Exploit Chain: When One Vulnerability Isn’t Enough
A vulnerability is a weakness that cybercriminals can exploit to gain unauthorized access to a computer system. Cybersecurity experts continually stress the importance of addressing these “vulnerabilities” because new ones emerge daily, adding to the ever-growing ocean of digital threats.
Once an attacker exploits a vulnerability, they can infiltrate a system, execute malicious code, install malware, steal sensitive data, or move laterally across a network. The possibilities are vast, depending on the type and severity of the vulnerability.
While even a single unchecked security flaw can bring a company demise, the situation becomes even more dire when exploit chains are involved. An exploit chain involves exploiting multiple vulnerabilities in succession, enabling further actions and sometimes amplifying the damage.
An AI-created visual for ‘Exploit Chain’ (DALL-E)
In this blog post, we will explore the concept of exploit chains, examine their applications, and look into recent examples for further context. Our aim is to provide a clear understanding of exploit chains, highlight real-world examples of their use in cyberattacks, and offer recommendations for mitigating the risks associated with this attack technique.
Why Do Attackers Chain Vulnerabilities?
Cyber attackers chain vulnerabilities as part of a strategic approach to compromise a target’s systems and data. This process involves exploiting multiple weaknesses in software, hardware, or network infrastructure to gain unauthorized access and execute attacks. In essence, a sequence of steps where each vulnerability exploited builds upon the previous one can be called an ‘exploit chain’.
By chaining vulnerabilities, attackers can also increase the likelihood of successfully breaching a system and achieving their objectives.
In some cases, chaining vulnerabilities gives attackers the flexibility to adapt their methods based on the target’s defenses. If one vulnerability is patched or mitigated, the attacker can shift to another, maintaining their foothold.
Other benefits of an exploit chain (from an attacker’s point of view) can be listed as follows:
- Escalated Privileges: Chaining vulnerabilities can help attackers escalate their privileges within a system. For example, an attacker might exploit one vulnerability to gain initial access and another to elevate their permissions, gaining more control over the compromised system.
- Increased Success Rate: By chaining vulnerabilities, attackers can create multiple points of entry, making it more difficult for defenders to protect their systems.
- Stealth and Persistence: Using multiple exploits in succession can help attackers remain undetected. Each vulnerability exploited can provide new ways to hide their presence, maintain control, and move laterally within the network.
- Compounding Damage: By exploiting several vulnerabilities, attackers can cause more extensive damage. They can move from one compromised area to another, exfiltrating data, disrupting operations, and spreading malware more effectively.
Anatomy of an Exploit Chain
Let’s examine an exemplary case of an exploit chain, in which an attacker first conducts intrusion and then escalates privileges.
- The attacker starts by identifying and exploiting a vulnerability that provides initial access to the target system. For example, they might use a phishing email containing a malicious attachment that exploits a vulnerability in a commonly used application, like a PDF reader.
- Once inside the system, the attacker uses another vulnerability to escalate privileges. They might exploit a known privilege escalation vulnerability in the specific operating system, which allows them to gain administrative rights.
- With elevated privileges, the attacker could move laterally within the network and exploit additional vulnerabilities to access other systems and data.
- Finally, the attacker achieves their ultimate goal, whether it is stealing data, installing ransomware, or disrupting operations. For instance, they might deploy ransomware, encrypting sensitive files and demanding a ransom. Alternatively, they could exfiltrate valuable data through an encrypted tunnel, ensuring that the stolen information is transferred to their remote server without detection.
