Estimated reading time: 4 minutes
Recently, we came across a new banking trojan called Coyote, which utilizes a tool/library called Squirrel Installer, developed to install and manage updates of windows applications. The malware looks more evolved than our normal banking trojans and can potentially be at a higher threat level in the coming days.
Some Background:
This newly found trojan targets different Brazilian Banking Institutions and points out the market it focuses on. The interesting thing is the involvement of Squirrel Installer. In the initial stage, it disguises itself as an update packager, and once executed, it sideloads the malicious code.
The end payload is written in .NET. Coyote Trojan works on loading the CLR (Common Language Runtime) and running the decrypted assembly with the help of it. This all happens in memory to evade possible AV detections.
Analysis:
On checking the malicious dll being loaded, we found that almost all the files’ exports point to the same code; this may increase the chance of execution (Fig1).
Md5 of the dll being discussed- 03eacccb664d517772a33255dff96020
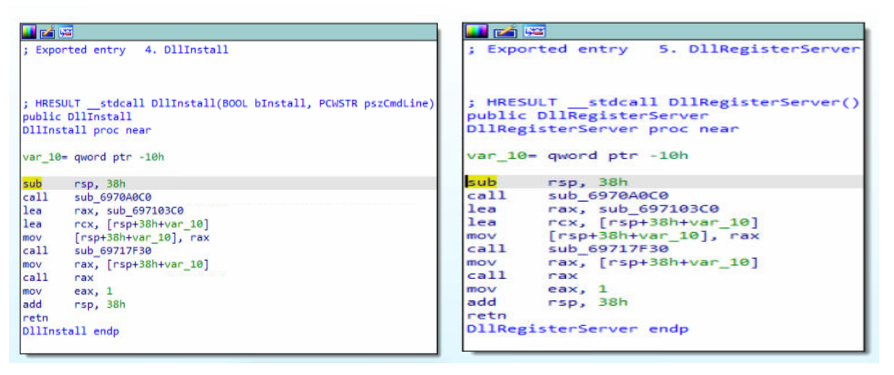
Fig1. Similar code in exports
On dynamic analysis of the DLL, we got an msil payload in memory, which was dumped for further analysis.
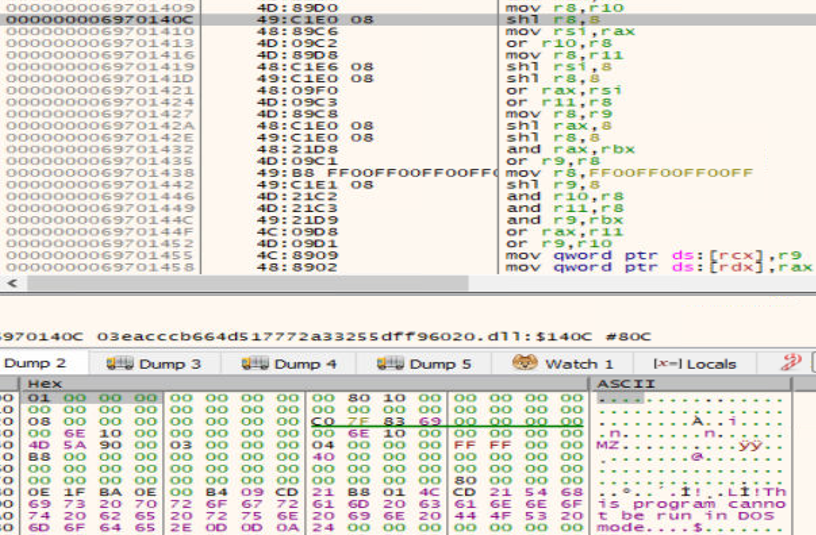
Fig2. Msil extracted from memory
Extracted file – ae688dff6f64f1317af09641ae037300
MSIL Payload:
On checking the MSIL file statically, we can see a list of base64 strings, which are called as per their index.
