Author: Sunhyung Shim, Jaehak Oh | S2W Marketing
 Photo by Kajetan Sumila on Unsplash
Photo by Kajetan Sumila on Unsplash[Table of Contents]
- Darkweb Trend: Key incidents and trends in cybercrime for 2023
- Darkweb Statistics: Users, affected industries
- Targeting South Korea: Major incidents and Statistics
- Targeting North Korea: Major incidents and Statistics
#1. Darkweb Trend: Key incidents and trends in cybercrime for 2023
1. Hacktivists

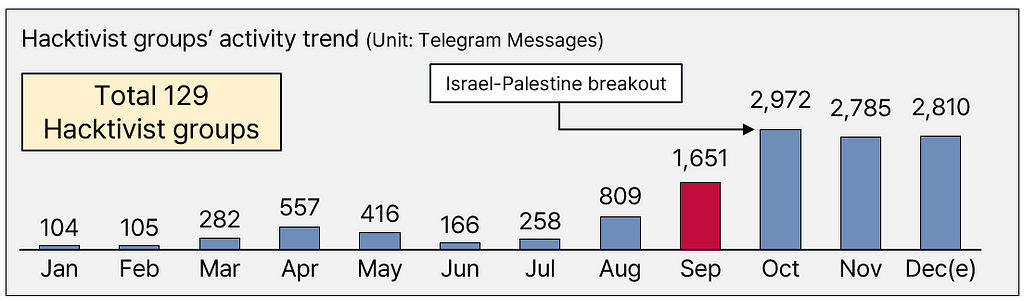
 Source: S2W Database
Source: S2W Database- Following the Russo-Ukrainian conflict, hacktivist groups have shown renewed vigor, especially during the Israel-Palestine conflict.
- Two key trends define them:
- Cyber Nationalism: This manifests as a West versus Russia & Arab League narrative based on domestic prioritization, nationalism, and factional logic. There’s a distinct hostility toward other cultural spheres, targeting any oppositional forces within their own nation.
- Telegram Channels: Predominantly operating on Telegram channels, these groups disseminate political messages and leak data. To promote these channels, they manage dual operation: Dark web and Telegram Channels.
- Targets include adversary nations like Russia-Ukraine and Israel-Iran, as well as peripheral supporters. Consequently, nations like South Korea and Japan are also impacted despite having limited direct association with the conflicts.
- When specifying target nations, they utilize hashtags like ‘#OP’ and ‘#FCK’ (e.g., OPBrazil, OPRussia), launching DDoS attacks or data breaches against governmental agencies or corporations of the target nations.
- Notably, their focus extends to critical national institutions and infrastructure. There have been instances where the operations of certain companies or institutions were paralyzed, leading to substantial societal costs.
[Distribution of targeted countries by hacktivist groups]
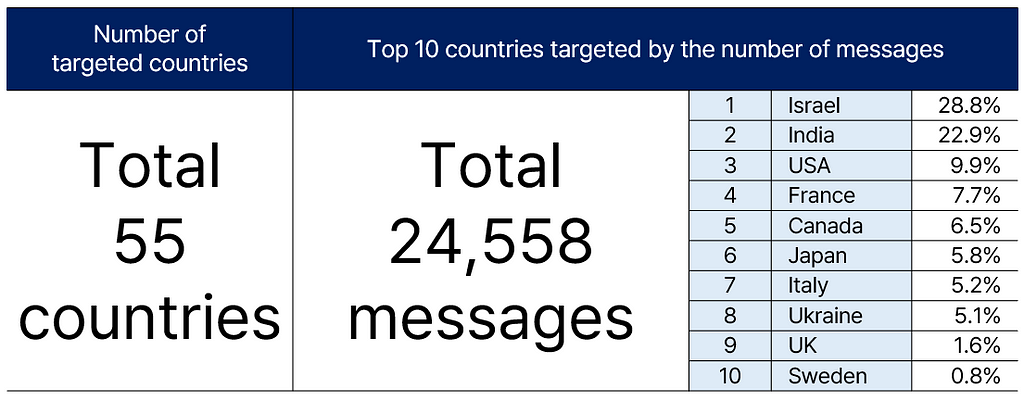
- Hacktivist groups demonstrate strong anti-Western tendencies.
A total of 55 countries have been targeted for hacking, with messages directed towards Western countries, including Israel, comprising over 95% of the total. - Israel tops the list of frequently targeted countries.
While Ukraine and the U.S. were primary targets before the Russo-Ukrainian conflict, the emergence of an Arab-Russian hacking alliance has shifted the focus post-conflict.
Arab-Russian Hacking Alliance: Centered around traditional hacking powerhouse Russia, this alliance includes groups from China and Indonesia, along with Arab groups opposing Israel. The alliance appears more loosely connected, based on individual nations’ political and economic interests rather than a tight alliance.
