In light of the extended tax deadline due to the coronavirus pandemic, tax fraud remains a viable avenue for the criminal group behind the IcedId banking malware.
By Joshua Platt, Jason Reaves, Vitali Kremez
Executive Summary
- IcedID is actively harvesting tax-related information.
- IcedID also actively seeks to procure important documents.
- The gang utilizes custom PowerShell uploaders to exfiltrate specific tax data.
- IcedID continues to evolve and operate in obscurity, but the group is well-known for their banking operation. The operators use sophisticated custom scripting designed to locate and upload tax files.
Background
The Neverquest operation suffered a major arrest in 2017 (Stanislav Lisov) and subsequently disappeared for a short time. Shortly thereafter, the operation picked up in the form of IcedID, which continues to operate relatively quietly although they remain an active and elite operation.
Stanislav Vitalievich Lisov (aka “Black”, “Blackf”) was responsible for the administration and fraud operations portion of the Neverquest operation. The botnet itself was routinely referred to by members of the operation as “Catch,” “Porsche,” and “Smile.”
The history behind the Neverquest project dates back to the infamous crimeware-as-a-service business model called “76service” operated by the Russian national Nikita Kuzmin.
Since the arrest of Nikita Kuzmin and years later, Neverquest operation also adopted a similar business crimeware-as-a-service model splitting the backend into projects and profiting from project-based affiliate operations.
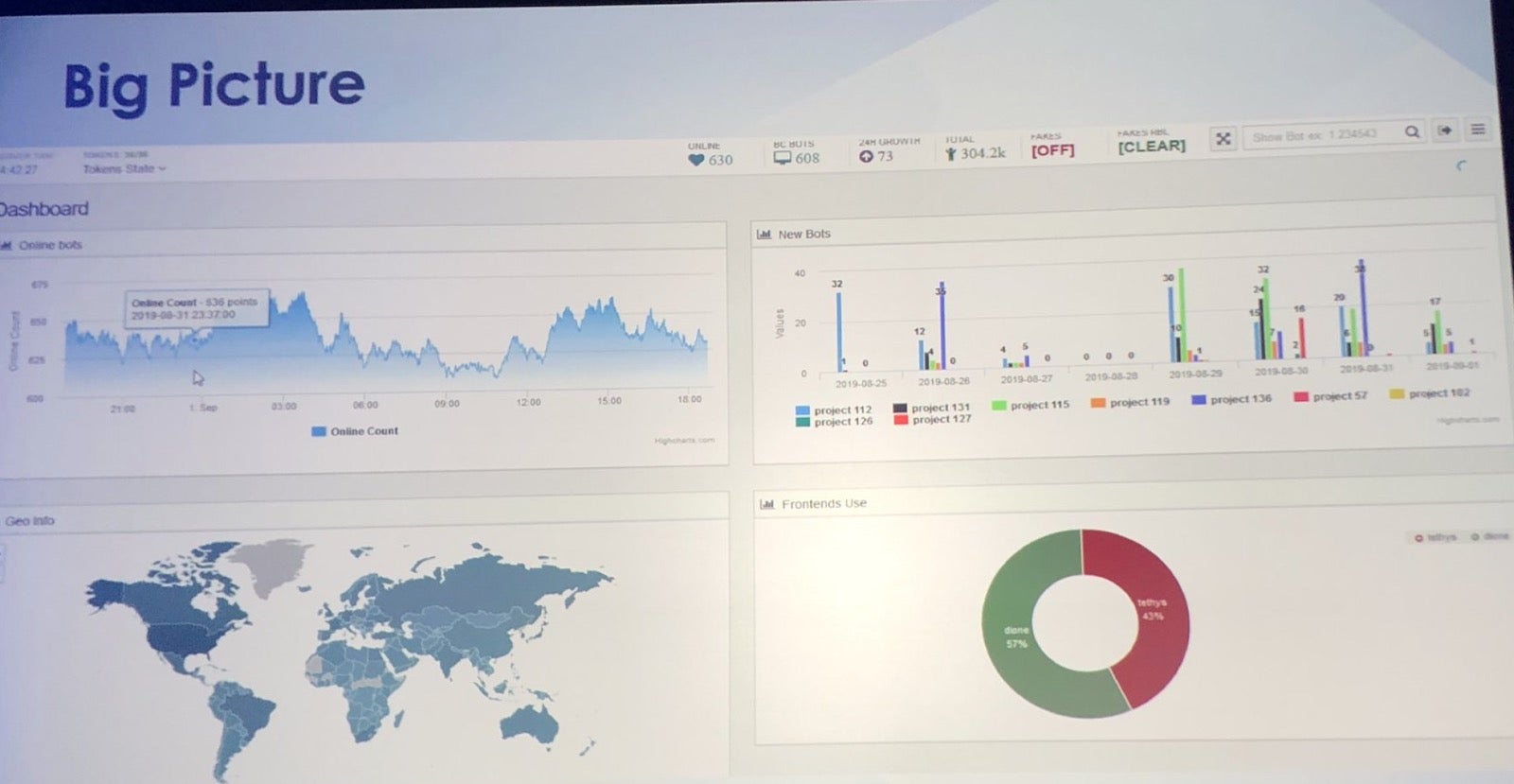
The IcedID/BokBot backend screenshot was displayed by the security researcher during the FireEye summit. It demonstrates the project-based IcedId structure SourceResearch Insight
Recent research has revealed the group has been targeting tax software and using custom kits to solicit important documentation from unsuspecting users. Recovered PowerShell scripts show they have been targeting tax returns and are actively harvesting the data. In the image