Read about insights on real malware and spam campaigns based in the testimony of a victim and a threat actor!
 This post is sponsored by Malcore.io
This post is sponsored by Malcore.ioThreat actors need to innovate in order to keep business going on, and these operations can’t be hidden because people need to be fooled into clicking that link that would download something suspicious or get us into a suspicious page. If a victim can reach the malicious content, we can also reach it!
The main source from where I get this malicious content is social platforms such as Youtube or GitHub.
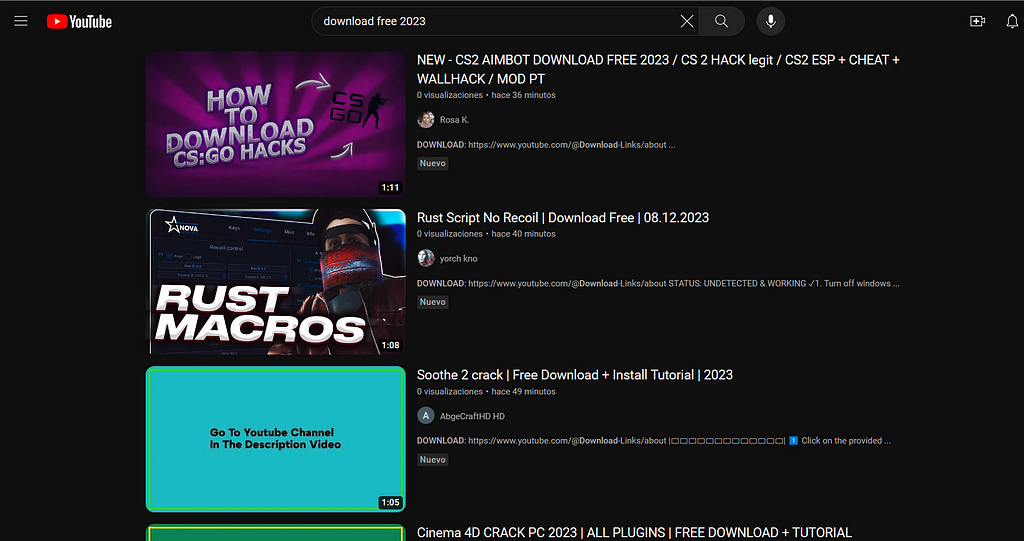
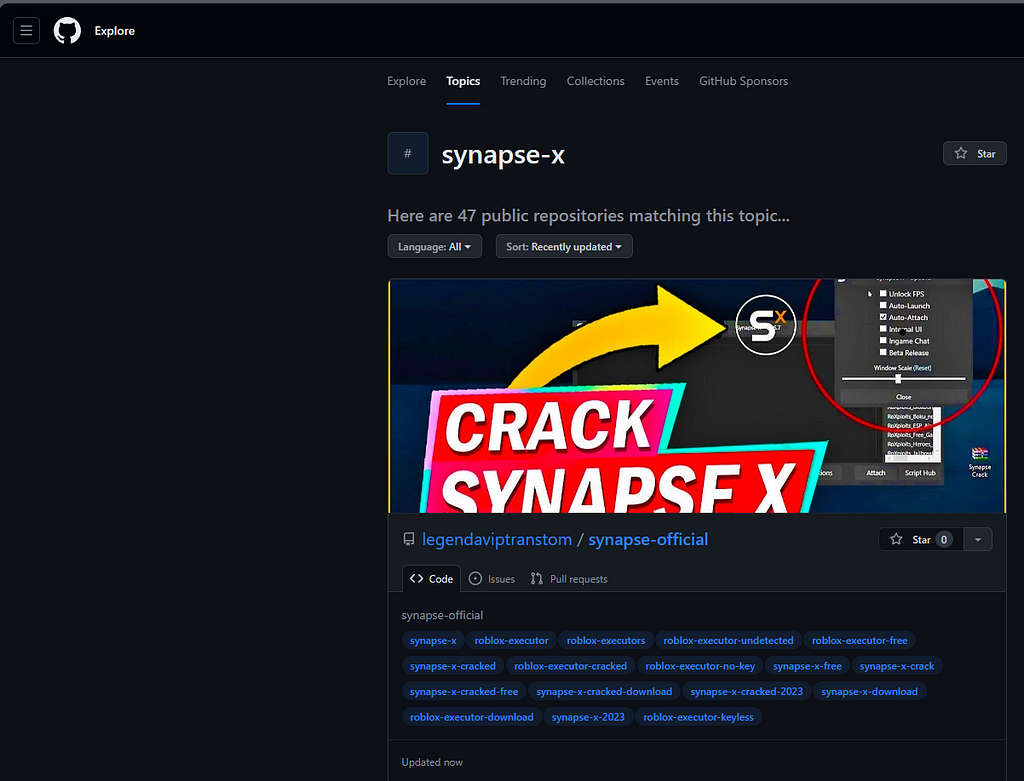
From what I observed, these platforms are mostly used by individual threat actors, who work for themselves or on a team.
But there is another source of malicious threats (even bigger) disguised as fake software downloads or game cracks, and being spread on domains, available to every one of us as easy as a Google search.
Introduction
While hunting for malware on GitHub, I noticed an unusual amount of compromised accounts serving malicious repos with links leading to malware downloads.
And I’m not talking about accounts with no activity, more likely accounts from real people (from university students to PhD teachers) with their own old repositories and newly created ones with malicious content. So I decided to contact both victims and threat actors using these accounts.
I’m just providing one example of each one
Side A: Threat Actors
Alledgelly known as “Stevie”, this guy was serving a website (softonixx[.]com) of fake game cheats, that in fact, were Lumma Stealer builds:
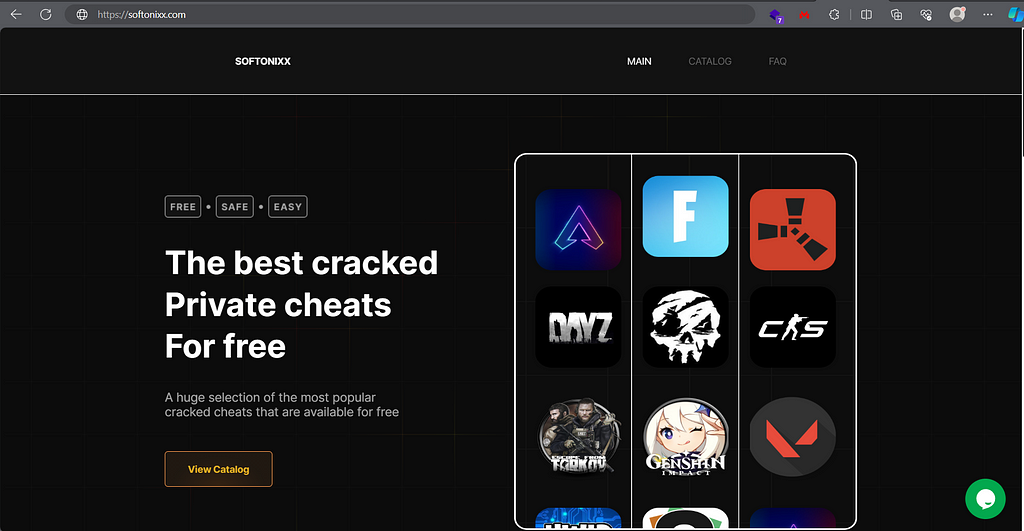
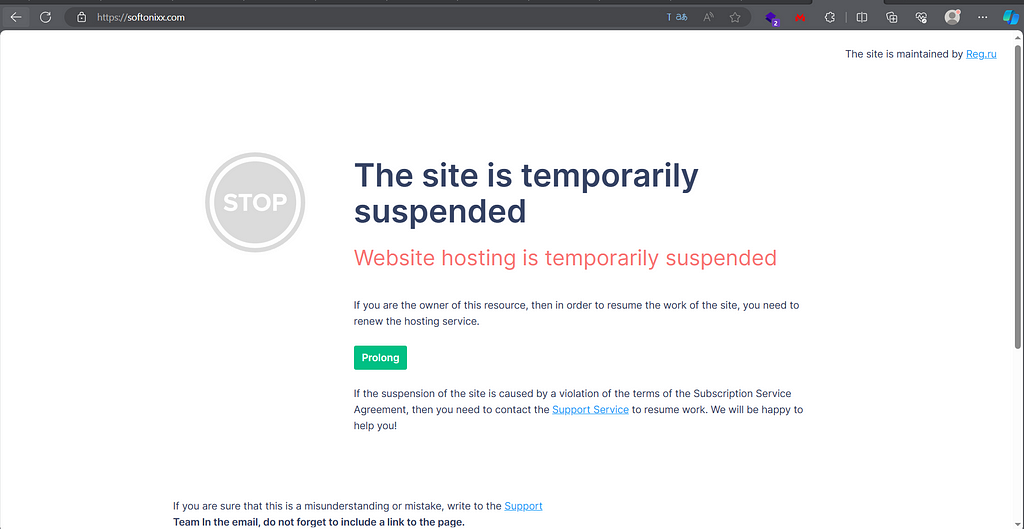 Before & After
Before & AfterWith the help of Malcore, we can know more about this domain:
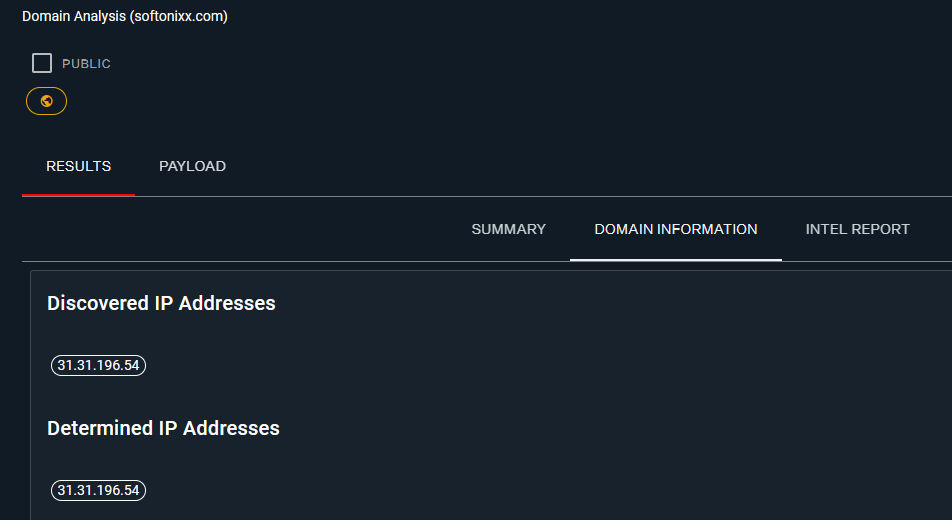
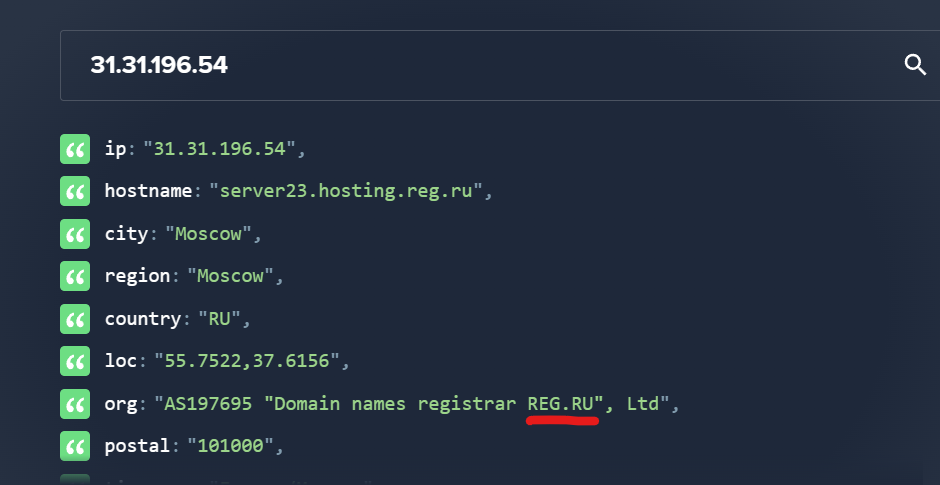
So I could report this abusive domain to the hosting :)
Detonation: Analysis https://cutt.ly/RwRNEzWo Malicious activity — Interactive analysis ANY.RUN
Lumma ID: HPJGYy — Stevie
This guy provided his website with a tawk.to module in order to talk with people visiting his site, and I had a little talk with him:
Welcome to our site, if you need help simply reply to this message, we are online and ready to help.
