Safeguarding sensitive data, maintaining brand reputation, and cultivating customer trust pose continuous challenges for enterprise organizations. However, the dark web, a hidden corner of the internet, poses unique challenges for cybersecurity professionals. Criminal activities such as the sale of stolen credentials and plans for targeted attacks thrive in this dark section of the internet.
This blog post explores some of the threats that originate on the dark web and how external threat intelligence solutions can enable organizations to proactively defend themselves.
Since its inception in the early 2000s, the dark web has evolved into a hub for illegal activities. It facilitates the trade of hacking methods and compromised credentials as well as the distribution of malware and ransomware. Its also constantly evolving, with threat actors discovering, sharing, and acting on new vulnerabilities and exploits every day.
During the early stages of the dark web, secretive forums and file-sharing platforms thrived, resembling a shadowy version of Reddit or Etsy. The notorious Silk Road, extensively detailed in the book American Kingpin, and the emergence of cryptocurrencies like Bitcoin have been pivotal in shaping the dark web, giving rise to sophisticated underground markets akin to a dark eBay.
Notorious ransomware groups like LockBit and ALPHV have been operating on dark web platforms, taking credit for their actions and revealing their targets. Additionally, Telegram has emerged as a favored platform for secretive engagements, facilitating and enabling a range of activities from communication to coordination to distribution of malicious content.
Attacks stemming from conversations, information sharing, and transactions on the dark web have resulted in financial, operational, and reputational losses for organizations across the globe. However, improving dark web monitoring capabilities can help organizations be proactive in mitigating threats to their business, their customers, and their supply chain.
How does the dark web affect organizations?
The dark web in itself is not all that dangerous to most organizations, but whats taking place there should pique the interest of defenders. The dark web provides a platform for ransomware groups to operate and for bad actors to sell and exchange malware, compromised credentials, exploit kits, and stolen payment cards.
Ransomware
The dark web is a well known home for ransomware groups, which continued to wreak havoc on organizations in 2023. In the past year, ransomware payments ballooned to $1.1 billion (The Record) and, according to a report from Delinea, 76% of victims paid a ransom. The dark web provides a secure and anonymous environment for ransomware groups to communicate, collaborate, and conduct their illicit activities.
Credentials
Dark web markets and forums are popular destinations for initial access brokers and threat actors looking to sell and buy valid credentials. Valid credentials have become so popular for threat actors that under MITRE ATT&CKs initial access vectors, Valid Accounts (T1078) was the top TTP according to both Recorded Future and IBM X-Force.
Using information from our Identity Intelligence module, Recorded Future researchers found a 135% rise in the overall number of harvested credentials and a 166% increase in credentials associated with cookies. Additionally, researchers at IBM found a 266% upsurge in the use of infostealers. With the right access and contacts, someone could purchase a valid credential for just $10, enabling them to log in to a corporate network or personal account, bypass multi-factor authentication controls, and begin their infiltration.
