On December 14th, 2023, shortly after the launch of our Holiday Bug Extravaganza, we received a submission for an Arbitrary File Upload vulnerability in File Manager Pro, a WordPress plugin with an estimated 10,000+ active installations. This vulnerability made it possible for authenticated attackers to create a PHP file that could contain malicious content and be used for complete site takeover.
Props to Tobias Weißhaar who discovered and responsibly reported this vulnerability through the Wordfence Bug Bounty Program. This researcher earned a bounty of $657.00 for this discovery during our Bug Bounty Program Extravaganza. Although the installation count would typically place this vulnerability out of scope for our bug bounty program, the severity and ease of exploitation combined with the much larger installation count of the free version of the plugin warranted some flexibility.
Wordfence Premium, Wordfence Care, and Wordfence Response users received a firewall rule to protect against any exploits targeting this vulnerability on January 8, 2024. Sites still using the free version of Wordfence will receive the same protection on February 7, 2024.
We contacted the File Manager developer team on December 14th, 2023, and received a response on December 15th, 2023. After providing full disclosure details, the developer released a patch on January 8th, 2024.
We urge users to update their sites with the latest patched version of File Manager Pro, version 8.3.5 at the time of this writing, as soon as possible.
Did you know we’re running a Bug Bounty Extravaganza again? Earn over 6x our usual bounty rates, up to $10,000, for all vulnerabilities submitted through February 29th, 2024!
Vulnerability Summary from Wordfence Intelligence
Affected Plugin: File Manager Pro
Plugin Slug: wp-file-manager-pro
Affected Versions: <= 8.3.4
CVE ID: CVE-2023-6846
CVSS Score: 8.8 (High)
CVSS Vector: CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H
Researcher/s: Tobias Weißhaar
Fully Patched Version: 8.3.5
Bounty Award: $657.00
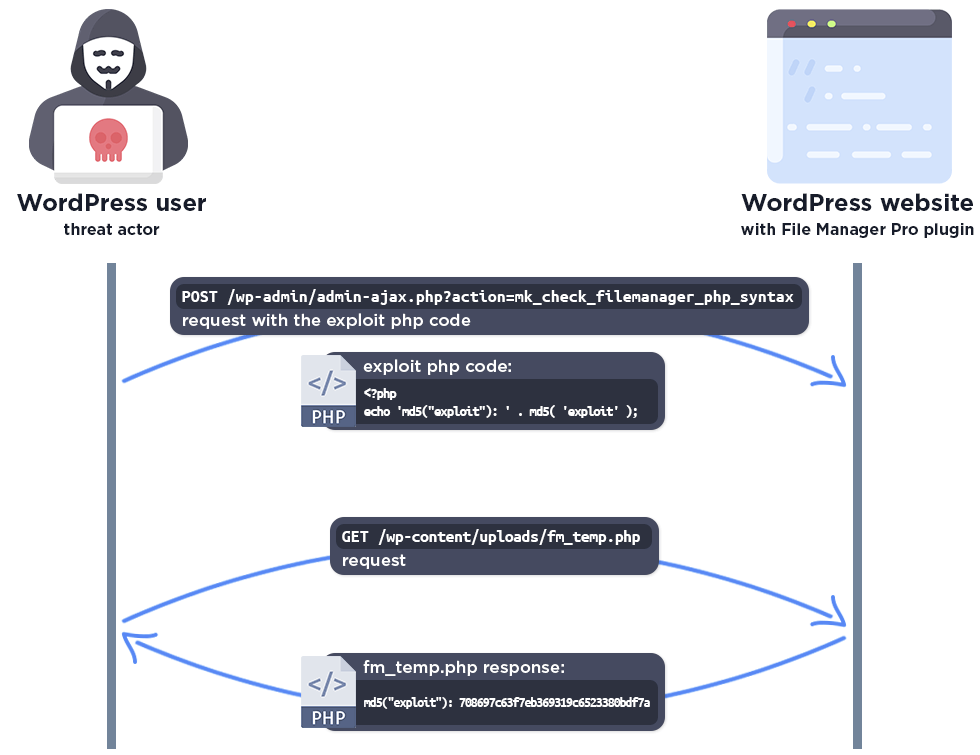
The File Manager Pro plugin for WordPress is vulnerable to Arbitrary File Upload in all versions up to, and including, 8.3.4 via the mk_check_filemanager_php_syntax AJAX function. This makes it possible for authenticated attackers, with subscriber access and above, to execute code on the server. Version 8.3.5 introduces a capability check that prevents users lower than admin from executing this function.
Technical Analysis
The File Manager Pro plugin is the premium version of the most popular File Manager WordPress plugin, which includes many premium features and functions. One such feature is the syntax checker, which completes code reviews for errors before saving files.