g0njxa: **** you
stevie: thank you
[...]
stevie: lol
you know how many ppl you can find
only i am on the github
with website + support page
g0njxa: yes i know
others using redline and meta
stevie: yes
for me lumma is better
[...]
g0njxa: you know how much people are doing this?
stevie: a lot
g0njxa: you are just one more
man you are getting money but people are suffering from this
stevie: ;c
g0njxa: malware is not good
stevie: the whole world are doing this
g0njxa: maybe where you are
not everyone
stevie: if not me that will do anybody else
no i mean the whole world doesnt care about other ppl
so why should i care
g0njxa: I do
stevie: if you are smart then dont download it
thats why I do this
stevie: if you are fuckign brain dead
g0njxa: this is not personal man
stevie: bro you know what
who downloads cheats and cracks
g0njxa: is not about you is the thing
stevie: are hurting other feelings
other humans
by doing this
maybe its karma?
g0njxa: lmao
do you thing karma is a thing??
stevie: no i mean
he gets what he needs
he download cheat
he got hacked
g0njxa: fake cheats
stevie: but if he wants to dwnload cheats
then hes about to hurt other
ppl
or even cracks
g0njxa: man how can I hurt someone cheating on fortnite
stevie: BRO play normally
g0njxa: tell me
stevie: somebody can cry because you killed him
g0njxa: is the same to steal money from a bank account than to cheat on a game?
stevie: if you are good person
you are not gonna download
cheat or crack
g0njxa: i used to download cheats
in the past
when I was young
stevie: then you are not a good person
somebody can suffer bcuz you downloaded cheat
and played not fair against them
g0njxa: you consider yourself a good person?
stevie: nah
i consider myself a karma for those who try to download cheats or cracks
but maybe im even the worse
[...]
g0njxa: i mean what you can get 1k logs?
stevie: nah
g0njxa: less
stevie: maybe 75 today
only
85
i have problem with github accounts rn
g0njxa: so every day people are getting thousands of logs
stevie: yes ik
g0njxa: 75 is just nothing
[...]
g0njxa: lmao
how is sales
of logs
stevie: wdym
g0njxa: is market good now or bad?
stevie: im just giving them to differnet pep
who uses them to get money
like banks , game
then they pay me
g0njxa: have you tried lolz market
stevie: yeah
everybody who does this job
knows lolz
[...]
g0njxa: i just wanted to know from where you were connecting
stevie: if i know lzt market
then you know where im from
g0njxa: CIS
stevie: :)
g0njxa: xaxax
is just everything is there man
stevie: yeah
g0njxa: protect the motherland and the motherland will protect you rigth?
stevie: nah
only dumb ussr pep have that in mind
g0njxa: so you worked on CIS huh?
stevie: a few times
g0njxa: friendly fire
stevie: xd
you know about conflict
some of malwares
are not allowing to install from cis
[...]
g0njxa: i can use translator
i mean why to put a chat on your website
stevie: bcuz i crypto streamed before
and it was fun
to add chat ther
g0njxa: man you are infecting childs, thats not what a grow up man will do
stevie: bruuuuhh
come on
g0njxa: you are not 15
stevie: im not gonna stop bcuz
im hurting somebody`s feeling
g0njxa: imagine you got a child
and you bank account gets drained bcuz your child got infected
stevie: i mean thats life
he will learn a lesson
and never will do that
g0njxa: but is your money
u know what i mean
stevie: yeah i get it
i wouldve fuckign kill him
g0njxa: dumb
stevie: just kididng
im not such evil
[...]
g0njxa: are you testing things or just lumma
stevie: tested a lot
meta
redline
now lumma
i share with my dude
payed him 125$
g0njxa: for a lumma panel
stevie: yeah it costs 250 per month
g0njxa: oh okay
split
stevie: yeah
[...]
stevie: you are not gonna do anything by tracking pep
you know that
its internet
thats not how it works
come on man
especially in cis
g0njxa: well you broke 1st rule
working on cis
stevie: hahaha
thats right
but its not gonna happen
nobody got arrested for doing that
you cant track all that
g0njxa: specially if you are not inside russia
stevie: thats the proble mman
other countries are more fucked
stevie: bcuz of that war
its much harder to find
[...]
g0njxa: at least this malware campaign is more elaborate
where do you get the templates
this is new to me
stevie: made by myself
everything
yeah really hard to work
g0njxa: because some people sometimes buy crap
stevie: ALL PEPS FROM GITHUB
ARE USING MY TEMPLATES
70% of scammers in github
are really dumb
g0njxa: i mean sometimes is just downlad here
and a link
stevie: YES
AHHAHAHAH
g0njxa: why to spend that money on a website
stevie: bcuz actually
i can update my malware
with newer malware
i mean crypted file
g0njxa: yh i know
stevie: then its just beatiful
its not DOWNLOAD HERE
everytime i try to do something more original than others
i have two websites
g0njxa: bulletproof hosting
stevie: i bought from one guy
then russian one hosting
[...]
stevie: microsoft defender are
such an nightmare
for us peple
and google are blocking every link or every malware thing
g0njxa: thats why people put a .txt saying to put off defender
think smarter
stevie: bcuz they are cheap fucks
who doesnt want to pay
25$ for crypt
gimme your telegram if you want to speak more
cuz im really busy rn
Opinions are on your own.
We ended up talking further on Telegram. At the time of seeing his username, he was part of the “Raven Logs” Team, in which he confessed to work in the past. Also he confessed to be getting his GitHub accounts on the channel: ”https://t.me/LOGSfreecloud”, parsing the cookies from these public logs and using an automatic uploader tool to create malicious repos on compromised Github accounts.
Side B: Victims
GitHub user “AlfredGarciaa” got his account compromised by an unkown threat actor (not by the guy above), and was being used to share Redline Stealer by user https://t.me/Oleheskevich
Detonation: Analysis https://707.su/Exloader Malicious activity — Interactive analysis ANY.RUN
C2 Redline: 91.103.252.48:33597
I contacted this compromised user using the contact methods he was providing in his account. As usual, his account was reported because he was sharing malware, and I got it suspended after some days. He replied to me late and he wasn’t aware of this issue, so he deleted the malicious repos although the account was already reported.
I archived a copy of his account on The Internet Wayback Machine, so you can look how his account looked while was compromised:
AlfredGarciaa (Nightwing) · GitHub (archive.org)
When I asked to him how he though he was compromised, he told me he downloaded “a game from a Mega link shown on a website and, when he executed it, the AV was triggered and he rebooted his PC”. Ineed malware.
The website is blizzboygames.net
It somehow seems like a “legit” site, in terms of that is providing real game cracks BUT under a weird and massive amount of ads, link shorteners and fake download buttons that are leading to an endless malvertising and deadly spam.
Let’s dive into this.
Fooling the eye
With the help of Malcore, we can gain some insights into this domain.
Malcore - Simple File Analysis
Although we can see that this domain is protected by Cloudflare, we can see some interesting historical NSGlue records:
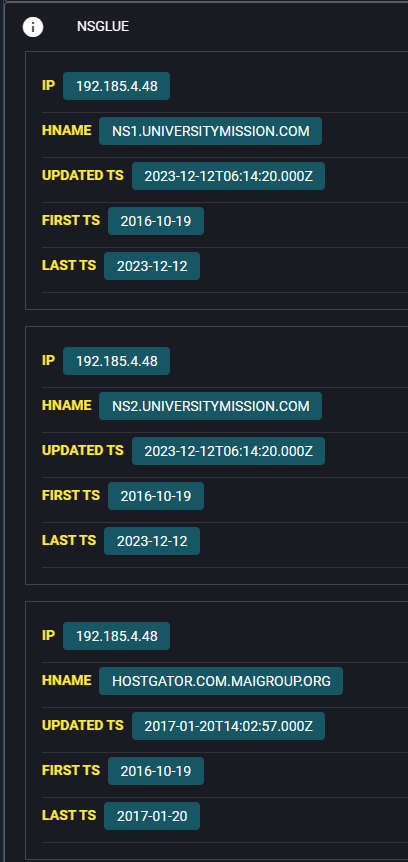
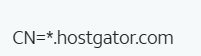 Certificate Subject (universitymission.com) — hostgator.com
Certificate Subject (universitymission.com) — hostgator.comRelated to Hostgator, not a bulletproof host but a giant in hosting services, it is also a kind of abused host by threat actors related to phishing and malware, especially from the RU criminal side.