below, specific tax software is targeted. It is worth noting the tax information appears to be for a prior year, which is usually necessary for filing current taxes. While the software is clearly defined, it is possible others have also been targeted in the past.
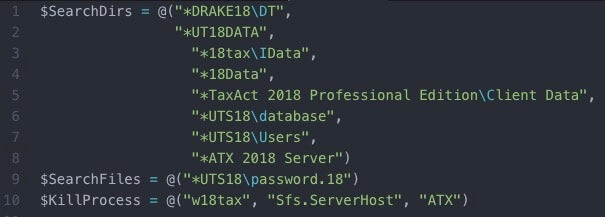 Tax Directories and files
Tax Directories and files
Next, the identified processes are killed and system drives are enumerated.
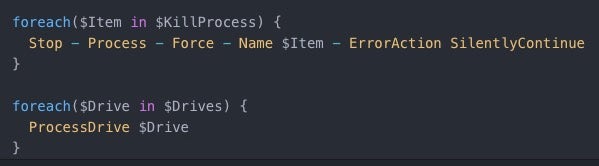 Processes killed and drives enumerated
Processes killed and drives enumerated
Finally, if the software is found the data is uploaded to the attackers’ servers using the PUT method to upload the file.
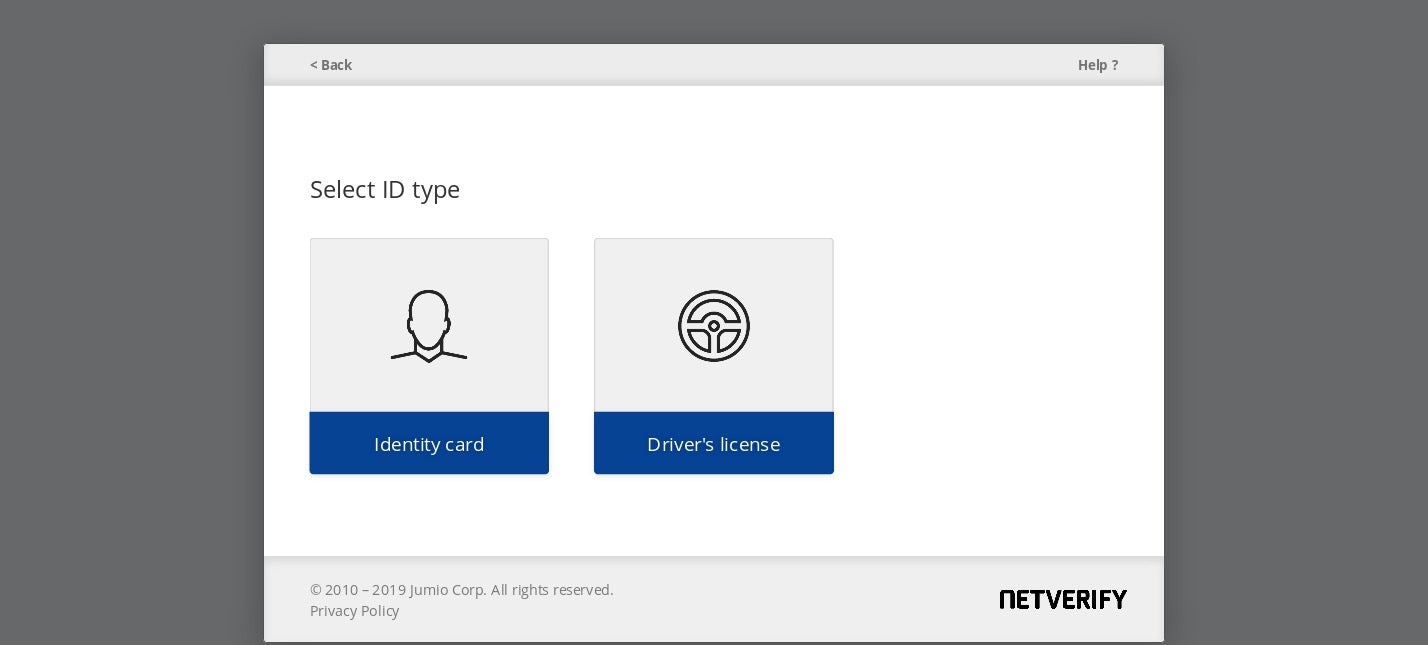
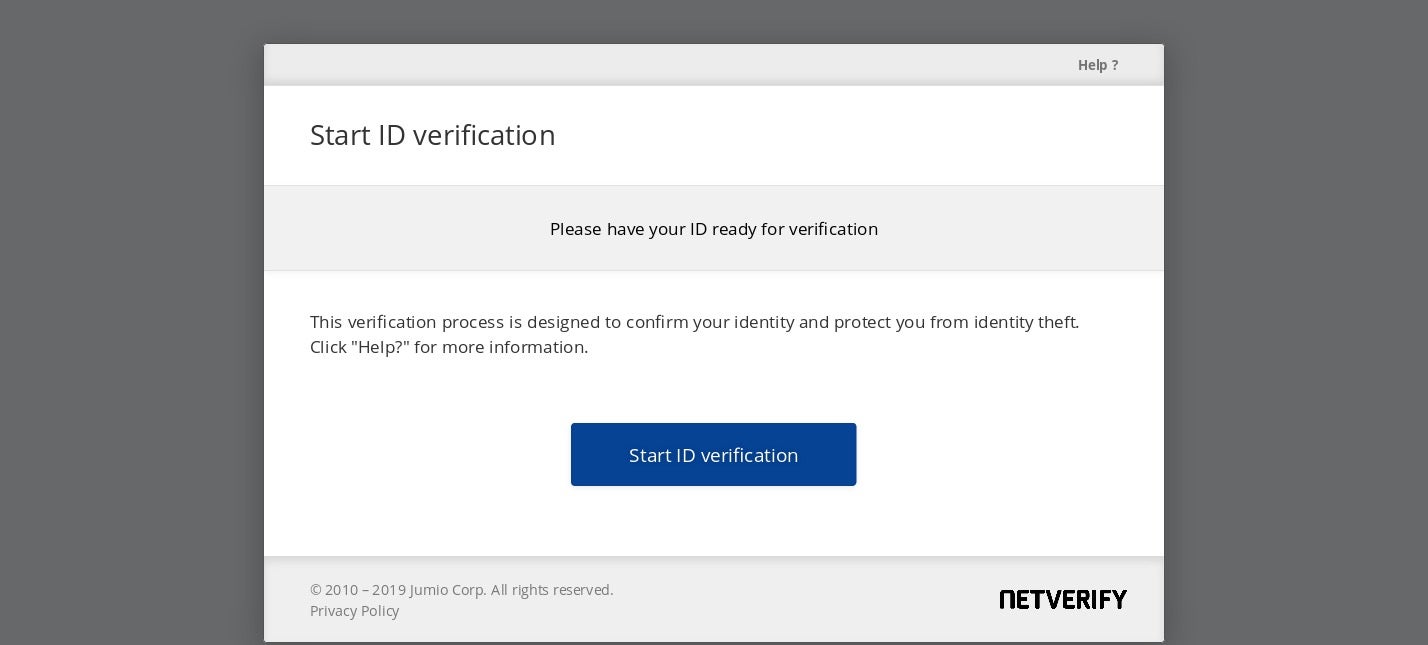
Upload functionAlong with stealing Tax documents, the IcedID gang uses social engineering to gain access to victims’ identity documents. In the images below, the IcedID actors masquerade as the Jumbio service Netverify and engineer users to upload their identification documents.
