GitLab Issues Critical Patches for CE/EE Alongside Fortra & MOVEit (CVE-2024-5655, CVE-2024-5276, CVE-2024-5805, CVE-2024-5806)
GitLab has rolled out new security updates for both its Community Edition (CE) and Enterprise Edition (EE), addressing one critical and three high-severity issues among over a dozen vulnerabilities.
With GitLab being one of the most popular platforms in DevOps, it’s essential to upgrade all installations and review the resolved vulnerabilities.
In addition to GitLab, Fortra and MOVEit, two widely used Managed File Transfer (MFT) solutions, have recently released critical patches that users should apply immediately.
GitLab CE/EE Vulnerabilities: Details and Affected Versions
GitLab’s latest security updates address a total of 14 CVEs. Here are the most severe vulnerabilities:
CVE-2024-5655 (CVSS: 9.6) – Run pipelines as any user
This vulnerability allows an attacker to trigger a pipeline as another user under certain conditions.
Affected Versions (GitLab CE/EE):
- From 15.8 to 16.11.4
- From 17.0 to 17.0.2
- From 17.1 to 17.1.0
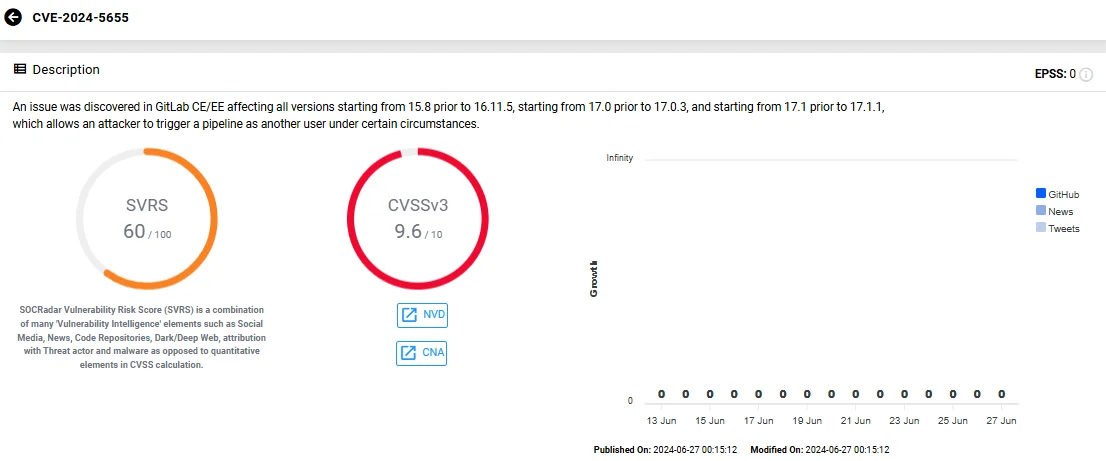
Vulnerability card of CVE-2024-5655 (SOCRadar Vulnerability Intelligence)
The fix specific for this critical vulnerability modifies the Merge Request (MR) re-targeting workflow to prevent automatic pipeline runs when a merge request is automatically re-targeted due to its previous target branch being merged.
CVE-2024-4901 (CVSS: 8.7) – Stored XSS injected in imported project’s commit notes
This stored Cross-site Scripting (XSS) vulnerability can be imported via malicious commit notes, potentially allowing attackers to execute arbitrary scripts in the context of the user’s session.
