In my last article on Chinoxy backdoor, this version has its configuration in a resource called NNKK and it is deciphered. The purpose of this article is to explain the unpacking and deciphering of the configuration of this backdoor.
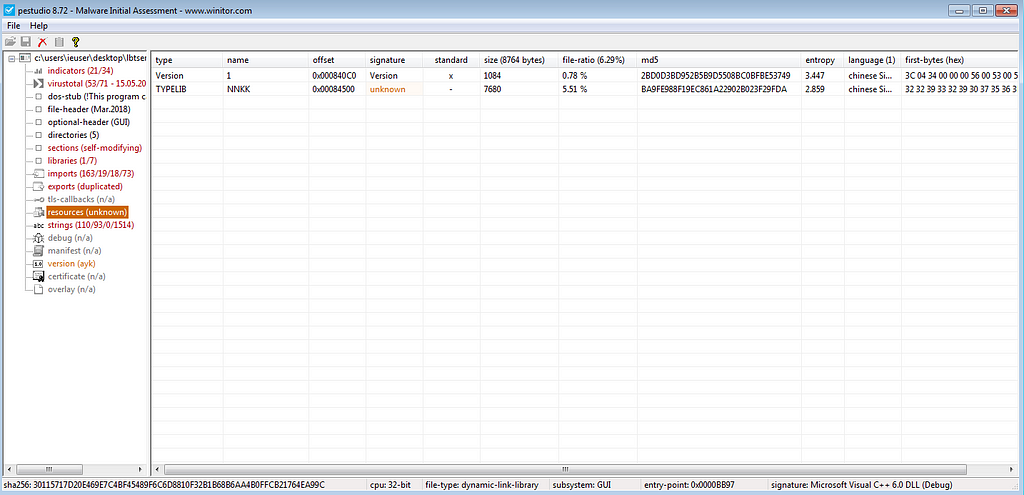
The backdoor is loading with the program confax.exe, a utility of Logitech for the Bluetooth.
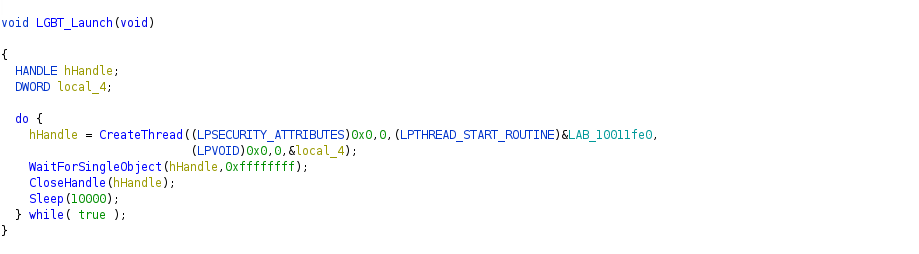
The function called by confax.exe is LGBT_Launch.
In checking this function,
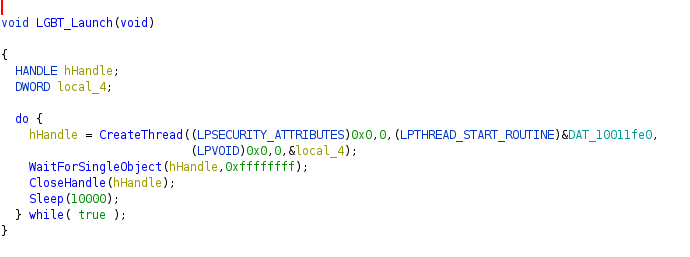
The entry of the thread is pointed by the address DAT_10011fe0. this address is in the section .bss. This section has rwx and the entropy is very high.