- Not all targeted backgrounds are war-related. For instance,
Japan’s repeated targeting is tied to the release of Fukushima-contaminated water, and Thailand’s incidents relate to territorial disputes with Cambodia.
(South Korea has been targeted four times due to its relationship with the West and Israel.) - The alliances are not consistently unified.
Disputes arise within these groups based on individual countries’ circumstances.
 Sample of hacktivism messages
Sample of hacktivism messages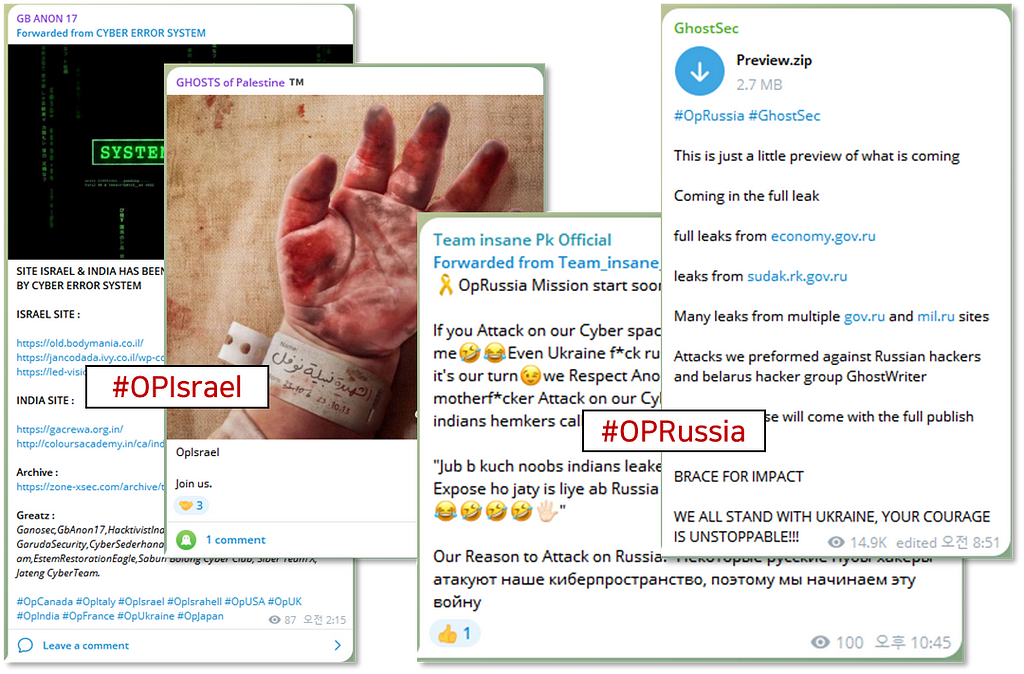
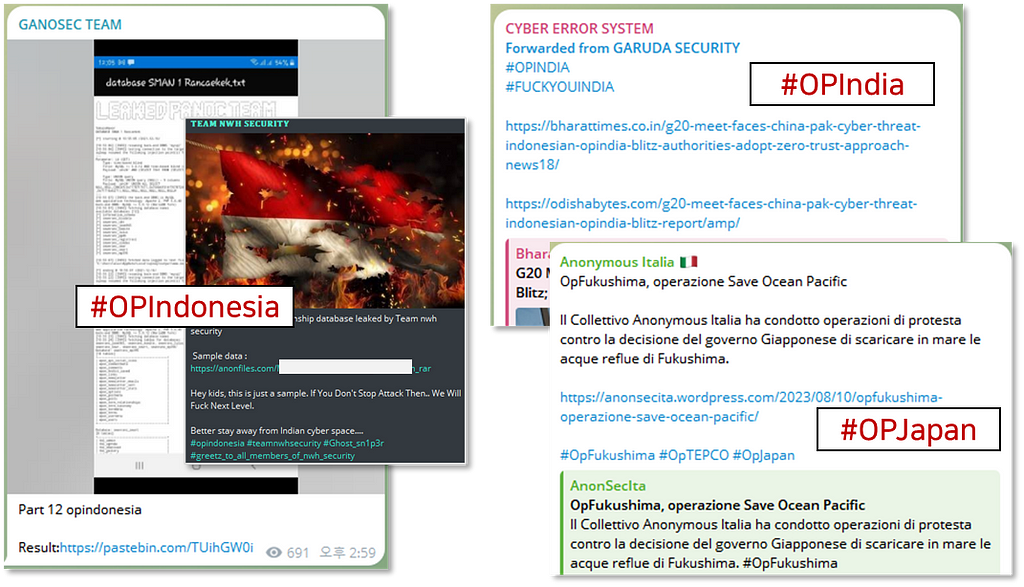 Hacktivist 그룹의 텔레그램 메시지 샘플
Hacktivist 그룹의 텔레그램 메시지 샘플2. Dual Operation: Telegram & Dark Web
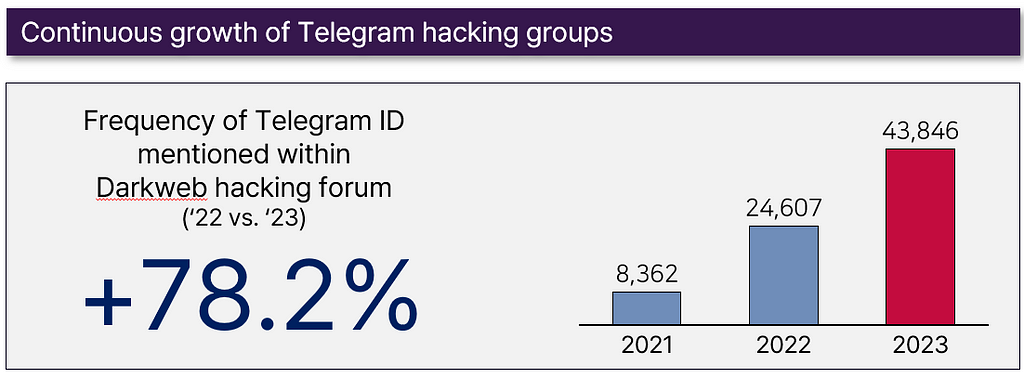
- The number of threat actors operating separate Telegram channels while being active on renowned hacking forums or communities is steadily increasing.