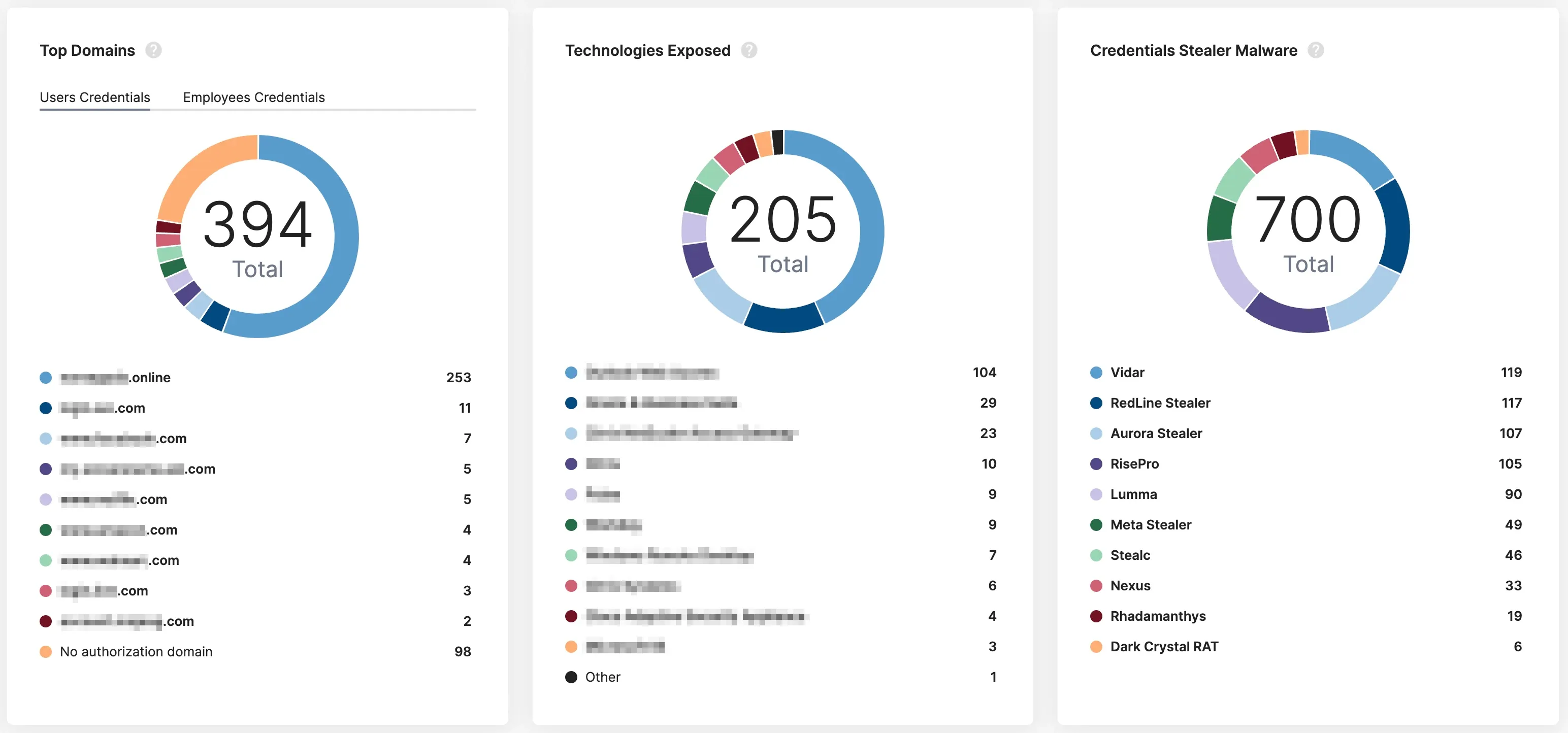 Recorded Futures Identity Intelligence module helps organizations defend against employee and customer credentials that have been stolen by infostealer malware. Watch how Toyota Motors North America defends against compromised credentials, and take an interactive tour of Identity Intelligence.
Recorded Futures Identity Intelligence module helps organizations defend against employee and customer credentials that have been stolen by infostealer malware. Watch how Toyota Motors North America defends against compromised credentials, and take an interactive tour of Identity Intelligence.
Exploit Kits
Similar to how novice cooks purchase meal kits, less-skilled threat actors can purchase exploit kits on the dark web. Despite their slight dip in popularity, dark web exploit kits are pre-packaged tools and frameworks that cybercriminals use to exploit vulnerabilities in software and systems. These kits make it easier for threat actors to launch attacks and gain unauthorized access to targeted systems. They often provide a convenient gateway for cybercriminals to exploit vulnerabilities without needing advanced technical skills.
Payment Cards
In 2022 it looked like the dark web market for stolen credit cards was slowing down. However, supply bounced back to previous levels in 2023. According to the 2023 Annual Payment Fraud Intelligence Report from Recorded Future, 71.4 million payment cards were posted for sale on the dark web in 2023, and another 48 million were posted for free on various sources. A median fraud charge of $79 caused $9.4 billion in preventable fraud losses for card issuers and $35 billion in potential chargeback fees for merchants and acquirers.