Affected Versions (GitLab CE/EE):
- From 16.9 to 16.11.4
- From 17.0 to 17.0.2
- From 17.1 to 17.1.0
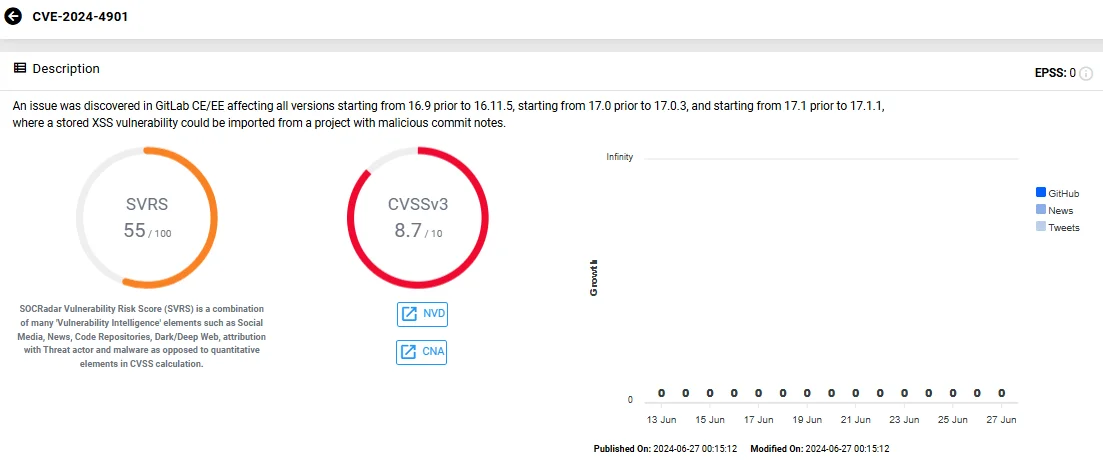
Vulnerability card of CVE-2024-4901 (SOCRadar Vulnerability Intelligence)
CVE-2024-4994 (CVSS: 8.1) – CSRF on GraphQL API IntrospectionQuery
This Cross-Site Request Forgery (CSRF) vulnerability in GitLab’s GraphQL API can lead to unauthorized actions within the GitLab instance by allowing the execution of arbitrary GraphQL mutations.
Affected Versions (CE/EE):.
- From 16.1.0 to 16.11.4
- From 17.0 to 17.0.2
- From 17.1.0 to 17.1.0
CVE-2024-6323 (CVSS: 7.5) – Remove search results from public projects with unauthorized repos
It involves improper authorization in GitLab EE’s global search, allowing an attacker to leak content from a private repository in a public project.
Affected Versions (GitLab EE):
- From 16.11 to 16.11.4
- From 17.0 to 17.0.2
- From 17.1 to 17.1.0
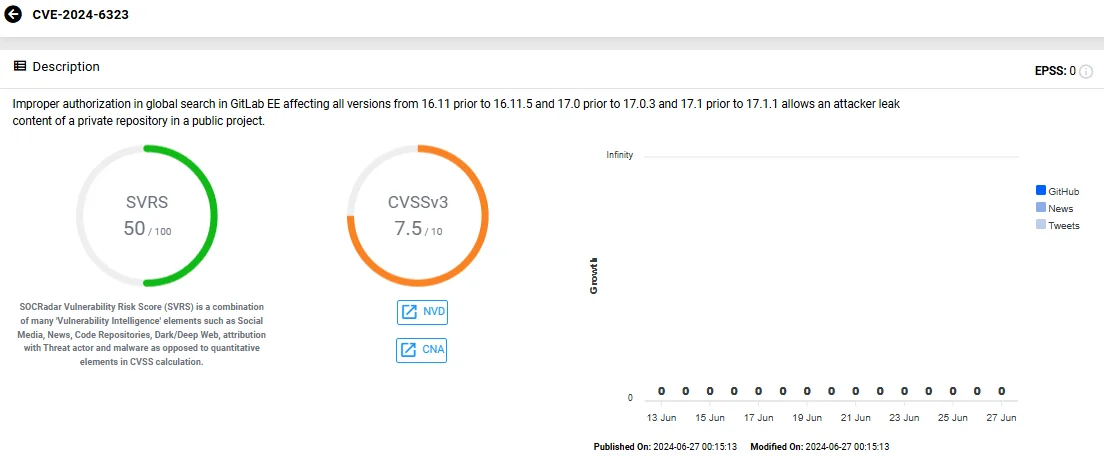
Vulnerability card of CVE-2024-6323 (SOCRadar Vulnerability Intelligence)
SOCRadar’s user-friendly Vulnerability Intelligence dashboard provides a comprehensive view of global vulnerability trends, enabling you to identify which vulnerabilities threat actors are exploiting and prioritize patching more effectively.