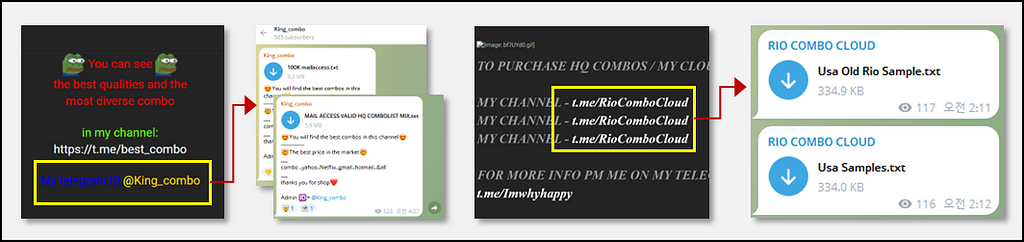 Examples of threat actors' posts and mentioned Telegram channels within dark web forums
Examples of threat actors' posts and mentioned Telegram channels within dark web forums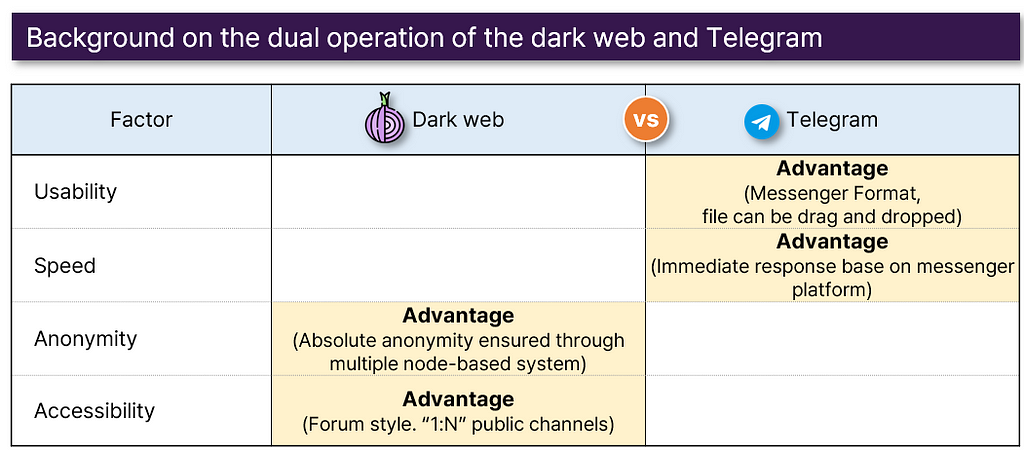
- Due to its usability, convenience, and speed, many threat actors and threat actor groups are transitioning to Telegram. However, if one does not know the address of a particular Telegram channel, accessing it can be challenging. Additionally, in terms of anonymity and security, the advantages of the dark web are evident. Typically, renowned hacking groups utilize both platforms simultaneously.
Dark Web: Used for forums or operating separate web pages.
Telegram: Used as a communication channel, for uploading leaked files, among other things.
