Cyber threat intelligence (CTI) is a framework for collecting, processing, and analyzing information about potential or ongoing cyber threats.
Put simply, it’s the collection of various types of threat intelligence, such as IOCs, TTPs used by threat actors, and their motivations and capabilities, with the ultimate goal of understanding your system’s attack surface and proactively patching vulnerabilities.
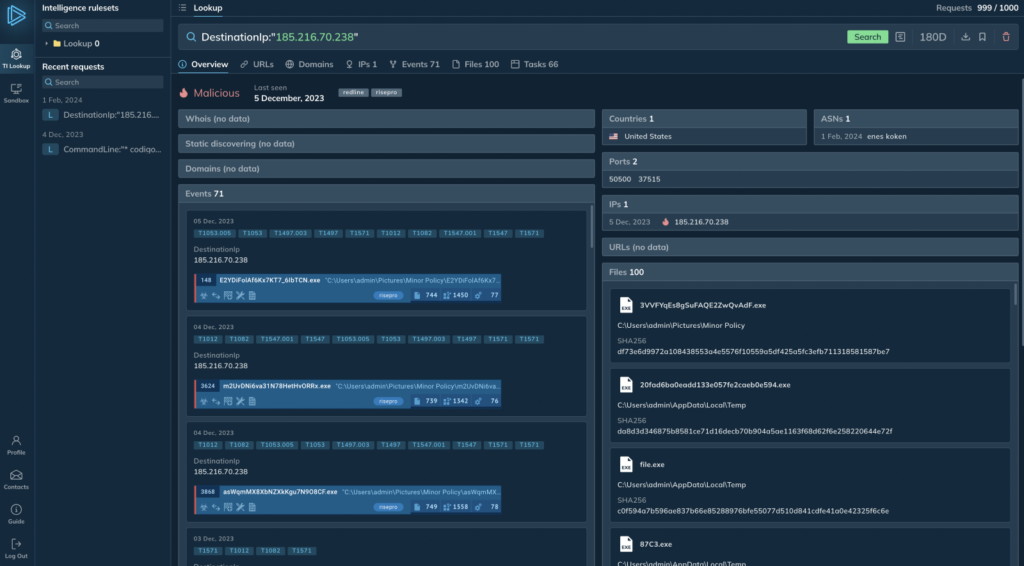 Link isolated IOCs to known threats with ANY.RUN TI Lookup
Link isolated IOCs to known threats with ANY.RUN TI Lookup But collecting data is one thing. Making sense of it is another. In this article, we’ll look at the different levels of threat intelligence, and a few examples of how to effectively collect data, and then — apply it.
Understanding 4 categories of Threat Intelligence
We can categorize threat intelligence into 4 categories based on the type of information and analysis scope:
1. Strategic
2. Operational
3. Technical
4. Tactical
Let’s break each one down in more detail
1. Strategic threat intelligence is the highest-level view of the threat landscape. It addresses things like threat actor trends, motivations, and capabilities, and answers questions like “Who can attack us and why?
 Examples of strategic TI tools
Examples of strategic TI tools- Threat landscape reports
- Geopolitical threat analysis
- APT profiles
2. Operational threat intelligence focuses on the TTPs used by threat actors and helps security teams detect and respond to threats effectively.
 Examples of operational TI tools
Examples of operational TI tools- TI platforms (OpenCTI)
- Lookup portals (Threat Intelligence Lookup)
- Sandboxes (ANY.RUN interactive malware sandbox)
3. Technical threat intelligence focuses on specific indicators of compromise, such as IP addresses, domain names, file hashes, and other technical artifacts. It helps configure security and monitoring systems to prevent or detect and stop attacks.
 Examples of technical TI tools
Examples of technical TI tools- Feeds (ANY.RUN Threat Intelligence Feeds)
- Network traffic analysis
- Deobfuscation and reverse engineering
4. Tactical threat intelligence is the immediate information you need to respond to threats here and now. It includes things like information about exploited vulnerabilities in your infrastructure or specific malware families involved in an ongoing attack.
