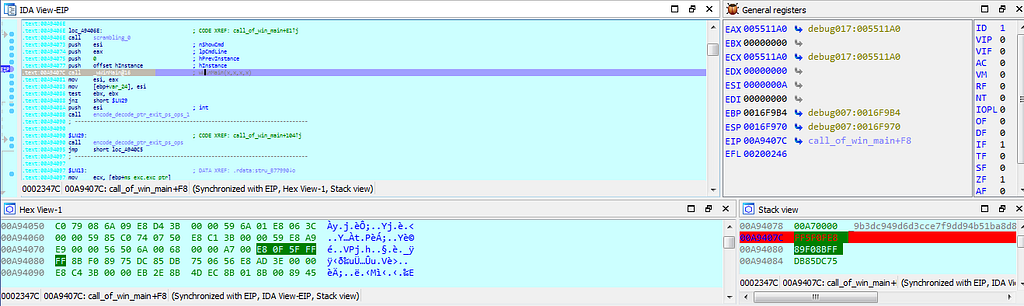 In call_of_win_main function dbg hits at the wWinMain() function.
In call_of_win_main function dbg hits at the wWinMain() function.Following debugging further we encounter with the next breakpoint which is at “command_and_control_ops” function where the operations related to C2/C&C is being carried out.
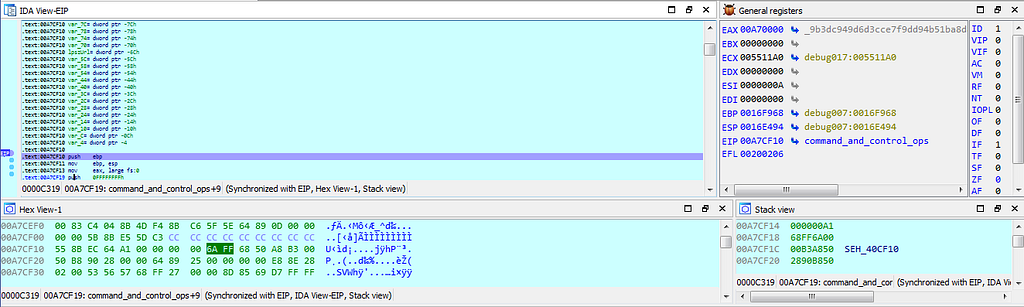
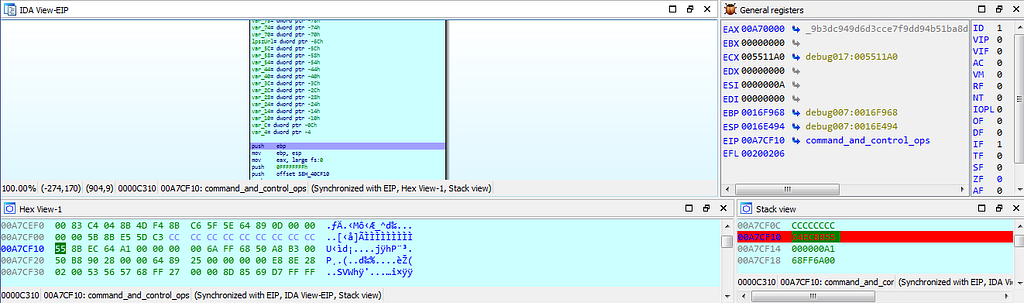 Text & Graph view of dbg hitting at breakpoint inside command_and_control_ops() function.
Text & Graph view of dbg hitting at breakpoint inside command_and_control_ops() function.Now debugger hits few other breakpoints inside this “command_and_control_ops” function which are shown here in image.
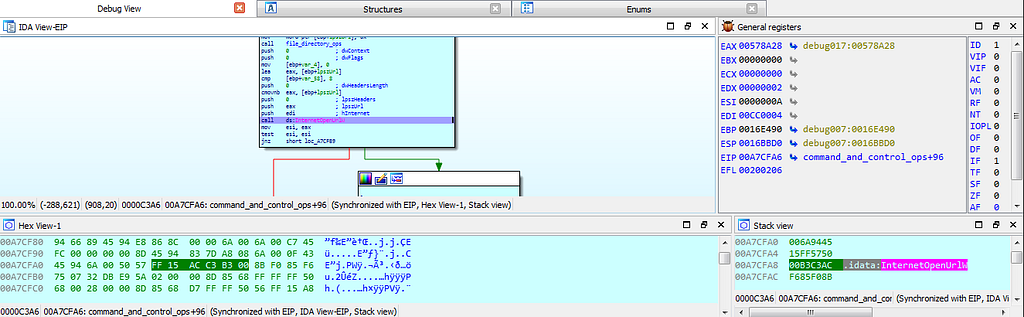
 Dbg hits breakpoints inside command_and_control_ops() function.