3. MOVEit Vulnerability
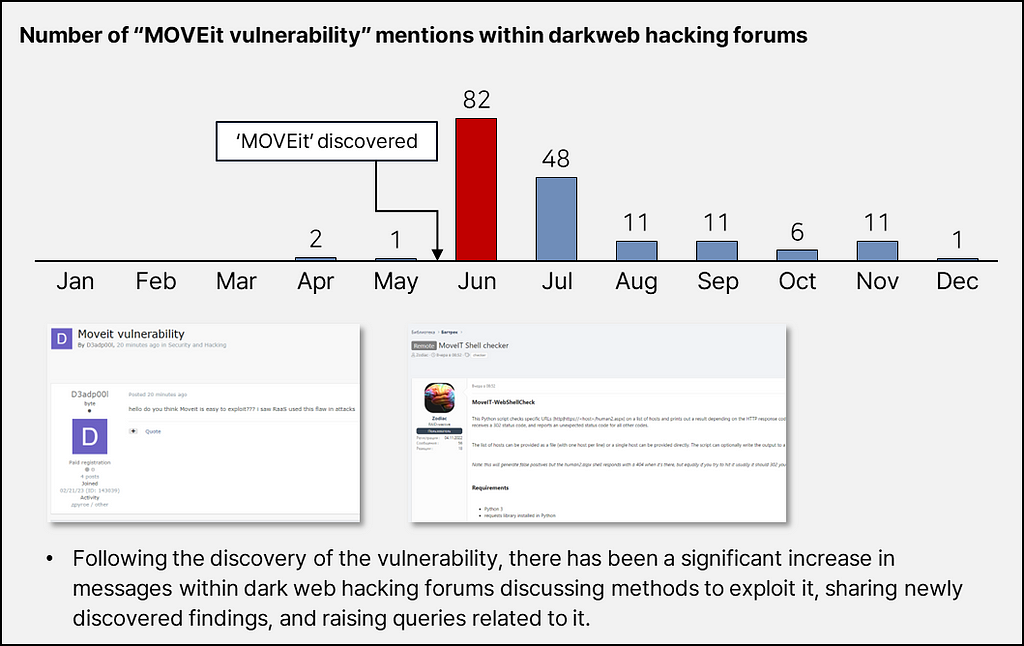
- In June 2023, a critical vulnerability was discovered in the widely-used file transfer software ‘MOVEit’ by corporations.
Immediate attention and prompt patch application by software users were required. - The known vulnerabilities are CVE-2023–34362 and CVE-2023–35036, applicable to all versions of MOVEit. Exploitation of these vulnerabilities could lead not only to data theft from files managed by the software but also potentially allow for the takeover of internal network systems.
- Notably, the infamous dark web ransomware group CLOP has actively leveraged these vulnerabilities, targeting numerous enterprises. Global corporations like Sony, PWC, and EY have reportedly suffered due to these vulnerabilities.

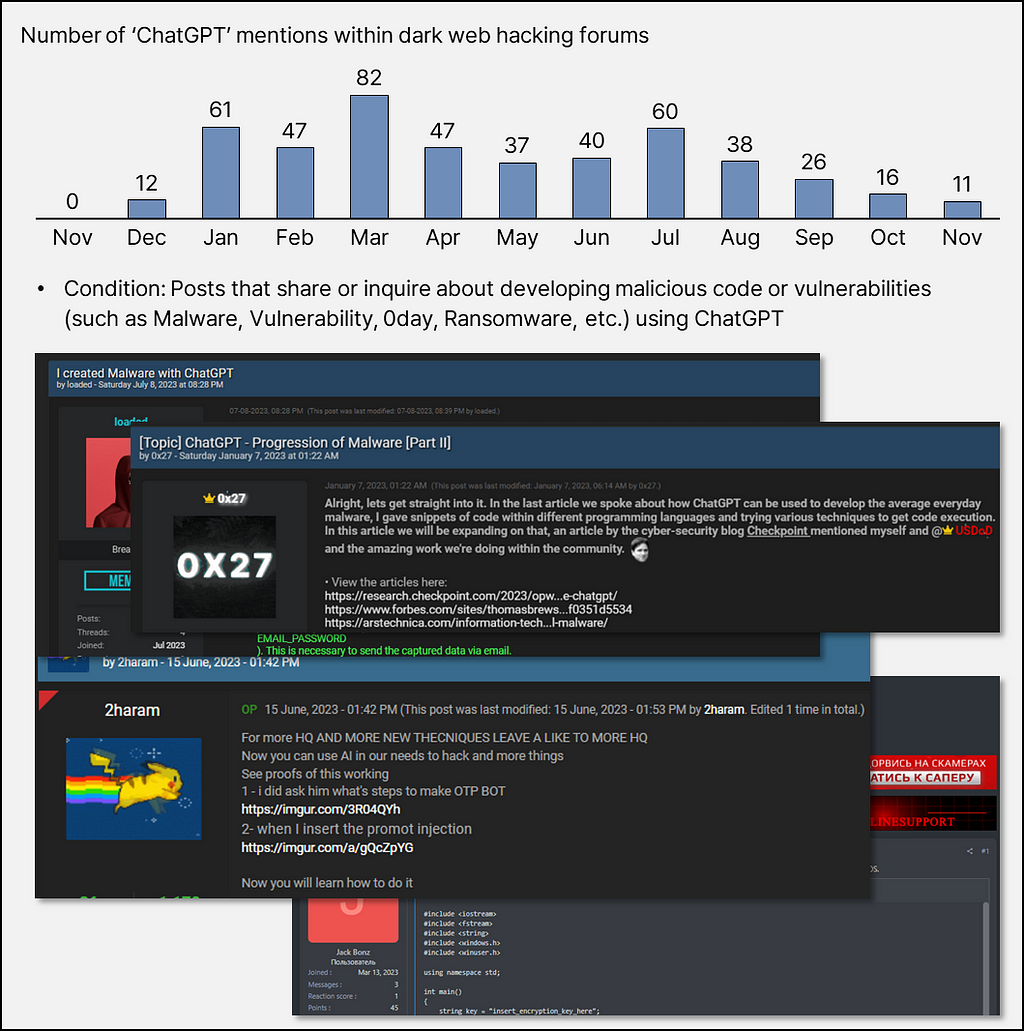
4. New technology being abused within the Dark Web: ChatGPT
- Since the release of ChatGPT in March 2023, dark web hacking forums have seen not only posts leaking paid accounts for ChatGPT but also numerous discussions and inquiries about exploiting ChatGPT to develop various malware and vulnerabilities.