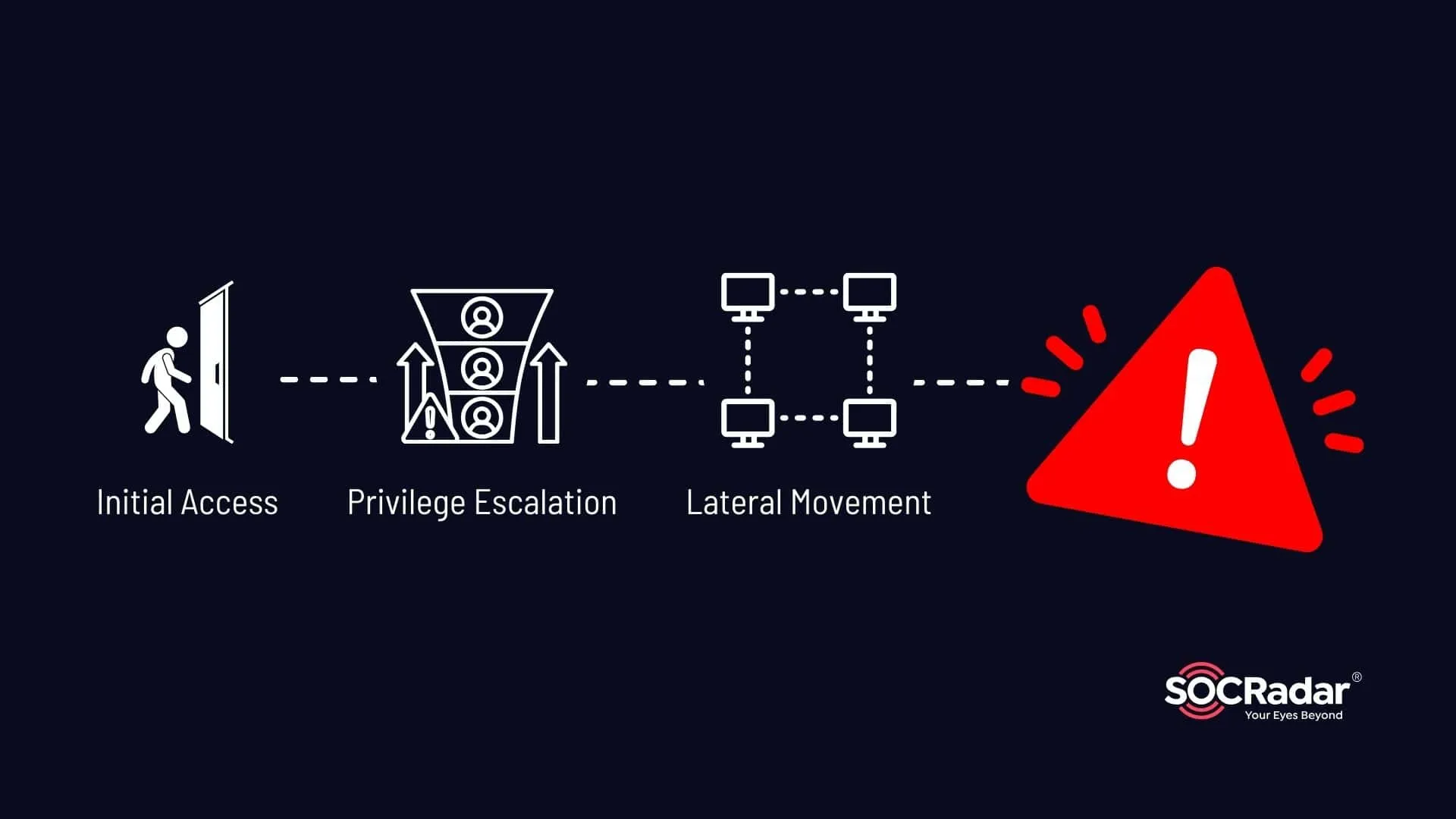
Simple visual for an exploit chain example
Each step in this example exploit chain brings the attacker closer to their objective, highlighting the importance of understanding and defending against such attacks.
Real Examples of Exploit Chains
Now that we have established an understanding of exploit chains and their use cases, let’s look at some real-world examples.
One well-known example is the ProxyShell attack chain, which exploits three critical vulnerabilities in Microsoft Exchange (CVE-2021-34473, CVE-2021-34523, and CVE-2021-31207) to perform remote code execution. This attack has been widely exploited for creating web shells and planting ransomware, demonstrating the power and danger of chained vulnerabilities.
Below, we outlined several, more recent examples of exploit chains, highlighting how attackers leverage multiple vulnerabilities to compromise systems and achieve their malicious goals.
CVE-2024-4879, CVE-2024-5217, and CVE-2024-5178 (ServiceNow, 2024)
Recently, threat actors have exploited ServiceNow security vulnerabilities to breach various organizations, conducting data theft attacks.
A ZoomEye search for ServiceNow reveals nearly 160,000 instances exposed on the internet, indicative of the issue’s scale.