How does Recorded Future remediate threats originating on the dark web?
Ransomware Extortion Websites
Threat actors use ransomware extortion websites to threaten to leak victim files. These files often include network details, financial information and documents, PII, employee or client credentials, and other sensitive information that motivates the victim to pay the ransom. Victims who concede typically do so based on a promise that the data will be deleted, but we saw with Lockbit that this doesnt always happen. On the other hand, victims who dont pay are likely to have additional data leaks posted to the extortion site.
For years, Recorded Future has collected information from ransomware extortion websites, analyzed it, and turned it into actionable intelligence to help organizations proactively mitigate the impact of a ransomware attack. Presently, Recorded Future collects information from text posts, images, and leaked file metadata on over 100 ransomware extortion websites.
Information found in ransomware victim metadata can help identify companies and organizations that could be direct or indirect victims of a ransomware attack. Access to leaked file metadata enables organizations to investigate leads for potential data exposure that could impact them as well as relevant third and fourth parties.
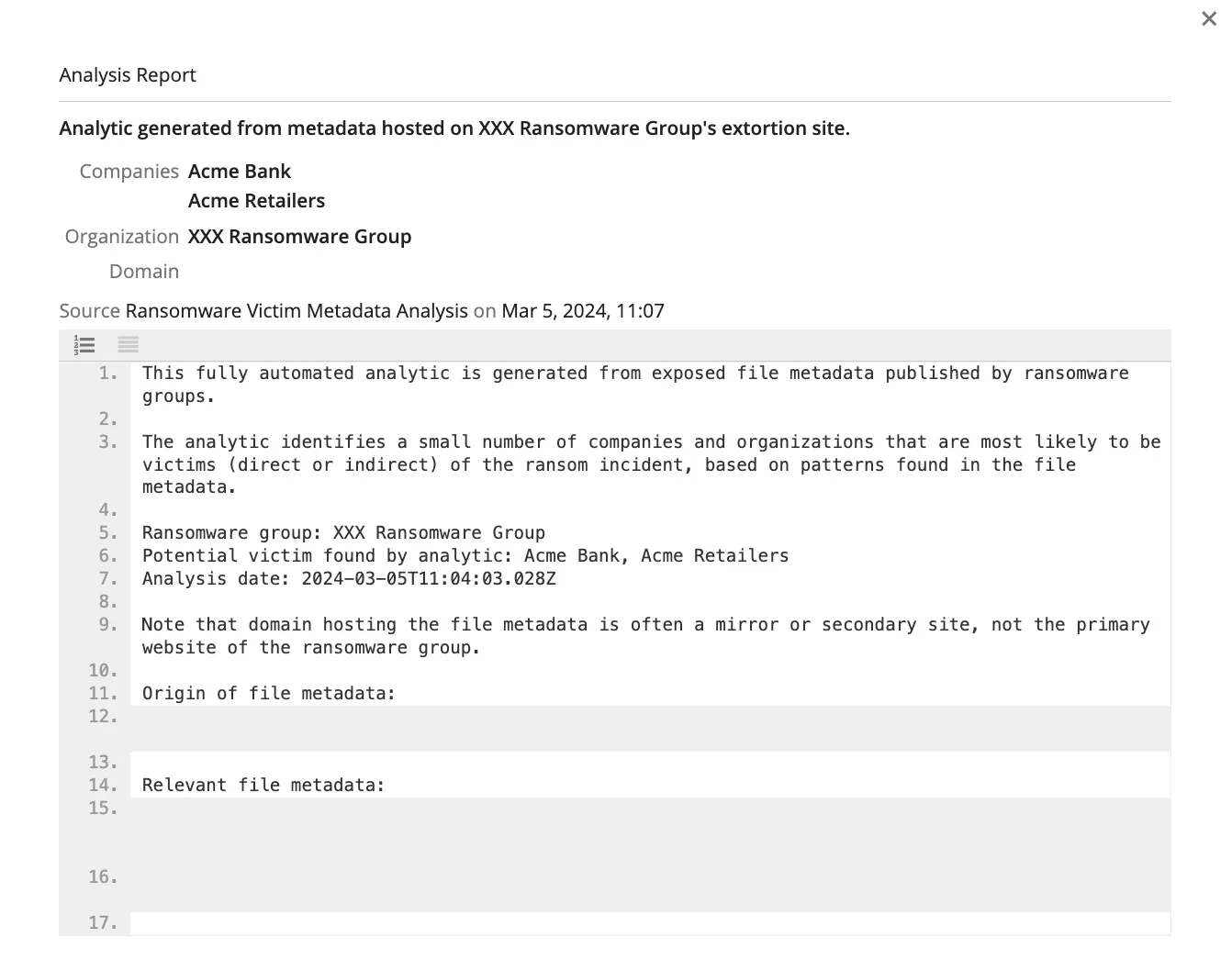 Image of Recorded Futures ransomware victim metadata analysis, which helps identify organizations that are most likely to be victims (direct or indirect) of a ransomware incident.
