The Microsoft Security blog highlights the active exploitation of CVE-2025-24983, a zero-day vulnerability in the Windows Common Log File System (CLFS) that allows local privilege escalation to SYSTEM-level access. The threat actor group Storm-2460 is exploiting this flaw in ransomware campaigns, using tools such as the PipeMagic loader to execute their attacks. The blog offers critical insights into identifying both pre-exploitation and post-exploitation artifacts, enabling defenders to detect malicious activity across different stages of the attack lifecycle and enhance threat-hunting efforts.
Introduction to Malware Binary Triage (IMBT) Course
Looking to level up your skills? Get 10% off using coupon code: MWNEWS10 for any flavor.
Enroll Now and Save 10%: Coupon Code MWNEWS10
Note: Affiliate link – your enrollment helps support this platform at no extra cost to you.

Go To Section
Tags
Background
Microsoft’s Threat Intelligence Center (MSTIC) and Security Response Center (MSRC) have identified active post-compromise exploitation of a zero-day vulnerability that allows local privilege escalation in the Windows Common Log File System (CLFS). Microsoft released a security patch for this vulnerability on April 8 as part of its Tuesday update cycle. As noted in the Microsoft blog, the vulnerability tracked as CVE-2025-29824 has been used in highly targeted attacks affecting a number of organizations across various sectors and regions. The identified targets include:
-
Spanish software company
-
Organizations in the Information Technology (IT) and Real Estate sectors in the United States
-
Financial Sector in Venezuela
-
The Retail Sector in Saudi Arabia
| CVE | CVSSv3 Score |
|---|---|
| CVE-2025-29824 |
7.8 |
Severity: High
Vector: CVSS:3.1/AV:L/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H/E:F/RL:O/RC:C
Current situation: Exploited in the wild, POC not available as of publication.
Affected Versions
Check out Microsoft Security Guide or CVE for updated information.
| Product Name | Version | Build/Edition | Platform |
|---|---|---|---|
| Windows 10 | 1507 | up to 10.0.10240.20946 | x64 |
| Windows 10 | 1607 | up to 10.0.14393.7875 | x64 |
| Windows Server 2008 | SP2 | - | x64 |
| Windows Server 2008 | SP2 | - | x64 |
| Windows Server 2008 R2 | SP1 | - | x64 |
| Windows Server 2012 | - | All editions | x64 |
| Windows Server 2012 R2 | - | All editions | x64 |
| Windows Server 2016 | - | up to 10.0.14393.7875 | x64 |
Overview
As per Microsoft’s blog, the exploit has been weaponized using the PipeMagic malware, with attribution to the threat actor group Storm-2460. According to Microsoft, their modus operandi typically involves leveraging initial access—often obtained via commodity malware—and elevating privileges to facilitate lateral movement and large-scale ransomware deployment.
In multiple incidents observed by Microsoft, the threat actor leveraged certutil, a native Windows utility, to download malware-laden files. Notably, these downloads originated from legitimate third-party websites that had been compromised and repurposed to host malicious content. This abuse of trusted infrastructure helped evade detection and added credibility to the attacker’s delivery method.
The downloaded files were malicious MSBuild project files. These files carried encrypted payloads, which were decrypted and executed using a technique involving the EnumCalendarInfoA API callback—a stealthy method that aids in bypassing traditional defenses.
Once decrypted, the payload was identified as PipeMagic. Upon execution, PipeMagic triggered the exploitation of CVE-2025-29824, allowing the adversaries to escalate privileges on the compromised system. With elevated access, they proceeded to dump LSASS and began preparing the environment for a ransomware attack by:
- Deleting backups using tools like wbadmin
- Modifying Boot Configuration Data (BCD) to disable recovery options
- Clearing event logs using wevtutil to cover their tracks
Detecting CVE-2025-29824 with Logpoint
Adversaries can use any vector for initial access, and they must first gain access to the system to exploit this vulnerability. The hunting queries and alerts below are designed to detect pre-exploitation and post-exploitation activities, focusing on the TTPs documented by Microsoft Security Response Center (MSRC).
Required Log Sources
- Windows
- Process Creation with Command Line Auditing explicitly enabled
- Windows Sysmon
-
- Relevant rules must be configured to log Pipe Creation and file download.
- Firewall
- IDS/IPS
Pre-Exploitation Activities
As highlighted in Microsoft's blog, the pre-exploitation activity begins with the use of certutil.exe, a built-in Windows utility, to download the malicious payload. To identify such behavior, analysts can monitor for file download events involving certutil.exe.
Suspicious Usage of Certutil
There are several ways to detect this activity. One effective method is to look for suspicious command-line usage. For this, analysts can leverage the alert Suspicious Certutil Command Detected, which is designed to detect common parameters used by attackers to download files using certutil.

Note: Known use case of certutil.exe to download file is using /urlcache parameter, so above alert is provided assuming adversaries have used the parameter to download, so if any other unknown technique or bypassed is used, then it may not detect those actions.
Another effective approach is to look for file download events directly. The hunting query below can help detect such activity by identifying instances where certutil.exe is used to download files.
