VMware has addressed two critical vulnerabilities in VMware Tools, CVE-2023-34057 and CVE-2023-34058, both carrying high severity scores. These vulnerabilities can enable threat actors to escalate privileges or bypass SAML token signatures, risking the confidentiality and integrity of services.
VMware Tools encompasses a range of services and modules designed to enhance VMware product functionality. Installed on the guest operating system, it offers features including improved graphics performance, networking, storage, seamless VMware hypervisor integration, and enhanced management.
Details of the Vulnerabilities Affecting VMware Tools (CVE-2023-34057 and CVE-2023-34058)
CVE-2023-34057 is a privilege escalation vulnerability in VMware Tools for macOS operating systems with a CVSS score of 7.8. According to VMware’s advisory, a local user with access to a guest virtual machine can exploit this vulnerability to gain elevated privileges within that virtual machine.
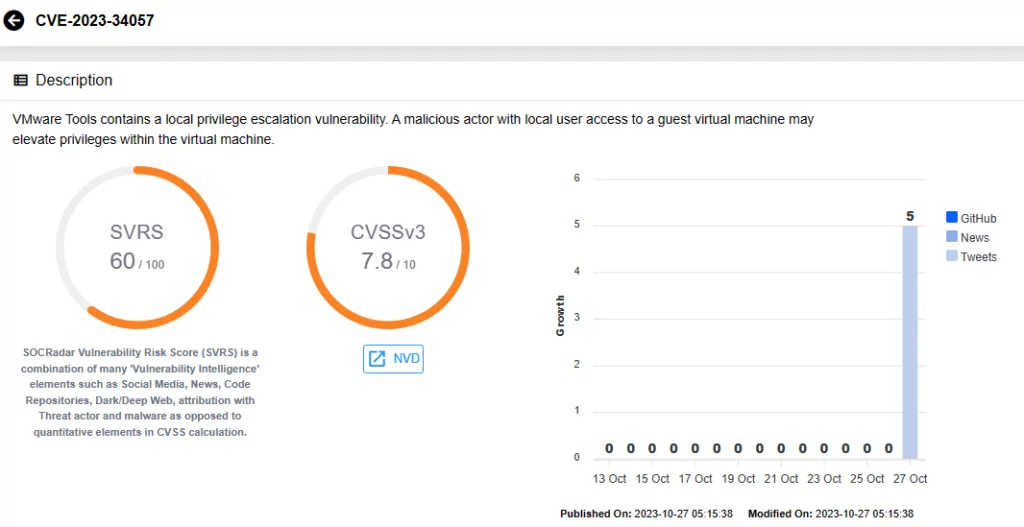 Vulnerability card for CVE-2023-34057 on SOCRadar
Vulnerability card for CVE-2023-34057 on SOCRadar
The second vulnerability, CVE-2023-34058, has a CVSS score of 7.5 and affects VMware Tools on Windows operating systems. The vulnerability enables an attacker to bypass SAML Token Signature, but only if they are assigned Guest Operation Privileges in the target virtual machine, and the target virtual machine has been assigned a more privileged Guest Alias.
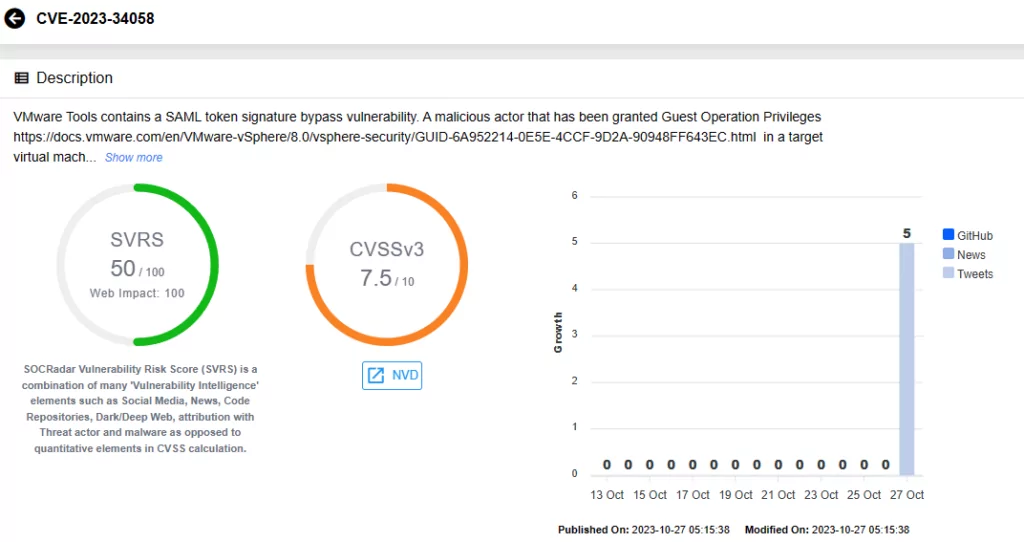 Vulnerability card for CVE-2023-34058 on SOCRadar
Vulnerability card for CVE-2023-34058 on SOCRadar
VMware acknowledges that CVE-2023-34058 also impacts open-vm-tools, and notes that fixes are provided to the Linux community for distribution.