Examining the code reveals that the plugin uses the mk_check_filemanager_php_syntax_callback() function to check the php syntax via AJAX.
add_action('wp_ajax_mk_check_filemanager_php_syntax', array(&$this, 'mk_check_filemanager_php_syntax_callback'));
/* Check php Syntax Errors */
public function mk_check_filemanager_php_syntax_callback()
{
$filename = isset($_POST[‘filename’]) ? sanitize_file_name($_POST[‘filename’]) : ‘’;
$fileMime = isset($_POST[‘filemime’]) ? sanitize_mime_type($_POST[‘filemime’]) : ‘’;
$code = stripslashes($_POST[‘code’]);
if (is_user_logged_in() && $fileMime == ‘text/x-php’) {
$current_user = wp_get_current_user();
$upload_dir = wp_upload_dir();
if (isset($current_user->user_login) && !empty($upload_dir[‘basedir’])) {
$fm_temp = $upload_dir[‘basedir’].‘/fm_temp.php’;
$handle = fopen($fm_temp, ‘w’);
fwrite($handle, $code);
$check = shell_exec('php -d display_errors=1 -l '.$fm_temp);
if(empty($check)){
echo '<p>('.__('Unable to execute php syntax checker due to server permissions.', 'wp-file-manager-pro').')</p>';
} elseif(strpos($check, 'No syntax errors') === false) {
$check = str_replace('on line', 'on line number', $check);
echo str_replace($fm_temp, '<strong>'.$filename.'</strong>', $check);
echo '<p>('.__('File', 'wp-file-manager-pro').' <strong>'.$filename.'</strong> '.__('not saved.', 'wp-file-manager-pro').')</p>';
} else {
echo '1';
}
}
} else {
echo '1';
}
die;
}
The function creates the temp file, and puts the php code in it. After that, it executes a syntax check only, which is completely safe as it is not possible to execute the code.
But the temp file is not deleted immediately. The remove_fm_temp_file() function deletes the temp file, which is added to the admin_init hook, but it only runs when the admin page is reloaded. This means there is a period of time where the test file lives on the server before it is deleted, making it accessible to a threat actor.
add_action('admin_init', array(&$this, 'remove_fm_temp_file'));
/* Remove Fm Temp File */
public function remove_fm_temp_file()
{
$upload_dir = wp_upload_dir();
$fm_temp = $upload_dir[‘basedir’].‘/fm_temp.php’;
if (file_exists($fm_temp)) {
unlink($fm_temp);
}
}
Unfortunately no capability checks were used in the vulnerable versions, there is only a check to verify that the user is logged in to WordPress, and the temp file is not immediately deleted either. This means that any logged in user, such as a subscriber, can add any PHP code to the temp file and subsequently access it. This makes it possible for attackers to upload arbitrary malicious PHP code and then access the file to trigger remote code execution on the server.
The complete exploit process looks like this:
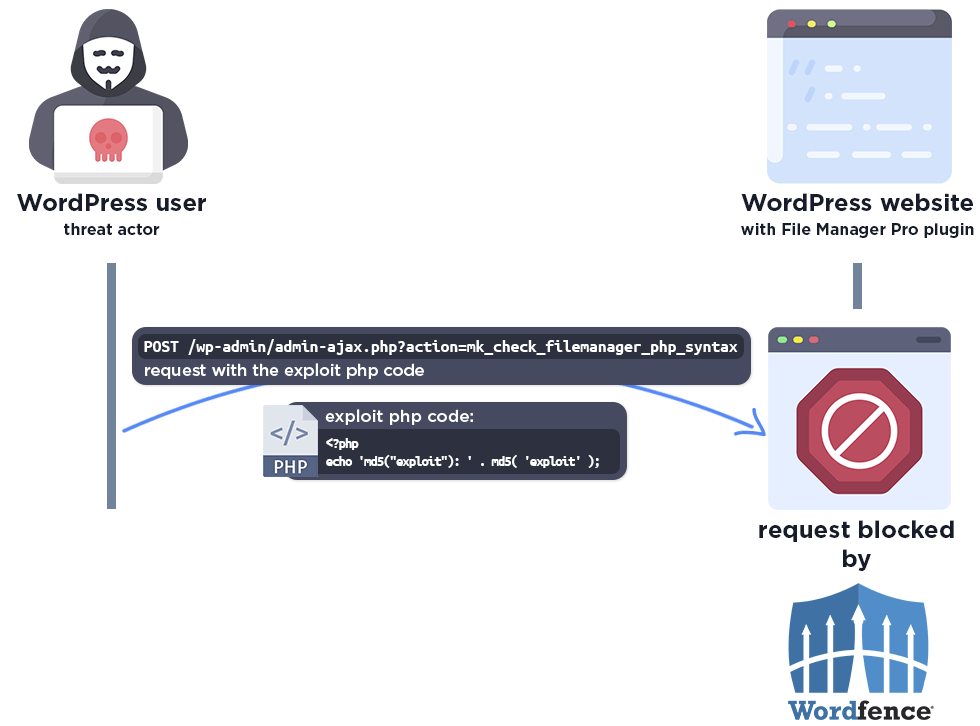
Wordfence Firewall
The following graphic demonstrates the steps to exploitation an attacker might take and at which point the Wordfence firewall would block an attacker from successfully exploiting the vulnerability.