Image of Recorded Futures ransomware victim metadata analysis, which helps identify organizations that are most likely to be victims (direct or indirect) of a ransomware incident.
Dark Web Markets
Unlike e-commerce sites on the open web, dark web markets like Russian Market, 2Easy, and others make their fortunes selling compromised credentials, PII, and stolen credit cards. Threat actors can use this information to access an employees account, create personalized spearphishing campaigns, or place fraudulent transactions.
Recorded Future collects information from a number of dark web markets to help organizations mitigate any risk stemming from items for sale. For example, by identifying stolen credit card information being sold on dark web markets, card issuers can place heightened controls on cards with a high risk of being used for fraud. Additional signals, such as the card being sold or used in transactions with known tester merchants, can enable the issuer to take proactive actions to block the card from further transactions or issue the customer a new card.
According to a large North American financial institution, When transactions occur on customer cards identified by Recorded Future as being present on the dark web or used on known tester merchants, most of the time the transaction is actually fraudulent.
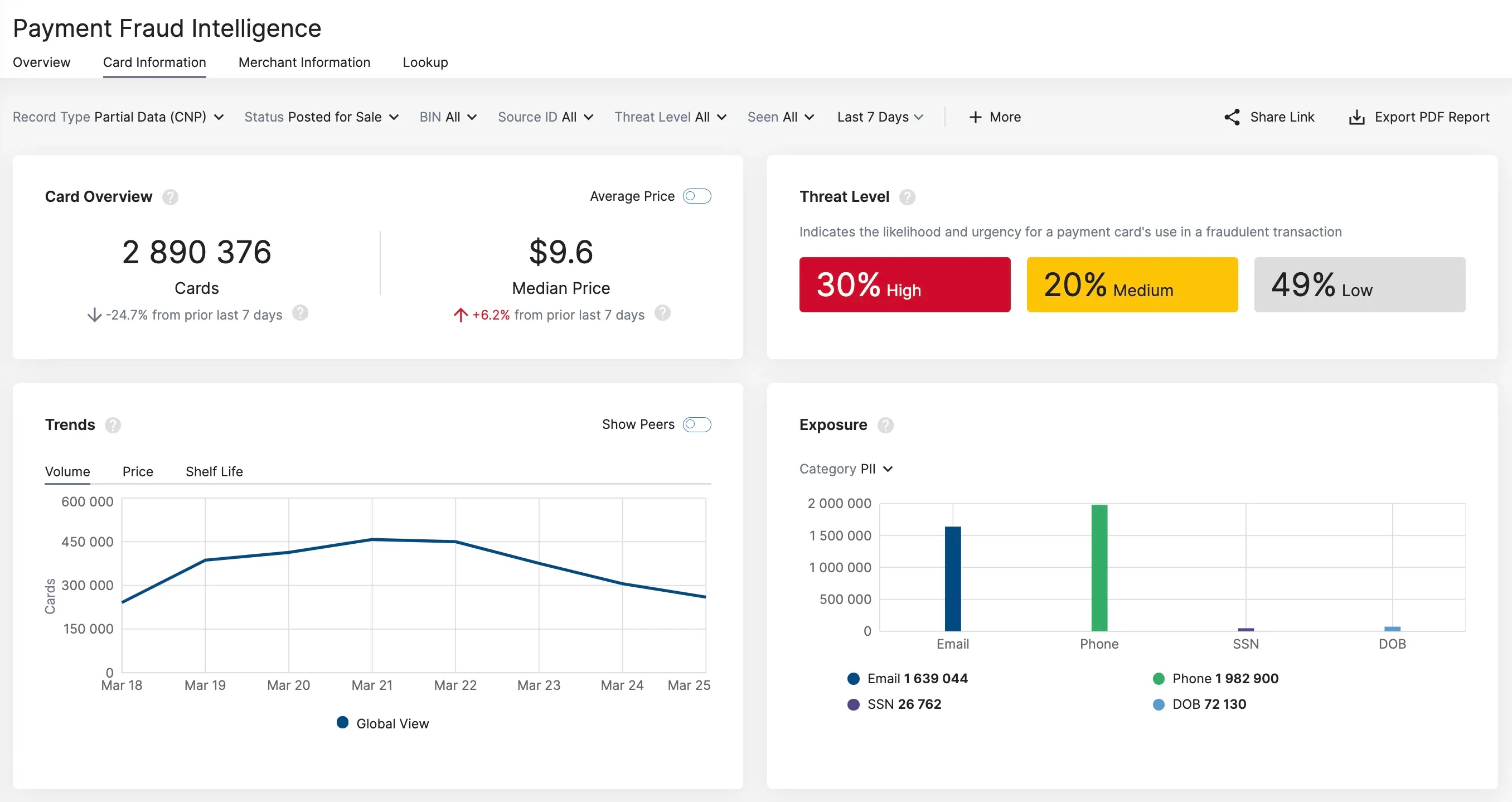 Recorded Future Payment Fraud Intelligence detects compromised payment cards for sale on the dark web, enabling financial institutions to take a proactive approach to preventing fraud.
Recorded Future Payment Fraud Intelligence detects compromised payment cards for sale on the dark web, enabling financial institutions to take a proactive approach to preventing fraud.
Dark Web Forums