- Some posts even share ransomware codes developed using ChatGPT or provide detailed explanations through videos, showcasing immediate exploitable instances.
- In the future, with the emergence of socially impactful new technologies, we can anticipate a rise in such posts on dark web hacking forums, detailing methods to exploit them.
#2. Dark Web Statistics: Users, affected industries
1. Dark Web Users
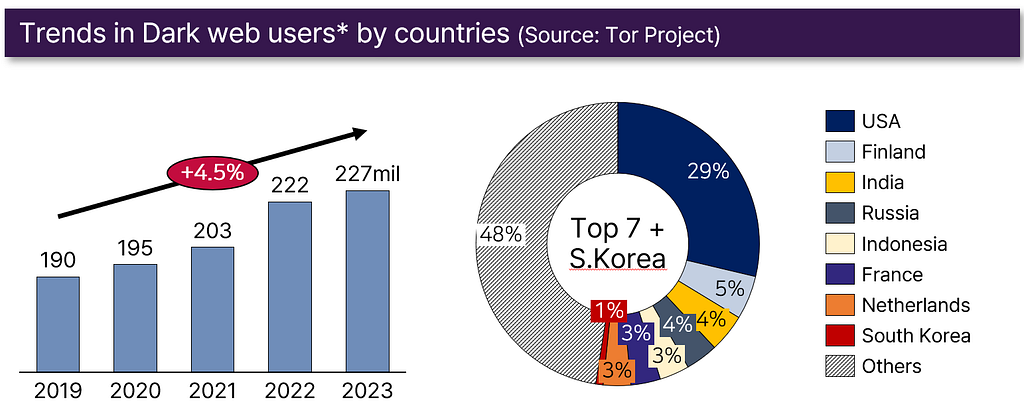
- Dark web users are growing, reaching a record daily average of about 2.27 million this year.
- Top user countries include the U.S., Finland, and India.
Russia’s user base has declined since imposing nationwide sanctions last year. - South Korea averages 18,000 daily users, ranking 26th globally in dark web activity.
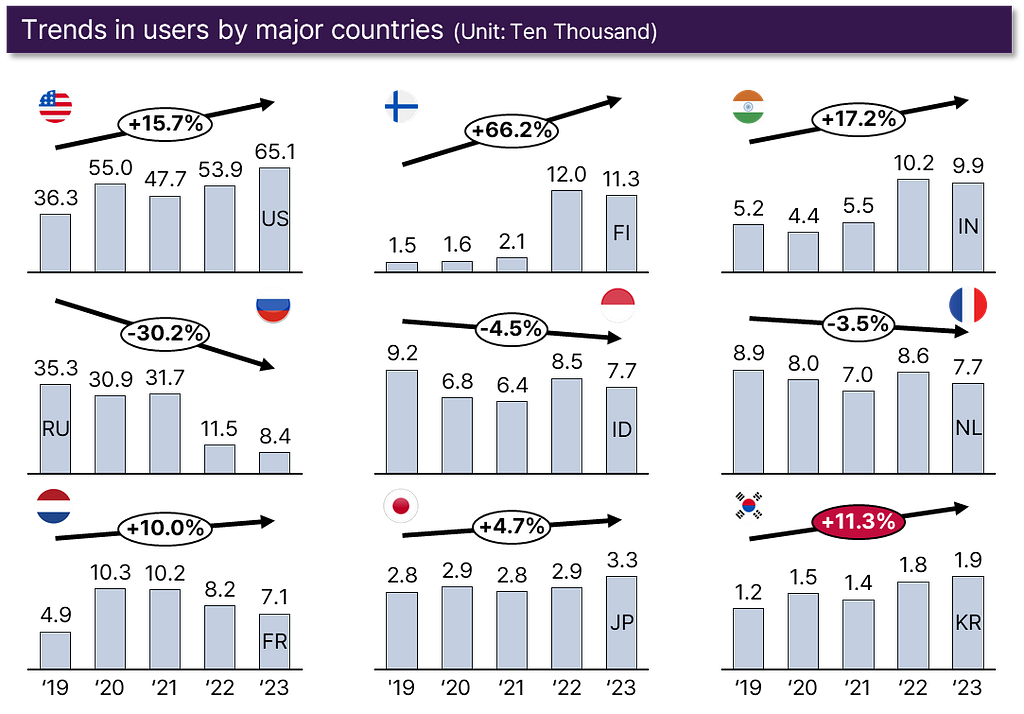 Germany is excluded from the statistics because there has been an unusually sharp increase starting from June 2023. The ‘Tor Project’, responsible for dark web statistics, has announced that they began the investigation on this case. (With Germany included, the global count for this year is approximately 3.62 million.)