Suspicious Usage of MsBuild
The file downloaded via certutil.exe is a malicious MSBuild project file that contains an encrypted malware payload. This payload is decrypted and executed using the EnumCalendarInfoA API callback, an evasion technique to bypass traditional detection.
The image below, sourced from Cisco Talos, illustrates the initial command-line execution flow of this process.
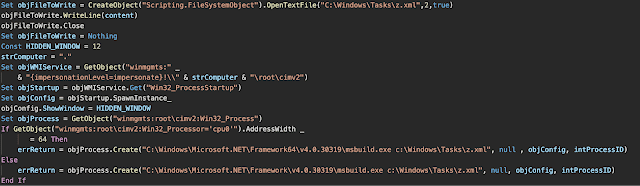
Malicious file Execution via MsBuild Source - Cisco Talos
Detecting malicious activity solely based on the execution of msbuild.exe can be challenging, as it is a legitimate tool used in many environments. However, for hunting purposes, monitoring process creation events involving msbuild.exe can be valuable. Analysts should then investigate the returned results further by analyzing suspicious or unusual command-line arguments associated with its execution.
Msbuild Spawned by Unusual Parent Process
Additionally, as noted in the Cisco Talos blog, msbuild.exe is spawned by an anomalous parent process—specifically, winword.exe. This unusual behavior can be leveraged as a detection opportunity. An alert based on msbuild.exe being launched by suspicious or non-standard parent processes can help identify potential exploitation attempts.
Suspicious Child Process Spawned by Microsoft Office Product
Alternatively, this alert can be used to detect the specific behavior showcased in the Cisco Talos blog, where msbuild.exe is spawned by an unusual parent process like winword.exe.
Remote Connection via MSbuild
Furthermore, after the execution of msbuild.exe, as mentioned in the Talos Blog, a network connection is established to download and execute the payload. Therefore, it’s important to search for network connection events initiated by msbuild.exe, which can be done using the hunting query provided below.
PipeMagic Execution
According to Kaspersky, PipeMagic generates a 16-byte random array to create a named pipe in the format \\.\pipe\1.<hex string> so we can use the below hunting query to detect the creation of such Named Pipe.
Note: This may generate false positives (FPs), so it's recommended to use regex filtering to narrow down results based on relevant or suspicious pipe name patterns.
Post-Exploitation Activities
The execution of PipeMagic is responsible for preparing and launching the payload that ultimately exploits the vulnerability CVE-2025-29824.
Suspicious file Creation
In the Microsoft report, after the successful exploitation of the vulnerability, a .blf file is created under the C:\ProgramData\SkyPDF folder. This file serves as a trace of post-exploitation activity. You can use the following query to hunt for such artifacts.
Alternatively, you can hunt for the creation of .blf (Binary Log Files), which is generally uncommon and may indicate suspicious activity. While it's best to focus on specific folders like C:\ProgramData\SkyPDF, analysts should also consider inspecting .blf creation across the system, especially in unusual or non-standard directories, as this may vary depending on the environment.
LSASS Dump
Following the exploitation, the adversaries were observed dumping LSASS using procdump.exe. The hunting query below can be used to detect such activity.
Alternatively, you can rely on the alert Usage of Procdump Detected to identify potential LSASS dumping attempts.
A Few More Artifacts
To further enhance detection coverage, the following hunting queries and alerts can be used to identify indicators of compromise (IOCs) related to ransomware activity. These alerts are designed to detect key behaviors and artifacts observed during the attack.
Possible Modification of Boot Configuration
Ransomware often targets Boot Configuration Data (BCD) to disable system recovery options, making recovery more difficult. To achieve this, attackers abuse the Windows native toolbcdedit.exe. Such behavior can be detected using this alert.
Shadow Copy Deletion Using OS Utilities Detected
Since most ransomware strains attempt to delete backup data, they commonly use commands like wbadmin to remove shadow copies and other restore points. This alert can help detect such activity, including the use of wbadmin and other native Windows tools that are often abused for backup deletion.
Suspicious Eventlog Clear or Configuration Using Wevtutil Detected
Microsoft observed the threat actor Storm-2460 uses wevtutil to clear the Application event log, likely as an attempt to cover their tracks. This alert can be used to detect suspicious usage of wevtutil, which is often a strong indicator of post-exploitation or anti-forensic activity.
PipeMagic C2 Communication
The PipeMagic malware was observed connecting to the command-and-control (C2) domain aaaaabbbbbbb.eastus.cloudapp.azure[.]com. To detect such activity, analysts should review firewall logs, IDS/IPS alerts, and network connection logs for any evidence of outbound connections to this domain.
Final Words: Apply patch without delay
Microsoft has already released security updates addressing this vulnerability, and we strongly recommend that organizations apply these updates as soon as possible. While it may be challenging to patch all systems immediately, it's crucial to prioritize critical and sensitive systems first to reduce the risk of exploitation.
For more guidance on staying protected and detecting similar threats, be sure to check out our other blogs focused on detection, prevention, and response strategies.
The blog will be updated as new updates regarding vulnerability are publicly updated.
The post From Exploit to Ransomware: Detecting CVE-2025-29824 appeared first on Logpoint.
Article Link: From Exploit to Ransomware: Detecting CVE-2025-29824
