Detecting advanced in-memory threats is critical for security teams — read on about how Intezer’s Endpoint Scanner ensures your team can quickly identify and analyze fileless threats, packed malware, malicious code injections, or any unrecognized code.
At Intezer, we are constantly working to improve our products and provide our customers with the best threat detection and response capabilities. Our Endpoint Scanner is a powerful forensics tool for detecting advanced in-memory threats on Windows operating systems, including identifying malicious code injections, packed and fileless malware, or any unrecognized code.
Today, we are excited to announce the release of new features for our Endpoint Scanner, which will make it even more powerful and effective in detecting and responding to advanced in-memory threats. These features include a redesigned user interface with search, sort, filter and pagination capabilities and a new Scheduled Tasks tab that provides information about all the registered scheduled tasks on an endpoint. It is available to try in our free 14-day trial or for accounts using our Autonomous SOC plan. As part of the Autonomous SOC plan, the Endpoint Scanner can be launched directly from your endpoint security platform (such as CrowdStrike, SentinelOne, or Microsoft Defender).
Simplifying Endpoint Forensics for Incident Response
Endpoint forensics can be complicated and beyond the skills of Tier 1 SOC analysis. Simplifying this complicated process means that endpoint forensics and memory analysis can be used as part of an automated alert triage process. Enabling teams to easily and automatically leverage deep forensic analysis makes it accessible to use at the point of initial triage for every alert (without taking significant time or any advanced skills). This best practice of using memory analysis results for triaging alerts gives teams confidence an assessment is correct, and allows them to quickly identify and classify advanced in-memory threats. Teams can also run a scan at scale across their organization’s endpoints, detecting lateral movement to additional machines or proactively hunt for compromised endpoints.
What’s New: A Fresh Look and Even More Context for Investigations
One of the most significant new features is the redesigned user interface (UI) for improved navigation and investigation experience. The new UI includes a table view for files and memory dumps collected from the endpoint, with pagination for analyses with many files, making it easier for you to view and navigate through the data. Additionally, search, sort, and filter capabilities have been added to help you quickly find and focus on specific files or data. With the redesigned UI, you can easily triage a suspected endpoint or proactively hunt for malware loaded to memory, providing a more efficient and effective way to detect and respond to advanced in-memory threats.
The new file details panel provides more comprehensive information about each file collected by the Endpoint Scanner and analyzed. This includes the file analysis summary and link to full analysis, file properties such as sha256, md5, and other hashes, process tree, and file paths where the file was found on disk. Additionally, the creation time of each file is displayed, which provides more context on the timeline of the attack. The download URL, if available, is also displayed, which can help you identify where the malware came from.
 Showing the redesigned UI with the file details panel expended.
Showing the redesigned UI with the file details panel expended.
Another new feature is the Scheduled Tasks tab, which provides information about all the registered scheduled tasks on an endpoint. This new capability in the Endpoint Scanner allows you to find suspicious scheduled tasks that could have been registered by an attacker to achieve persistence. The Scheduled Tasks tab includes a table view that displays information about each task, such as the task name, state, author, registration time, last run time, next run time and action. The Scheduled Task Details panel provides additional info, including location, description, whether the task is hidden, and the executing user/group. You can search, sort, and filter the tasks to quickly find and focus on specific tasks that may be suspicious.
