A Complete Walkthrough of Intezer’s Autonomous SOC Platform
In the rapidly evolving world of cybersecurity, the industry faces a significant challenge: a growing shortage of skilled professionals. As the complexity and volume of threats increase, the demand for expertise in managing security operations far outstrips the available supply. This is where Intezer steps in. We have developed an Autonomous SOC platform that automates the process of alert triage and incident response, effectively augmenting your security team’s capabilities.
This article provides a technical overview of how our platform works, from monitoring to reporting. We will delve into each stage of our process, explaining how we collect and analyze data, how we determine the risk level of each alert, and how we respond to confirmed threats — providing you with a comprehensive understanding of how Intezer works to keep your organization secure and team members happy.
Mimicking Expert Security Analysts
Our platform is designed to mimic the actions of an expert human analyst, collecting as much evidence as possible, conducting thorough investigations, and making informed decisions based on the data. By automating these processes, we allow your security team to focus on their core responsibilities, improving efficiency and effectiveness.
To provide a clear understanding of how Intezer works, here’s a high-level overview of our process:
- Monitor – Intezer continuously monitors and collects alerts 24/7 from your integrated security tools, ensuring that no potential threat goes unnoticed.
- Collect Evidence – Upon receiving an incoming alert, Intezer collects all relevant data associated with the alert, including files, processes, command lines, evidence from process arguments, URLs, IPs, parent and child processes, memory images, and more.
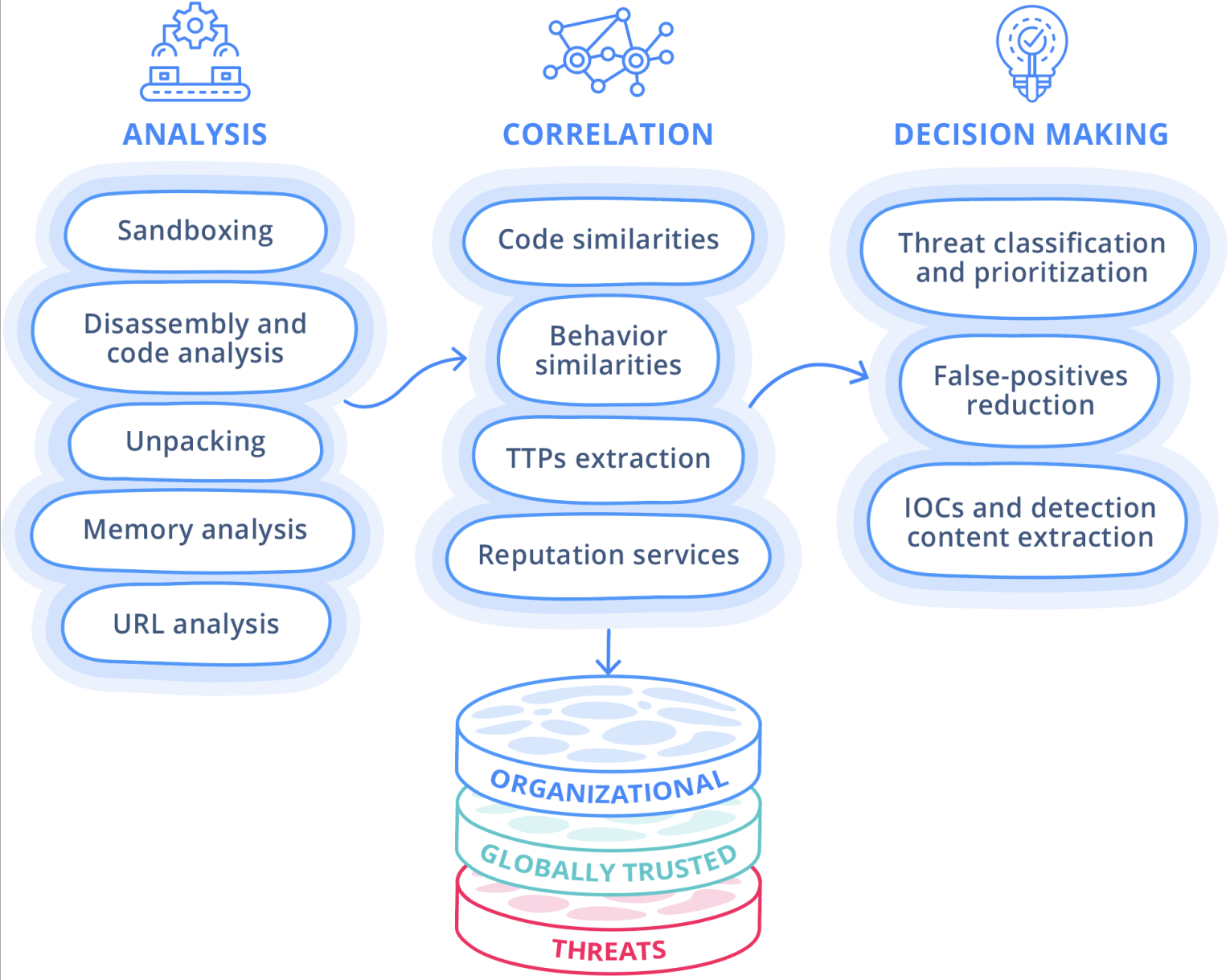
- Investigate – Intezer analyzes each piece of collected evidence using a variety of sophisticated techniques, including sandboxing, genetic analysis, static analysis, open-source intelligence (OSINT), memory analysis, and reverse engineering. The results of these individual analyses are then summarized into a cohesive incident-wide assessment using AI models.
