Static and Dynamic Analysis.
In this blog i will be taking you through the tour of reversing the alleged malware app F-droid.
Analysis: Hammering off “F-droid” app
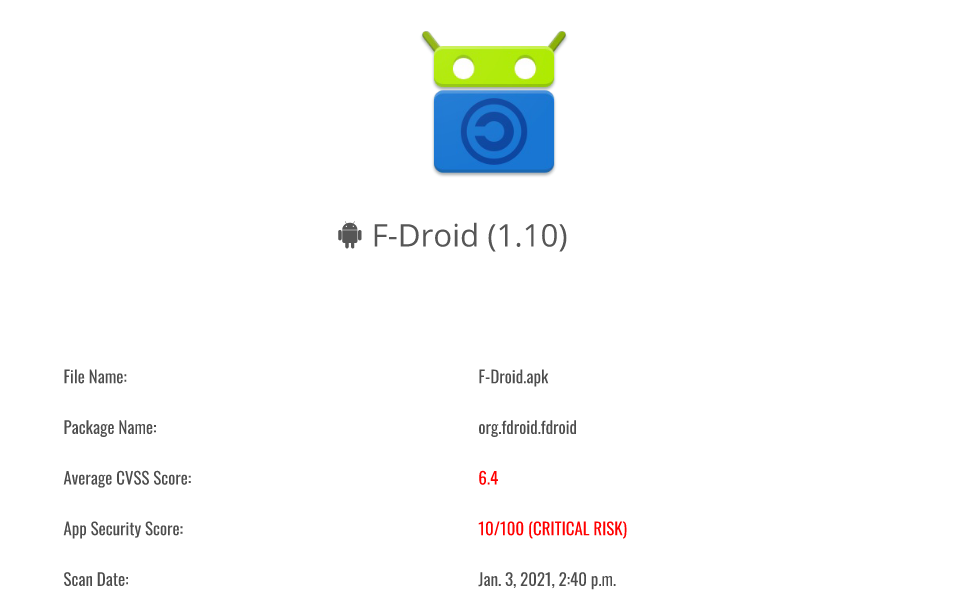
Static Analysis:-[Basic]
Hash’s:
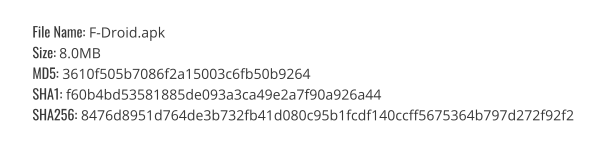 Hash’s of F-droid 1.10
Hash’s of F-droid 1.10Information about app :

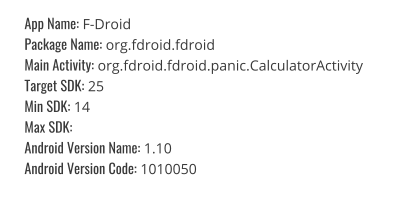 info. of App.
info. of App.Certificate Info:
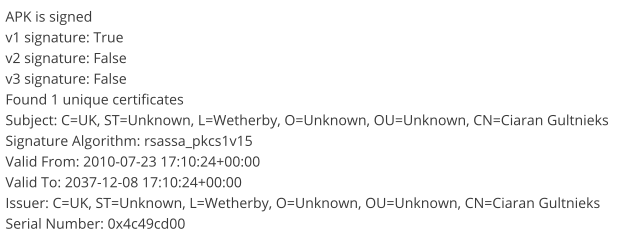 Certificate Information shows 2 false signature.
Certificate Information shows 2 false signature.App Permissions:
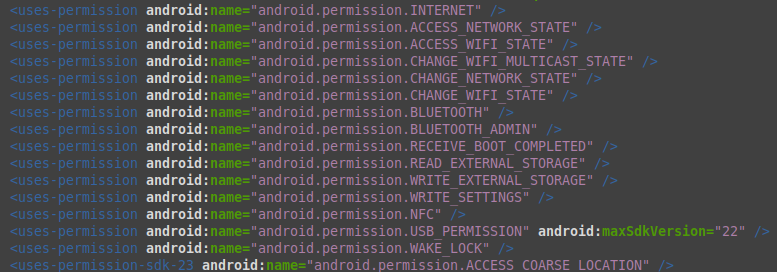 In image we can see app has access to many malicious permissions.