Dbg hits breakpoints inside command_and_control_ops() function.Now just after these hits inside “command_and_control_ops” function, debugger hits at few exceptions.
 Dbg hitting at exception.
Dbg hitting at exception.And then after hitting exception, debugger hits at the “offset aAdmin” what it does is that payload looks for the Admin privileges.
 dbg hits at location when payload of Stop Ransom looks for Admin Privileges.
dbg hits at location when payload of Stop Ransom looks for Admin Privileges.Now debugging further , debugger hits at the breakpoint “ShellExecuteW” where the shell command is being executed.
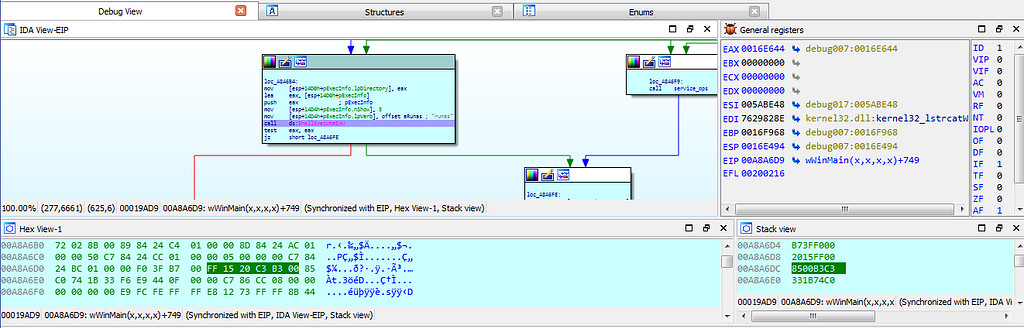 dbg hits at the location where ShellExecuteW cmd is being executed.
dbg hits at the location where ShellExecuteW cmd is being executed.Debugging further we encounter with the debugging causing error as shown.
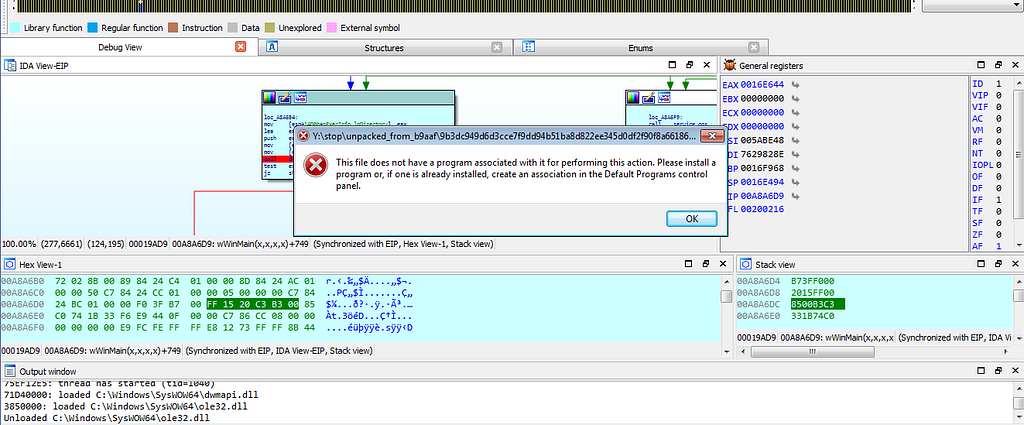 Further Debugging showing error.
Further Debugging showing error.Debugging further , debugger hits several times at the function “allocation” where the allocation of memory is being done.
