A recent update by CrowdStrike on July 18, 2024, resulted in a worldwide outage, causing significant disruption for users who were left with blue screens of death (BSODs) on their devices. Cybercriminals seized the opportunity to target affected users with phishing scams and malware disguised as updates or hotfixes.
The ANY.RUN team has been closely monitoring the situation after the outage and has identified two primary sources of threats — domains and malware disguised as updates or bug fixes.
Fake CrowdStrike Domains
One of the earliest consequences of the outage was the creation of websites with domain names that mimicked CrowdStrike’s official domain. Although some of them were created with no malicious intent, others were used as part of phishing attempts.
These websites included newly registered ones and those that were still under construction.
Some examples:
- Crowdstriketoken[.]com: https://app.any.run/tasks/f58a7af0-e5ad-4d1c-8c18-f2093cddc28c/
- Crowdstrikebluescreen[.]com: https://app.any.run/tasks/789aa98b-fe9d-4758-a023-72a0b67530f8/
- crowdstrikedown[.]site: https://app.any.run/tasks/577a9a3c-148d-419f-9eb2-89adbbabeef4/
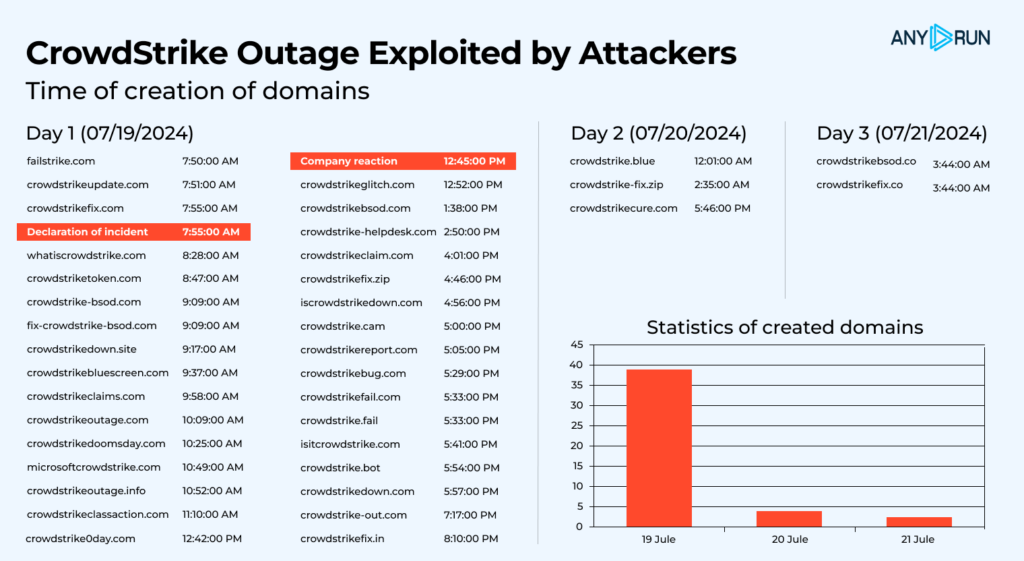 Fake domains identified within three days following the outage
Fake domains identified within three days following the outage Looking at the data, the first day after the outage saw the highest volume of fake domains. Threat actors were quick to respond, potentially tricking numerous users into visiting fake websites while they were trying to fix the problem on their own.