Follow emerging CVEs and exploitation trends via SOCRadar’s Vulnerability Intelligence
Other GitLab Vulnerabilities
Besides the severe vulnerabilities already discussed, GitLab’s recent updates also tackle various medium and low-severity issues that could lead to information leaks, Denial-of-Service (DoS) attacks, and unauthorized access.
GitLab released the security updates on June 26, 2024, urging all users of GitLab CE and EE to upgrade immediately to maintain the security of their installations.
Are there any exploitation attempts?
Although GitLab has not detected any exploitation of these vulnerabilities in the wild, the severity of these flaws demands prompt action.
Which GitLab versions include fixes?
To protect against these vulnerabilities, GitLab strongly recommends upgrading all installations to one of the following versions immediately:
- 17.1.1
- 17.0.3
- 16.11.5
For more details, refer to GitLab’s official patch release article.
Fortra FileCatalyst Workflow Receives Fix for a Critical SQL Injection (CVE-2024-5276), PoC Available
Fortra recently patched a critical vulnerability in FileCatalyst Workflow, identified as CVE-2024-5276 with a CVSS score of 9.8. If exploited, this vulnerability could allow an attacker to tamper with the application database.
FileCatalyst Workflow is a widely used file transfer acceleration solution that offers a web portal to streamline large file exchanges, enhancing business productivity.
What is CVE-2024-5276?
CVE-2024-5276 is an SQL injection vulnerability in Fortra FileCatalyst Workflow that allows an attacker to modify application data. According to Fortra, likely impacts include creating administrative users and deleting or altering data in the application database.
Fortra additionally notes that successful unauthenticated exploitation requires a Workflow system with anonymous access enabled, though it can also be exploited by an authenticated user.
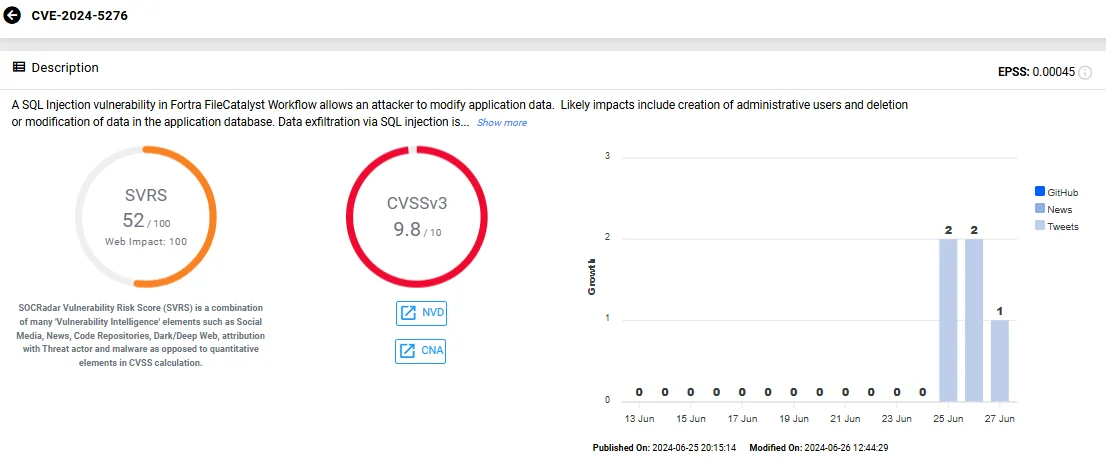
Vulnerability card of CVE-2024-5276 (SOCRadar Vulnerability Intelligence)
CVE-2024-5276 affects Fortra FileCatalyst Workflow versions 5.1.6 Build 135 and earlier.