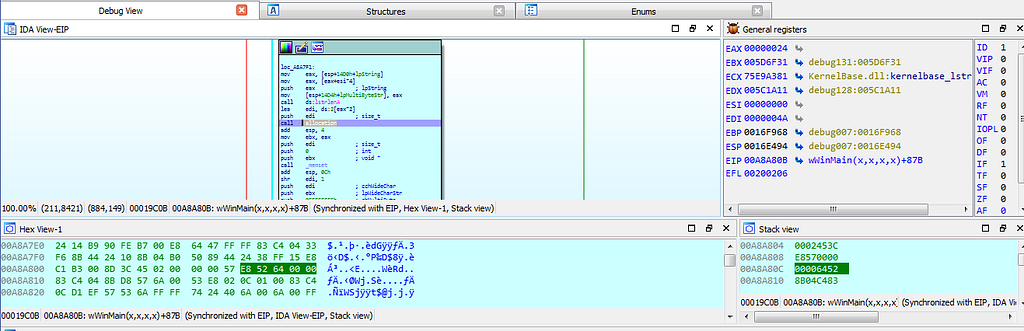 Debugger hits at allocation function.
Debugger hits at allocation function.Then after that debugger hits at the “calls_crypto_ops_main_ip4_info_anti_techqs” function.
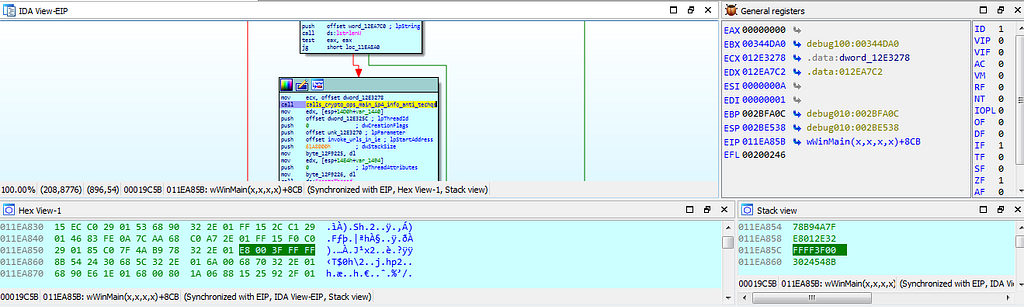 dbg hitting at the calls_crypto_ops_main_ip4_info_anti_techqs function.
dbg hitting at the calls_crypto_ops_main_ip4_info_anti_techqs function.Next breakpoint which gets hit is the “file_dir_ops” function where the operations related to file directory is being carried out.
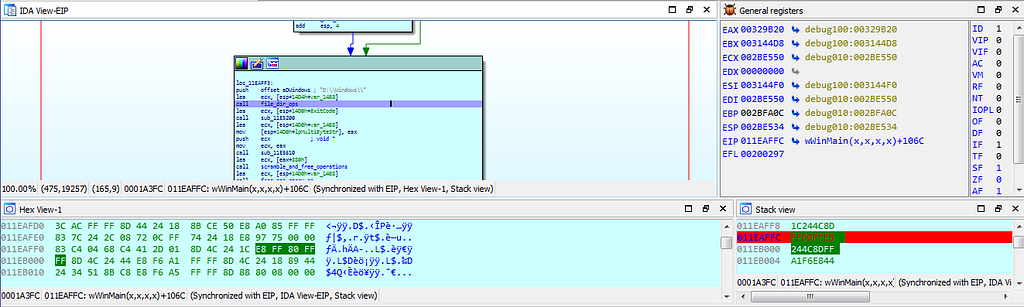 dbg hits at the file_dir_ops function.