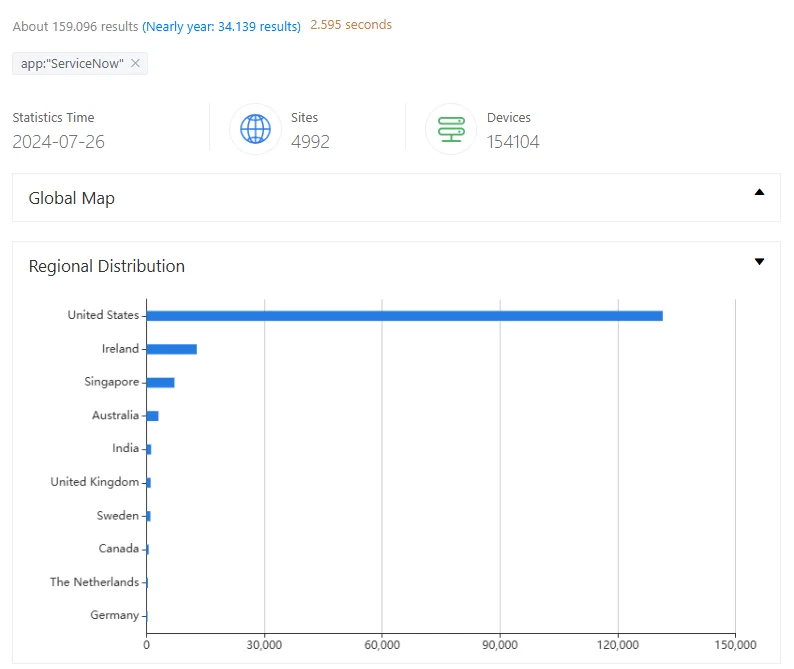
ZoomEye search results for ServiceNow
Threat actors have targeted a range of organizations, including government agencies, data centers, and software firms. The exploit chain involves three flaws:
- CVE-2024-4879 (CVSS: 9.8): An input validation flaw allowing remote code execution.
- CVE-2024-5217 (CVSS: 9.8): Another flaw enabling full database access.
- CVE-2024-5178 (CVSS: 4.9): An additional flaw contributing to full database access.
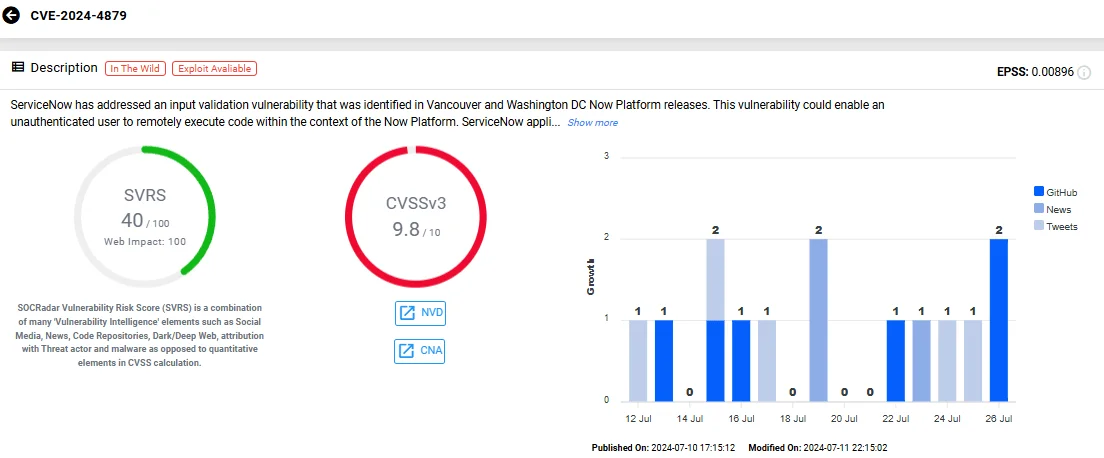
Vulnerability card of CVE-2024-4879 (SOCRadar Vulnerability Intelligence)
Researchers published details and exploits for these vulnerabilities, which threat actors quickly leveraged. Attackers use payload injection to check server responses, followed by a second payload to access database contents, leading to the theft of user lists and account credentials.
With ongoing exploitation and increasing interest from threat actors, it is crucial to update ServiceNow promptly to avoid breaches. Patches have been available since July 10, 2024, and can be found in the following advisories: CVE-2024-4879, CVE-2024-5178, and CVE-2024-5217.
CVE-2023-46805 and CVE-2024-21887 (Ivanti, 2024)
The CVE-2023-46805 (CVSS: 8.2) vulnerability in Ivanti Connect Secure and Ivanti Policy Secure allowed remote attackers to bypass authentication, while CVE-2024-21887 (CVSS: 9.1) permitted authenticated administrators to execute arbitrary commands via crafted requests. When used together, these vulnerabilities created a powerful exploit chain.