In image we can see app has access to many malicious permissions.Obfuscation and Anti-VM Code:
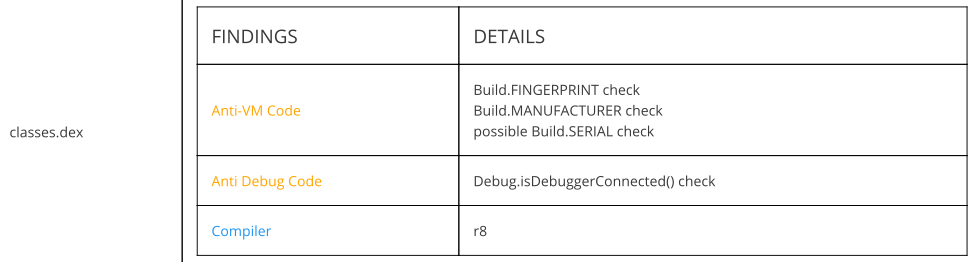 Anti-VM code and Anti-Debug Code used.
Anti-VM code and Anti-Debug Code used.Code Analysis:
App logs into the sensitive information, has weak hash’s, sensitive to SQL injection, app files contains hard-coded usernames and passwords, consists of insecure RNG and discloses the IP address.
Urls:
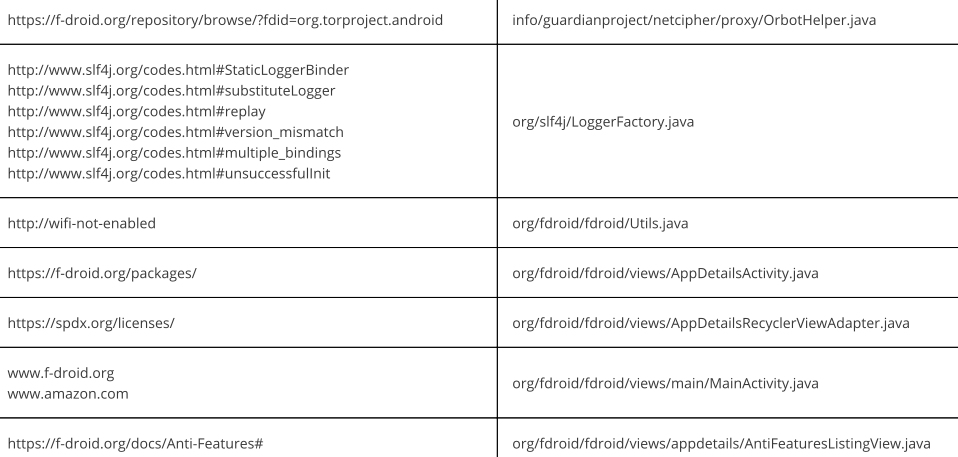 URLs found during static analysis of app.
URLs found during static analysis of app.Activities Run by App:
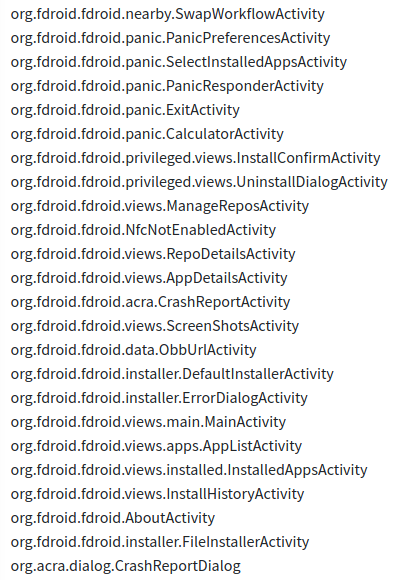 Activities found during static analysis of app.
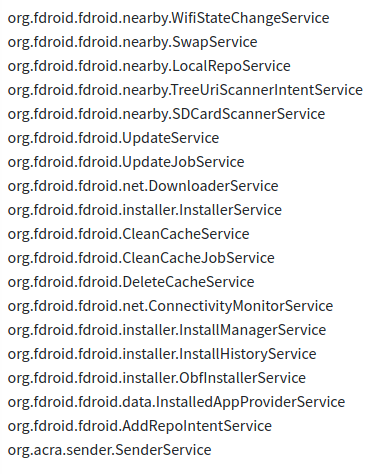
Activities found during static analysis of app.Services run by App:
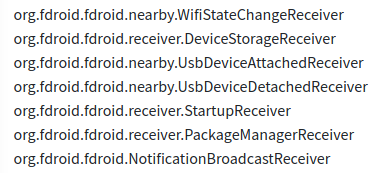
Receivers:
Dynamic Analysis:-
URLs:
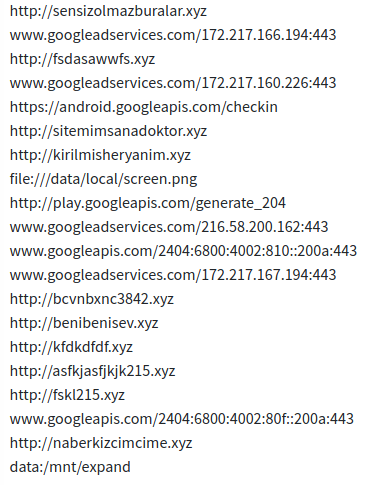
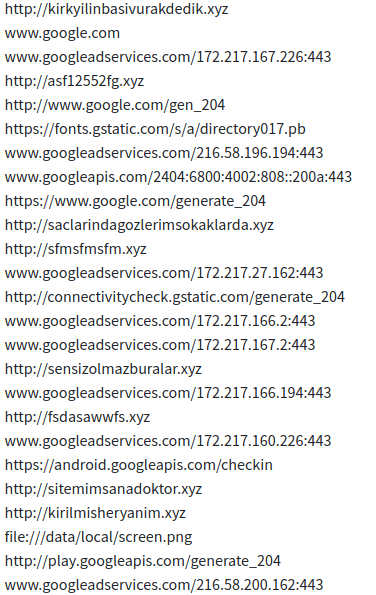 Urls found during dynamic analysis.