dbg hits at the file_dir_ops function.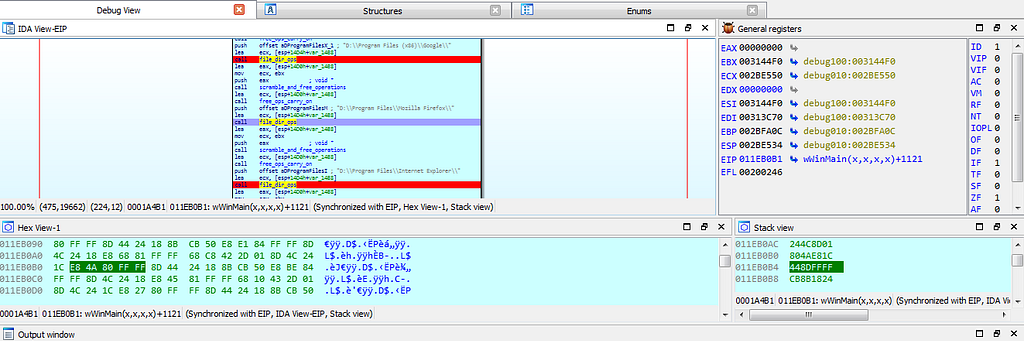
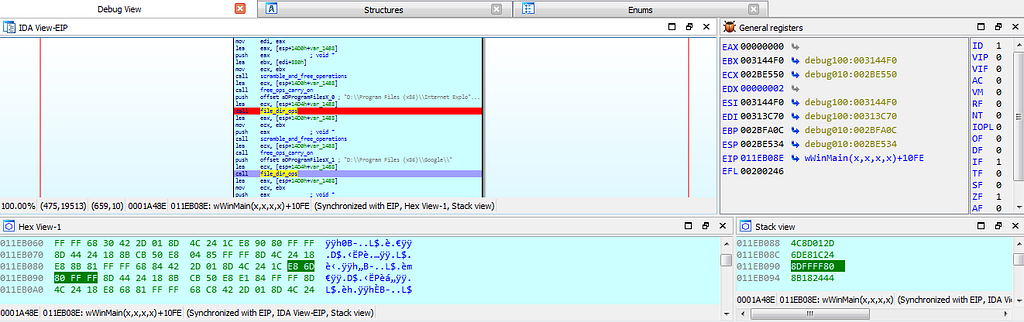
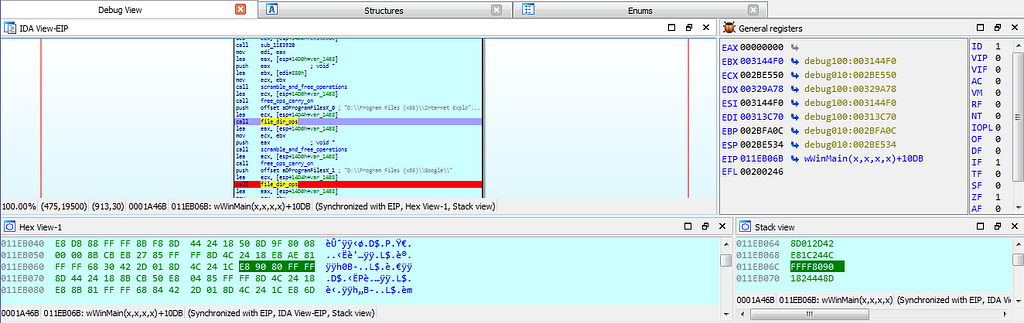
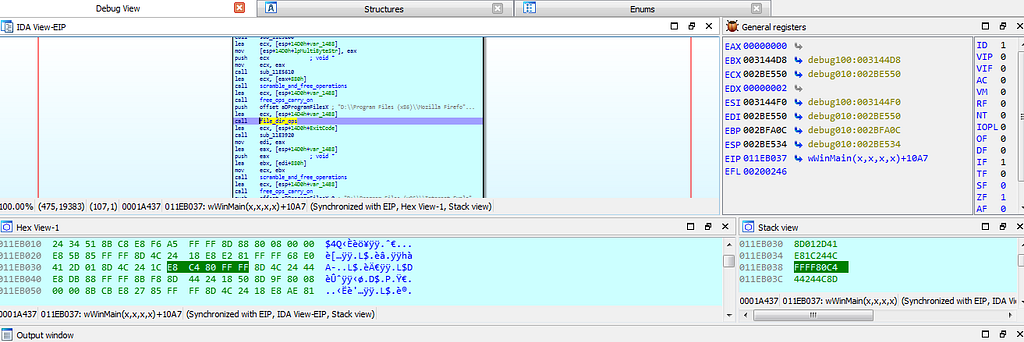 dbg hitting at breakpoints related to file_dir_ops function.
dbg hitting at breakpoints related to file_dir_ops function.next dbg hits at the breakpoint where some kind of config of Stop ransom is being stored in resource section.