Here is a list of domains collected by ANY.RUN so far:
<tbody> <tr>
<td>
crowdstrike-bsod[.]co </td>
<td>
crowdstrike-bsod[.]com </td>
<td>
crowdstrike-fix[.]zip </td>
<td>
crowdstrike-helpdesk[.]com </td>
<td>
crowdstrike-out[.]com </td>
</tr>
<tr>
<td>
crowdstrike[.]blue </td>
<td>
crowdstrike[.]bot </td>
<td>
crowdstrike[.]cam </td>
<td>
crowdstrike[.]ee </td>
<td>
crowdstrike[.]es </td>
</tr>
<tr>
<td>
crowdstrike[.]fail </td>
<td>
crowdstrike0day[.]com </td>
<td>
crowdstrikebluescreen[.]com </td>
<td>
crowdstrikebsod[.]co </td>
<td>
crowdstrikebsod[.]com </td>
</tr>
<tr>
<td>
crowdstrikebug[.]com </td>
<td>
crowdstrikeclaim[.]com </td>
<td>
crowdstrikeclaims[.]com </td>
<td>
crowdstrikeclassaction[.]com </td>
<td>
crowdstrikecure[.]com </td>
</tr>
<tr>
<td>
crowdstrikedoomsday[.]com </td>
<td>
crowdstrikedown[.]com </td>
<td>
crowdstrikedown[.]site </td>
<td>
crowdstrikefail[.]com </td>
<td>
crowdstrikefix[.]co </td>
</tr>
<tr>
<td>
crowdstrikefix[.]com </td>
<td>
crowdstrikefix[.]in </td>
<td>
crowdstrikefix[.]zip </td>
<td>
crowdstrikeglitch[.]com </td>
<td>
crowdstrikehelp[.]com </td>
</tr>
<tr>
<td>
crowdstrikelawsuit[.]com </td>
<td>
crowdstrikemedaddy[.]com </td>
<td>
crowdstrikeold[.]com </td>
<td>
crowdstrikeoops[.]com </td>
<td>
crowdstrikeoopsie[.]com </td>
</tr>
<tr>
<td>
crowdstrikeoopsies[.]com </td>
<td>
crowdstrikeout[.]com </td>
<td>
crowdstrikeoutage[.]com </td>
<td>
crowdstrikeoutage[.]info </td>
<td>
crowdstrikepatch[.]com </td>
</tr>
<tr>
<td>
crowdstrikeplatform[.]com </td>
<td>
crowdstrikeplatform[.]info </td>
<td>
crowdstrikerecovery[.]com </td>
<td>
crowdstrikereport[.]com </td>
<td>
crowdstrikesettlement[.]com </td>
</tr>
<tr>
<td>
crowdstrikesuporte[.]com </td>
<td>
crowdstrikesupport[.]info </td>
<td>
crowdstriketoken[.]com </td>
<td>
crowdstrikeupdate[.]com </td>
<td>
crowdstrikeyou[.]xyz </td>
</tr>
<tr>
<td>
crowdstrikezeroday[.]com </td>
<td>
fix-crowdstrike-apocalypse[.]com </td>
<td>
fix-crowdstrike-bsod[.]com </td>
<td>
fix-crowdstrike[.]com </td>
<td>
fixcrowdstrike[.]com </td>
</tr>
<tr>
<td>
fixmycrowdstrike[.]com </td>
<td>
fuckcrowdstrike[.]com </td>
<td>
howtofixcrowdstrikeissue[.]com </td>
<td>
iscrowdstrikedown[.]com </td>
<td>
iscrowdstrikefixed[.]com </td>
</tr>
<tr>
<td>
iscrowdstrikestilldown[.]com </td>
<td>
isitcrowdstrike[.]com </td>
<td>
microsoftcrowdstrike[.]com </td>
<td>
microsoftoutagescrowdstrike[.]com </td>
<td>
secure-crowdstrike[.]com </td>
</tr>
<tr>
<td>
suportecrowdstrike[.]com </td>
<td>
whatiscrowdstrike[.]com </td>
<td>
</td>
<td>
</td>
<td>
</td>
</tr>
</tbody></table>
To stay informed about the latest suspicious domains, use TI Lookup. Our service lets you search our continuously updated threat database using 40 parameters, including domain names.