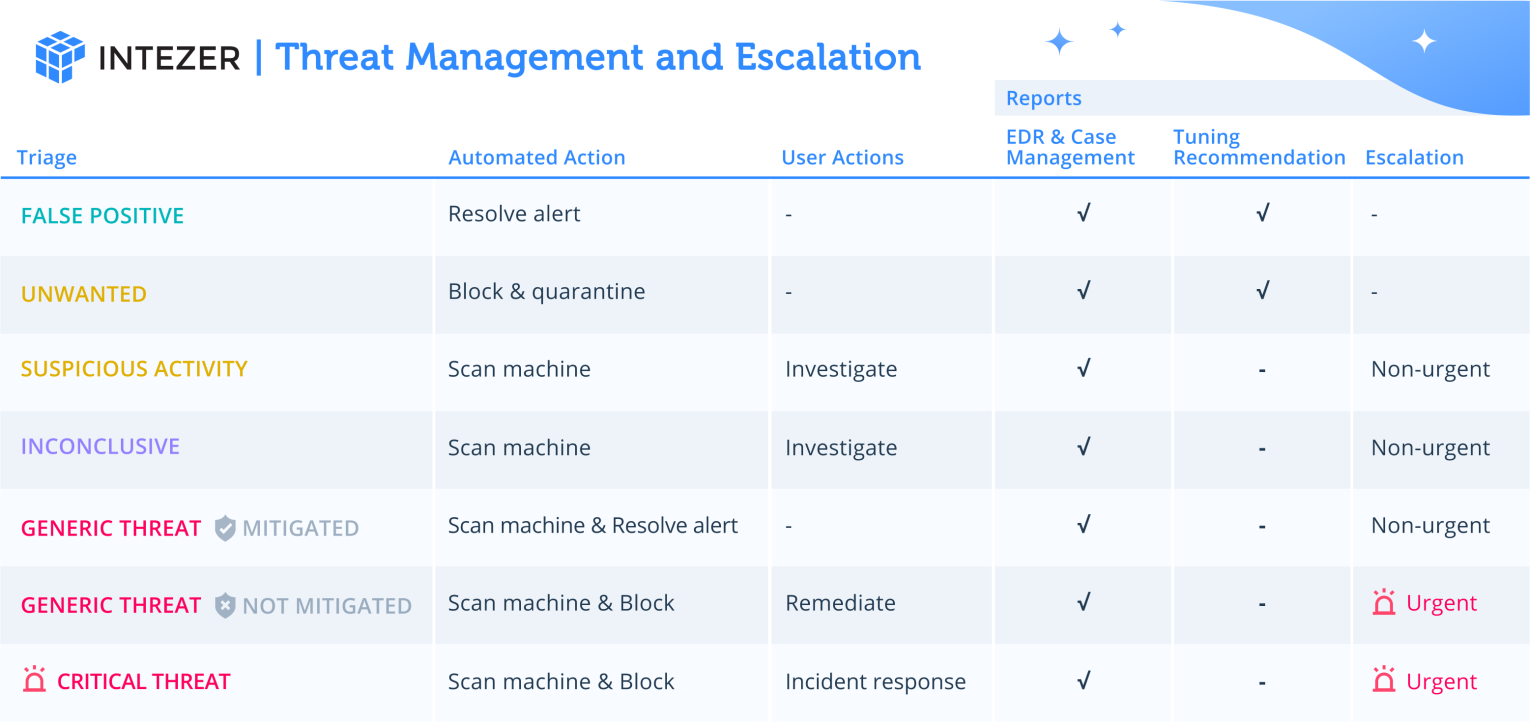
- Triage – Intezer categorizes the risk associated with each alert and decides whether to escalate it based on the investigation results. In addition, Intezer reduces noise by auto-resolving false positives within your detection systems.