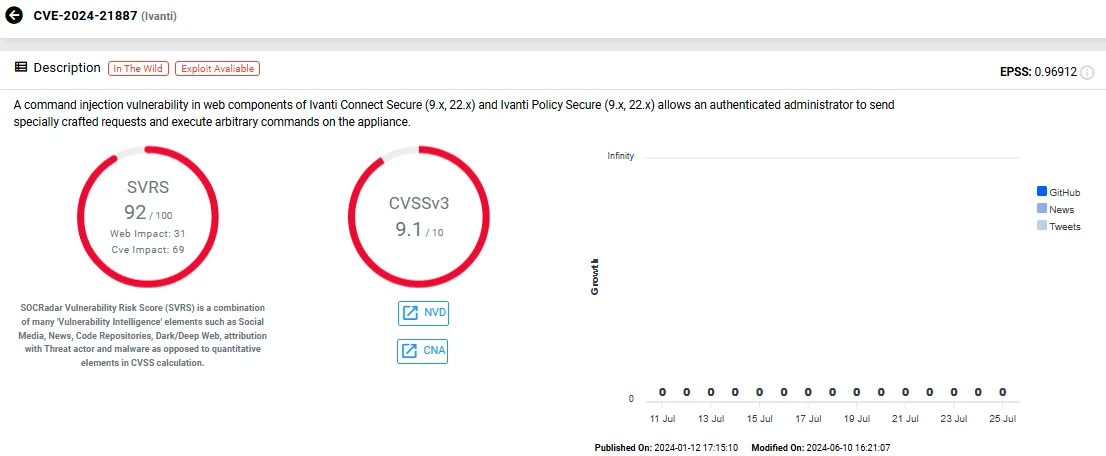
Vulnerability card of CVE-2024-21887 (SOCRadar Vulnerability Intelligence)
In a notable attack, threat actors first exploited CVE-2023-46805 to gain unauthorized access to Ivanti Connect Secure VPN appliances. They then leveraged CVE-2024-21887 to execute commands, which allowed them to steal configuration data, modify files, and download remote scripts. Researchers observed attackers using Living Off the Land (LOTL) techniques, deploying webshells, and bypassing integrity checks with tools like GLASSTOKEN and GIFTEDVISITOR webshells.
The attackers’ systematic approach included moving laterally within networks using compromised credentials and further exploiting systems via Remote Desktop Protocol (RDP). This multi-stage attack highlighted the effectiveness of chaining vulnerabilities to achieve deep network penetration and control.
CVE-2024-1708 and CVE-2024-1709 (ConnectWise, 2024)
Critical ConnectWise ScreenConnect vulnerabilities, CVE-2024-1708 and CVE-2024-1709, allowed attackers to gain unauthorized access and control over systems, leading to ransomware deployment and significant disruptions.
CVE-2024-1708 (CVSS: 8.4) is a path-traversal vulnerability that enabled attackers to access restricted directories and files, leading to potential information disclosure and system compromise. On the other hand, CVE-2024-1709 (CVSS: 10) is an authentication bypass vulnerability that allowed attackers to gain direct access to sensitive systems by exploiting a path issue in the SetupModule of ScreenConnect.Web.dll.
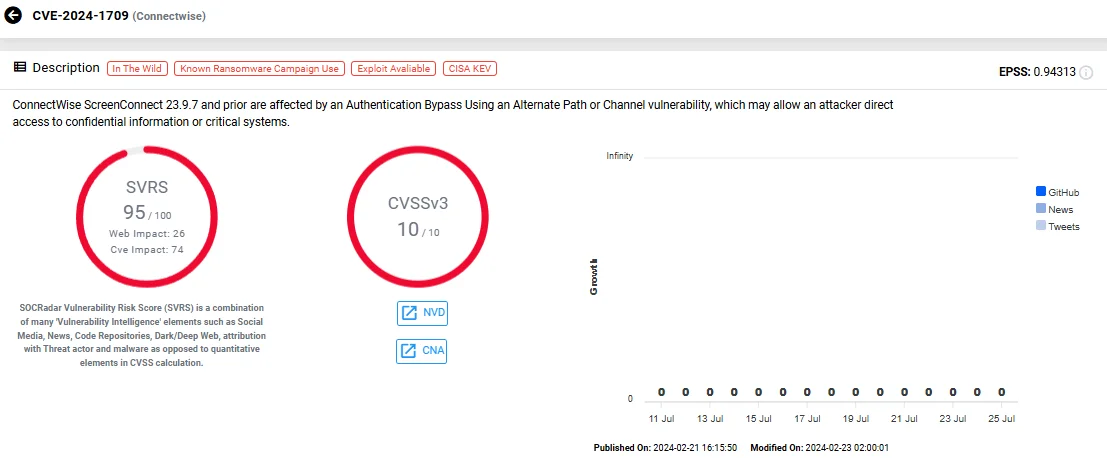
Vulnerability card of CVE-2024-1709 (SOCRadar Vulnerability Intelligence)
Attackers exploited CVE-2024-1709 to bypass authentication and then used CVE-2024-1708 to upload malicious files, such as web shells, achieving full remote code execution. This led to ransomware deployment and other malicious activities.
