The widely-used industrial software development kit, CODESYS, has been found to harbor multiple security vulnerabilities. Moreover, researchers have identified a significant issue within Python’s URL parsing function, which undermines the efficacy of domain and protocol filtering methods.
In this blog post, we take a close look at these recent vulnerabilities and provide solutions for the security concerns entwined with the dynamically evolving landscape of security vulnerabilities.
Total of 16 Vulnerabilities in CODESYS SDK: CoDe16
Researchers at Microsoft have uncovered 16 high-severity vulnerabilities within the CODESYS V3 software development kit (SDK).
CODESYS is compatible with over a thousanddifferent device types from over 500 manufacturers, and it is used by millions of devices to implement the international industrial standard IEC 611131-3, which is a standard for Programmable Logic Controllers (PLCs).
The vulnerabilities, grouped together as CoDe16, could be exploited by an attacker to achieve remote code execution (RCE) and carry out Denial-of-Service (DoS) attacks in certain circumstances. This puts operational technology (OT) environments at risk of being compromised.
Among these vulnerabilities, one of the CVEs has been assigned a severity rating of 7.5 (CVE-2022-47391), with the rest receiving a CVSS score of 8.8.
CODESYS Exploitation Could Potentially Shut Down a Power Plant
According to researchers, a Denial-of-Service (DoS) attack against a power plant’s device using a vulnerable version of CODESYS could cause the entire power plant to shut down. Furthermore, exploiting a remote code execution vulnerability could potentially allow attackers to establish a backdoor.
Exploiting these vulnerabilities necessitates user authentication and an understanding of CODESYS V3’s exclusive protocol as well as the various services it employs.
In their investigation, researchers effectively employed 12 instances of buffer overflow vulnerabilities to achieve remote code execution on PLCs. To carry out such an exploit, an attacker would also need to bypass the PLCs’ Data Execution Prevention (DEP) and Address Space Layout Randomization (ASLR) features.
To get past the user authentication, researchers used a known vulnerability, identified as CVE-2019-9013. This enabled a replay attack against the PLC by exploiting the unsecured username and hashed password transmitted during the sign-in process.
Proof-of-Concept Available: ASLR Bypass for CODESYS Exploit
The researchers also provided a video Proof-of-Concept (PoC), showcasing an attack that bypasses ASLR.
The exploit process involves stealing credentials using the CVE-2019-9013 vulnerability, setting up a new attack channel, logging into the device with the stolen credentials, exploiting vulnerabilities using a malicious packet to trigger buffer overflow, and ultimately gaining full control of the device.
More information on the vulnerabilities in CODESYS V3 can be found in the CoDe16 GitHub repository.
Ensuring Security for Industrial Control Systems: Apply Patches
Microsoft issued an advisory stating that the discovered vulnerabilities emphasize the importance of ensuring the security of industrial control systems. They also underscore the necessity for consistently monitoring and safeguarding these environments.
To ensure the security of industrial control systems, it is critical to actively apply patches to affected devices within your network and update device firmware to version 3.5.19.0 or higher. Disconnect and segment all critical devices, such as PLCs, routers, and PCs, from the internet, regardless of whether they run CODESYS.
Only permit access to CODESYS devices from authorized components. Given the nature of the CVEs, which still require a username and password, if prioritizing patching is challenging, mitigate risk by implementing proper segmentation, requiring unique usernames and passwords, and reducing the number of users with writing authentication.
High-Severity Vulnerability in Python URL Parsing Function: CVE-2023-24329
The Python URL parsing function has revealed a high-severity security flaw that attackers could potentially use to bypass domain or protocol filtering methods implemented with a blocklist.
This flaw affects the widely utilized parsing function, urllib.parse, which allows breaking down URLs into their constituents or combining components to form a URL string.
Security experts have assigned the identifier CVE-2023-24329 (CVSS score: 7.5) to this flaw. If exploited, it could lead to unauthorized file access and the execution of arbitrary commands.
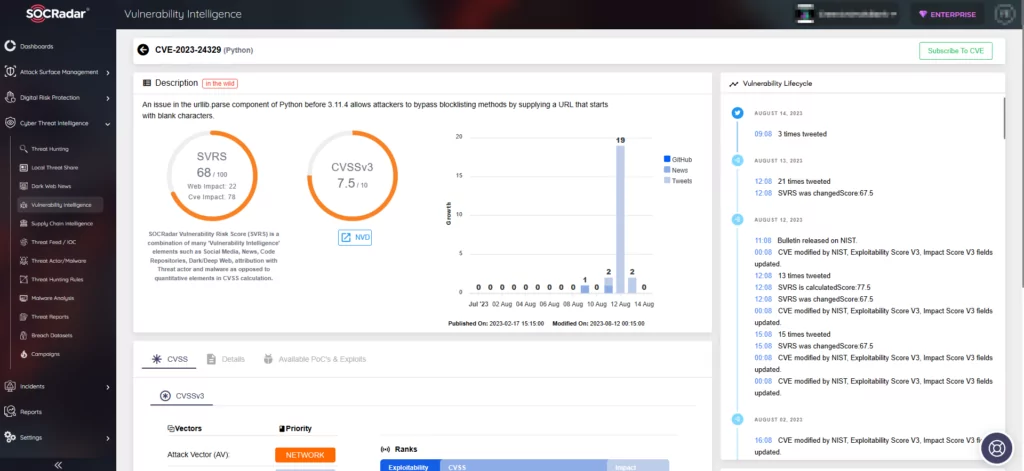 Details of CVE-2023-24329 on SOCRadar
Details of CVE-2023-24329 on SOCRadar
URLparse Issue: Blank Characters Exploit and Blocklist Bypass
The CERT Coordination Center (CERT/CC) stated in an advisory that there exists a parsing issue within urlparse when the entire URL begins with blank characters. This issue impacts both the parsing of the hostname and scheme, consequently causing the failure of any blocklisting methods.