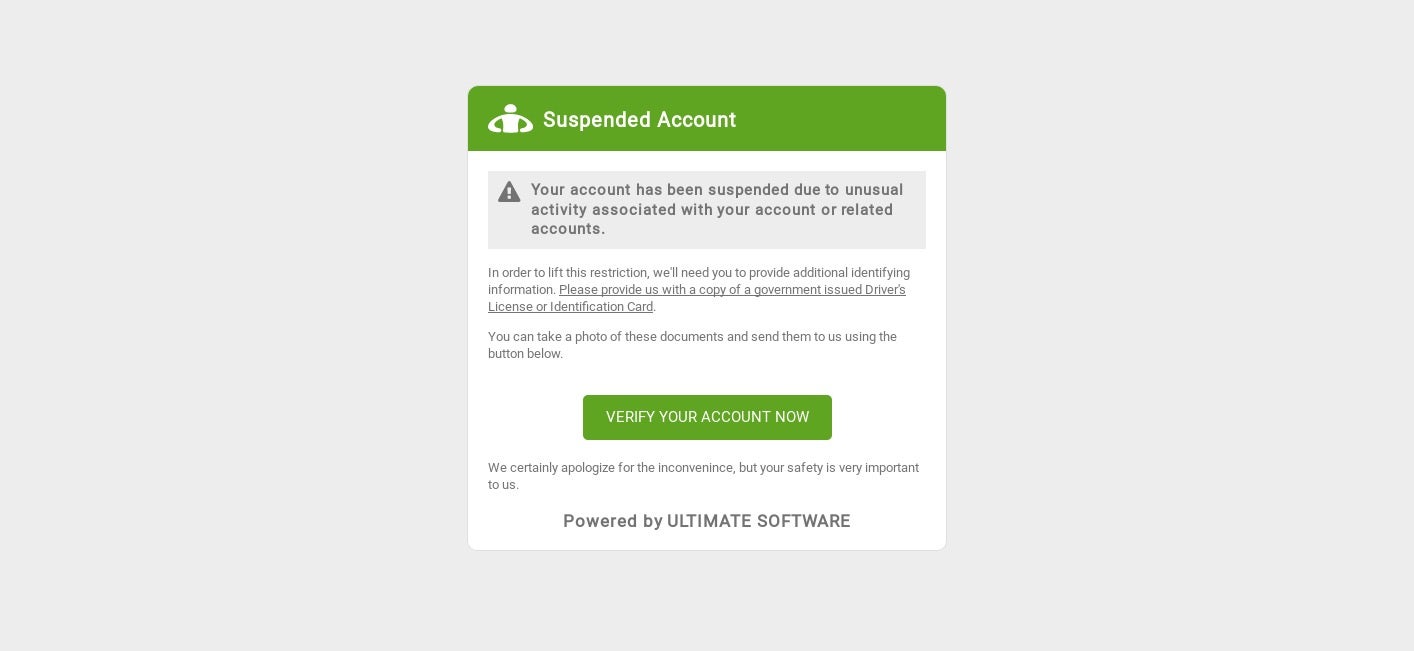
Netverify webfakeA secondary target for the IcedID gang is Ultimate software’s utilipro services.
Ultimate Software WebfakeConclusion
IcedID continues to evolve and operate in obscurity. However, IcedID is well-known for their banking operation; the operators demonstrate a more sophisticated side in the custom scripting, which is designed to locate and upload tax files. Couple this with a renewed interest by actors in targeting the tax season, in part due to the Covid-19 pandemic which has caused tax day to be extended to July 15.
The post ICEID Botnet | The Iceman Goes Phishing for US Tax Returns appeared first on SentinelLabs.
Article Link: https://labs.sentinelone.com/iceid-botnet-the-iceman-goes-phishing-for-us-tax-returns/