This tutorial is an excerpt of my own master thesis which was modified for blog usage.
Viruses use different strategies to infect host files. This article explains these strategies so that the infection type of viruses can be identified during analysis.
Depending on the file infection strategy it is sometimes possible to remove or disable the malicious code from an infected file. This process is called disinfection and performed by antivirus software. Disinfection does not necessarily restore the file to its original form.
Overwriting
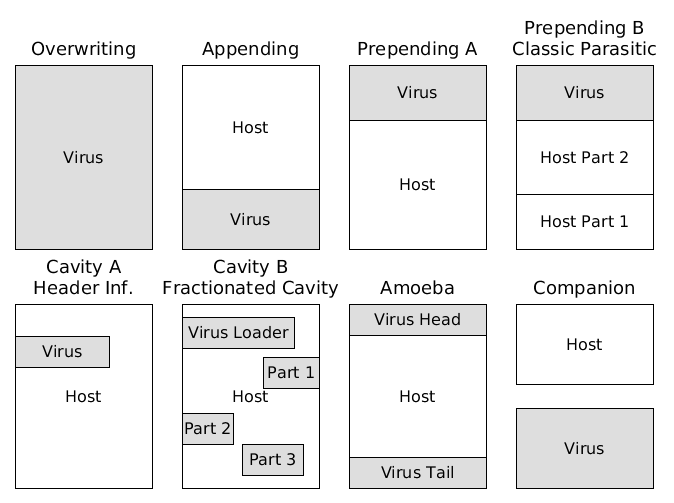
Overwriting viruses employ the simplest strategy. They search for other files on disk and copy their own body in place of them (see page 115 in szor05). Infections by overwriting viruses can cause severe damage to the system because they destroy the files they are overwriting and render disinfection impossible. Users can recognise the side effects of the damage soon, which is why this infection strategy is usually not very successful (see page 115 in szor05).
A variant of the overwriting virus only replaces the beginning of the host file with its own body (see page 116 in szor05). The infected file keeps the original size of the host file. The overwritten part of the host file is destroyed.
Appending
Appending viruses write their own body after the end of the host file and modify a jump instruction at the beginning of the host file to point to the virus code (see page 117 in szor05). The appending virus typically passes control to the host file again after it has done its tasks, so the user does not get aware of the infection (see page 118 in szor05).
Some file formats, like the Portable Executable format, define an entry point, which is an address that points to the start of code execution. Viruses appending to these file formats may change the address of the entry point to point to the virus code, or add a jump instruction right after the entry point to jump to the virus code.
Files that were infected by appending viruses usually can be disinfected.
Prepending
Infection by prepending is done by writing the virus code to the front of the file (see pages 118--120 in szor05). The original file stays intact, which makes disinfection possible.
To hide the infection from the user, the prepending virus executes the host file, \eg{, by copying the host file as temporary file to disk and using a function call like system() to run the host file (see page 120 in szor05).
A subtype of infection by prepending is the classic parasitic infection (see Prepending B in figure). A virus that employs this strategy replaces the beginning of the host file with its own body and appends the overwritten part to the host file (see pages 120, 121 in szor05).
Cavity Infection
Cavity viruses overwrite parts of the host file that are not necessarily used by the host file (see page 121 in szor05). These are usually parts that contain only zeroes---so called caves of the file (see page 121 in szor05). An example is the cave between the file header and the actual start of the file. If a virus infects this cave, it is called header infection (see Cavity A in figure). Viruses that infect a single cave must be small enough to fit into them.
The cavity virus may save the original entry point of the host file and pass control to the host file after it is done.
A subtype of the cavity infection is the fractionated cavity infection (see Cavity B in figure), where the virus splits itself and writes the code fractions into several caves. The first fraction contains the loader code, which is responsible to put the virus' fractions back together in memory (see pages 122, 123 in szor05).
Disinfection of a host file with cavity infection can be complicated and is sometimes impossible if the overwritten parts cannot be restored (see page 123 in szor05).
Amoeba Infection
This infection strategy is rare according to Szor page 124 in szor05. The virus splits itself into two parts. The head is prepended to the host file and the tail is appended. If the file is executed the head will load the tail of the virus to execute it.
The amoeba virus may reconstruct the host file, write it to disk as temporary file and execute it.
Companion Infection
Companion viruses do not modify the host file. They take advantage of the order the operating system executes files, so they are executed instead of the host file.
There are three types of companion viruses:
The companion virus exists beside its host file.
Deletion of the companion file or the alias in case of an alias companion will remove the infection.
References
Viruses use different strategies to infect host files. This article explains these strategies so that the infection type of viruses can be identified during analysis.
Depending on the file infection strategy it is sometimes possible to remove or disable the malicious code from an infected file. This process is called disinfection and performed by antivirus software. Disinfection does not necessarily restore the file to its original form.