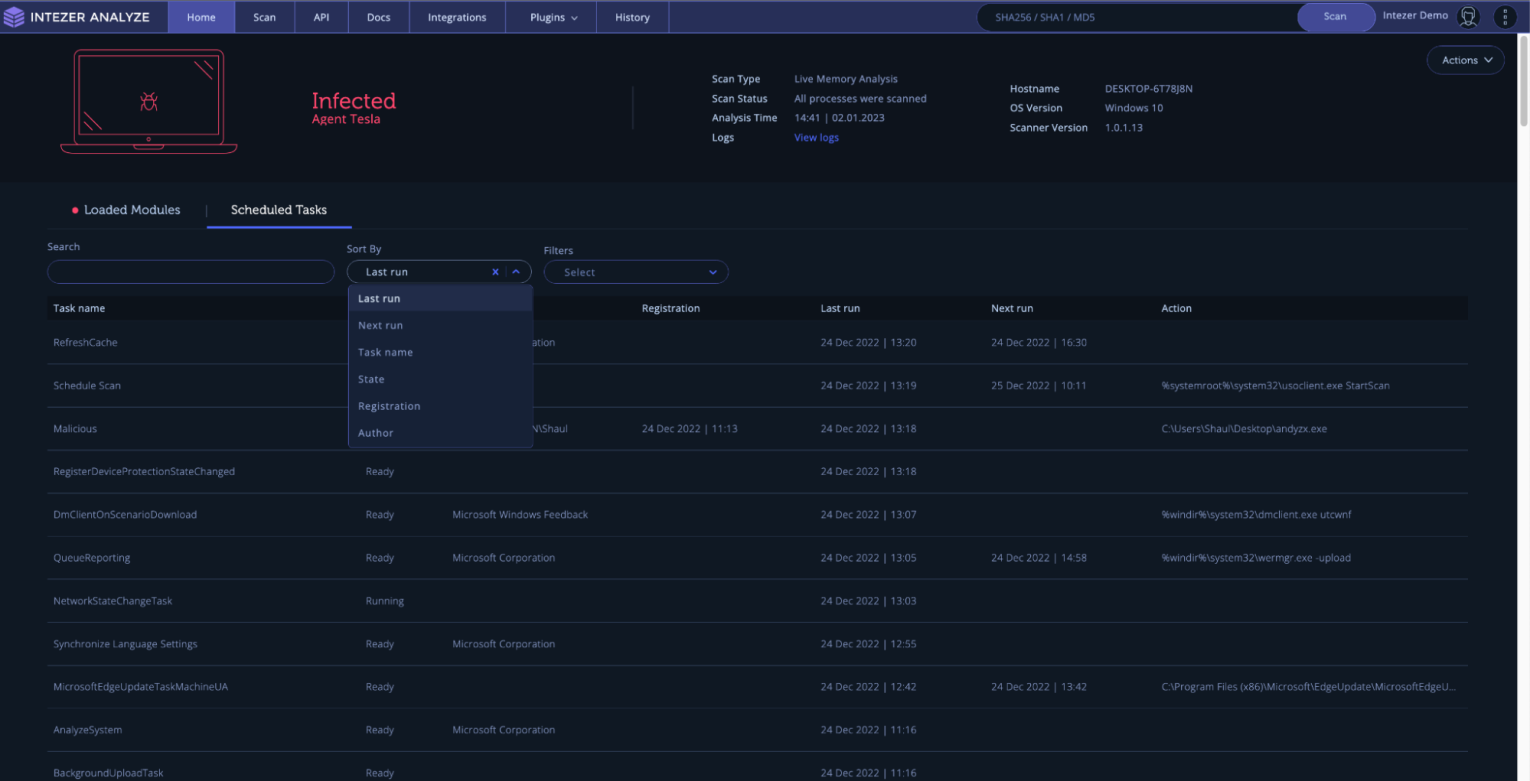 Showing the endpoint analysis scheduled tasks tab, highlighting the sorting options.
Showing the endpoint analysis scheduled tasks tab, highlighting the sorting options.
Get Started Using the Updated Endpoint Scanner
To get the latest version of our endpoint scanner, ensure that you download the scanner from the Endpoint Scanner page. It’s important to note that the Scheduled Tasks feature is supported only when using the scanner version v1.0.1.12 and above.
As always, we encourage our customers to update to the latest version of our products to ensure they have the latest capabilities and protection. For more detailed information on how to use the new features and capabilities of the Endpoint Scanner, please refer to our documentation on live endpoint analysis. There you’ll find step-by-step instructions, usage tips, and troubleshooting advice. If you have any questions or feedback, please reach out to our support team.
Not a customer yet? The Endpoint Scanner is available in our free 14-day trial for our Autonomous SOC plan. To get a demo, reach to talk with us about how this could help your security team
The post Endpoint Forensics and Memory Analysis, Simplified appeared first on Intezer.
Article Link: Endpoint Forensics and Memory Analysis, Simplified