Notable threat actor groups, including Black Basta and Bl00dy Ransomware, actively exploited these vulnerabilities. Black Basta deployed Cobalt Strike beacons for reconnaissance and privilege escalation, while Bl00dy Ransomware used leaked builders to deploy ransomware.
Privilege Escalation Exploit Chain in Google Kubernetes Engine (Google, 2023)
An investigation revealed a dual privilege escalation chain that could have impacted Google Kubernetes Engine (GKE). This theoretical exploit chain, arising from misconfigurations in GKE’s FluentBit logging agent and Anthos Service Mesh (ASM), could have allowed attackers with initial cluster access to escalate their privileges.
Attackers could have first exploited the FluentBit container, which automatically mounted the /var/lib/kubelet/pods volume. By compromising FluentBit, they might have accessed service account tokens stored in the kube-api-access volume. These tokens would have enabled attackers to impersonate a privileged pod and interact with the Kubernetes API.
Next, attackers could have targeted Anthos Service Mesh’s (ASM) Container Network Interface (CNI) DaemonSet. This DaemonSet, enabled by ASM, retained excessive permissions post-installation. Attackers could have created new pods with these permissions, gaining administrative control over the Kubernetes cluster. By updating the clusterrole-aggregation-controller (CRAC) service account in the pod’s YAML file, attackers could have secured the CRAC token, achieving full cluster admin privileges.
SOCRadar’s Attack Surface Management module greatly enhances cloud security. The module can accurately identify if buckets are “public,” “private,” or “protected.” As part of its proactive approach, SOCRadar provides real-time alerts on bucket status changes and newly discovered user-owned cloud storage, effectively reducing the risk of vulnerabilities in your essential cloud assets.
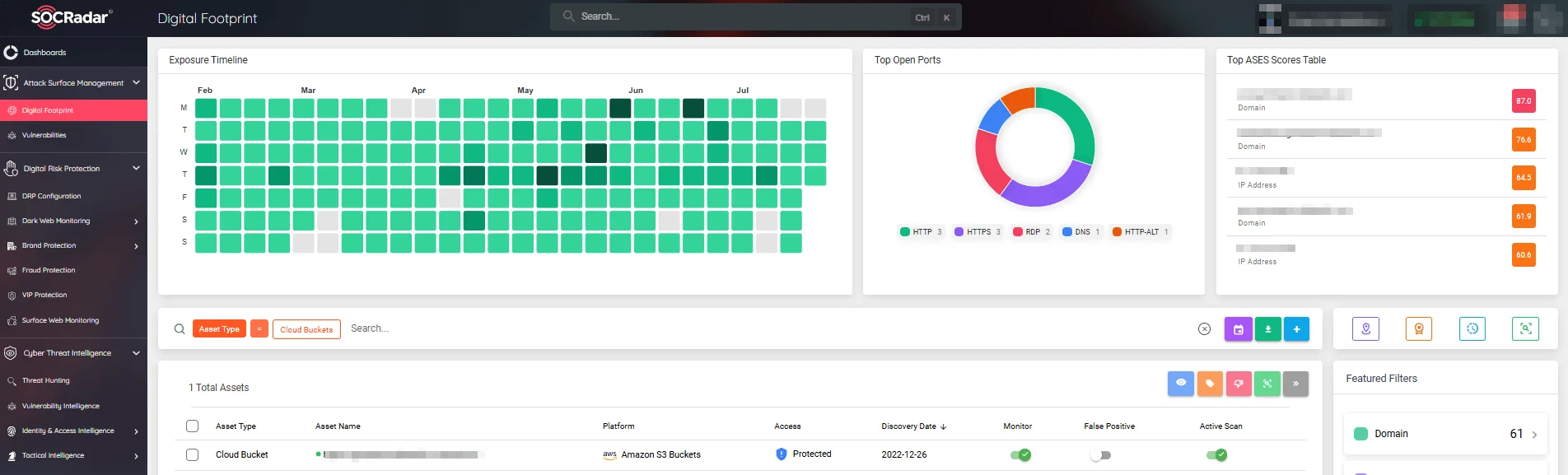
SOCRadar’s Attack Surface Management module, Digital Footprint
CVE-2023-41993, CVE-2023-41991, CVE-2023-41992, and CVE-2023-4762 (iOS, Android, 2023)
Google’s Threat Analysis Group (TAG) and The Citizen Lab uncovered an in-the-wild 0-day exploit chain targeting iPhones, developed by Intellexa to install Predator spyware.