Overwriting
Overwriting viruses employ the simplest strategy. They search for other files on disk and copy their own body in place of them (see page 115 in szor05). Infections by overwriting viruses can cause severe damage to the system because they destroy the files they are overwriting and render disinfection impossible. Users can recognise the side effects of the damage soon, which is why this infection strategy is usually not very successful (see page 115 in szor05).
A variant of the overwriting virus only replaces the beginning of the host file with its own body (see page 116 in szor05). The infected file keeps the original size of the host file. The overwritten part of the host file is destroyed.
Appending
Appending viruses write their own body after the end of the host file and modify a jump instruction at the beginning of the host file to point to the virus code (see page 117 in szor05). The appending virus typically passes control to the host file again after it has done its tasks, so the user does not get aware of the infection (see page 118 in szor05).
Some file formats, like the Portable Executable format, define an entry point, which is an address that points to the start of code execution. Viruses appending to these file formats may change the address of the entry point to point to the virus code, or add a jump instruction right after the entry point to jump to the virus code.
Files that were infected by appending viruses usually can be disinfected.
Prepending
Infection by prepending is done by writing the virus code to the front of the file (see pages 118--120 in szor05). The original file stays intact, which makes disinfection possible.
To hide the infection from the user, the prepending virus executes the host file, \eg{, by copying the host file as temporary file to disk and using a function call like system() to run the host file (see page 120 in szor05).
A subtype of infection by prepending is the classic parasitic infection (see Prepending B in figure). A virus that employs this strategy replaces the beginning of the host file with its own body and appends the overwritten part to the host file (see pages 120, 121 in szor05).
Cavity Infection
Cavity viruses overwrite parts of the host file that are not necessarily used by the host file (see page 121 in szor05). These are usually parts that contain only zeroes---so called caves of the file (see page 121 in szor05). An example is the cave between the file header and the actual start of the file. If a virus infects this cave, it is called header infection (see Cavity A in figure). Viruses that infect a single cave must be small enough to fit into them.
The cavity virus may save the original entry point of the host file and pass control to the host file after it is done.
A subtype of the cavity infection is the fractionated cavity infection (see Cavity B in figure), where the virus splits itself and writes the code fractions into several caves. The first fraction contains the loader code, which is responsible to put the virus' fractions back together in memory (see pages 122, 123 in szor05).
Disinfection of a host file with cavity infection can be complicated and is sometimes impossible if the overwritten parts cannot be restored (see page 123 in szor05).
Amoeba Infection
This infection strategy is rare according to Szor page 124 in szor05. The virus splits itself into two parts. The head is prepended to the host file and the tail is appended. If the file is executed the head will load the tail of the virus to execute it.
The amoeba virus may reconstruct the host file, write it to disk as temporary file and execute it.
Companion Infection
Companion viruses do not modify the host file. They take advantage of the order the operating system executes files, so they are executed instead of the host file.
There are three types of companion viruses:
- The regular companion places itself in the same directory as the host file, having the same filename, but a different file extension. If the user only gives the filename without the extension, the regular companion will be executed instead of the host file (see section 2.2.1 in bontchev00). For example files with the extension .COM are searched before files with the extension .EXE on MS-DOS. A companion virus can infect files with .EXE extension by placing itself in the same directory and the same filename with a .COM extension (see section 2.2.1 in bontchev00).
- The PATH companion takes advantage of the order of directories that the operating system uses to search for files. Operating systems usually have a variable called PATH that determines the search order for executable files. The PATH companion has the same name as its host file and places itself in a directory that takes precedence over the directory of the host file. (see section 2.2.2 in bontchev00). An example are viruses that mimic common DLL files. Applications that import functions of a DLL can be tricked into loading the functions of the virus instead of the actual DLL file.
- The alias companion uses user-defined command-line macros, aka aliases, to get executed (see section 2.2.2 in bontchev00). Aliases are used as a shortcut for long command sequences. A virus can create an alias that replaces a common command with execution of the companion (see section 2.2.3 in bontchev00).
The companion virus exists beside its host file.
Deletion of the companion file or the alias in case of an alias companion will remove the infection.
References
@misc{bontchev00,
howpublished = {\url{http://repo.hackerzvoice.net/depot_madchat/vxdevl/vdat/epposatt.htm} (last access on Oct. 2014)},
author = {Vesselin Bontchev},
title = {{Possible Virus Attacks Against Integrity Programs and How to Prevent Them}},
year = {1994},
}
@book{szor05,
author = {Peter Szor},
title = {{The Art of Computer Virus Research and Defense}},
publisher = {Addison Wesley Professional},
year = {2005},
pages = {744},
month = {February},
isbn = {0321304543}
}
Article Link: http://struppigel.blogspot.com/2017/11/file-infection-strategies.html