So we have this situation:
You want to play a PC game but paying for it is not an option, so you decide to look for a game crack over the Internet (bad choice)
You end up on a random page, and you look for your game. Pop-up ads start to appear while clicking links…
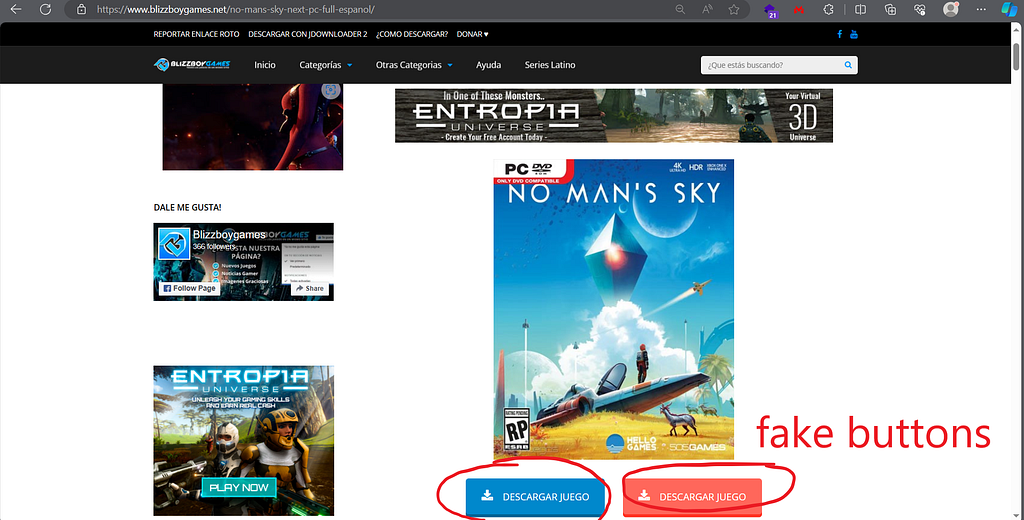
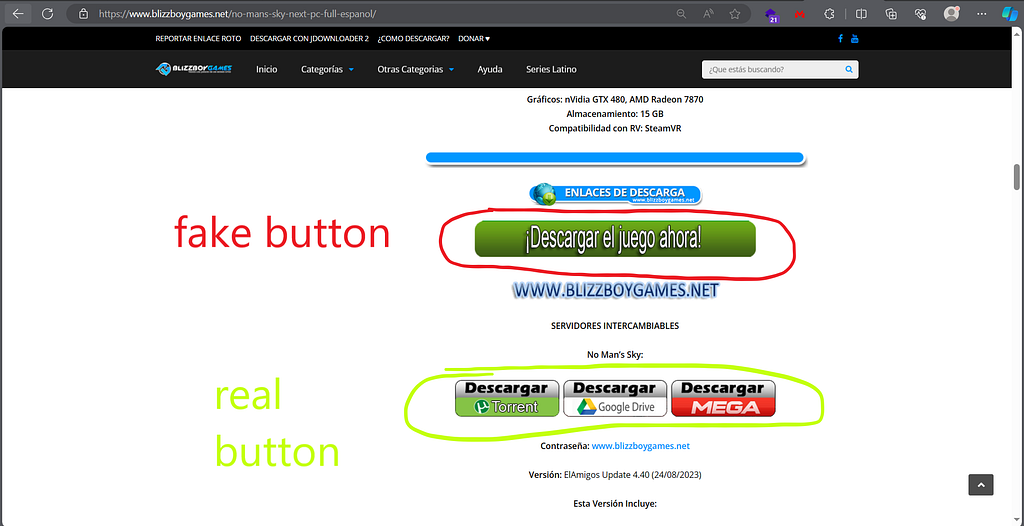
You skip some fake buttons leading to malware downloads, and the LAST button is the real one. Do you think you are safe? NO
You end up on a page like this:

And to successfully download what you were looking for, you need to skip a chain of 2–3 abusive shortener links with more pop-up ads, more malware downloads, and more spam…
What are the chances of getting a malicious download? HIGH, indeed
Please avoid suspicious downloads from the Internet, do things in the proper way to avoid unwanted situations.
You clicked the wrong link
Please note that random clicks on this website are being served with an additional pop-ad window by the ad service popads.net
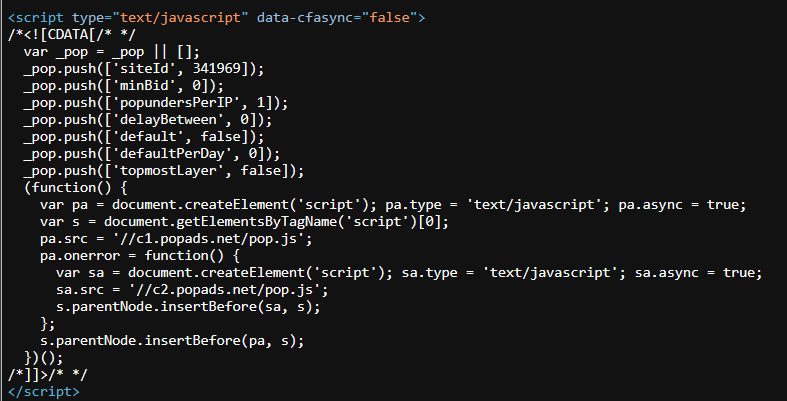
In this specific website, fake download buttons are redirecting the victim to a redirection chain started by a shortened service and managed by domain “onclickalgo.com”:
bit.ly >>>>> onclickalgo.com/jump/next.php
With the Intel report that Malcore provides us, we can see this domain is related to even more spam download sites, and what is specially interesting, it is seen at Browser History records from victims malware logs. So we can see that malware is present.
FYI, a “Log” is the packed information exfiltrated from an infected host by an infostealer malware.
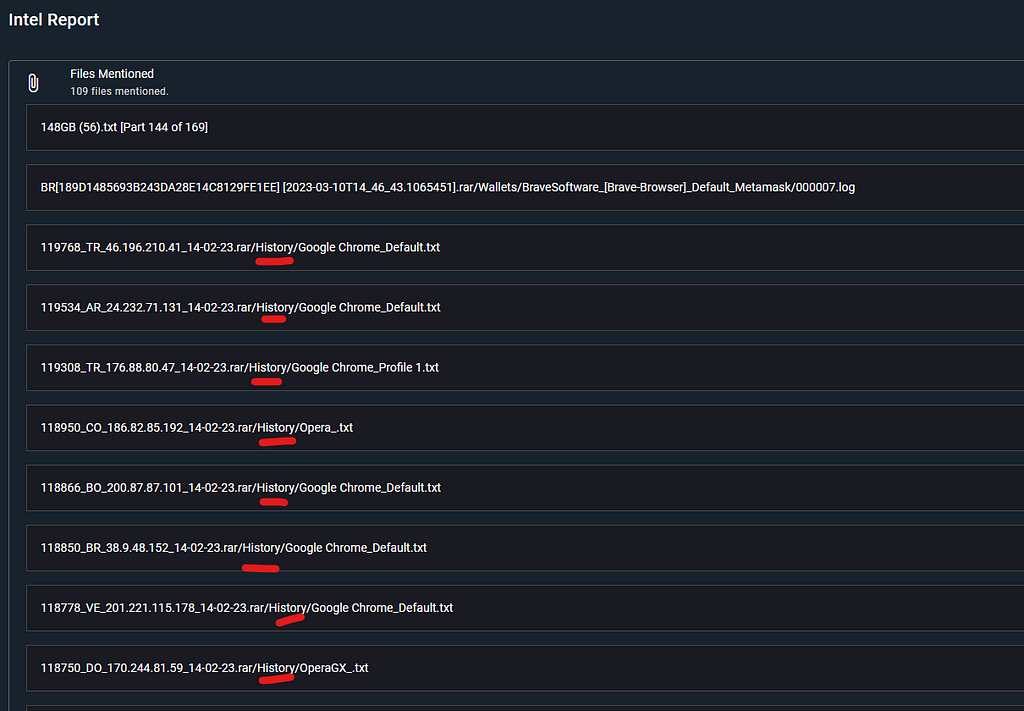
Check full analysis on:
Malcore - Simple File Analysis
This domain is checking on User-Agents and IP locations (in order to redirect traffic to the corresponding ad)
At first, I am using a common PC user-agent (Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/120.0.0.0 Safari/537.36 Edg/120.0.0.0) and IP will be set to some random VPN connection to an European country.