![]()
Fig3. Code being called as per index
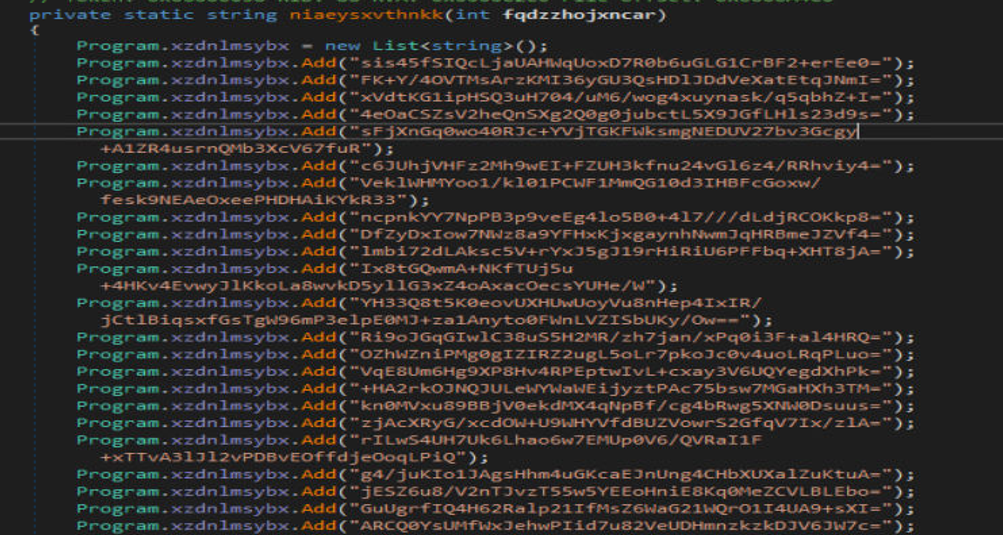
Fig4. Table of base64 strings
These are AES obfuscated strings that are decrypted by the below routine:
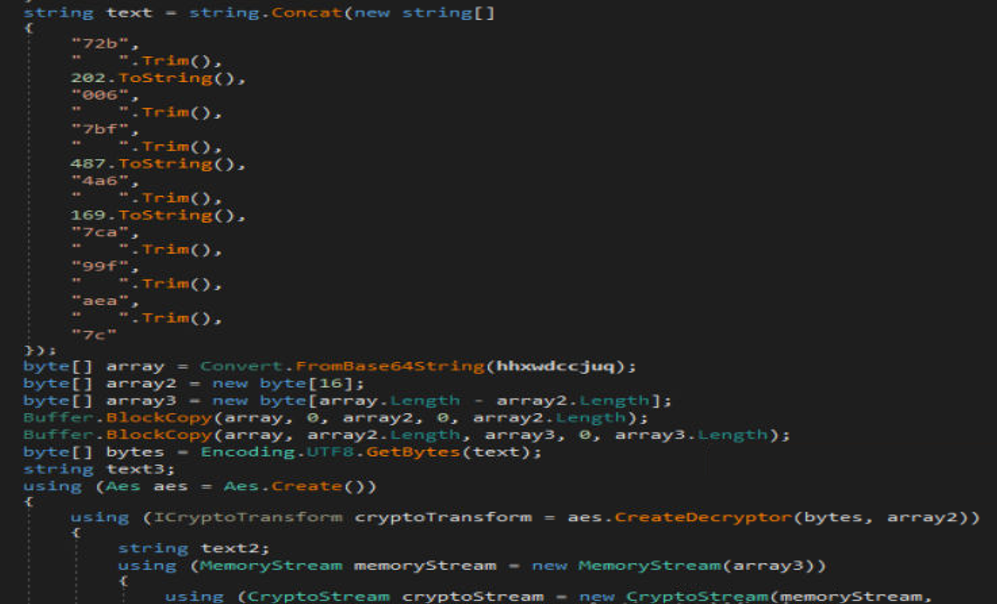
Fig5. AES decryption routine
In this process, each array undergoes conversion from base 64. The initial 16 bytes are extracted and allocated to array2, while the rest of the array constitutes encrypted code referred to as array3. Each file possesses a unique key, with array2 serving as the Initialization Vector for decrypting array3.