Dark web forums are often where conversations get started between threat actors, those with something to sell, and lower-skilled cybercriminals looking for more advanced tools. Threat actors can exchange information, techniques, and tools to improve their hacking skills and stay up to date on the latest trends in cybercrime. Some will use dark web forums to recruit affiliates to carry out cybercriminal activities, including distributing malware, launching phishing campaigns, and participating in ransomware attacks.
Similar to dark web markets, dark web forums also serve as marketplaces where threat actors can sell compromised credentials, personal data, financial details, and other valuable information. They can also facilitate the trade of hacking tools, exploit kits, remote access trojans (RATs), and other malicious software that can be used to compromise systems and networks.
Recorded Future collects information from over 250 top-tier and medium-tier dark web forum sources to provide actionable information to organizations. Information can include whether threat actors are mentioning an organizations brand or supply chain partners, whether any new vulnerabilities are being referenced, and which threat actors are known to utilize specific forums.
Frequent mentions of a company or product on the dark web often correlate, indicating an imminent attack, an illicit sale of company assets or accounts, or potentially more complex fraud schemes.
Dark web monitoring provides visibility into this restricted environment to help clients stay a step ahead of cybercrime campaigns that could affect their organizations, their suppliers, or the software products they use.
Telegram
Since its creation in 2012, Telegram a multi-purpose chat application has quickly gained popularity among the underground cybercriminal community. Telegrams security, large number of chat options, and convenience have led to its growing popularity. Few dark web markets rival Telegrams reliability.