The first clicks on these fake buttons are distributing: PRIVATELOADER
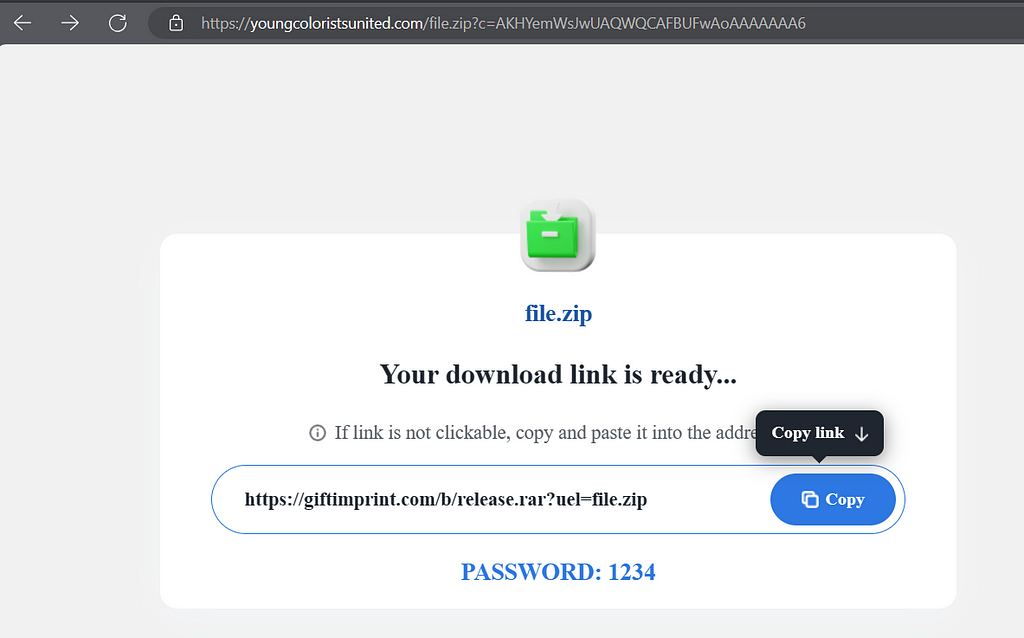
Privateloader is a malware that “loads” other malware families into the infected machine. If you want to see what Privateloader is capable of doing to your machine, please check:
With some days of observation, these domains serving Privateloader (where the download link is displayed) are changing in a weekly basis.
Getting some insigths on the domain with Malcore,
Malcore - Simple File Analysis
We can see Cloudflare is also protecting this domain and I can suspect this domain was parked in the past and someway is now used by these Threat Actors.
PrivateLoader campaigns often uses Mega to distribute its builds, so I strongly believe that’s what “AlfredGarciaa” downloaded.
And what happens with the next clicks?
If we continue triggering the ad redirection chain, we can go through a whole stack of spam.
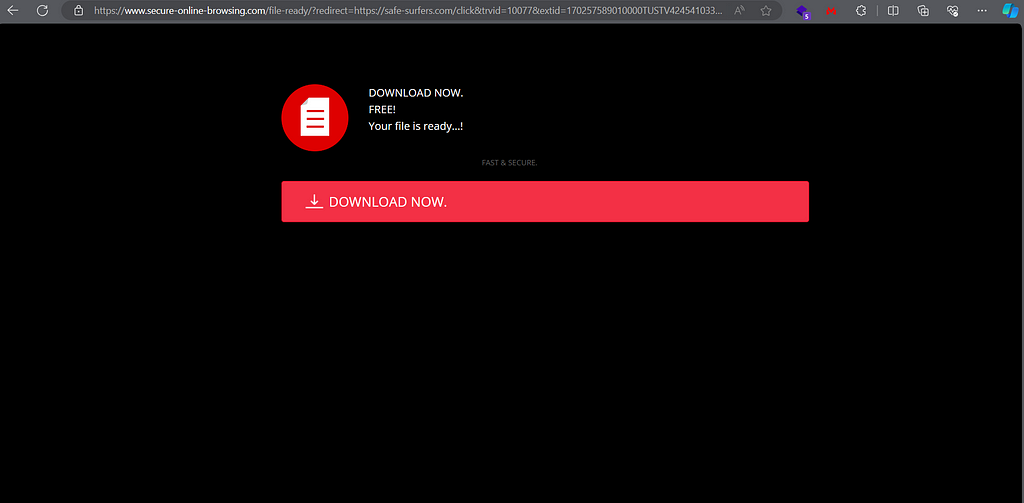
ADWARE
Some other downloads include some kind of adware or affiliate downloads from domains:
safe-surfers.com downloads from mediatrackerr.com
https://safe-surfers.com/click?trvid=10083&trvx=cab25468&extid=170257776210000TUKTV431200596654V13&cost=&campid=375459420&zoneid=6058394&lang=en&banid=23747924&form=1000
Detonation here:
Examples:
qBitTorrent
https://mediatrackerr.com/download?app=trnt&camp=100126058394
VLC media player
https://mediatrackerr.com/download?app=vlc&camp=100026058394
Domain secure-online-browsing.com provides us with downloads from the same site but another campaign
https://mediatrackerr.com/download?app=zipt&camp=10077
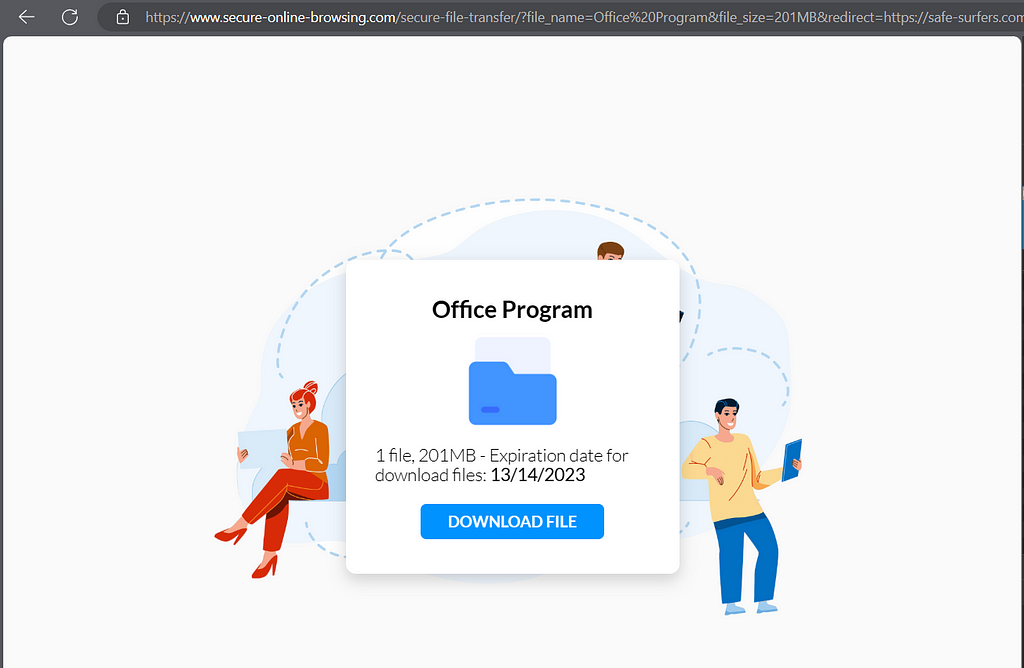
download4access.com provides us with geo-based downloads.
Blocked countries get the 7-zip client from the official site, but other countries (such as the tested, Mexico) gets a download from an Amazon Bucket:
https://s3.us-east-2.amazonaws.com/beverageynv/iftg180vxv/SetupFile_605351.html?utm_source=partner_consent
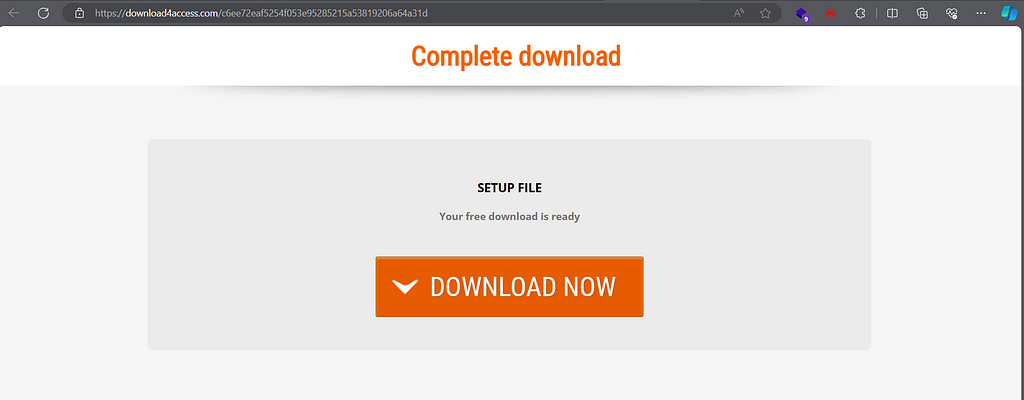
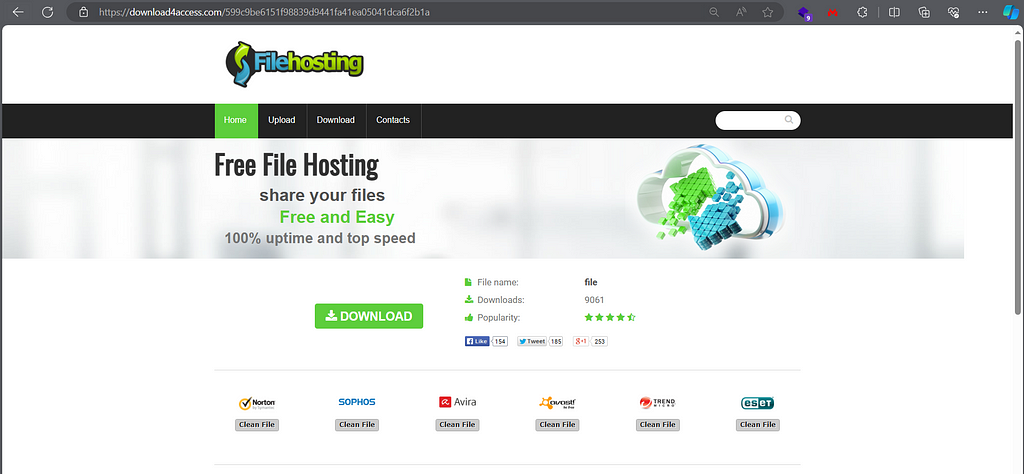
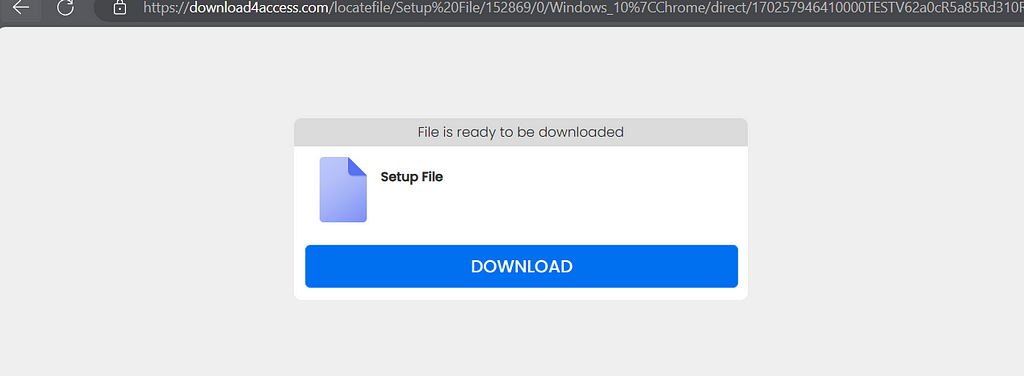
The detonation of the downloaded file can be found here:
It makes suspicious requests to globalinstallationfile.com and then downloads the same 7zip client.