Behavior:
The payload achieves persistence by adding itself to HKCU\Environment\UserInitMprLogonScript
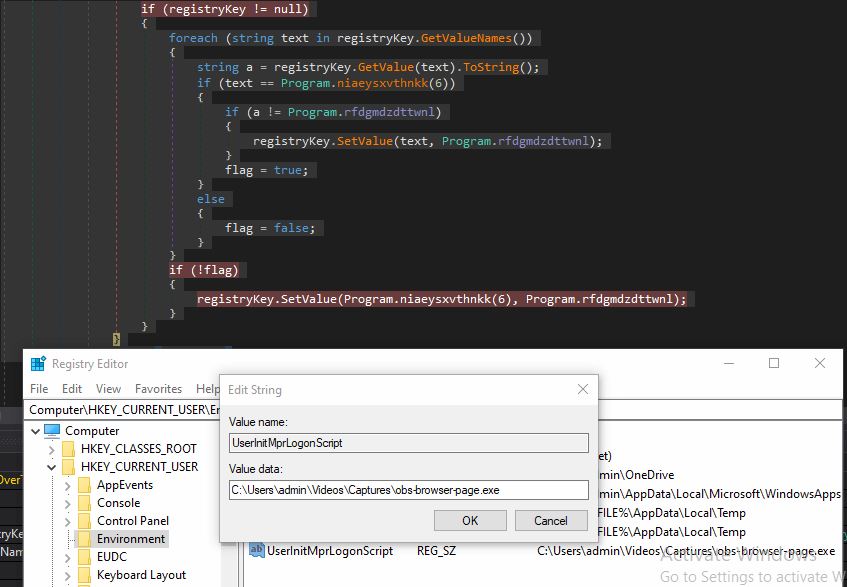
Fig6. Addition in UserInitMprLogonScript to achieve persistence
While running, it takes the value of foregroundwindow, i.e., the current screen a user is working on, and compares it with some banking application name, which are hardcoded in the application. Hardcoded names belong to different Brazilian banking institutes. If a user visits any of them, the trojan tries to establish a connection to the CnC server with some details like respective banking application details, Machine name etc.
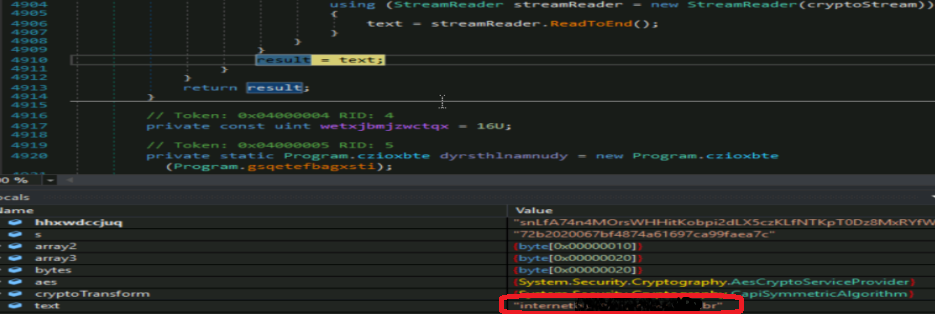
Fig7. Brazilian institutions targeted
Command and Control:
Before connecting to CnC, Coyote imports an embedded X.509certificate from its resource. This certificate is kept encrypted and used in the communication for the authentication and encryption process.