The vulnerability CVE-2023-24329 emerges due to lack of input validation. This leads to a situation where bypassing blocklisting methods becomes achievable by providing a URL that initiates with blank characters.
Versions Patched for CVE-2023-24329 Vulnerability
The problem has been resolved in the subsequent versions:
- Version 3.12 or later
- Versions 3.11.x starting from 3.11.4
- Versions 3.10.x starting from 3.10.12
- Versions 3.9.x starting from 3.9.17
- Versions 3.8.x starting from 3.8.17
- Versions 3.7.x starting from 3.7.17
Stay Ahead of Vulnerability Exploitation with SOCRadar
SOCRadar’s Vulnerability Intelligence helps you effectively manage security vulnerabilities and prioritize essential patches. You can easily search for and find detailed information about vulnerabilities using the SOCRadar XTI platform, staying ahead of possible threats.
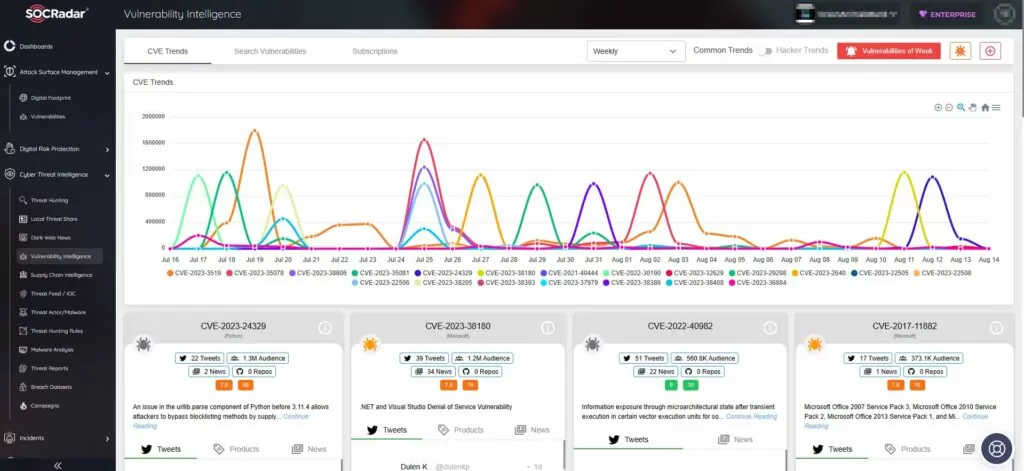 SOCRadar Vulnerability Intelligence under Cyber Threat Intelligence
SOCRadar Vulnerability Intelligence under Cyber Threat Intelligence
Additionally, our External Attack Surface Management (EASM) is vital for safeguarding your digital assets. SOCRadar actively discovers and monitors your digital environment using this advanced system, quickly alerting you to any emerging issues that might put your security at risk. With SOCRadar, you can be confident that we are actively protecting your online presence.
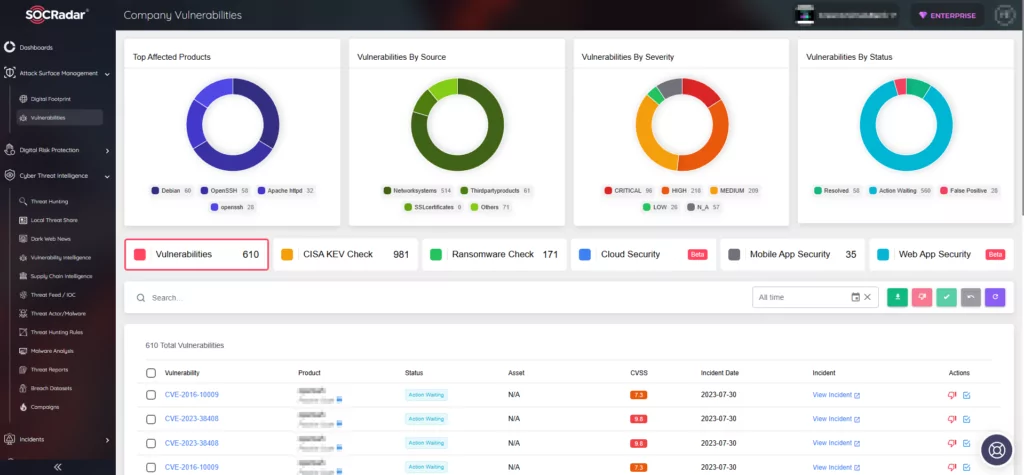 SOCRadar Company Vulnerabilities under Attack Surface Management (ASM)
SOCRadar Company Vulnerabilities under Attack Surface Management (ASM)
The post High-Severity Vulnerabilities in CODESYS V3 SDK and Python’s URLlib.parse Library appeared first on SOCRadar® Cyber Intelligence Inc..
Article Link: High-Severity Vulnerabilities in CODESYS V3 SDK and Python’s URLlib.parse Library