Delivered via a Man-in-the-Middle (MITM) attack, this chain exploited three iOS vulnerabilities:
- CVE-2023-41993 (CVSS: 9.8), an RCE in Safari
- CVE-2023-41991 (CVSS: 5.5), a certificate validation issue
- CVE-2023-41992 (CVSS: 7.8), local privilege escalation in the XNU Kernel
By redirecting targets to an exploit server, the chain executed these vulnerabilities, installing Predator spyware without user interaction. TAG also identified a similar exploit chain for Android devices in Egypt, targeting Chrome with CVE-2023-4762.
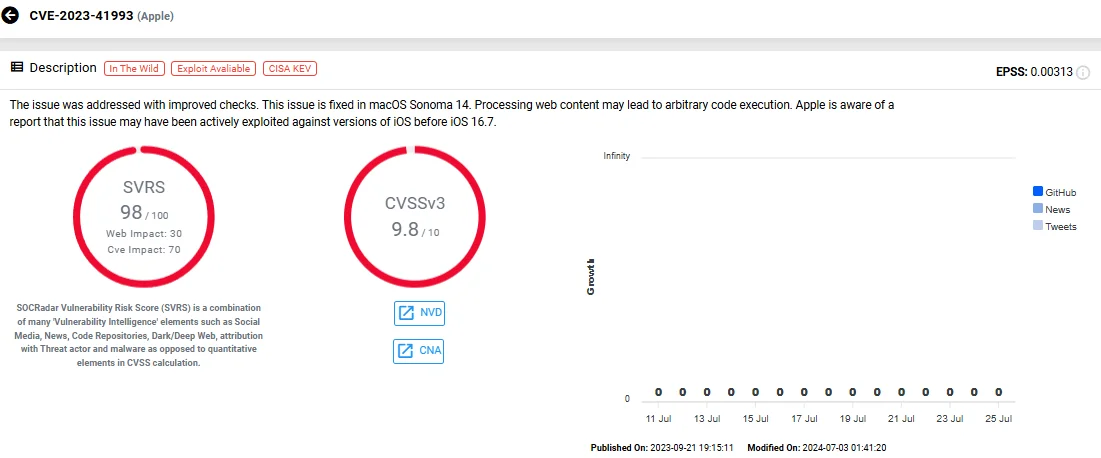
Vulnerability card of CVE-2023-41993 (SOCRadar Vulnerability Intelligence)
CVE-2023-41064 and CVE-2023-41061 (Apple, 2023)
A zero-click and zero-day exploit named BLASTPASS, developed by the NSO Group, was used to deliver the Pegasus spyware to Apple devices without any interaction from the victim.
Citizen Lab discovered the BLASTPASS exploit chain on a device belonging to an employee of a Washington DC-based civil society organization. This exploit was capable of compromising iPhones running iOS 16.6 through malicious PassKit attachments sent via iMessage. The attachments contained harmful images that executed the exploit upon receipt.
The exploit chain involved two CVEs:
- CVE-2023-41064 (CVSS: 7.8), a buffer overflow vulnerability in the ImageI/O framework that allows arbitrary code execution via maliciously crafted images.
- CVE-2023-41061 (CVSS: 7.8), a validation issue in Apple’s Wallet that enables arbitrary code execution through maliciously crafted attachments.
Recommendations for Mitigating Exploit Chain Risks
To mitigate the risks posed by exploit chains, organizations must prioritize proactive vulnerability management. Regular patching and vulnerability assessments are crucial for identifying and addressing potential weaknesses before threat actors can exploit them.
Implementing automated tools for continuous monitoring and scanning can further enhance vulnerability management efforts. For this purpose, you can rely on SOCRadar, utilizing the platform’s Attack Surface Management (ASM) and Vulnerability Intelligence modules for comprehensive protection.