 Examples of tactical TI tools
Examples of tactical TI tools- Incident response playbooks
- Malware analysis reports
- Vulnerability repair guides
Understanding Threat Intelligence lifecycle
The Threat Intelligence Lifecycle is a 6-step framework designed to help you keep pace with evolving threats.
Why it’s important
Hackers are constantly looking for new ways to attack; finding new vulnerabilities, morphing code, creating new versions of malware — today they might come at you with a baseball bat, tomorrow with a laser blaster. As a result, your attack surface is also in a constant state of flux. This means that your security posture must be as dynamic as the evolution of malware, ideally taking into account future threats.
The threat intelligence lifecycle is a 6-step process that helps you stay on top of current and future threats. Here’s how it works:
- Plan: First, you identify the critical assets you need to protect, define what information (intelligence) is needed to take protective action, and set measurable goals to know when you’ve established an effective TI strategy.
- Collect: Then, collect data from multiple sources, including open-source intelligence (OSINT), human intelligence (HUMINT), and technical sources: these are your logs and threat feeds.
- Process: Convert the collected data into a format that’s easy to analyze. This step typically includes data normalization, de-duplication, and enrichment.
- Analyse: Analyze the processed data. Look for patterns, trends, and potential threats. This stage often involves techniques such as data mining, machine learning, and statistical analysis.
- Disseminate: Share insights with stakeholders: security teams, executives, and external partners. Package your findings into reports and alerts. You can use a threat intelligence tool with built-in reporting to make this process easier.
- Get feedback: Use feedback from stakeholders to refine intelligence requirements, goals, and your overall security posture.
To be effective, this process exists in a state of constant iteration — it’s like a water mill that never stops.
How often should you run a threat intelligence lifecycle?
There is no one-size-fits-all solution, but as a general guideline, complete a full cycle every 1-3 months to keep your intelligence relevant. Review and update intelligence requirements quarterly and prioritize and distribute critical intelligence immediately: Establish clear criteria for knowing which alerts are and aren’t worth sharing immediately to avoid alert fatigue.
 TI lifecycle frequency
TI lifecycle frequency- Full cycle: Once every 1-3 months
- Reviews: Once per quarter
- Intelligence distribution: immediately (for critical threats)
Automated systems, such as TI feeds, ensure that you collect and process data from various sources continusly. This way the threat information your analyst can use remains always up-to-date.
Best practices for use of threat intelligence tools
There are many ways to incorporate threat intelligence tools into your strategy. Here are just a few.
Use threat intelligence feeds to set up early incident detection
TI Feeds provide data on the latest IOCs and the context of their use in real-world threats. This data is then fed into TIP and SIEM systems, where the security team can further enrich it and then configure automated security products such as EDR and WAF.
Tell us about your security goals
and find out if ANY.RUN TI Feeds are a good fit for you
Use a malware sandbox to analyze threats
Imagine a scenario: following suspicious network logs, you identify malicious behavior in the system, but even as you collect artifacts about the malware and identify the malicious executable, the threat still doesn’t fit any known profile. You’ve encountered something previously unknown, and you don’t know the extent of its impact on your system.
In this scenario, you need to figure out everything about what this threat is capable of as quickly as possible, in order to avoid responding to it blindly.