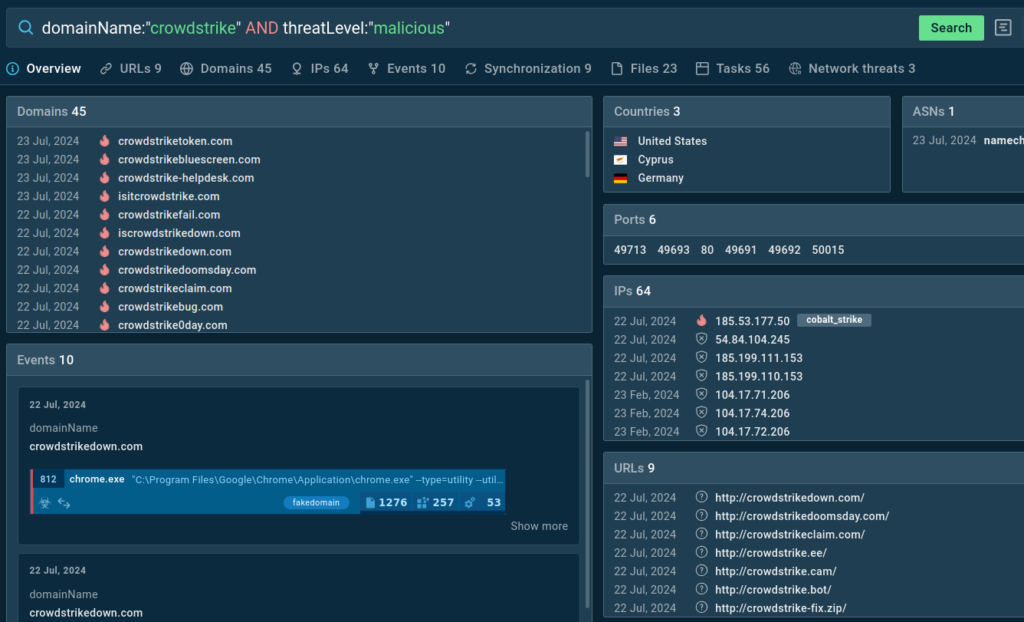 An example of a query for finding malicious domains mimicking CrowdStrike’s
An example of a query for finding malicious domains mimicking CrowdStrike’sUse queries like the ones below to look for more examples of websites impersonating CrowdStrike:
<tbody> <tr>
<td>
<a href="https://intelligence.any.run/analysis/lookup#%7B%2522query%2522:%2522domainName:%255C%2522crowdstrike%255C%2522%2520AND%2520threatLevel:%255C%2522malicious%255C%2522%2520%2522,%2522dateRange%2522:180%7D" rel="noreferrer" target="_blank">domainName:”crowdstrike" AND threatLevel:"malicious"</a>
domainName:”crowdstrike" AND threatLevel:"malicious"
Our analysts have created a Suricata rule to identify domains that may contain phishing or malicious software.
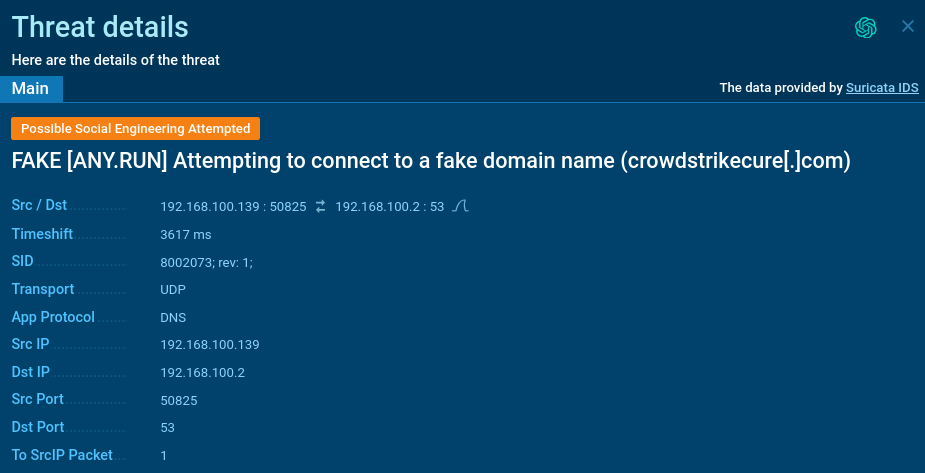 Suricata rule used for detecting fake domains
Suricata rule used for detecting fake domains <tbody> <tr>
<td>
<a href="https://app.any.run/submissions/#tag:fakedomain" rel="noreferrer" target="_blank">https://app.any.run/submissions/#tag:fakedomain</a> </td>
</tr>
</tbody></table>
Malicious Archive with Remcos
After the incident, there has been a rise in campaigns spreading malware as updates or #bug fixes.