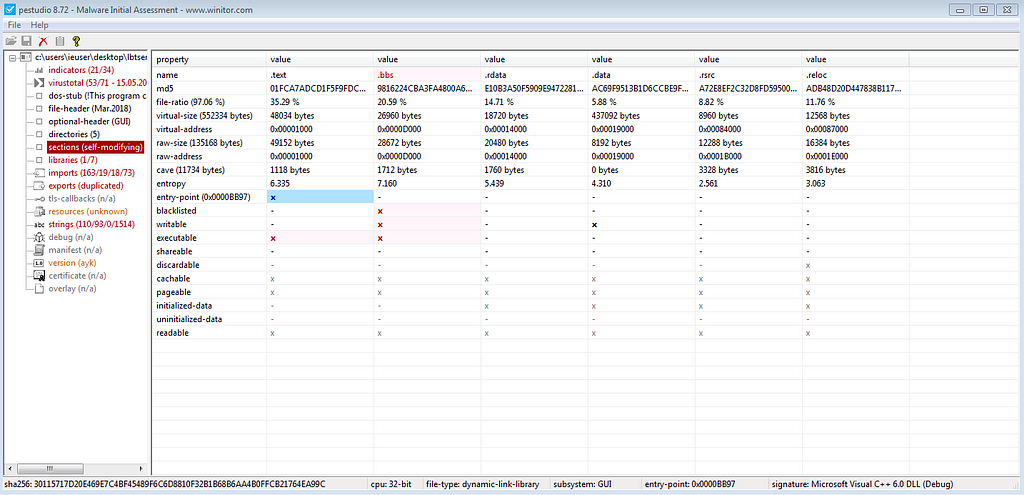
Before the unpack, there are not a call with the function using this resource.
And at the address DAT_10011fe0, there is just data without code.
So the unpack procedure is using the entrypoint of the backdoor, and the code is executing when confax.exe load LBTServ.dll.
The entrypoint of the dll, the function interesting is FUN_10007800.
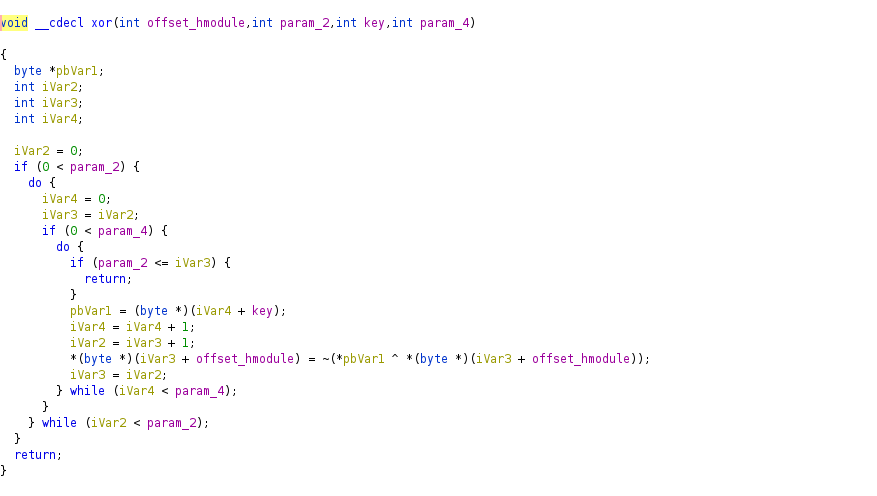
the code call the function 10007770 with two parameters: an handle on the dll and the key hceqhqn of the xor.

In this function, the xor is at the end of the function after manipulating the the &DAT_1001a7dc for a copy.
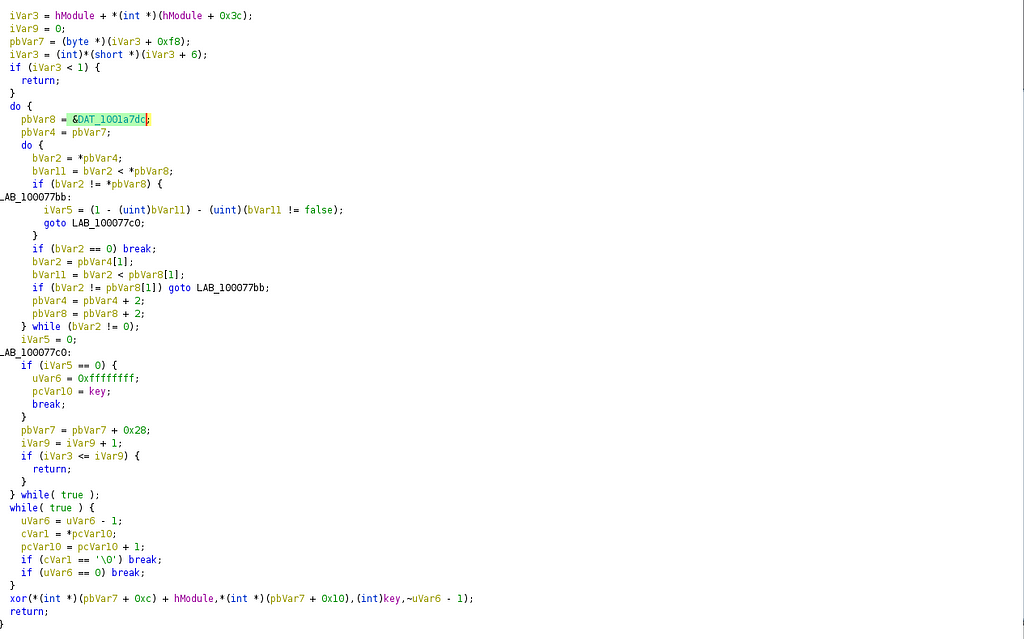
the xor function is located at 10007730.