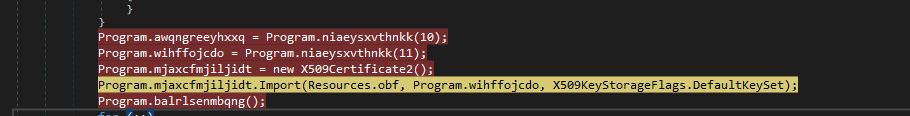
Fig8. Importing Certificate for Communication
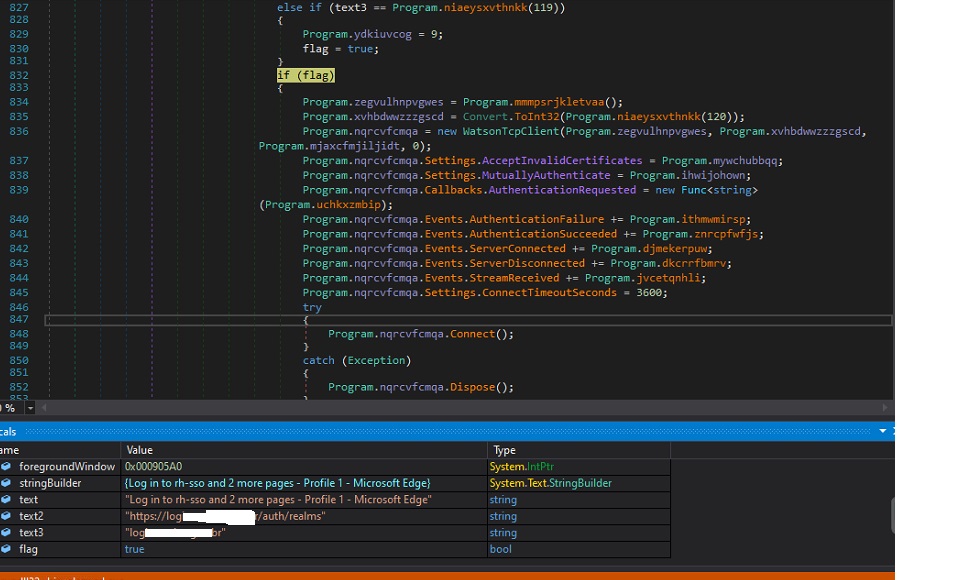
Fig9. Attempt to CnC Connect once the user visits specific websites (Banking Related)
If the connection is successful, the attacker sends a response string with the action that must be performed on the infected system, along with some other details. This response string contains a random separator to split the string.
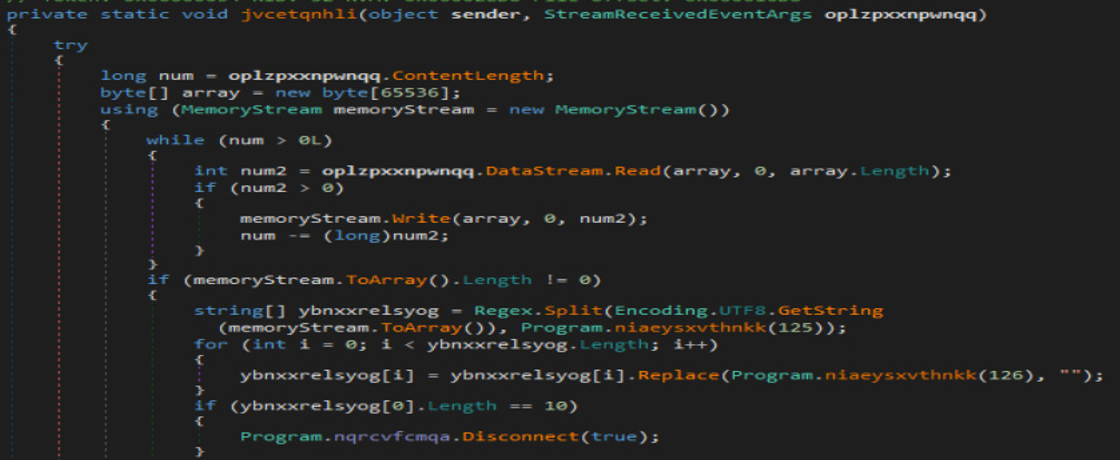
Fig10. Processing the string data received from CnC
The length of the first split string determines what action the trojan will take on the system. We have observed around 25 or more actions that are supported by it.