Urls found during dynamic analysis.Emails:
C2 Server:
148[.]251[.]140[.]42 & 217[.]160[.]165[.]113
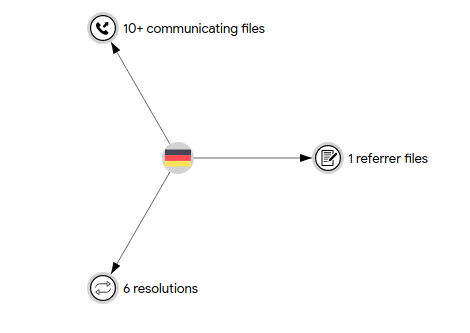
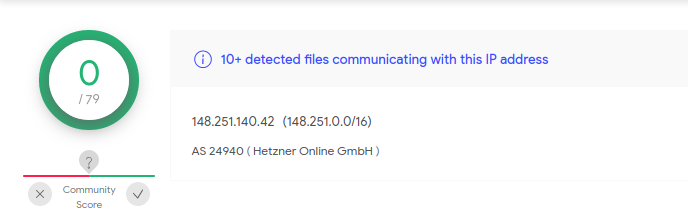
Communicating Files with C2 Server:
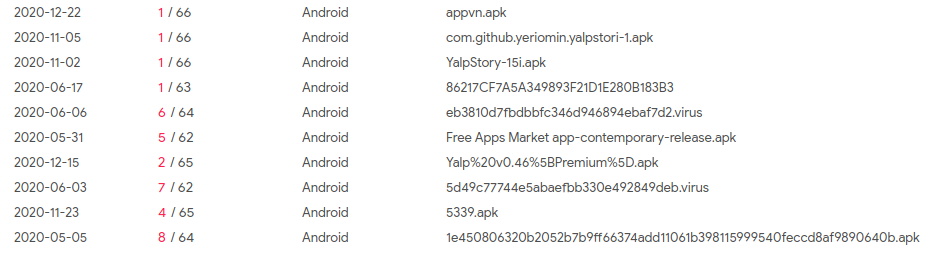
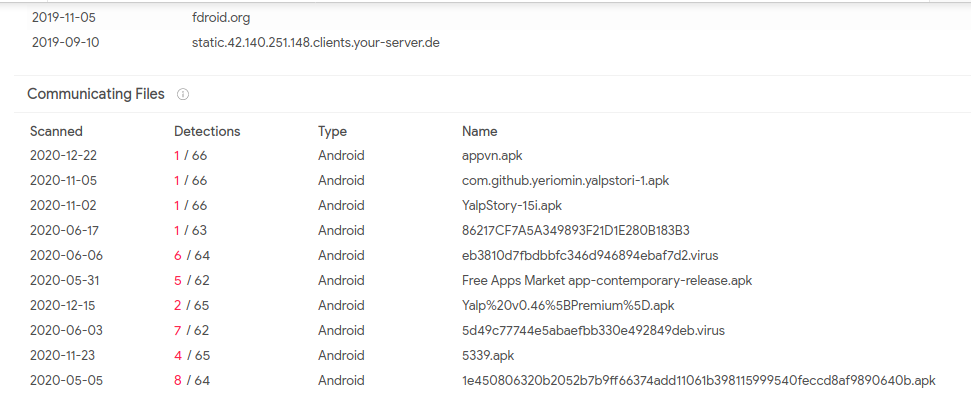 Files cmmunicating with C2 server.
Files cmmunicating with C2 server.Conclusion:
C2 server of F-droid app is hosting many apps that are legit hacking tools malware.
That’s all for today.
Article Link: https://medium.com/@0xthreatintel/f-droid-malware-internals-fefdc6307f05?source=rss-a15183055fd6------2