Forensic Artifacts — Parsing Symantec EDR “localdatastore” LevelDB Files
Last week I wrote a blog post about an interesting forensic artifact related to the Symantec EDR (localdatastore) that can be found inside the Symantec SEP “program data” folder. If you haven’t read it, i suggest you do before continuing as this is a direct continuation.
Forensics Artifacts — Symantec EDR “localdatastore” Folder
Last time i focused on the “.log” file that was being generated by the Symantec EDR while it was writing the collected events to the “.ldb” files. While this file can contains a ton of information about events happening on the system. One of the drawbacks of the method i described is that it requires live interaction with the a system, meaning that to collect as much information as possible one must execute the watcher script on a running machine (Also old data cannot be found inside the “.log” files).
So to get all the information collected / stored by Symantec EDR we must take a look and analyze the “.ldb” files stored inside the “localdatastore” folder.
Without further ado let us get started.
Symantec EDR “.ldb” Files
Symantec EDR stores the information collected from an endpoint in “.ldb” files inside the “localdatastore” folder. These files are actually “LevelDB” files. Here is a small definition from their official GitHub.
LevelDB is a fast key-value storage library written at Google that provides an ordered mapping from string keys to string values. — GitHub
So to extract the contents of these files we need to be able to parse LevelDB files. Fortunately a parser exists thanks to @_RyanBenson work.
Parsing Symantec EDR “.ldb” files
So to extract all the data collected by SEDR here is how to proceed.
- First clone the “ccl_chrome_indexeddb” repository (Link Below)
obsidianforensics/ccl_chrome_indexeddb
- Next, copy the SEDR “localdatastore” folder to a separate location.
- Execute the “dump_leveldb.py” script on a folder containing “.ldb” files (found inside the localdatastore folder).
#!/usr/bin/python3.8
python3 dump_leveldb.py /path/to/ldb/folder
- This will generate a CSV file containing “all” the information that was stored inside the “.ldb” files. (See screenshot)
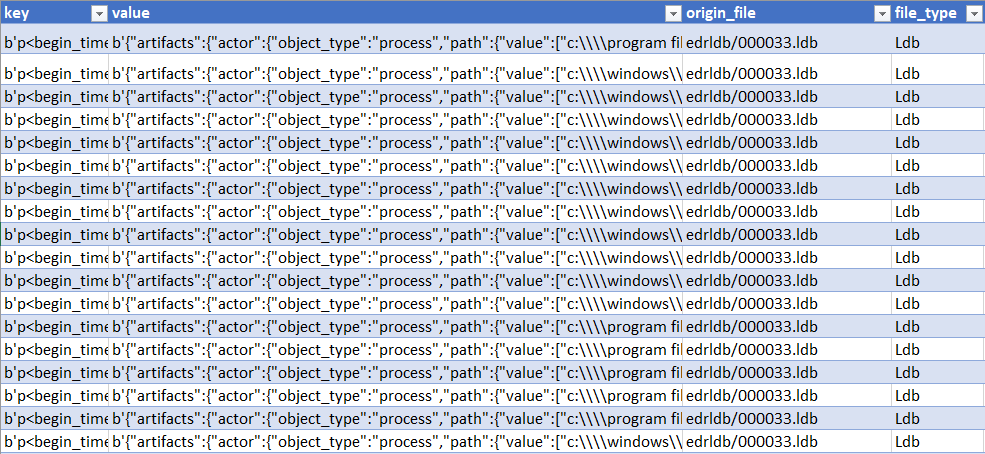 Parsed / Reconstructed Level DB database
Parsed / Reconstructed Level DB databaseOne might consider this as enough and call it a day but the information is not easily searchable in its current state. To solve this i went ahead and created a small parser that’ll beautify and organize all the information inside this CSV. You can download it from my GitHub [Link Below].
nasbench/sedr-localdatastore-parser
The script is straight forward. Just feed it the CSV generated before and it’ll spit out a formatted version of everything. Here is an example of the expected results.
python sedr_localdatastore_parser.py /path/to/generated/csv/file
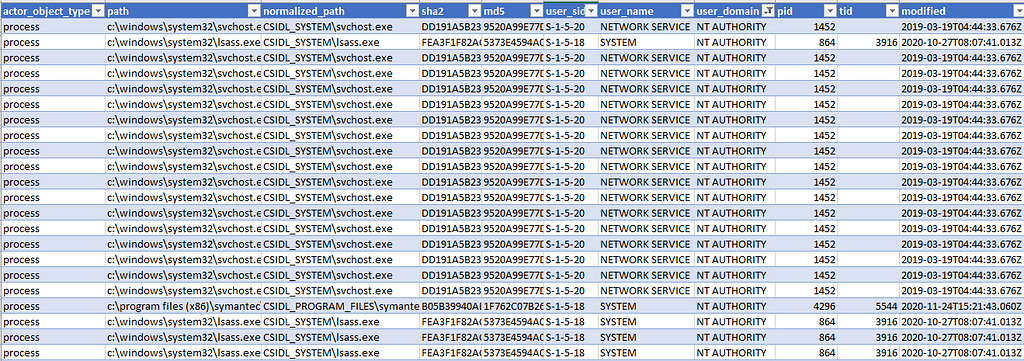 Parsed SEDR Data
Parsed SEDR DataConclusion
That’s it for this blog post. I hope you enjoyed reading this as i did researching it. If you have any suggestions or questions hit me up on twitter @nas_bench
Happy Hunting.
Article Link: Forensic Artifacts — Parsing Symantec EDR “localdatastore” LevelDB Files | by Nasreddine Bencherchali | Medium