- Respond – For confirmed threats, Intezer provides assessments and recommendations, including detection content and ready-to-use hunting rules, to guide the response process. Intezer can also conduct automated deeper forensics if needed.
- Report – Intezer generates weekly reports to keep your team informed and provide tuning suggestions, allowing for continuous improvement in your security operations.
By automating these processes, Intezer enhances the efficiency and effectiveness of your security team, allowing them to focus on their core responsibilities.

1. Monitor
Our platform connects directly to your alert sources via API Key, and within the same hour, it starts ingesting alerts automatically 24/7. This ensures a seamless and immediate integration of our system with your existing security infrastructure.
The main alert source Intezer supports are endpoint security tools (Crowdstrike, SentinelOne, and Microsoft Defender). These tools are widely used in the industry and generally provide the most important alerts for our platform to analyze, as they provide the deepest visibility to assets in the organization. Importantly, Intezer pulls the alerts directly from these endpoint security tools using their APIs, ensuring real-time, accurate data for analysis. Intezer monitors ALL types of alerts, including fileless threats and alerts that are based on suspicious activity.
In addition to endpoint security tools, we also connect with Security Orchestration, Automation, and Response (SOAR) tools through a dedicated app in each of those vendors’ marketplace. Currently, we support Splunk Phantom, XSOAR, and Chronicle/Siemplify. Connecting via SOAR allows our users to leverage Intezer’s decision-making and analysis capabilities for a wide range of custom alert sources and playbooks, including the investigation of suspicious emails and employee-reported phishing.
Through the combination of endpoint security tools and SOAR, your team should be able to cover the main part of their workload. Furthermore, we are committed to expanding our integration capabilities to meet your evolving security stack.
2. Collect Evidence
Once an alert is detected, the next step is to collect evidence. This involves gathering all relevant data associated with the alert, a process that mirrors what an expert human analyst would do. The goal is to collect as much evidence as possible to provide a comprehensive view of the potential threat.
The types of evidence we collect are wide-ranging and thorough. They include files, processes, command lines, evidence from process arguments, URLs, parent and child processes, memory images, and more. This extensive collection of evidence allows us to gain a deep understanding of the alert and the potential threat it represents.
We collect this evidence using the API of the security tool that fired the alert and the API of the endpoint security tool. This approach allows us to gather both textual information from the raw alert data, such as IPs/URLs, and actual artifacts from the endpoint, such as files and processes.
It’s important to note that the automatic collection of many artifacts from endpoints is a complex task. It requires sophisticated engineering to handle edge-cases, reduce duplicates, and more. However, at Intezer, we have invested heavily in developing the capabilities to carry out this task effectively and efficiently. This ensures that our platform can provide the most comprehensive and accurate analysis of each alert, allowing your security team to respond effectively to each potential threat.
3. Investigate
The investigation stage is where Intezer truly shines. It is also a critical part of our process, where the goal is to assign a verdict (true/false positive), risk level, and recommended next steps for each alert. This is achieved by conducting a thorough investigation for each piece of evidence separately, assigning a verdict (malicious, trusted, and others), and classification (malware family, threat actor, or software vendor in case it is trusted) for each individual piece of evidence.
Each individual artifact is analyzed using a variety of sophisticated techniques, including sandboxing, genetic analysis, static analysis, open-source intelligence (OSINT), memory analysis, and reverse engineering. These techniques allow us to gain a deep understanding of the behavior of the threat, its origin, and its potential impact.
Once all individual pieces of evidence have been analyzed, we then provide an assessment for the entire alert, taking into account the investigation results of multiple pieces of evidence. This summary of all individual analyses into a coherent incident-wide verdict, risk level, and recommended next steps is done via smart machine learning models and AI algorithms.
The alert investigation summary can be seen either in Intezer’s alert page, inside your security tool that fired the alert, or alternatively via API.
This approach makes it easy for the user to understand the overall assessment while still enabling the user to dig into each individual artifact and explore why exactly we came to a certain conclusion. By providing both a high-level overview and detailed analysis, we ensure that your security team has all the information they need to respond effectively to each potential threat.
4. Triage
The triage stage is where we determine the appropriate response based on the risk level determined in the investigation stage. Here, we decide whether an alert should be escalated or resolved as a false positive.
Escalated alerts are those that our platform identifies as requiring further attention. These can be notified via email or any other webhook-supported system, as described in our documentation. The notification method is configurable by the user, allowing for seamless integration with your existing workflows.
