On December 12, 2023, FortiGuard announced the release of security updates to address several critical vulnerabilities in its FortiOS, FortiPAM, FortiMail, FortiNDR, FortiRecorder, FortiSwitch, and FortiVoice products. These vulnerabilities, if exploited, could allow cyber threat actors to gain control of affected systems.
Double Free Vulnerability in FortiOS and FortiPAM HTTPSd Daemon
A double free vulnerability [CWE-415] was identified in FortiOS and FortiPAM HTTPSd daemon. This vulnerability, tracked as CVE-2023-41678 with a CVSSv3 score of 8.3, could allow an authenticated attacker to execute arbitrary code through specially crafted commands.
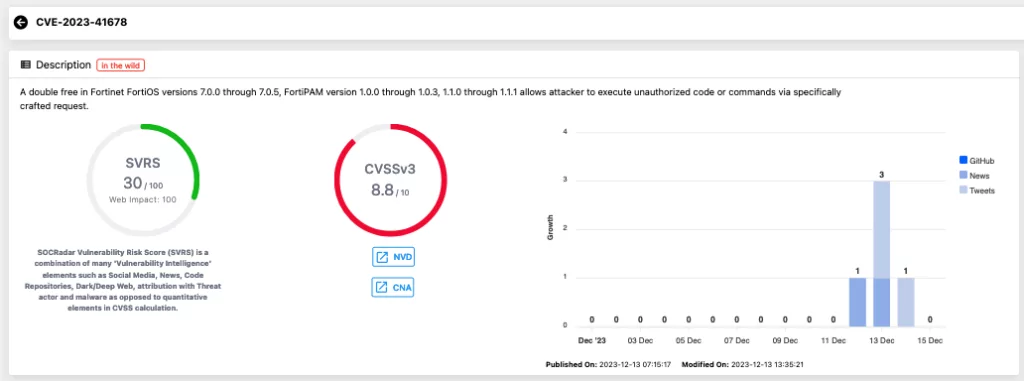 Vulnerability card of CVE-2023-41678, SOCRadar Vulnerability Intelligence Module
Vulnerability card of CVE-2023-41678, SOCRadar Vulnerability Intelligence Module
In the recent announcement, this particular vulnerability has been highlighted as the most critical among others. Although there is currently no public exploit available, the assigned CVSS vector string for this vulnerability, CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H, suggests that an attacker could exploit this issue over a network with low-level system privileges. The impact of this vulnerability is significant, as it poses a serious threat to the confidentiality, availability, and integrity of the targeted system.
Affected Versions and Solution
FortiOS 7.0: Versions 7.0.0 to 7.0.5 are affected. The solution is to upgrade to version 7.0.6 or above.
FortiPAM 1.1: Versions 1.1.0 to 1.1.1 are affected. The solution is to upgrade to version 1.1.2 or above.
FortiOS 7.2, 6.4, and FortiPAM 1.2 and 1.0 are not affected.
Cross-Site Request Forgery (CSRF) in HTTPd CLI Console
A CSRF vulnerability [CWE-352] was found in the CLI of FortiMail, FortiNDR, FortiRecorder, FortiSwitch, and FortiVoiceEnterprise. This high-severity issue, with a CVSSv3 score of 7.5, could enable a remote, unauthenticated attacker to execute commands on the CLI by deceiving an authenticated administrator into executing malicious GET requests.
Affected Versions and Solution
FortiMail: Versions 7.0.0 to 7.0.3 and 6.4.0 to 6.4.6 are impacted. Upgrading to versions 7.0.4 and 6.4.7 or above, respectively, is required.
FortiNDR: Versions 7.1.0 to 7.0.4, and all versions of 1.5 to 1.1 are affected. Upgrading to the fixed releases is necessary.
FortiRecorder, FortiSwitch, and FortiVoice also have specific affected versions with recommended upgrades.
Format String Bug in FortiOS and FortiProxy HTTPSd
A format string vulnerability [CWE-134] in the HTTPSd daemon of FortiOS and FortiProxy may allow an authenticated user to execute unauthorized code or commands through specially crafted API requests. This vulnerability is tracked as CVE-2023-36639, with a high severity score of 7.
Affected Versions and Solution
FortiOS: Versions 7.4.0, 7.2.0 to 7.2.4, 7.0.0 to 7.0.11, 6.4.0 to 6.4.12, and 6.2.0 to 6.2.15 are impacted. Upgrading to the respective fixed versions is advised.
FortiProxy: Versions 7.2.0 to 7.2.4 and 7.0.0 to 7.0.10 are affected. Upgrades to versions 7.2.5 and 7.0.11 or above, respectively, are recommended.
Users of the affected FortiGuard products are advised to review the specific version information and apply the provided security updates immediately. Verify if your systems are running any of the affected versions and follow the recommended upgrade paths.
Streamlined Vulnerability Management with SOCRadar’s Comprehensive Modules
SOCRadar’s Attack Surface Management, Supply Chain Intelligence, and Vulnerability Management modules offer an integrated approach to tackling complex vulnerabilities like those recently identified in FortiGuard products.
The Attack Surface Management module is crucial for identifying and monitoring external-facing assets, including those running vulnerable versions of software. It continuously scans the organization’s digital footprint, pinpointing at-risk assets and facilitating swift action.
Concurrently, the Supply Chain Intelligence module enhances this protection by evaluating the security posture of third-party vendors. It alerts organizations to vulnerabilities disclosed by suppliers, such as FortiGuard, ensuring that any potential risks are promptly managed. This module provides critical insights into how these vulnerabilities might impact an organization through its supply chain, elevating the importance of comprehensive vendor risk management.
In conjunction, SOCRadar’s Vulnerability Management module plays a key role in the identification and prioritization of vulnerabilities. It not only scans for known vulnerabilities within an organization’s infrastructure but also offers context-based prioritization, considering factors such as exploitability, impact, and the criticality of affected assets. This approach is especially effective in managing widespread vulnerabilities, ensuring that remediation efforts are targeted and efficient.
The post FortiGuard Releases Security Updates for Critical Vulnerabilities in Multiple Products Introduction to the Vulnerabilities appeared first on SOCRadar® Cyber Intelligence Inc..
Article Link: FortiGuard Releases Security Updates for Critical Vulnerabilities in Multiple Products Introduction to the Vulnerabilities