Another way to use Malcore is on his Browser Extension (Malcore WebProbe (google.com)) that makes our Threat Hunting journey a lot easier.
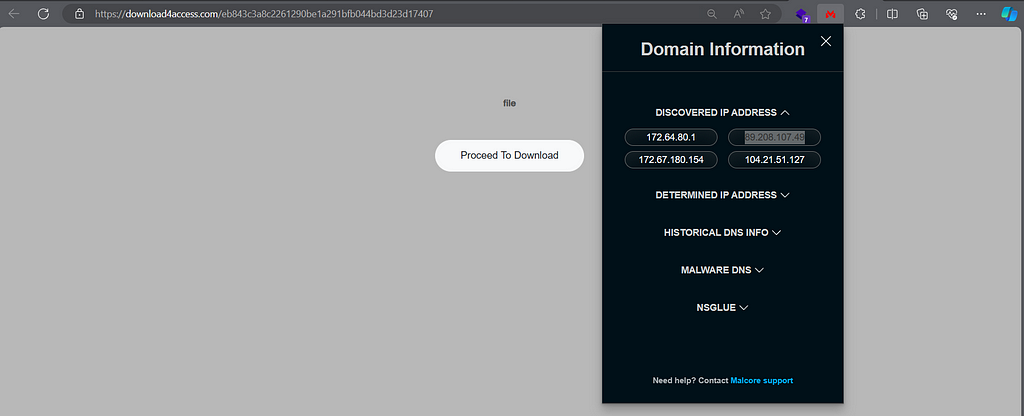
We see IP “89.208.107.49” contacting this domain, download4access.com.
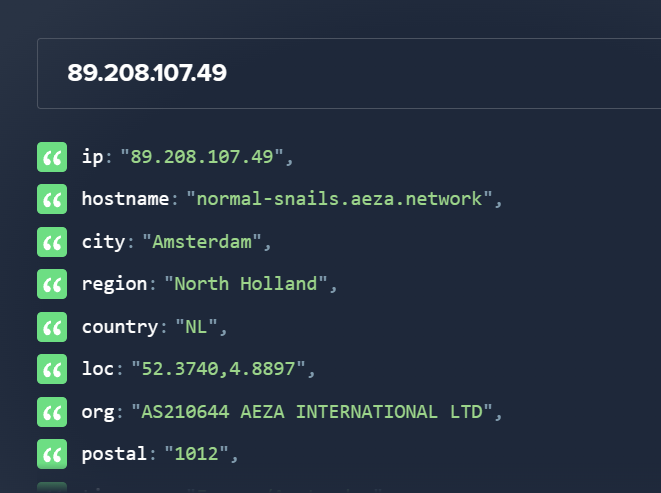
This IP belongs to AEZA, a Russian-based bulletproof hosting service provider and highly used by Threat Actors. Indeed, malicious domain.
ROBOT SPAM
There is a “Robot verification” spam (in order to send malicious notifications on user) that are redirected from affiliate traffic from tracking links like:
track.rankpeers.com/tracking.php
track.starmobmedia.com/tracking.php
tracking.prtrackings.com/click
Examples:
https://track.rankpeers.com/tracking.php?aff_id=10&offer_id=10&aff_sub=170257736410000TUKTV431200596654V23&aff_sub2=6058394
https://track.starmobmedia.com/tracking.php?aff_id=394&offer_id=1346928&aff_sub=170257761410000TUKTV431200596654V8e&aff_sub2=6058394
https://tracking.prtrackings.com/click?pid=4&offer_id=3946&sub1=170257806310000TUKTV431200596654V51&sub2=6058394
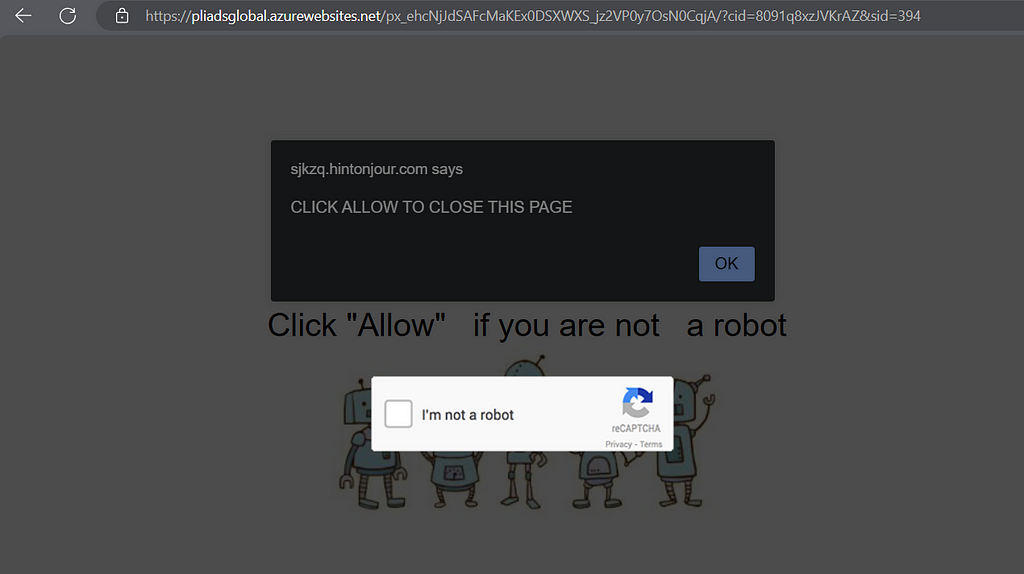
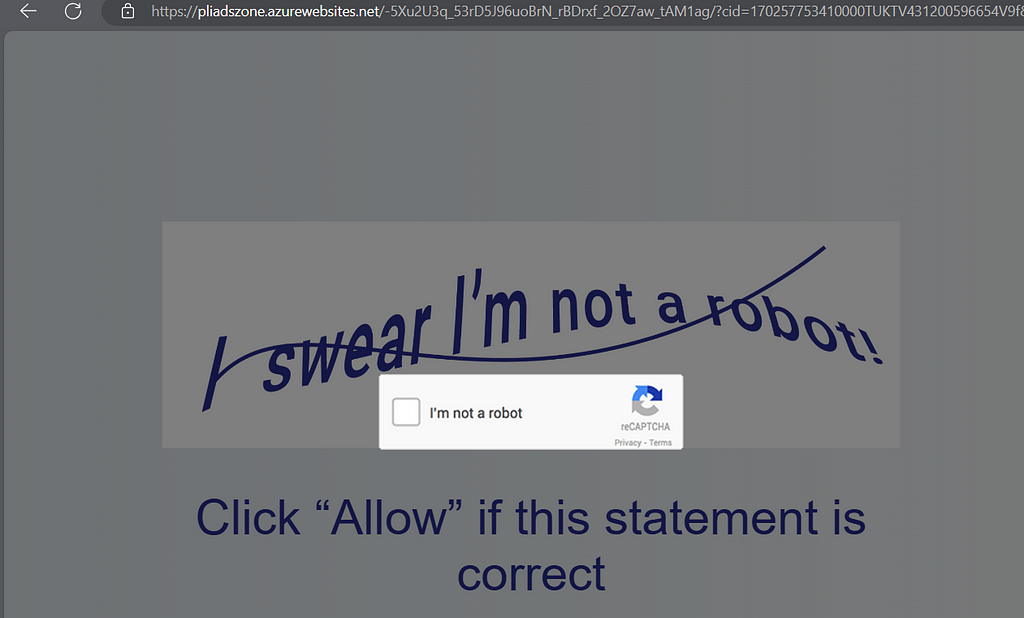
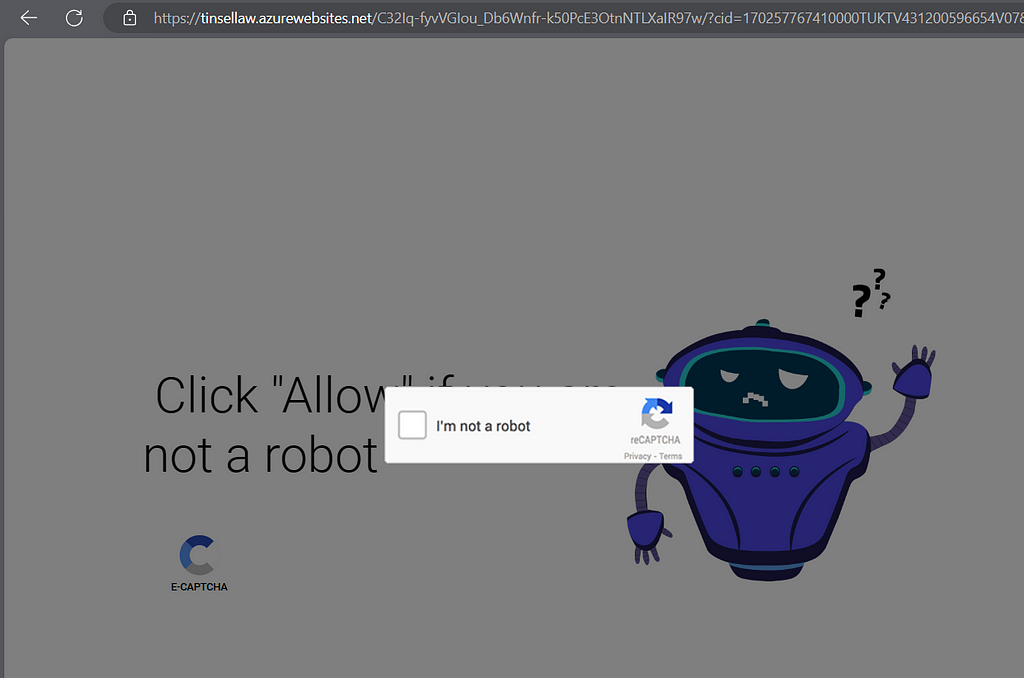
This “Robot Spam” are mainly based on Microsoft Azure websites such as:
oneanselllc.azurewebsites.net
tinsellaw.azurewebsites.net
pliadsglobal.azurewebsites.net
bestombudsblog.azurewebsites.net
platformnotice.azurewebsites.net
cretclub.azurewebsites.net
madssupport.azurewebsites.net
ekvadsstar.azurewebsites.net
madslive.azurewebsites.net
tvtadzone.azurewebsites.net
Also:
webregadvertising.com
realxavounow.com
glsfreeads.com
theamdads.com
kinitstar.com
ntmadz.com
This websites redirects to affiliate downloads on PUP applications after allowing notifications or a wait on the page. For example:
https://t.cn-rtb.com/aclk?u=https%3a%2f%2f22385d15-f9f7-4840-b62f-34022866157b.followthisredirectlink.site%2fdsp%2flink%2fredirect%3fssp%3d9dee120e-d78a-4a85-b799-78f0dfda9d9f%26hit%3d22385d15-f9f7-4840-b62f-34022866157b&l2=4FJd367u072qaklfZbnzUQO04zhDrYVOB1Y-3kIuKg_KKYT89zUbvFHCQToMBhkbnlQ2_CT-NGX9PxANqdDOAJWrEzQhbW3QWcNvDPWAcGBPkrZ0dKnLVHXT_tv_lbGkknkGWqbgZyBuaSJ71RjOI4XlL-O7XosvL76pFmnjJzv191Dc4EQIXKbDB2UNEFay
