Gootkit is a banking malware that I started analyzing few days ago.
After unpacking some samples, I found some creepy loops and encrypted strings…
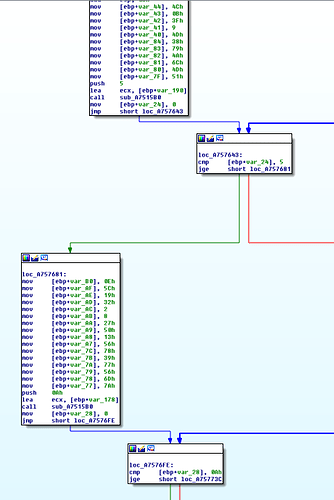
Image 1: Two encrypted strings.
For each string it uses, there is a loop to decrypt the string. After many samples analyzed (2 samples hahaha) I was bored with those loops. So I thought to write an script (my first radare2 script) to decrypt each string and comment my IDB.
Image 2: Many strings, many loops.
Finally, I have done a script (using radare2) which derypts/patches all strings and patches each loop. (because after the patch, the strings are decrypted, so it isn't necesary to continue decrypting the strings)
Lets analyze the encryption algorithm/loop.
In each loop there are two important values, one is the value for the control of the loop and the second one is the value which is used for dividing the counter of the loop (used as a module).
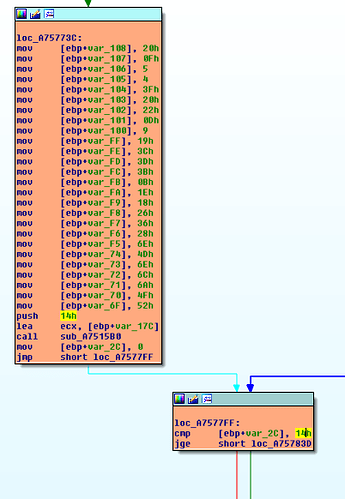
Image 3: The beginning of the loop to decryp a string.
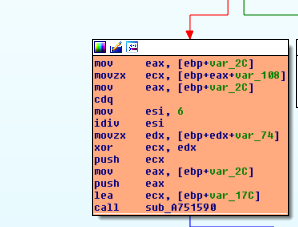
Image 4: The algorithm (XOR) to decryp a string.
Image 5: The code of the loop to decrypt a string.
In this loop that i will show as example, the value for ending the loop is 0x14 and the second value which is used for dividing the loop counter (as a module) is 0x6 (before idiv instruction).
After analyze this loop we notice that, the values of the the first 0x14 mov instructions are the characters of the encrypted string and the next 0x6 value are the characters of the key. The encryption algorithm is too easy, a simple xor between the string and the key.
Finally, after patching the program with the script, (and parsed de output for IDA comments) the result is the next one:
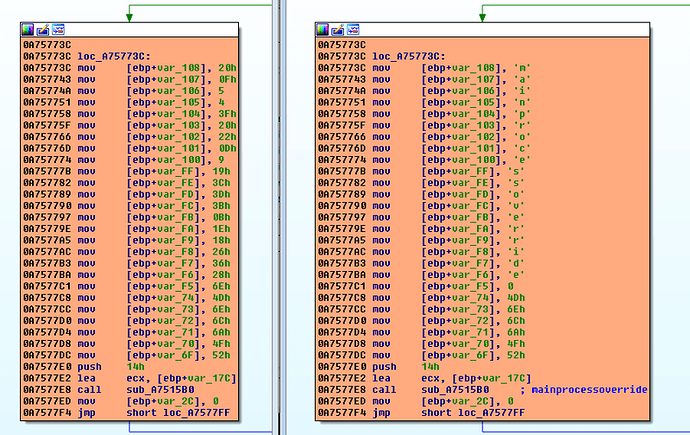
Image 6: In the left the original program with the encrypted string. In the right the patched program with the decrypted string and commented.
All strings are decrypted and a comment is added next to the string (And works without crashing =D)
The details of how it is implemented in radare2 are in the script.
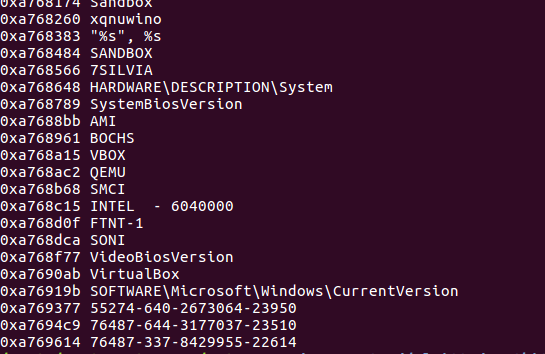
Image 7: The output of the program where you can see the decrypted strings and its offset.
Easy way.
Feel free for sending any suggestion.
Github (SCRIPT): gootkit_string_patcher
Author: @D00RT
Article Link: http://reversingminds-blog.logdown.com/posts/7369479