Which Versions of VMware Tools are Affected by CVE-2023-34057 and CVE-2023-34058?
CVE-2023-34057 affects VMware Tools versions 12.x.x, 11.x.x, and 10.3.x on macOS. Similarly, CVE-2023-34058 impacts the same versions of VMware Tools, but on Windows operating systems.
How to Fix the Vulnerabilities? Is There a Mitigation Available?
The VMware advisory does not list any available workarounds for these vulnerabilities. Therefore, it is crucial to promptly install the patches that VMware has released for your virtual machines to prevent the exploitation of these vulnerabilities.
CVE-2023-34057 has been resolved by VMware through the release of a patch in VMware Tools version 12.1.1 for macOS.
As for the CVE-2023-34058 vulnerability, affecting Windows builds, patches have been made available in version 12.3.5.
CISA Issues Alert for the Critical Vulnerability in VMware vCenter Server (CVE-2023-34048) Fixed in the Previous Patch
Recently, before patching the vulnerabilities in VMware Tools, VMware addressed a critical out-of-bounds write vulnerability (CVE-2023-34048, CVSS score: 9.8) and a moderate-severity information disclosure flaw (CVE-2023-34056, CVSS score: 4.3). These vulnerabilities were both discovered in vCenter Server, VMware’s widely-used server management software.
The Cybersecurity and Infrastructure Security Agency (CISA) issued an alert yesterday, announcing the availability of updates for CVE-2023-34048 and CVE-2023-34056. The U.S. agency underscored the potential for remote cyber actors to exploit these vulnerabilities for obtaining information or system control. CISA warned users against such risks, urging them to promptly apply the necessary patches to secure their VMware vCenter Servers.
CVE-2023-34048 resides in the implementation of the DCE/RPC protocol (a protocol for remote procedure calls). It permits an attacker with network access to a vulnerable vCenter Server virtual appliance to trigger an out-of-bounds write, potentially leading to remote code execution.
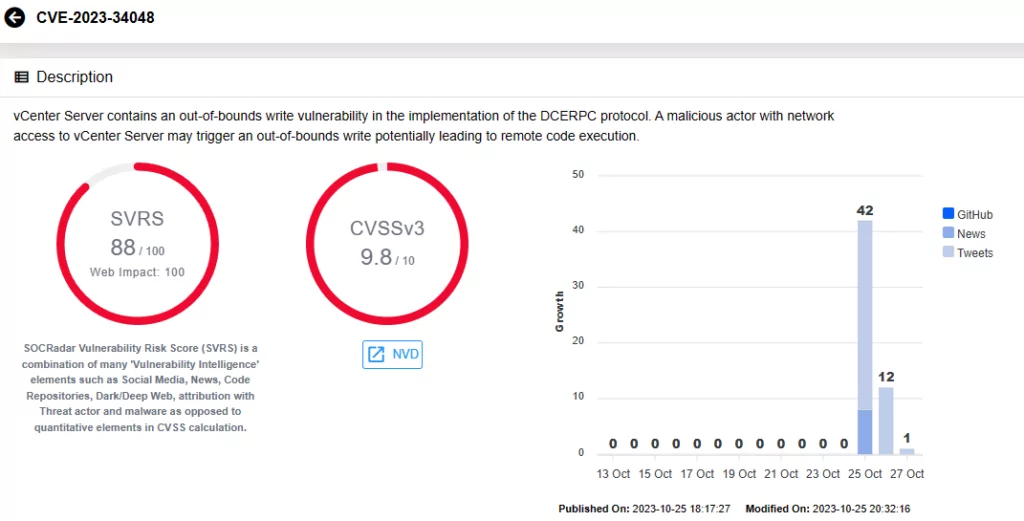 Vulnerability card for CVE-2023-34048 on SOCRadar
Vulnerability card for CVE-2023-34048 on SOCRadar
CVE-2023-34056 is described as a partial information disclosure vulnerability, which a malicious actor with non-administrative privileges to vCenter Server could exploit to access unauthorized data.