>>
https://22385d15-f9f7-4840-b62f-34022866157b.followthisredirectlink.site/dsp/link/redirect?ssp=9dee120e-d78a-4a85-b799-78f0dfda9d9f&hit=22385d15-f9f7-4840-b62f-34022866157b
>>
https://www.totalav.com/product/antivirus-pro
Domains cn-rtb.com and followthisredirectlink.site are being used
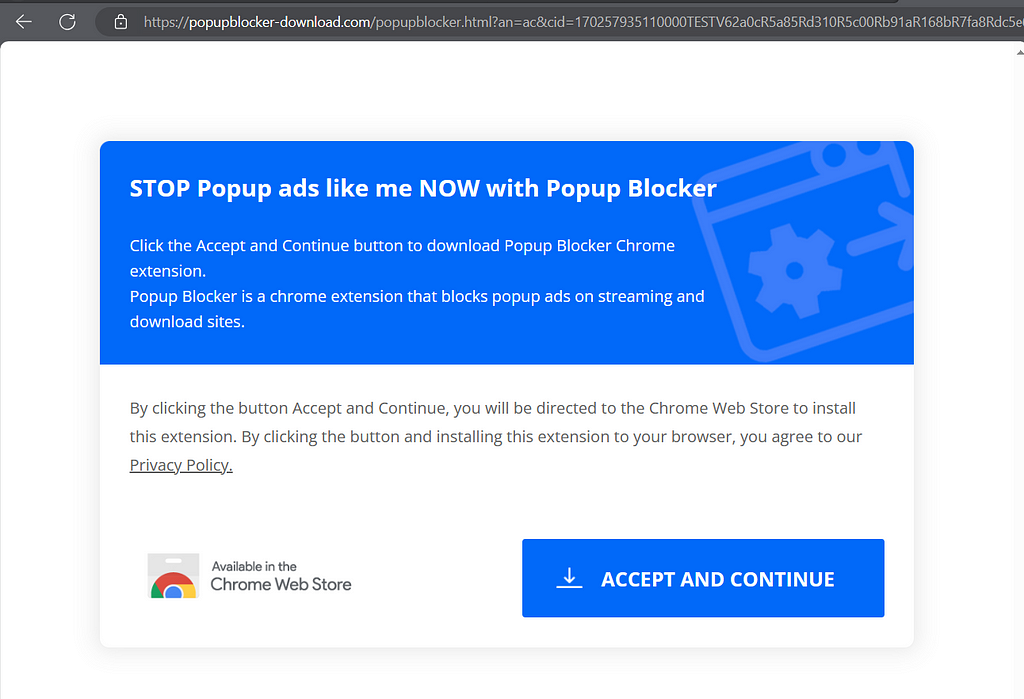
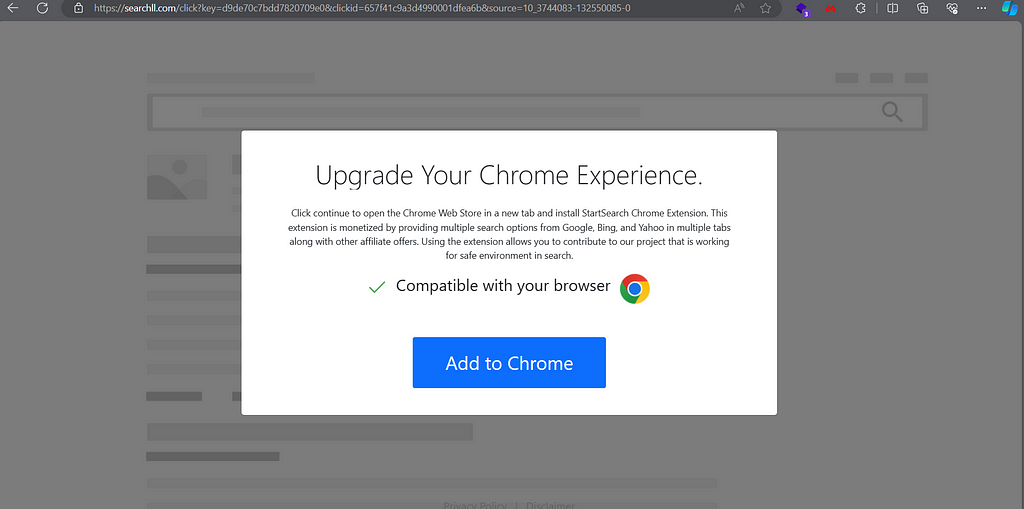
BROWSER EXTENSIONS
Playing with the User-Agent, we are redirected to Browser Extensions from very suspicious domains. It doesn’t means that the Browser Extensions are malicious, but more related to unwanted spam.
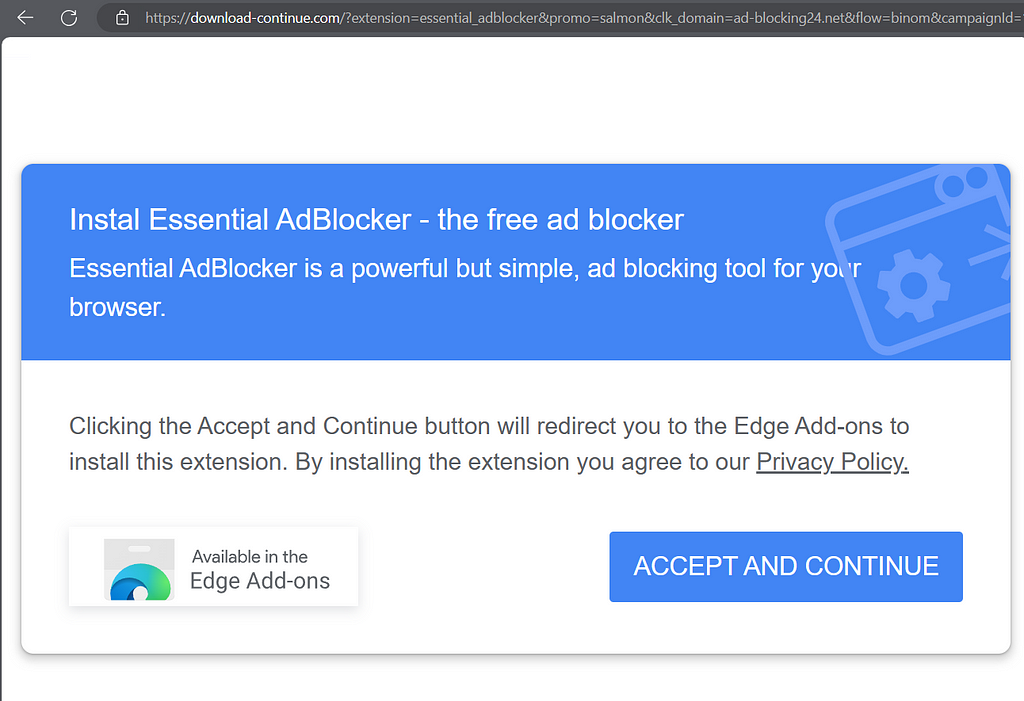
https://download-continue.com/?extension=essential_adblocker&promo=salmon&clk_domain=ad-blocking24.net&flow=binom&campaignId=10659&trafficsource=21&src=6_6058394&cid=7433bfnk29l8rwj47e&lpkey=170a0269575b866f91&uclick=fngh1ncidz&uclickhash=fngh1ncidz-fnk29l8rwj-syfe-0-usb7-ghb7-gh3z-57a58d
https://popupblocker-download.com/popupblocker.html?an=ac&cid=170257935110000TESTV62a0cR5a85Rd310R5c00Rb91aR168bR7fa8Rdc5e6V5c&sid=6058394#!
https://searchll.com/click?key=d9de70c7bdd7820709e0&clickid=657f41c9a3d4990001dfea6b&source=10_3744083-132550085-0
https://futureforgelabs.net/?extension=essential_adblocker&promo=salmon&clk_domain=ad-blocking24.net&flow=binom&campaignId=10659&trafficsource=21&src=6_6058394&cid=6e241fnwh9r52vrea5&lpkey=174502dc83c1947144&uclick=fnwh9r52vr&uclickhash=fnwh9r52vr-fnwh9r52vr-syfe-1mdz-us8w-ghj6-ghdv-0fd33e
Extensions offered:
https://microsoftedge.microsoft.com/addons/detail/essential-adblocker-ad/gfanbbhjiehkmcghbopnjjbbekkblplm
1 https://chromewebstore.google.com/detail/popup-blocker-bloquea-ven/dhemafmfialpibmahglbfgjihhfheepp/reviews
2 https://chromewebstore.google.com/detail/startnsearch/ianmmmlcnmakkffcgnoiocknagpejcfc?clickid=clvk3icvl93c73fj3mpg&source=
3 https://chromewebstore.google.com/detail/kryopage/idbdehpokikeobjcpgnleaaebmddflhi
With Malcore we can analyze Browser Extension (.crx) extracting interesting strings from the file and giving us a threat score based on suspicious permissions that the browser extension has.