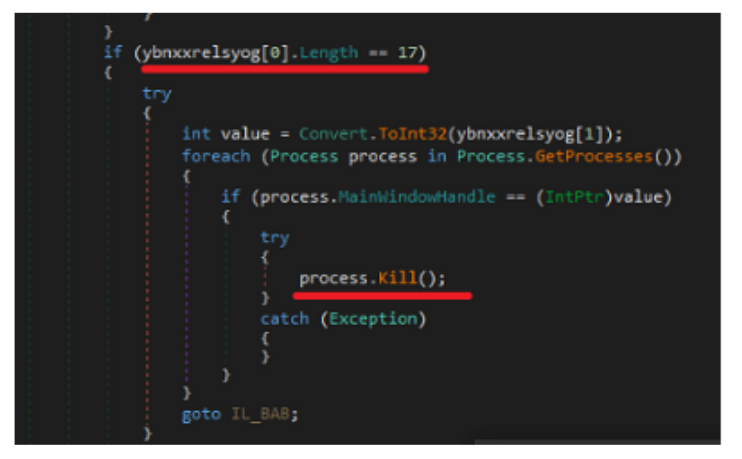
Fig11. Operation on the infected system as specified in the CnC response
Below is the list of some of the actions Coyote is capable of:
| Length | Action |
| 10 | Disconnect the connection |
| 12 | Taking screenshots and uploading them to servers |
| 14 | Setting a window as a foreground |
| 15 | Minimize the window identified by the handle |
| 16 | Attempting to bring a window to the foreground and then show it as usual. |
| 17 | Kill the process |
| 18 | Manipulating windows, E.g., Maximize |
| 21 | Starting a process with a handle |
| 22 | Setting the Registry values in the Current User space. |
| 23 | Simulating mouse actions, such as click |
| 24 | Simulate keyboard events |
| 26 | Disable Desktop Window Manager (DWM) composition |
| 27 | Executes a delegate in this thread |
| 31 | Key-logging |
| 33 | Handle keyboard commands |
| 34 | Iterate over Registry Entries |
Conclusion:
Coyote Trojan has unlocked a new evolution in banking trojan code, where the malware authors resort to new, more complex techniques than we have typically seen.
MITRE ATT&CK TTPs:
| T.1583.004 | Acquire Infrastructure |
| T.1037.001 | Boot or Logon Initialization Scripts |
| T.1574.002 | DLL Side-Loading |
| T1113 | ScreenCapture |
| T1041 | Exfiltration Over C2 Channel |
IOCs captured:
5134e6925ff1397fdda0f3b48afec87b
bf9c9cc94056bcdae6e579e724e8dbbd
3f27458d01eb53991770f18983a11a52
c00d8ec2f585c6197b8083951c504e50
7608ab0f1f07dc5842800fdebb0c372c
03eacccb664d517772a33255dff96020
071b6efd6d3ace1ad23ee0d6d3eead76
276f14d432601003b6bf0caa8cd82fec
URLs:
carfilmenew[.]com
carroderua[.]com
pepapigdesenho[.]com
nenembebe[.]com
carroeletrificante[.]com
You are protected:
Seqrite engine detects Coyote Trojan IOCs as Trojan.Coyote.S32693555 and Trojan.Coyote.S32879971
Author:
Kirti Kshatriya
Co-author:
Prashil Moon
The post Exposing Coyote: The Next-Gen Banking Trojan Revolutionizing Cyber Threats in Brazil appeared first on Blogs on Information Technology, Network & Cybersecurity | Seqrite.
Article Link: https://www.seqrite.com/blog/exposing-coyote-the-next-gen-banking-trojan-revolutionizing-cyber-threats-in-brazil/