Details of the PoC Exploit for CVE-2024-5276
Previously, we discussed a critical RCE vulnerability in FileCatalyst (CVE-2024-25153) that rapidly gained attention, with researchers quickly devising a Proof-of-Concept (PoC) exploit. Similarly, CVE-2024-5276 also has a PoC exploit available soon after its disclosure.
The exploit leverages the vulnerability in the workflow web application to perform anonymous logins and execute SQL injection (SQLi) attacks, adding a new administrator user, “operator,” with a specified password. Remote attackers can use a user-supplied jobID in various URL endpoints to form the WHERE clause in an SQL query to perform SQLi.
How to fix CVE-2024-5276?
The vulnerability has been addressed in version 5.1.6 build 139. For more information and to access updates, visit Fortra’s advisory.
For users unable to apply the patches immediately, disabling the vulnerable servlets in the “web.xml” file located in the Apache Tomcat installation directory can serve as a temporary workaround. These are:
- csv_servlet
- pdf_servlet
- xml_servlet
- json_servlet
A guide to disabling these servlets is available here.
New MOVEit Transfer & Gateway Vulnerabilities, CVE-2024-5805 and CVE-2024-5806: Exploitation Attempts Surge
Progress Software has addressed two significant vulnerabilities in their MOVEit managed file transfer (MFT) software: CVE-2024-5805 and CVE-2024-5806. These vulnerabilities pose severe security risks, particularly in MOVEit Transfer and MOVEit Gateway.
The MOVEit catastrophe caused by the Cl0p ransomware last year highlights the critical role MOVEit plays in many organizations and underscores that these vulnerabilities must not be underestimated.
Progress Software even privately instructed users to apply hotfixes before publicly disclosing the new vulnerabilities, emphasizing their seriousness.
What Is CVE-2024-5805 and How Was It Discovered?
CVE-2024-5805 (CVSS: 9.1) is a critical improper authentication vulnerability found in MOVEit Gateway, which acts as a proxy to allow MOVEit Transfer to receive inbound connections behind a firewall.
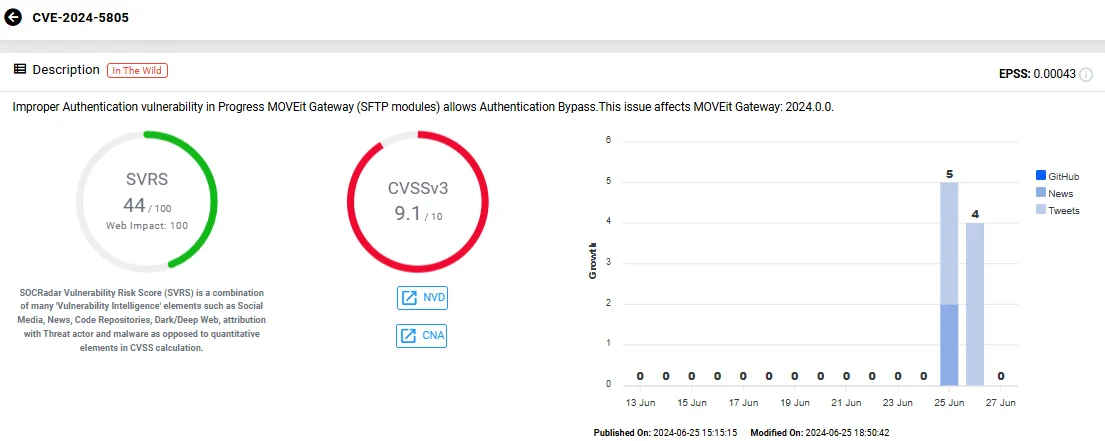
Vulnerability card of CVE-2024-5805 (SOCRadar Vulnerability Intelligence)
Discovered by security researcher Max Hase, this flaw affects the Secure File Transfer Protocol (SFTP) module in MOVEit Gateway version 2024.0.0. Attackers can exploit this vulnerability to bypass authentication, compromising the security of the system.
What Does CVE-2024-5806 Entail?