And after the function, if the dll is dumped. We found the good function of the thread and the function manipulating the resource.

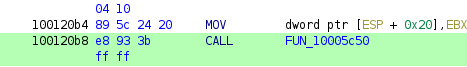
So we check the function 10005c50 using this resource called by the thread.
In this function, the ressource is locked and two keys are catching:

The keys are just top of the resource of TYPELIB.
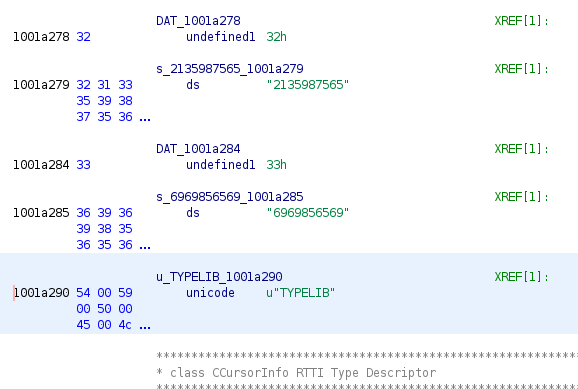
And the deciphered function is the function 10005bf0.
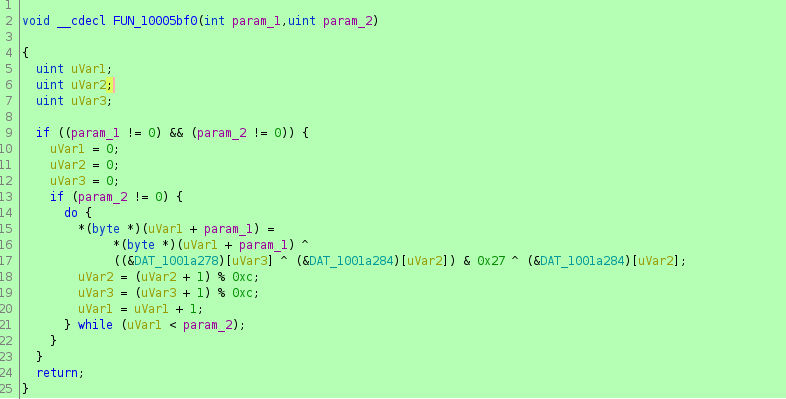
the param1 is the pointer on the resource and the param 2 the number of the step for the loop deciphering.
In python, the algorithm is the following. with the RatDecoders, we found the resource
from malwareconfig import fileparser
import binascii
rsc = file_info.pe_resource_by_name(‘NNKK’)
key_1= b’369698565690'
key_2= b’221359875650'
res=b’’.join([chr((key_1[i%12] ^ key_2[i%12]) & 0x27 ^ key_1[i%12] ^ rsc[i]).encode() for i in range(0,0x1300)])
res.replace(b’\x00',b’’).replace(b’0',b’’)
we have like result:
b'\x0f0\xc2\xb7\xc2\x99\x03YnJh0bmRzLm05ld3N00LmRuc20Fici5j0b206Mz0AxMHxi0cmFuZH0MubmV30c3QuZG05zYWJy0LmNvbT0ozMDEw0fHJ1Lm01zdC5k0bnMtY20xvdWQu0bmV0Oj0MwMTB800000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000se0rver.d0ll000000000000000000001234qw0er00000De0fault 0Group000005300000001.000000000006604893880000000000'
with a little cleaning, and base64 ninja, we have the result.
brands.newst.dnsabr.com:3010|brands.newst.dnsabr.com:3010|ru.mst.dns-cloud.net:3010|
This IOCs has been already done.
Conclusion
the purpose of this article is to explain to unpack quickly the Chinoxy backdoor and retrieve the configuration without reverse the backdoor.
Article Link: How to unpack Chinoxy backdoor and decipher the configuration of the backdoor | by Sebdraven | Medium