The ASM module helps manage digital assets, providing continuous monitoring to discover potential exposure points, while the Vulnerability Intelligence module offers insights into emerging vulnerabilities, hacker trends, and exploitation activities, enabling swift response.
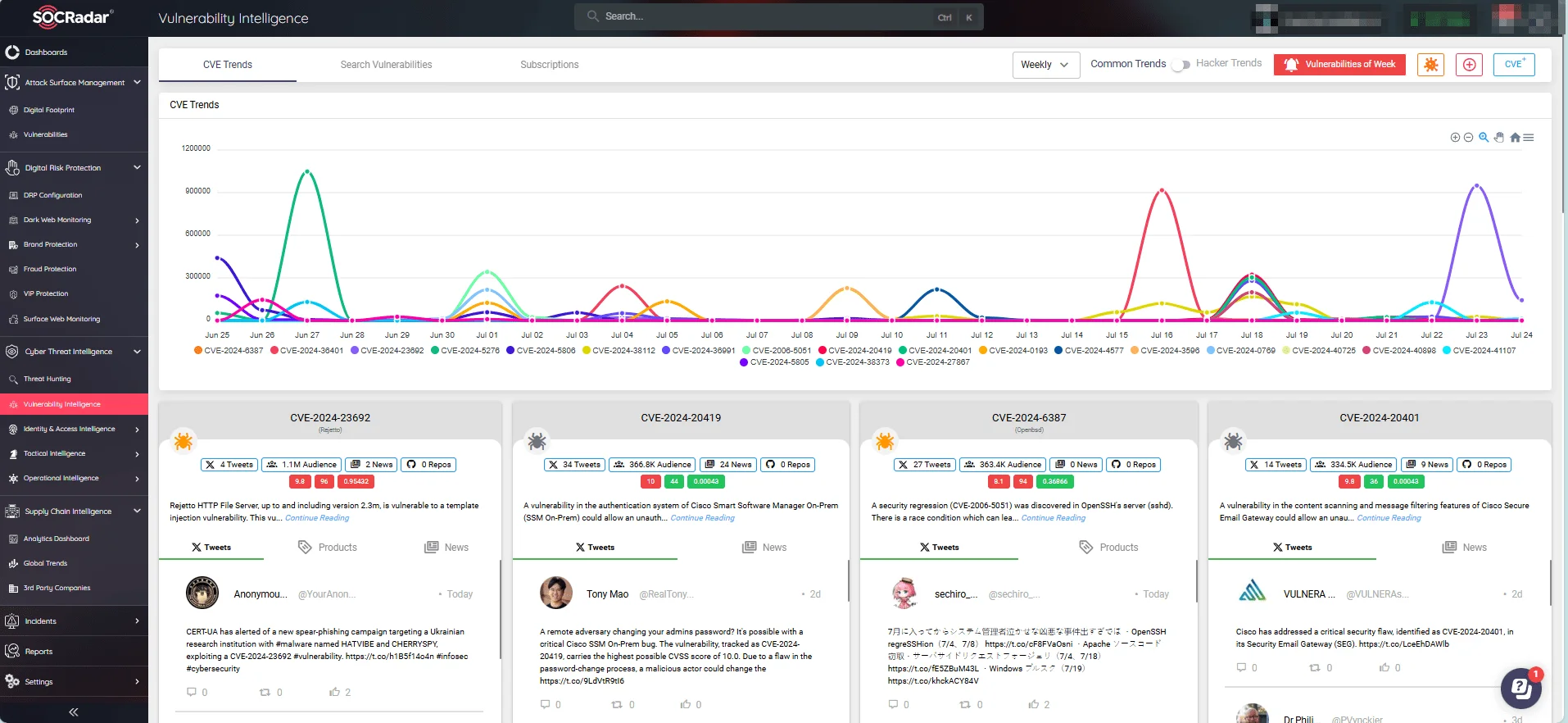
SOCRadar’s Vulnerability Intelligence: CVE and hacker trends, latest vulnerabilities
Implementing defense-in-depth strategies is also essential for mitigating the impact of vulnerabilities, or an exploit chain. Best practices include:
- Network Segmentation: Isolating different network segments to limit the lateral movement of attackers.
- Access Controls: Enforcing strict access controls to ensure that users and devices have only the permissions necessary for their roles.
- Endpoint Protection: Deploying comprehensive endpoint protection solutions to detect and block malicious activities.
Conclusion
In conclusion, exploit chains present a significant threat to organizations by enabling attackers to leverage multiple vulnerabilities to gain unauthorized access and cause extensive damage.