According to some experts, the future of large-scale, highly role-specialized criminal activity will take place on Telegram and future alternatives. Currently, cybercriminals have used Telegram groups to conduct transactions of illicit goods, post announcements from related internet forums, and communicate with fellow criminals.
Recorded Future helps organizations understand cyber-related chatter on Telegram about their own brands, relevant third parties, and other organizations of note. Since threat actors often discuss their activities on Telegram whether theyre reporting planned attacks, exchanging information, or sharing findings visibility enables organizations to stay out in front of threats and build resilience against unexpected risks.
Recorded Future helped one client detect exposed credentials on a Telegram channel, both identifying the threat and enhancing the urgency to remediate the risk. Another client in the financial services industry was able to identify a fraudulent check on a Telegram channel through Recorded Futures optical character recognition (OCR) capabilities. The analyst reported the incident to their internal fraud management team to prevent the check from being cashed.
How Recorded Future helps mitigate dark web threats
Threat actors have long used dark web sites and forums to remain anonymous and attempt to gain an advantage over their targets. This is unlikely to change anytime soon. To combat this challenge, organizations require proactive visibility into the deep recesses of the dark web to ensure that they can mitigate threats. To help security practitioners and leaders, Recorded Future provides extensive intelligence across a wide range of dark web channels, which can be delivered via alerts, playbooks, and human-curated intelligence reports.
Alert Notifications
Without timely alerting, intelligence becomes a collection of information. For many clients, the ability to prioritize alerts based on external threat intelligence and risk factors is crucial for improving their security operations and risk management. The ability to build different alert rules and manage notifications helps users ensure that theyre receiving relevant and timely alerts. In addition, Recorded Future AI Insights and transparent evidence help users swiftly determine the severity of an alert and what action to take.
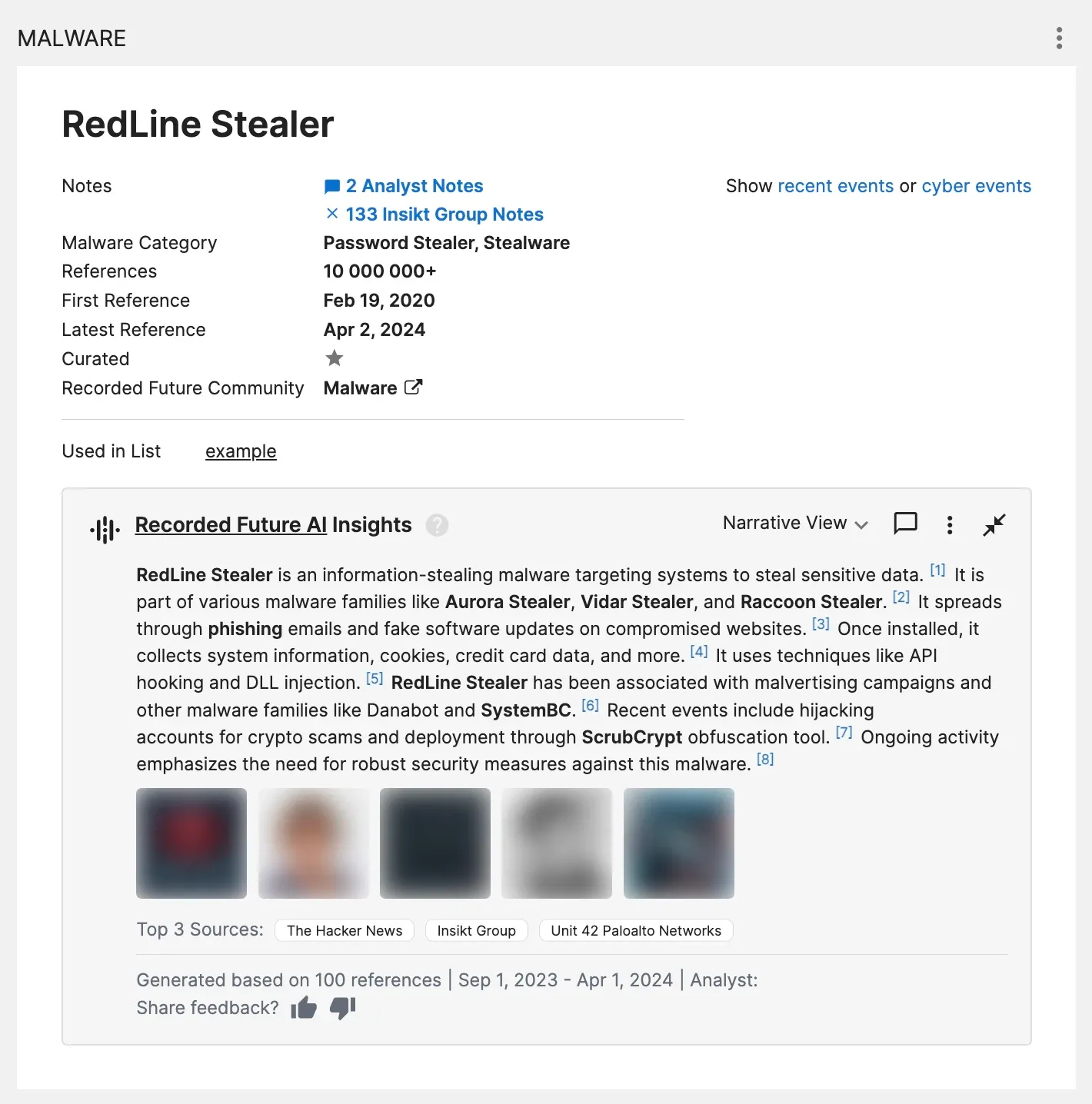 Recorded Future AI Insights help organizations reduce investigation time by providing automated and actionable context. The above example shows the AI Insights for RedLine Stealer. Learn more about recent updates to Recorded Future AI Insights in this blog post.