For example:
extension (1) ~ Threat Score 26%
Malcore - Simple File Analysis
It can interact with the browser tabs or execute scripts. Must be activity related to the “pop-up” blocker functionality. We can also see from where this extension is getting the content:
Based on string:
https://popupsblocker.org/customrules.php?
>>
https://github.com/lepoulp/popup-blocking/
extension (3) ~ Threat Score 14%
Malcore - Simple File Analysis
It can query and modify cookies or modify network requests based on rules. Such activity indeed can be used for malicious purposes.
Also promoted as Fake Updates.
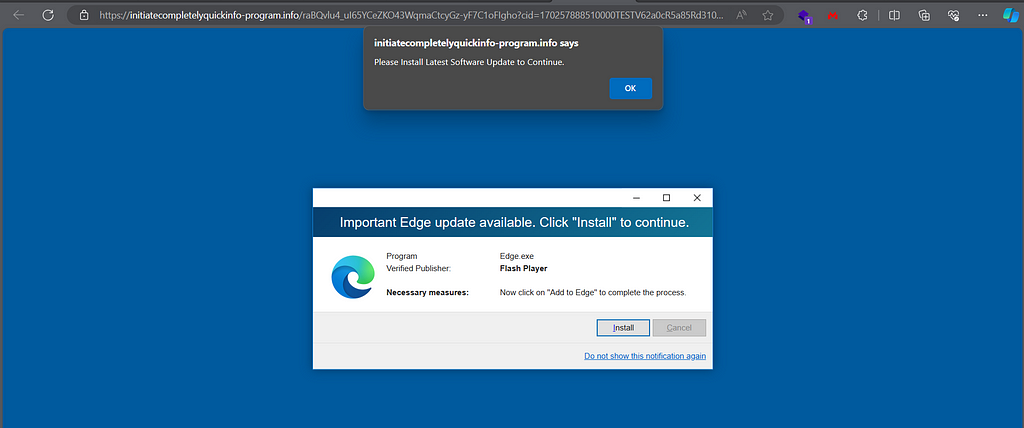
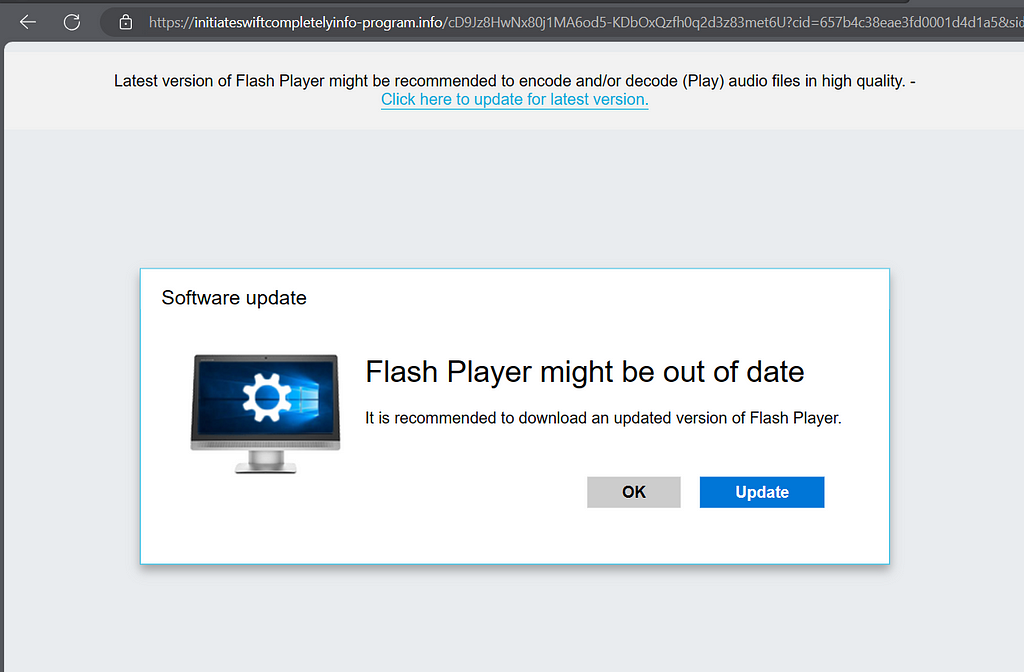
https://initiatecompletelyquickinfo-program.info/raBQvlu4_uI65YCeZKO43WqmaCtcyGz-yF7C1oFIgho?cid=170257888510000TESTV62a0cR5a85Rd310R5c00Rb91aR168bR7fa8Rdc5e6V11&pubid=6058394
https://initiateswiftcompletelyinfo-program.info/WvQqLADHXa6PYmHkbINESgOUPjOUqeab5y0ZBF6NNqY?cid=657f43acdbc1df000111c22b&sid=4_6058394
https://microsoftedge.microsoft.com/addons/detail/adsblocker-zero/pknhopblipiiggeknkacfnhncejnjaei
https://microsoftedge.microsoft.com/addons/detail/fastpix/mjfnppladcfbepmccgdmagmghpiiinoo
or more Robot Spam
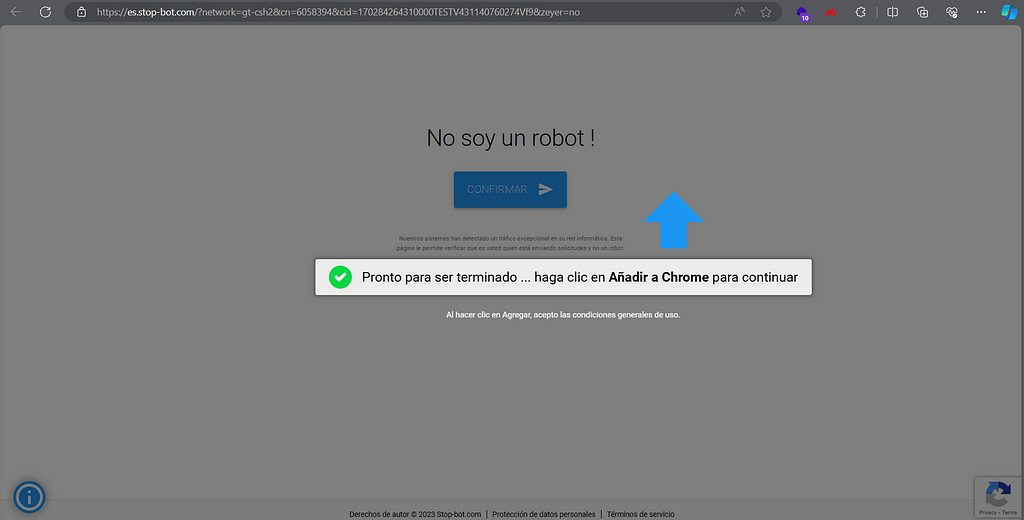
https://es.stop-bot.com/?network=gt-csh2&cn=6058394&cid=170284264310000TESTV431140760274Vf9&zeyer=no
Extension
https://chrome.google.com/webstore/detail/add-results/olkcmjmnlaepdbemdbbpgpkabemfpand/
Analysis:
Malcore - Simple File Analysis
We can see that this extension is modifying the Google search (on every google.* domain) and adding results from Accueil (hupzal.com). This behaviour must be considered malicious and can lead to more malvertising or spam.