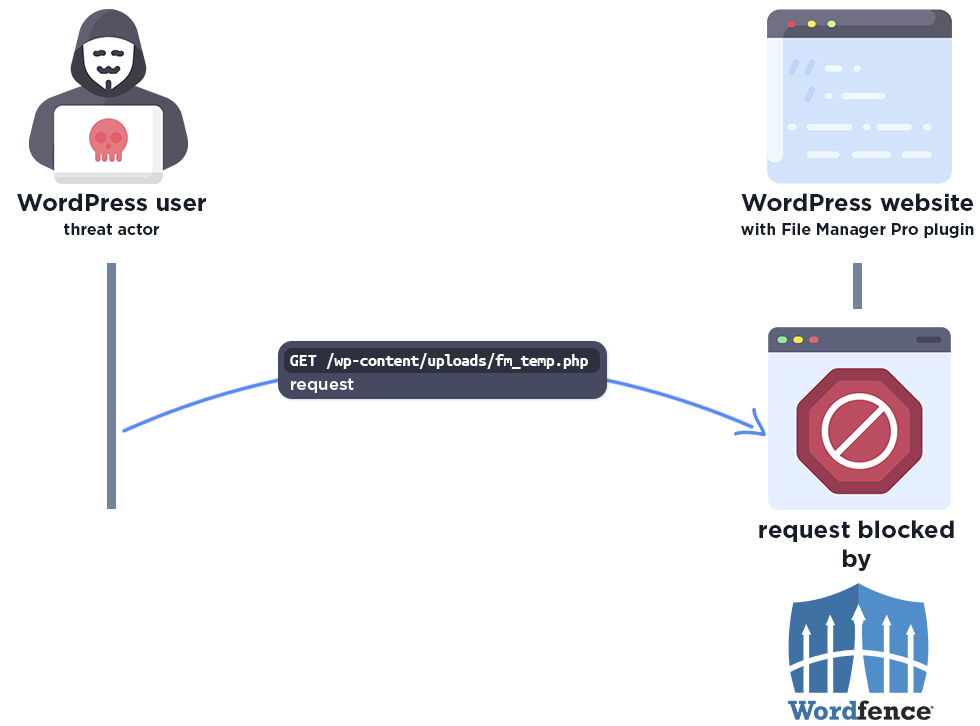
The firewall also blocks access to the temp file:
Disclosure Timeline
December 14, 2023 – We receive the submission of the Arbitrary File Upload vulnerability in File Manager Pro via the Wordfence Bug Bounty Program. We initiate contact with the plugin vendor asking that they confirm the inbox for handling the discussion.
December 15, 2023 – The vendor confirms the inbox for handling the discussion.
December 15, 2023 – We send over the full disclosure details. The vendor acknowledges the report and begins working on a fix.
January 8, 2024 – We see that version 8.3.5 of the plugin is released, and we validate it.
January 8, 2024 – Wordfence Premium, Care, and Response users receive a firewall rule to provide protection against any exploits that may target this vulnerability.
February 7, 2024 – Wordfence Free users receive the same protection.
Conclusion
In this blog post, we detailed an Arbitrary File Upload vulnerability within the File Manager Pro plugin affecting versions 8.3.4 and earlier. This vulnerability allows authenticated threat actors, with minimal permissions, to execute malicious code on the server. The vulnerability has been addressed in version 8.3.5 of the plugin.
We encourage WordPress users to verify that their sites are updated to the latest patched version of File Manager Pro.
Wordfence users running Wordfence Premium, Wordfence Care, and Wordfence Response have been protected against these vulnerabilities as of January 8, 2024. Users still using the free version of Wordfence will receive the same protection on February 7, 2024.
If you know someone who uses this plugin on their site, we recommend sharing this advisory with them to ensure their site remains secure, as this vulnerability poses a significant risk.
Remember we’re running a Bug Bounty Extravaganza again. Earn over 6x our usual bounty rates, up to $10,000, for all vulnerabilities submitted through February 29th, 2024!
The post High Severity Arbitrary File Upload Vulnerability Patched in File Manager Pro WordPress Plugin appeared first on Wordfence.
Article Link: High Severity Arbitrary File Upload Vulnerability Patched in File Manager Pro WordPress Plugin