One of the first instances of malware observed by ANY.RUN, disguised as a CrowdStrike hotfix, was an archive containing Hijackloader.
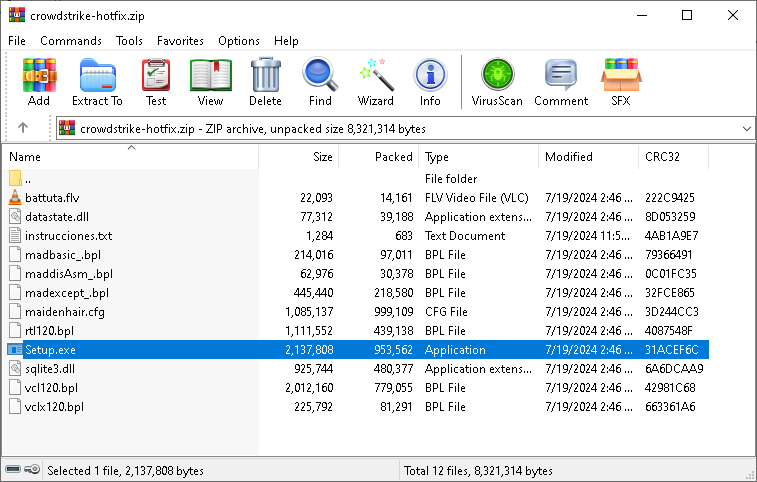 The malicious archive
The malicious archiveThe malicious file, named “crowdstrike-hotfix”, was distributed from hxxps://portalintranetgrupobbva[.]com. After execution, it delivered Remcos to the infected system.
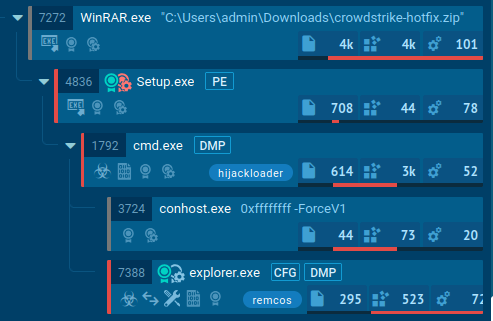 Process tree in ANY.RUN showing the infection chain
Process tree in ANY.RUN showing the infection chain To identify more suspicious files disguised as CrowdStrike updates, use TI Lookup with queries like:
<tbody> <tr>
<td>
<a href="https://intelligence.any.run/analysis/lookup#{%22query%22:%22fileName:%5C%22crowdstrike%5C%22%C2%A0AND%C2%A0threatLevel:%5C%22malicious%5C%22%22,%22dateRange%22:180}" rel="noreferrer" target="_blank">fileName:"crowdstrike" AND threatLevel:"malicious"</a> </td>
</tr>
</tbody></table>
IOCs:
<tbody> <tr>
<td>
crowdstrike-hotfix.zip </td>
<td>
c44506fe6e1ede5a104008755abf5b6ace51f1a84ad656a2dccc7f2c39c0eca2 </td>
</tr>
<tr>
<td>
Setup.exe </td>
<td>
5ae3838d77c2102766538f783d0a4b4205e7d2cdba4e0ad2ab332dc8ab32fea9 </td>
</tr>
<tr>
<td>
maddisAsm_.bpl </td>
<td>
52019f47f96ca868fa4e747c3b99cba1b7aa57317bf8ebf9fcbf09aa576fe006 </td>
</tr>
<tr>
<td>
battuta.flv </td>
<td>
be074196291ccf74b3c4c8bd292f92da99ec37a25dc8af651bd0ba3f0d020349 </td>
</tr>
<tr>
<td>
sqlite3.dll </td>
<td>
02f37a8e3d1790ac90c04bc50de73cd1a93e27caf833a1e1211b9cc6294ecee5 </td>
</tr>
<tr>
<td>
vclx120.bpl </td>
<td>
2bdf023c439010ce0a786ec75d943a80a8f01363712bbf69afc29d3e2b5306ed </td>
</tr>
<tr>
<td>
rtl120.bpl </td>
<td>
b1fcb0339b9ef4860bb1ed1e5ba0e148321be64696af64f3b1643d1311028cb3 </td>
</tr>
<tr>
<td>
maidenhair.cfg </td>
<td>
931308cfe733376e19d6cd2401e27f8b2945cec0b9c696aebe7029ea76d45bf6 </td>
</tr>
<tr>
<td>
datastate.dll </td>
<td>
6010e2147a0f51a7bfa2f942a5a9eaad9a294f463f717963b486ed3f53d305c2 </td>
</tr>
<tr>
<td>