AFFILIATE DOWNLOADS
Affiliate Networks represent such an income for this kind of Threat Actors generating traffic with this spam an ads:
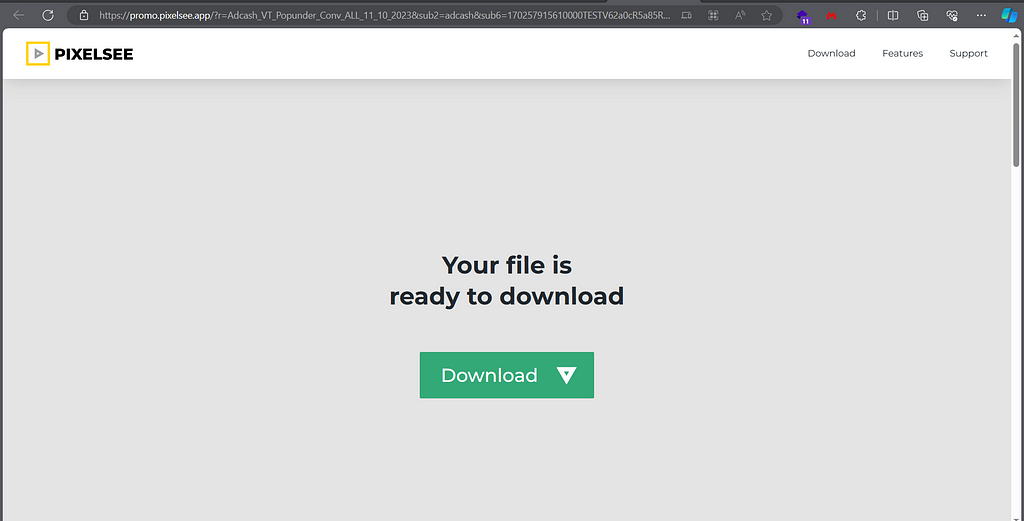
Some of these affiliate downloads pushed up on my investigations are the Opera Browser (not the first time I see this and highly abused on other platforms such as Youtube) or PixelSee
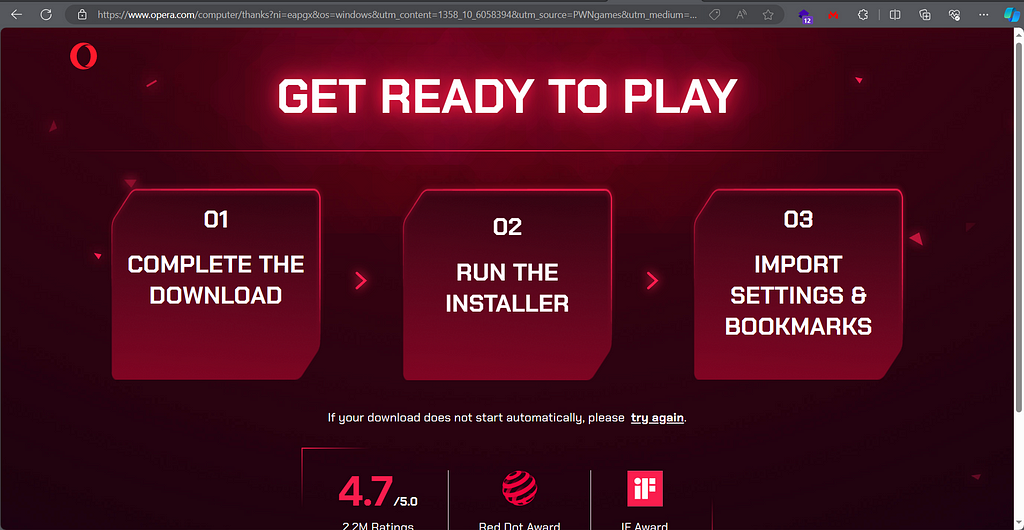
https://www.opera.com/computer/thanks?ni=eapgx&os=windows&utm_content=1358_10_6058394&utm_source=PWNgames&utm_medium=pa&utm_campaign=PWN_ES_HVR_WEB_1358&utm_id=696c8bdd49f64224990041c960802d13&edition=std-1
“PWNgames” is the affiliate ID on Opera browser downloads being promoted in this spam campaign. It should refer to pwngames.com:

Also “adcash” is the affiliate ID on Pixelsee downloads.
https://promo.pixelsee.app/?r=Adcash_VT_Popunder_Conv_ALL_11_10_2023&sub2=adcash&sub6=170257915610000TESTV62a0cR5a85Rd310R5c00Rb91aR168bR7fa8Rdc5e6V87
MORE AFFILIATE TRAFFIC BEING ABUSED
HBO MAX -> https://www.hbomax.com/affiliate
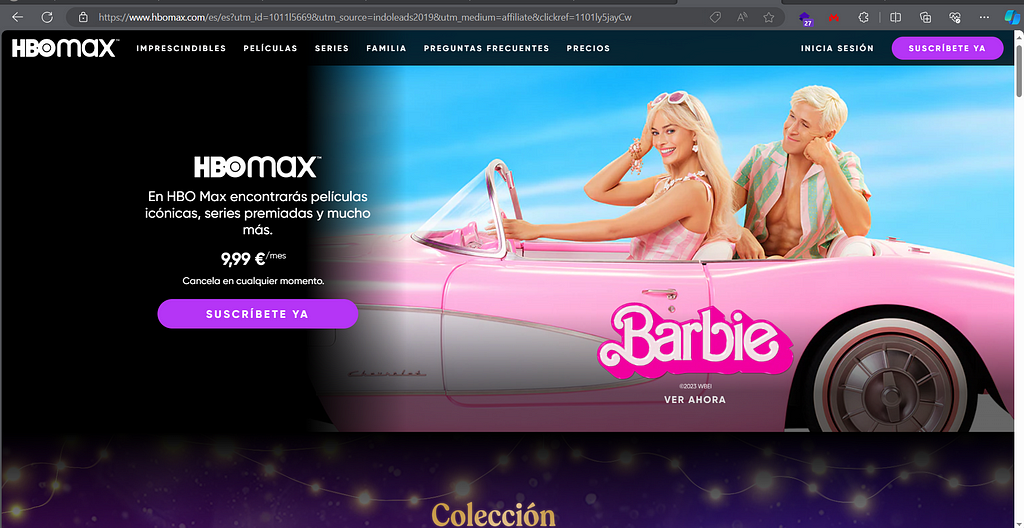
https://www.hbomax.com/es/es?utm_id=1011l5669&utm_source=indoleads2019&utm_medium=affiliate&clickref=1101ly5jayCw
The affiliate ID on this link is “indoleads2019”, and it would refer to indoleads.com, an Asian affiliate network.
Aliexpress -> AliExpress Affiliate Portals
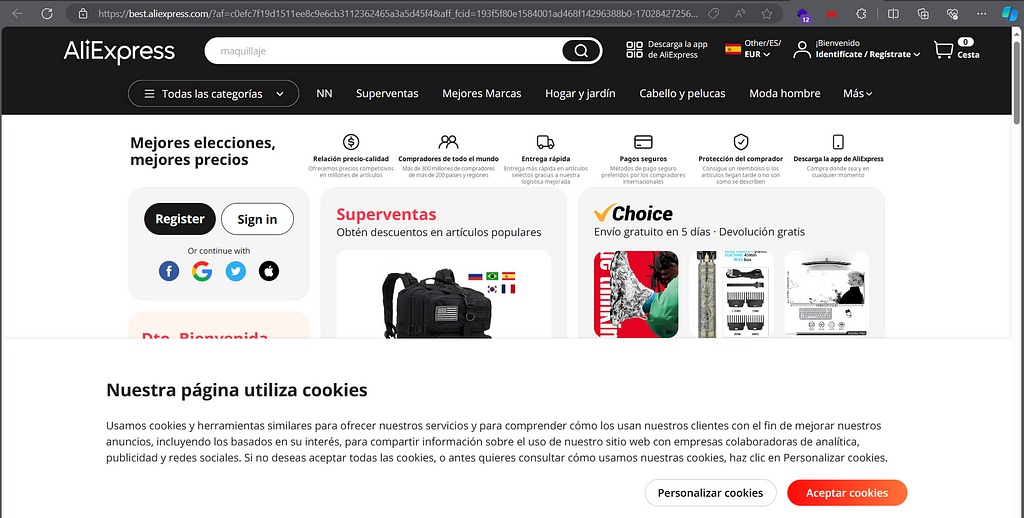
https://best.aliexpress.com/?af=c0efc7f19d1511ee8c9e6cb3112362465a3a5d45f4&aff_fcid=193f5f80e1584001ad468f14296388b0-1702842725632-08511-_DBsl7g3&tt=CPS_NORMAL&aff_fsk=_DBsl7g3&aff_platform=portals-tool&sk=_DBsl7g3&aff_trace_key=193f5f80e1584001ad468f14296388b0-1702842725632-08511-_DBsl7g3&terminal_id=67fb5517ed9e43feaf21add5b66404ad
Booking -> Affiliate Program by Booking.com — earn money on your website
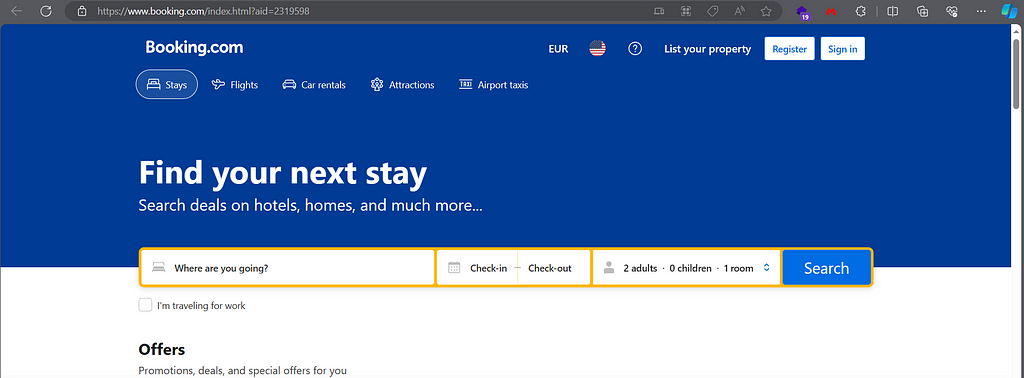
https://www.booking.com/index.html?aid=2319598
“ADCASH” FAKE CUPOUNS SPAM
Users are being redirected as more affiliate traffic to legit domains by this “Adcash” campaign promoting fake discount coupons.

https://coupons.oinde.com/?utm_source=Adcash&utm_medium=6058394_6058394
https://coupons.lifestylestip.com/?utm_source=Adcash&utm_medium=6058394_6058394
https://coupons.chonchon.in/?utm_source=Adcash&utm_medium=6058394_6058394
https://coupons.luxhotel.net/?utm_source=Adcash&utm_medium=6058394_6058394
https://coupons.tripdealsfinder.com/?utm_source=Adcash&utm_medium=6058394_6058394
https://coupons.alkhabri.com/?utm_source=Adcash-M-&utm_medium=6058394_6058394
At the time of writing this, no matter what “coupon” I clicked, I was being redirected to Bloomchic Affiliate Program-Make Money — BloomChic
https://bloomchic.com/?utm_source=admitad&utm_medium=affiliate&utm_content=1444969&bc_id=380001&tagtag_uid=85f6baa5ca5df338425fb45bf79c3566
How can I protect against these threats?
- Avoid unnecessary downloads on random websites on the Internet. There is no safe “free games” or “cracked software”, 99.999% of times you will be getting malware or ending up on a spam site.
- Always be skeptical about any suspiciously alarming notice or pop-up offers you receive.
- Never give permissions to any suspicious website or add extensions on your browser as request of these websites.
- Use common sense, for the sake of your privacy and the safety of the other users of the Internet. Your accounts can be used to compromise more people in an endless chain.
Best regards.
Article Link: Endless Malvertising & Deadly Spam: Threat hunting with Malcore! | by g0njxa | Medium