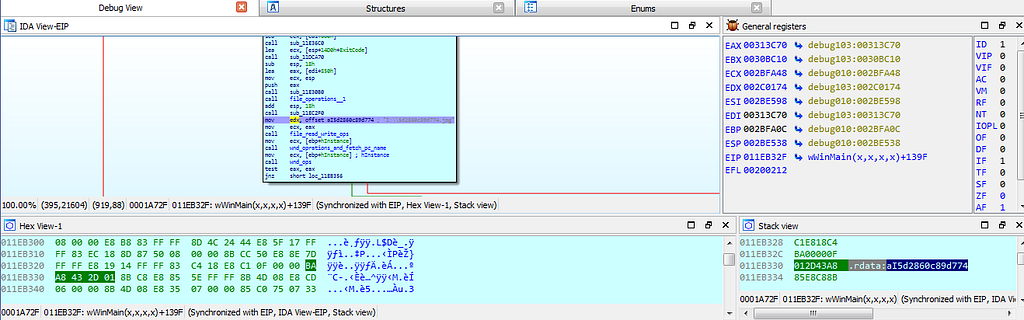 Dbg hitting breakpoint where config is being stored.
Dbg hitting breakpoint where config is being stored.After that debugger hits at the breakpoint where the exception is being raised.
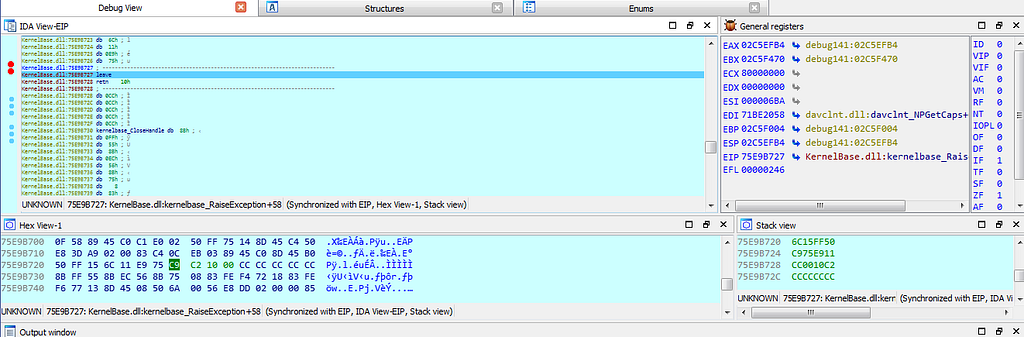 dbg hits at the exception.
dbg hits at the exception.Indicators of Compromise (IOCs) & Detection
Attack IDs
T1106, T1053, T1060, T1222, T1130 .
Mitre Attack Matrix
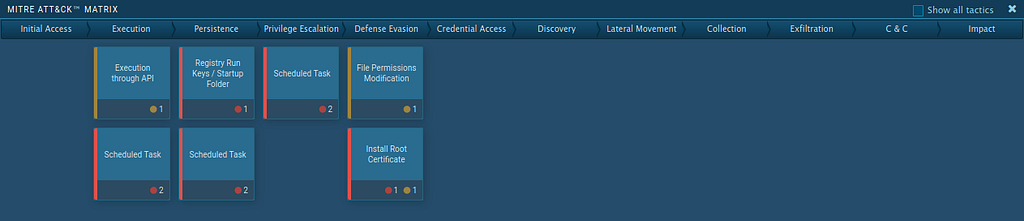 Mitre Att&ck Matrix from Any.Run .