CVE-2024-5806 (CVSS: 9.1) is another authentication bypass vulnerability, also posing critical severity.
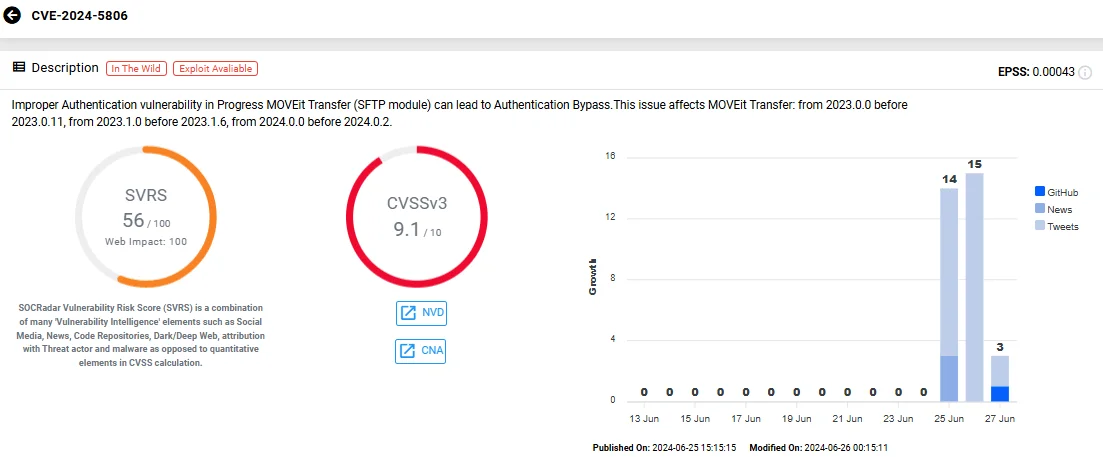
Vulnerability card of CVE-2024-5806 (SOCRadar Vulnerability Intelligence)
This vulnerability affects MOVEit Transfer versions from 2023.0.0 before 2023.0.11, from 2023.1.0 before 2023.1.6, and from 2024.0.0 before 2024.0.2.
The vulnerability lies in the SFTP module and can lead to authentication bypass in specific scenarios. Unlike CVE-2024-5805, CVE-2024-5806 also impacts MOVEit Cloud environments.
Exploitation Attempts Targeting MOVEit’s CVE-2024-5806
Exploitation attempts for CVE-2024-5806 began shortly after the details were disclosed. Details and a Proof-of-Concept (PoC) exploit for the CVE-2024-5806 vulnerability are already available; moreover, Shadowserver reports related exploitation attempts on their honeypots.
The vulnerability can be weaponized to impersonate any user on the server, as explained by WatchTowr Labs researchers Aliz Hammond and Sina Kheirkhah. They also identified that the vulnerability arises from the interplay between MOVEit and the IPWorks SSH library.
Researchers noted that attackers must know an existing username, the target account must authenticate remotely, and the SFTP service must be publicly accessible to exploit CVE-2024-5806. This requirement, while minimal, helps limit the scope of automated attacks.
For a demonstration as to how CVE-2024-5806 works, see the PoC exploit on GitHub.