Recorded Future AI Insights help organizations reduce investigation time by providing automated and actionable context. The above example shows the AI Insights for RedLine Stealer. Learn more about recent updates to Recorded Future AI Insights in this blog post.
One Recorded Future client has found it beneficial to set up automatic reporting for any mention of his organizations brand or credentials on the deep dark web. Alerts generated by Recorded Future free the organizations analysts from having to build and run the same queries over and over, giving them time to focus on more strategic tasks.
Playbook Alerts
When threats are found on the dark web, defenders need a way to rapidly distill information, triage alerts, and reduce time-to-action. Recorded Futures playbook alerts help defenders by automating large phases of the investigation, updating users on changes in risk, producing verdicts, and providing recommended next steps. In addition, playbook alerts are automatically prioritized based on severity and risk so organizations know where to focus.
Clients report being 48% faster at identifying a new threat than before, with playbook alerts being a key component in reducing mean time to detect (MTTD) and mean time to investigate (MTTI). These alerts have proven to be beneficial for high-impact third-party cyber events, helping organizations identify issues such as recent attention on ransomware extortion websites, credentials compromised by infostealer malware, and exploit chatter about vulnerabilities that could affect their tech stack.
HUMINT
Recorded Futures dark web collection is made possible by undercover engagements and human intelligence (HUMINT) from our Insikt Group, a team of expert analysts and researchers who provide analysis on nation-state threats, cybercriminals, technical sourcing and collection, and more. To infiltrate these restricted forums and deliver critical intelligence requires human expertise, an essential first step toward automating collections.
To learn more about the Recorded Future Insikt Group, check out our latest Intelligence Reports and our 2023 Annual Report.
When intelligence is neither timely nor actionable, it becomes old news quickly. To navigate todays complex threat ecosystem, organizations require proactive insights into the dark web and closed sources to help them monitor any threats to their organization, partners, or industry. With a vast collection of timely and actionable intelligence from dark web sources, Recorded Future arms defenders with distilled information to build resilience against unexpected threats.
To see how Recorded Future can improve dark web visibility for your organization, request a demo.
Article Link: Improving Dark Web Investigations with Threat Intelligence | Recorded Future