madexcept_.bpl </td>
<td>
835f1141ece59c36b18e76927572d229136aeb12eff44cb4ba98d7808257c299 </td>
</tr>
<tr>
<td>
vcl120.bpl </td>
<td>
b6f321a48812dc922b26953020c9a60949ec429a921033cfaf1e9f7d088ee628 </td>
</tr>
<tr>
<td>
madbasic_.bpl </td>
<td>
d6d5ff8e9dc6d2b195a6715280c2f1ba471048a7ce68d256040672b801fda0ea </td>
</tr>
<tr>
<td>
instrucciones.txt </td>
<td>
4f450abaa4daf72d974a830b16f91deed77ba62412804dca41a6d42a7d8b6fd0 </td>
</tr>
<tr>
<td>
Domain: </td>
<td>
hxxps://portalintranetgrupobbva[.]com/ </td>
</tr>
<tr>
<td>
C2 </td>
<td>
213.5.130.58:443 </td>
</tr>
<tr>
<td>
URLs: </td>
<td>
mail.zoomfilms-cz[.]com discussiowardder[.]website wxt82[.]xyz </td>
</tr>
</tbody></table>
Phishing Email with a Data Wiper
The most sophisticated attack so far involved the distribution of a data wiper.
 Phishing pdf
Phishing pdf It began with the CrowdStrike-themed phishing email and PDF attachment, which, in turn, included a link to downloading a ZIP file.
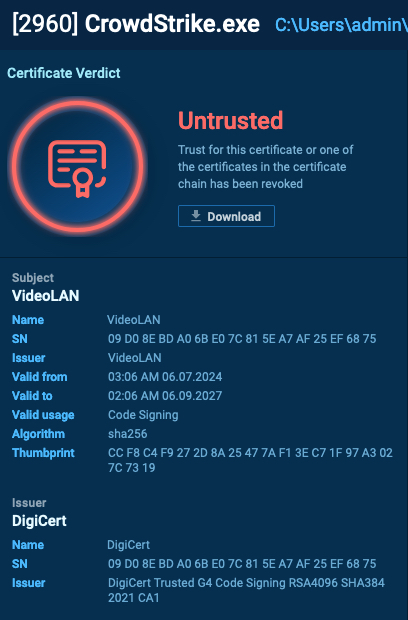 Certificate verdict in ANY.RUN
Certificate verdict in ANY.RUN The archive contained an executable that, once launched, asked the user if they wanted to install the update.
 Destroyed file
Destroyed fileUpon launching, the wiper devastated the system by overwriting files with zero bytes and then reported it over Telegram.
See analysis session in ANY.RUN
IOCs
<tbody> <tr>
<td>
update2.pdf </td>
<td>
1bbb795ce19f4dcc4ac9f8e8c12f3452f1f07c68a53ef631c76e392e1d06ea43 </td>
</tr>
<tr>
<td>
update.zip </td>
<td>
96dec6e07229201a02f538310815c695cf6147c548ff1c6a0def2fe38f3dcbc8 </td>
</tr>
<tr>
<td>
CrowdStrike.exe </td>
<td>
4491901eff338ab52c85a77a3fbd3ce80fda738046ee3b7da7be468da5b331a3 </td>
</tr>
<tr>
<td>
URL </td>
<td>
hxxps://link.storjshare[.]io/s/jwyite7mez2ilyvm2esxw2jq3apq/crowdstrikeisrael/update.zip?download=1 </td>
</tr>
</tbody></table>
Malicious Document with a Stealer
Attackers also used other ways to trick unsuspecting victims into running malware.