The Attack Surface
Researchers state observing around 2,700 MOVEit Transfer instances online, primarily in the U.S., Europe, and other regions. You can also view exposed MOVEit Transfer instances on Shadowserver:
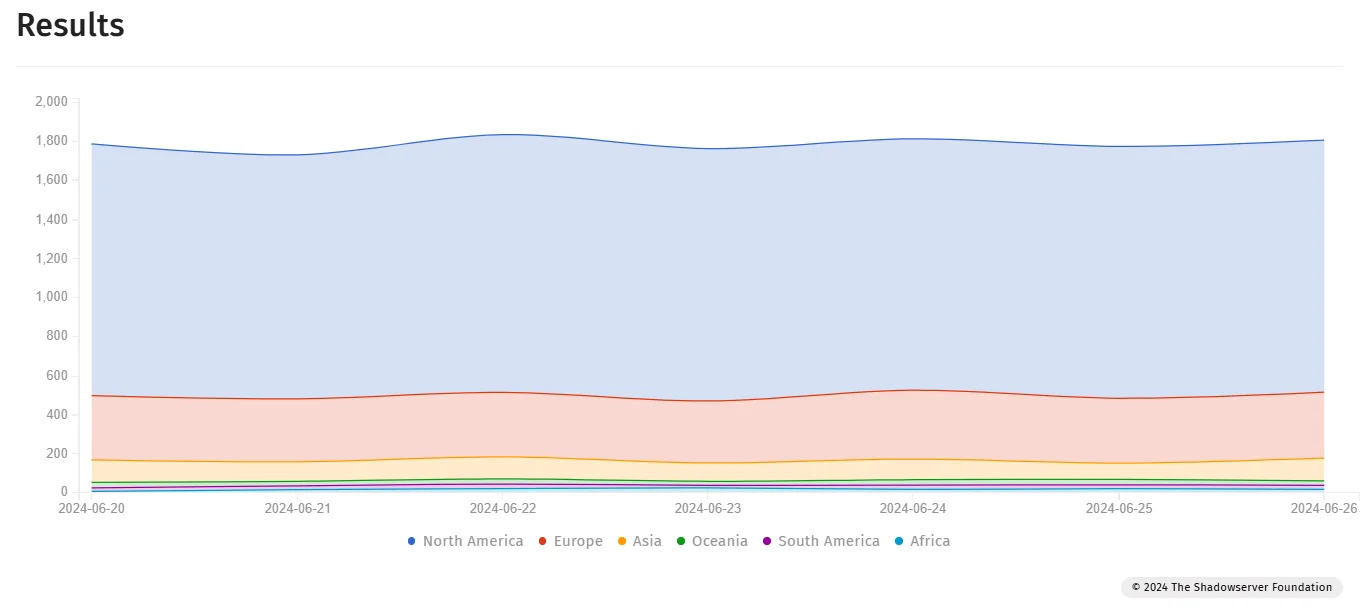
Exposed MOVEit Transfer instances over the last 7 days (Shadowserver)
How Can You Address These Vulnerabilities?
While CVE-2024-5805 does not affect MOVEit Cloud, as it does not use MOVEit Gateway, CVE-2024-5806 does impact MOVEit Cloud users. Progress Software has patched this issue for both cloud and on-premises installations, and urges users to upgrade to the latest versions:
For CVE-2024-5805, users must update to MOVEit Gateway version:
- 2024.0.1
For CVE-2024-5806, users should upgrade to MOVEit Transfer versions:
- 2023.0.11
- 2023.1.6
- 2024.0.2
The company highlighted that using the full installer is essential to ensure proper remediation and warned that the upgrade process would cause system outages.
The company also advised customers to block public inbound Remote Desktop Protocol (RDP) access to MOVEit Transfer servers and limit outbound access to known trusted endpoints to mitigate risks further.
All in all, to prevent exploitation of your MOVEit products:
- Apply the latest patches for MOVEit Gateway and MOVEit Transfer.
- Block public inbound RDP access to MOVEit Transfer servers.
- Limit outbound access to known trusted endpoints from MOVEit Transfer servers.
- Regularly monitor and update systems to address any new vulnerabilities promptly.
Enhance Vulnerability Management with SOCRadar
Stay ahead of emerging vulnerabilities and cybersecurity trends with SOCRadar’s Attack Surface Management (ASM) module.
ASM continuously monitors your digital assets, providing timely threat alerts and actionable insights. This proactive approach helps you strengthen your cybersecurity defenses and respond swiftly to potential threats, before exploitation can occur.
Monitor Company Vulnerabilities via SOCRadar’s Attack Surface Management
Article Link: https://socradar.io/gitlab-issues-critical-patches-for-ce-ee-alongside-fortra-moveit/