Understanding and defending against such cyberattacks is critical for maintaining your security. By prioritizing proactive vulnerability management, implementing defense-in-depth strategies, and leveraging advanced security solutions, organizations can mitigate the risks associated with exploit chains.
Enhance your organization’s security posture with SOCRadar. By improving patch management and delivering real-time alerts on security threats, SOCRadar ensures that you stay ahead of potential issues.
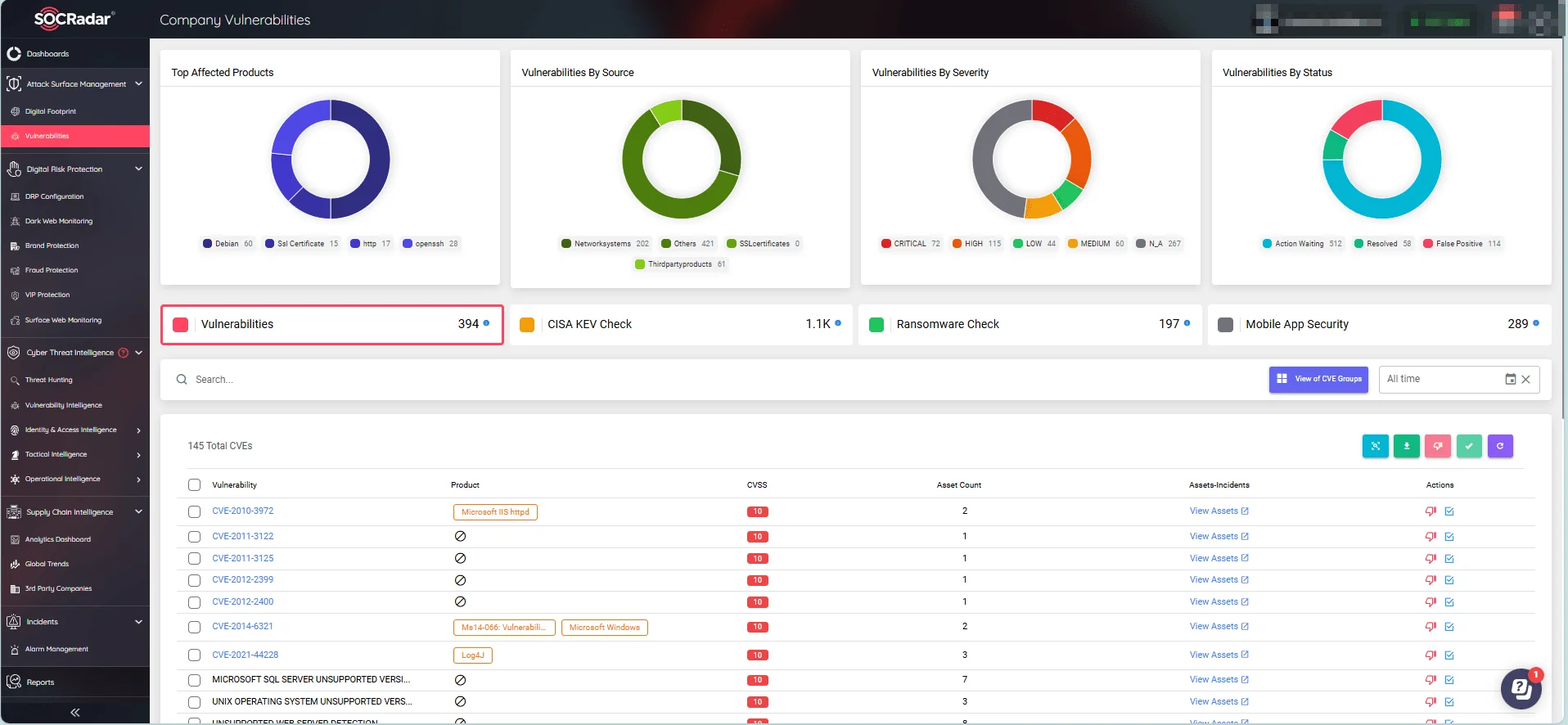
Monitor Company Vulnerabilities with SOCRadar’s Attack Surface Management
The platform also simplifies the monitoring of digital assets, tracks threat actors, and provides essential security insights, making threat management rather easy and more effective.
Article Link: Exploit Chain: When One Vulnerability Isn't Enough - SOCRadar® Cyber Intelligence Inc.