The picture below shows a harmful document that claims to provide instructions on how to resolve the issue.
Yet, when opened, it uses a bad VBS (Visual Basic Script) to start a series of tools on the infected computer.
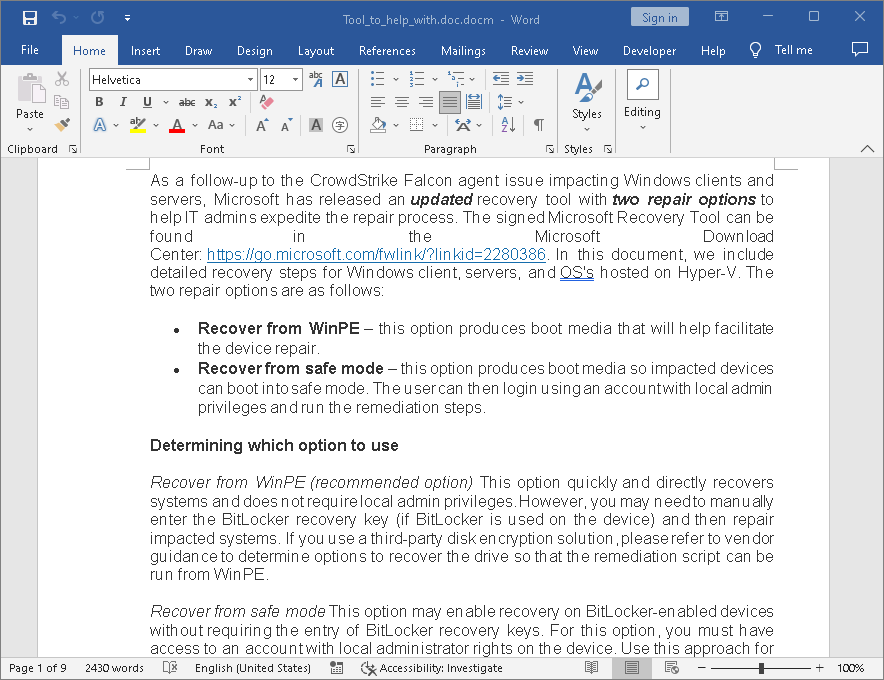 The malicious .docm file that kickstarts the malware
The malicious .docm file that kickstarts the malwareAfter execution, it downloads and launches a stealer malware using curl.
IOCs
Malicious document
<tbody> <tr>
<td>
Name </td>
<td>
New_Recovery_Tool_to_help_with_CrowdStrike_issue_impacting_Windows.docm </td>
</tr>
<tr>
<td>
Hash sum </td>
<td>
803727ccdf441e49096f3fd48107a5fe55c56c080f46773cd649c9e55ec1be61 </td>
</tr>
<tr>
<td>
URL </td>
<td>
hxxp[://]172.104.160[.]126:8099/payload2[.]txt </td>
</tr>
</tbody></table>
Stealer
<tbody> <tr>
<td>
Hash sum </td>
<td>
4ad9845e691dd415420e0c253ba452772495c0b971f48294b54631e79a22644a </td>
</tr>
<tr>
<td>
URL </td>
<td>
172.104.160.126:5000 </td>
</tr>
</tbody></table>
Recommendations
Users and organizations are advised to remain vigilant and thoroughly verify any updates or hotfixes before installation.
For any information concerning the course of action for affected users, it is important to follow CrowdStrike’s official statements and guidance.
The post Find Threats Exploiting CrowdStrike Outage with TI Lookup appeared first on ANY.RUN's Cybersecurity Blog.
Article Link: Find Threats Exploiting CrowdStrike Outage with TI Lookup - ANY.RUN's Cybersecurity Blog