Mitre Att&ck Matrix from Any.Run .Sample from Report
MD5 a6fe56089c98ee5373b4cf22d4b16d74
SHA1 120c33917ab39703c4ada6789748c8eed157c164
SHA256 9b3dc949d6d3cce7f9dd94b51ba8d822ee345d0df2f90f8a6618684824e2b95b
Dropped Executable
SHA1 120c33917ab39703c4ada6789748c8eed157c164
Domain Requests
api[.]2ip[.]ua
jfus[.]top
Connections
151[.]139[.]128[.]14
77[.]123[.]139[.]190
Network Traffic Mapping for C&C connections
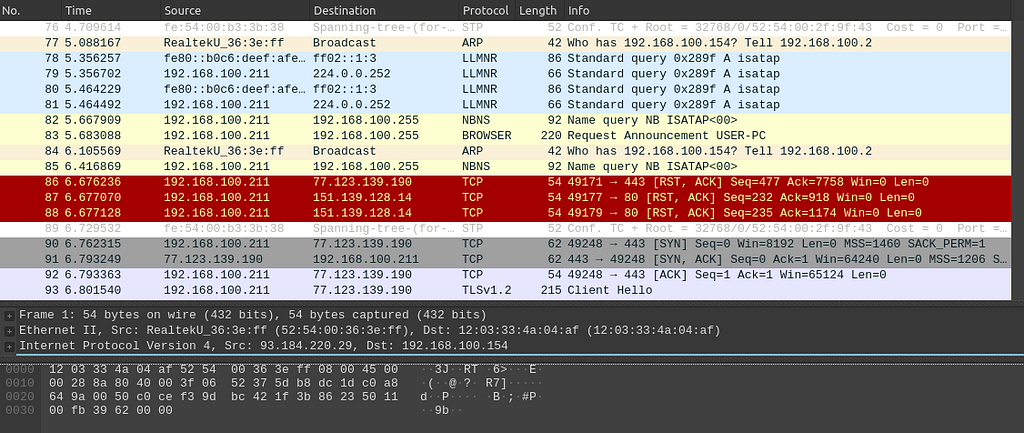 Network Traffic Analysis of C2 Communications.
Network Traffic Analysis of C2 Communications.YARA Signature
/*
YARA Rule Set
Author: 0xthreatintel
Date: 2021–05–15
Identifier: Stop_ransom
Reference: 0xthreatintel blog on Stop Ransom: https://medium.com/@0xthreatintel/in-depth-analysis-of-stop-ransomware-12b167b03fa9
*/
/* Rule Set — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — */
rule unpacked_stop_ransom {
meta:
description = “Stop_ransom — file unpacked_stop_ransom.bin”
author = “0xthreatintel”
reference = “0xthreatintel blog on Stop Ransom: https://medium.com/@0xthreatintel/in-depth-analysis-of-stop-ransomware-12b167b03fa9"
date = “2021–05–15”
hash1 = “9b3dc949d6d3cce7f9dd94b51ba8d822ee345d0df2f90f8a6618684824e2b95b”
strings:
$s1 = “E:\\Doc\\My work (C++)\\_Git\\Encryption\\Release\\encrypt_win_api.pdb” fullword ascii
$s2 = “C:\\SystemID\\PersonalID.txt” fullword wide
$s3 = “delself.bat” fullword ascii
$s4 = “e:\\doc\\my work (c++)\\_git\\encryption\\encryptionwinapi\\Salsa20.inl” fullword wide
$s5 = “C:\\Build-OpenSSL-VC-32/ssl/private” fullword ascii
$s6 = “C:\\Build-OpenSSL-VC-32/ssl/cert.pem” fullword ascii
$s7 = “C:\\SystemID” fullword wide
$s8 = “ <requestedExecutionLevel level=’asInvoker’ uiAccess=’false’ />” fullword ascii
$s9 = “C:\\Program Files (x86)\\Mozilla Firefox\\” fullword wide
$s10 = “C:\\Program Files\\Mozilla Firefox\\” fullword wide
$s11 = “D:\\Program Files (x86)\\Mozilla Firefox\\” fullword wide
$s12 = “D:\\Program Files\\Mozilla Firefox\\” fullword wide
$s13 = “bowsakkdestx.txt” fullword ascii
$s14 = “C:\\Build-OpenSSL-VC-32/ssl/certs” fullword ascii
$s15 = “C:\\Build-OpenSSL-VC-32/ssl” fullword ascii
$s16 = “C:\\Build-OpenSSL-VC-32/lib/engines” fullword ascii
$s17 = “Address: %s, mac: %s” fullword ascii
$s18 = “ thread=%lu, file=%s, line=%d, info=\”” fullword ascii
$s19 = “Error encrypting message: %s” fullword ascii
$s20 = “ filename=\”smime.p7s\”%s%s” fullword ascii
condition:
uint16(0) == 0x5a4d and filesize < 3000KB and
8 of them
}
Thanks for reading.
Article Link: https://0xthreatintel.medium.com/in-depth-analysis-of-stop-ransomware-12b167b03fa9?source=rss-a15183055fd6------2