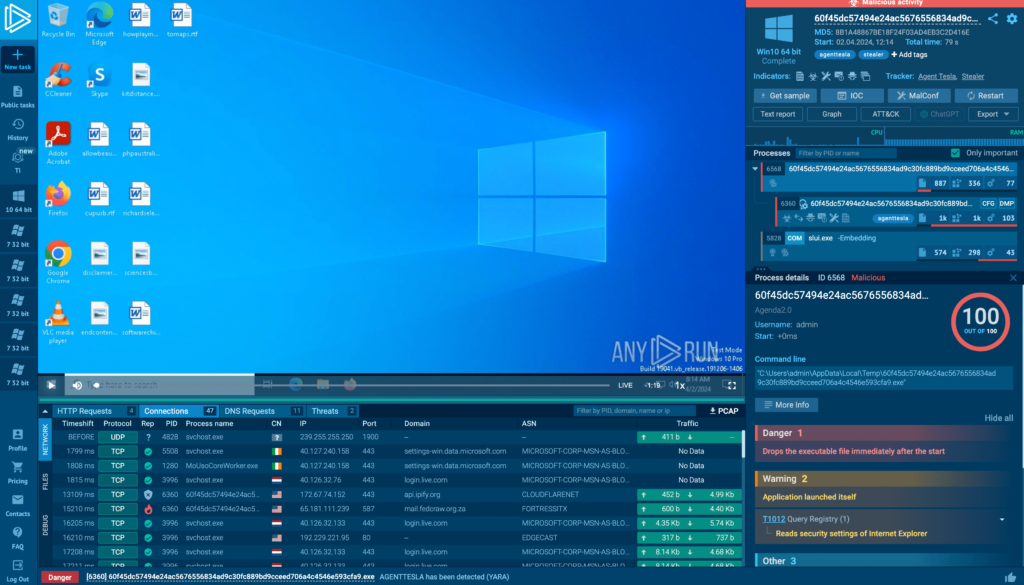 ANY.RUN malware sandbox gives immediate access to valuable threat data
ANY.RUN malware sandbox gives immediate access to valuable threat data You can use an interactive sandbox, like ANY.RUN, to upload the sample and let it run. Our sandbox is designed to allow malware to execute in an environment that closely resembles a real system, which you can set up to fit your specific execution context. As the malware executes, we collect events from the network, hard drive, and memory, and display them in real-time.
Try interactive malware analysis in ANY.RUN sandbox
Register for freeUse built-in reports to distribute threat intelligence
As we’ve discussed before, after analysis, it’s crucial to immediately share information with all relevant stakeholders and team members. However, creating a report can be a lengthy process. You can speed it up by using integrated reporting features, which most security products offer. For example, here are just a few options you can use in ANY.RUN:
In the context of immediate data sharing, a very useful report we use is the MITRE ATT&CK Matrix. It maps actions the malicious object performed in the system to techniques and links each TTP to full information from MITRE, which includes suggestions on how to mitigate it. Here’s what the TTP matrix looks like in ANY.RUN:
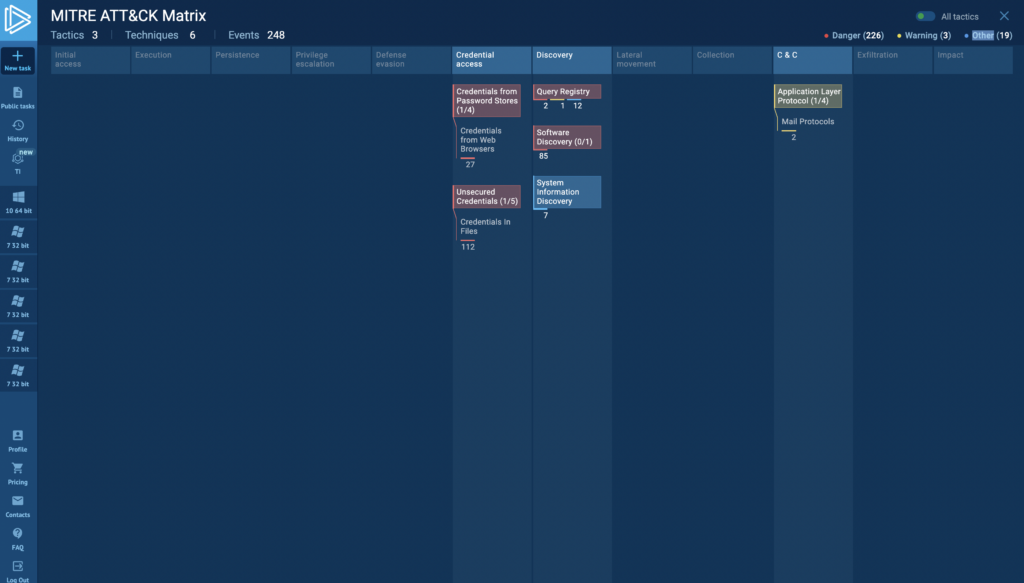 MITRE ATT&CK report in ANY.RUN
MITRE ATT&CK report in ANY.RUN You can also share full information about the results of your analysis, which is usually less relevant in the immediate context but is useful for sharing with stakeholders. In ANY.RUN, this can be done by generating text reports, which you can configure to include or omit information based on your specific analysis context, and share with a secure link — just as you would with a Google Doc.