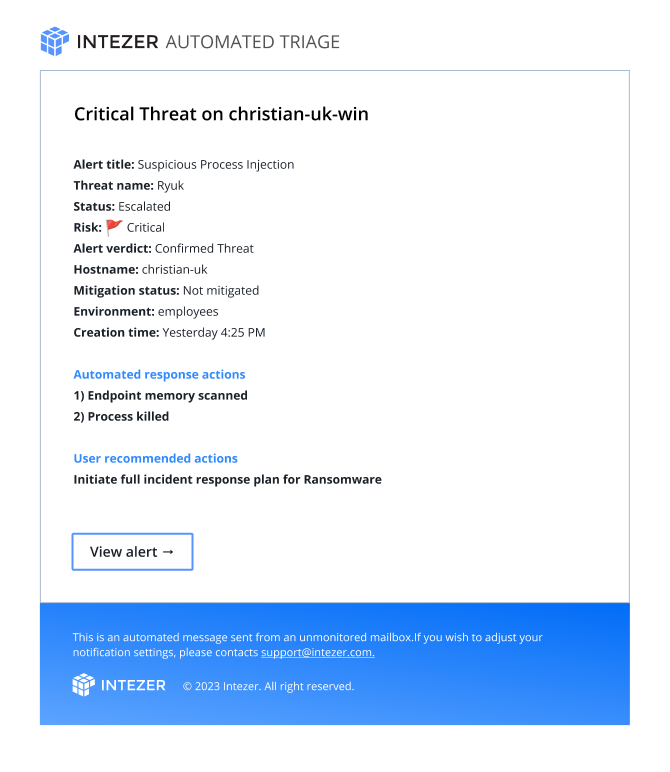
The decision to escalate an alert is not made lightly. It combines both Intezer’s sophisticated algorithm and the user’s configuration to suit the security team’s policies and workflows. Our algorithm takes into account both the investigation results done by Intezer as well as information from the security tool that originally fired the alert, to ensure maximum efficacy. For more information on how we handle incident escalations, please refer to our dedicated article on the subject.
On the other hand, alerts that are determined to be false positives can be automatically resolved within the tool that originally fired the alert. This feature is designed to reduce noise and ensure that your security team can focus on the alerts that truly matter. By automating this process, we save your team from time wasted on false positives and too many escalated alerts.
5. Respond
The response stage is all about taking action. Based on the recommended next steps determined in the investigation stage, Intezer acts to mitigate the potential threat.
The possible responses can vary depending on the nature of the threat and the recommended next steps. They can include conducting deeper forensics on the endpoint, applying Indicators of Compromise (IOCs) and other hunting rules, or other recommended next steps that are based on industry best practices.
In this stage, Intezer leverages the integrated security tools to carry out these actions. For example, using the endpoint security tool, Intezer can remotely execute its deep memory scan to conduct deeper forensics on a suspicious endpoint, if needed. This allows us to gather more information about the threat and develop a more effective response.
Looking ahead, we are working on expanding our response capabilities to automatically apply IOCs and hunting rules directly to your security tools. This will further streamline the response process, allowing your security team to respond to threats more quickly and effectively.
6. Report
The final stage in our process is reporting. Intezer generates weekly reports to keep your team focused on what matters most and provide tuning suggestions. These reports provide a clear and concise summary of all the threats detected and actions taken during the week, allowing your team to easily track their progress and adjust their strategies as necessary.
How is it different from automatic playbooks?
While some tasks in the six-step process can be automated via SOAR or other security automation products, there are several key differences that set Intezer’s Autonomous SOC apart.
Firstly, most tasks in traditional playbooks still require significant human involvement due to the decision-making needed. This includes deciding if an alert is a false positive or not, when to escalate, and more. Intezer’s platform, on the other hand, uses sophisticated algorithms to make these decisions, reducing the need for human intervention.
Secondly, truly automating tier-1 triage requires heavy custom engineering to create production-ready playbooks. For example, collecting a variety of evidence from actual endpoints, while addressing many edge-cases, is a challenging task to develop. Intezer has invested heavily in this area, developing capabilities that can handle these complex tasks effectively and efficiently.
Thirdly, even if you manage to do the required complex engineering, you often end up with large playbooks that are hard to maintain and keep up-to-date. This includes the need to maintain licenses and up-to-date logic of numerous third-party products to help automate the alert triage process, including a sandbox, URL scanner, reputation databases, reverse engineering platform, and more. Intezer’s platform, however, is designed to function as an all-in-one analysis platform, reducing the burden on your security team.
For more details about the difference between Intezer and SOAR platforms, and why they work so well together, please refer to our dedicated article.
Learn more
Discover how Intezer can help you automate your alert triage and decision-making processes for security alerts. We invite you to schedule your demo now, and our dedicated team will provide prompt assistance, ensuring you gain valuable insights into the capabilities of Intezer.
The post How Intezer Works appeared first on Intezer.
Article Link: How Intezer Works