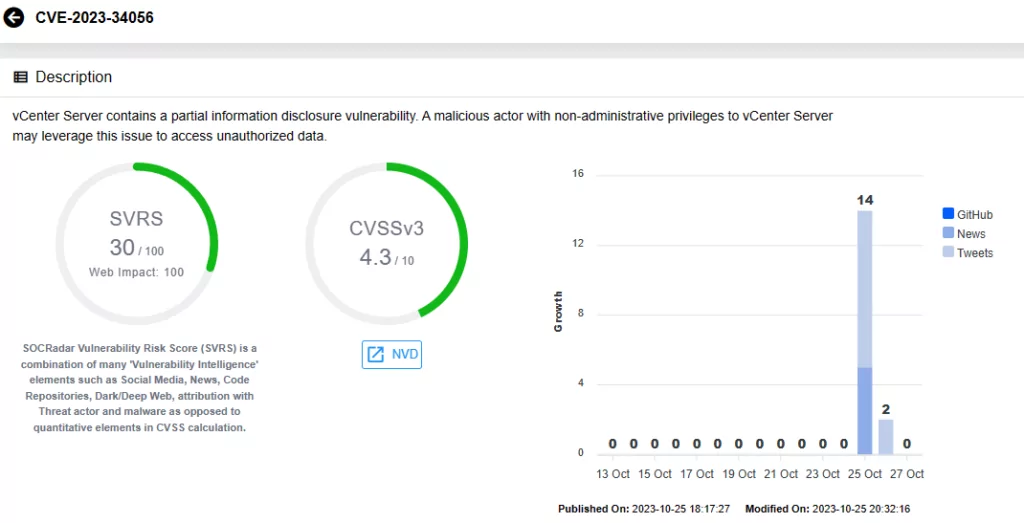 Vulnerability card for CVE-2023-34056 on SOCRadar
Vulnerability card for CVE-2023-34056 on SOCRadar
While there have been no reported instances of these vulnerabilities being exploited in the wild, considering the absence of available mitigation methods, users are strongly advised to apply patches immediately to thwart potential exploitation by threat actors.
Which Versions of vCenter Server Are Affected by CVE-2023-34048 and CVE-2023-34056?
The vulnerabilities impact VMware vCenter Server versions 4.x, 5.x, 7.0, and 8.0.
The advisory states that in-product workarounds were investigated for CVE-2023-34048 but were deemed unviable. Due to the critical severity of this vulnerability and the absence of a feasible workaround, VMware has made patches widely accessible for vCenter Server 6.7U3, 6.5U3, and VCF 3.x. Additionally, VMware has released additional patches for vCenter Server 8.0U1.
Utilize SOCRadar’s Attack Surface Management to Minimize Risks of Exploitation
SOCRadar maintains continuous monitoring of emerging security threats, updating the platform with vital information regarding vulnerabilities, encompassing their details, mentions, PoC exploits, lifecycle data, and the proprietary SOCRadar Vulnerability Risk Score (SVRS). To access a wealth of information on the latest vulnerabilities, simply search within the Vulnerability Intelligence tab under the Cyber Threat Intelligence module.
 Vulnerability Intelligence (SOCRadar CTI module)
Vulnerability Intelligence (SOCRadar CTI module)
Moreover, SOCRadar, through the Attack Surface Management (ASM) module, diligently observes your organization’s digital presence, tracks assets, and issues alerts in the event of emerging threats.
 Company Vulnerabilities (SOCRadar ASM module)
Company Vulnerabilities (SOCRadar ASM module)
The post High-Severity VMware Tools and vCenter Server Vulnerabilities Addressed with Recent Patches (CVE-2023-34057, CVE-2023-34058, CVE-2023-34048) appeared first on SOCRadar® Cyber Intelligence Inc..