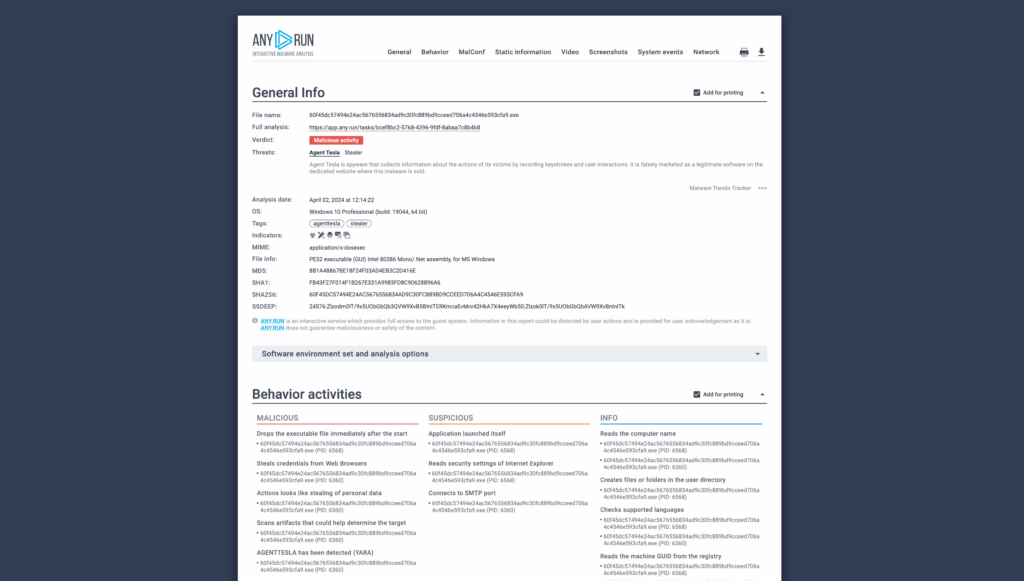 Text report example in ANY.RUN
Text report example in ANY.RUN About ANY.RUN
ANY.RUN’s flagship product is an interactive malware sandbox that helps security teams efficiently analyze malware.
Every day, a community of 400,000 analysts and 3000 corporate clients use our cloud-based platform to analyze Windows and Linux threats.
Integrate ANY.RUN Threat Intelligence in your organization
Contact SalesKey advantages of ANY.RUN for businesses:
- Interactive analysis: Analysts can “play with the sample” in a VM to learn more about its behavior.
- Fast and easy configuration. Launch VMs with different configurations in a matter of seconds.
- Fast detection: Detects malware within roughly 40 seconds of uploading a file.
- Cloud-based solution eliminates setup and maintenance costs.
- Intuitive interface: Enables even junior SOC analysts to conduct malware analysis.
Learn how ANY.RUN can benefit you or your security team. Schedule a free demo with one of our sales representatives, and we’ll walk you through real-world examples.
The post How to Use Cyber Threat Intelligence: the Basics appeared first on ANY.RUN's Cybersecurity Blog.
Article Link: How to Use Cyber Threat Intelligence: the Basics - ANY.RUN's Cybersecurity Blog