Germany is excluded from the statistics because there has been an unusually sharp increase starting from June 2023. The ‘Tor Project’, responsible for dark web statistics, has announced that they began the investigation on this case. (With Germany included, the global count for this year is approximately 3.62 million.)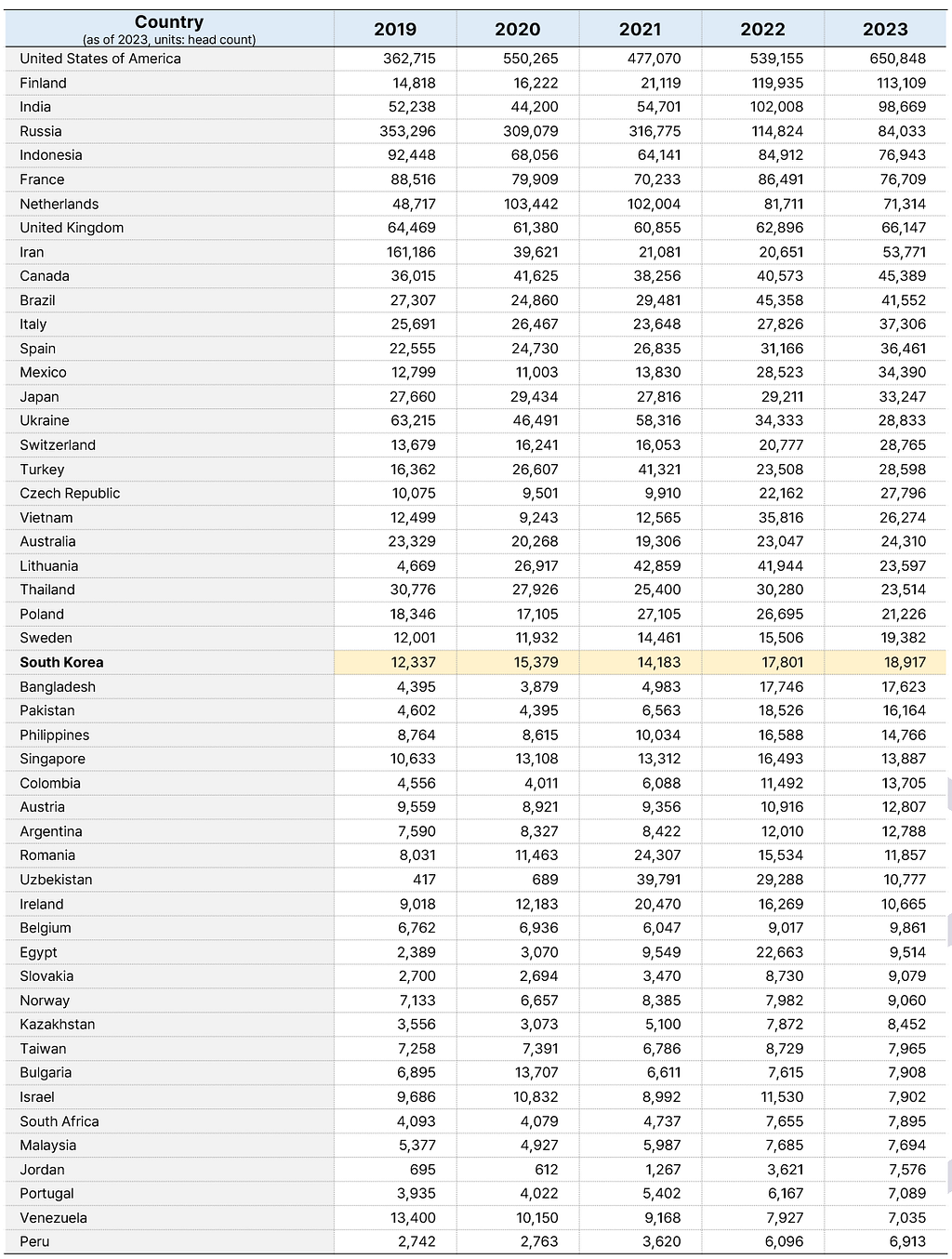
2. Data Breach: Impact across industries
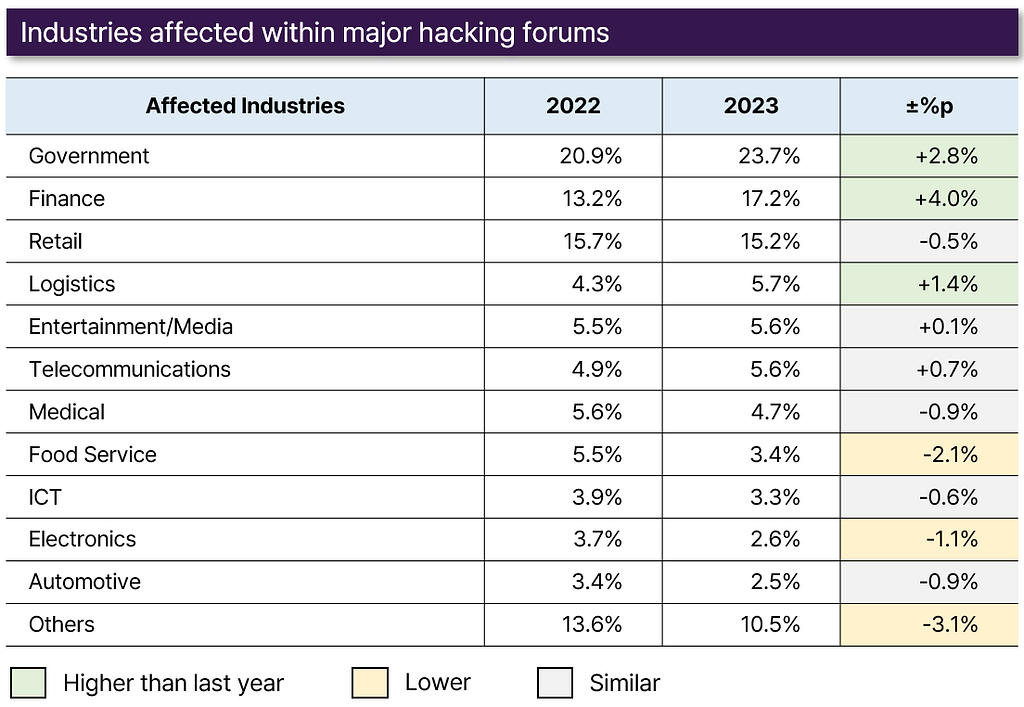
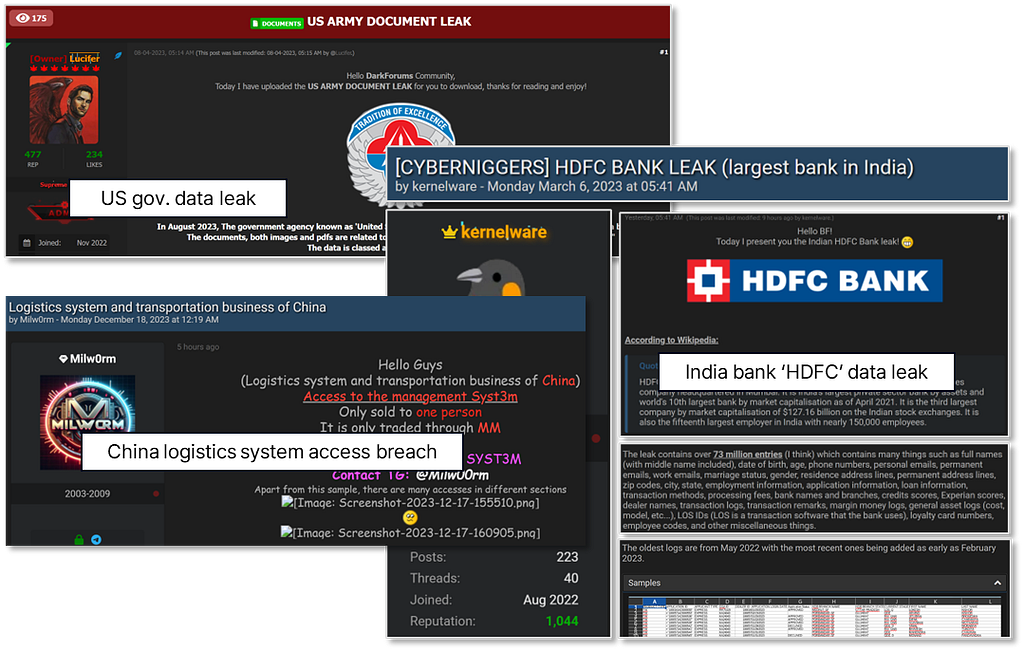 Leak samples
Leak samples3. Ransomware in Dark web
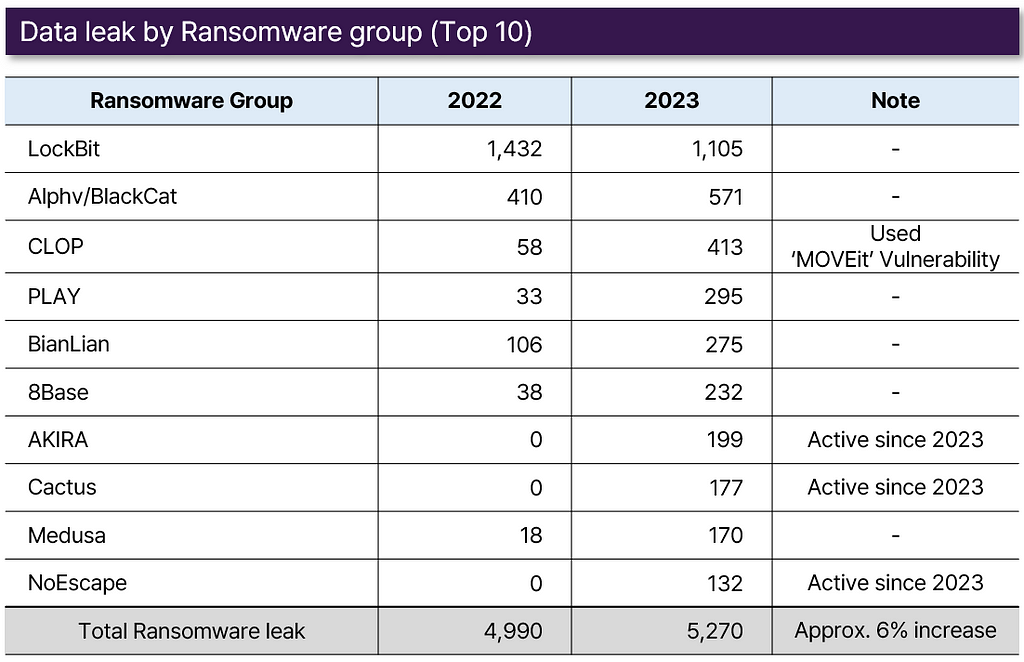
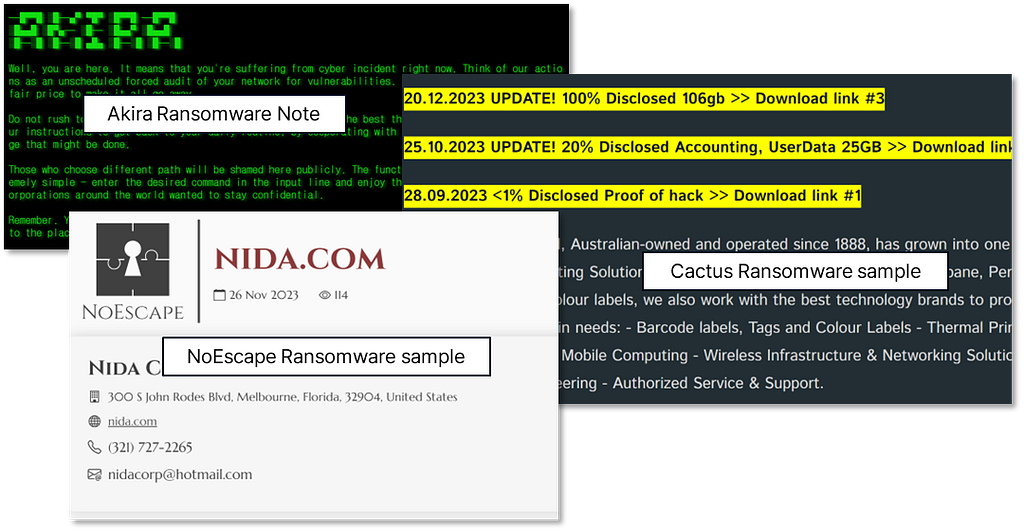
- This year, newly established ransomware groups ‘AKIRA,’ ‘Cactus,’ and ‘NoEscape’ have been among the most active top 10 ransomware gangs.
- The CLOP ransomware gang is known for actively exploiting the most dangerous vulnerability discovered this year, referred to as ‘MOVEit.’
#3. Targeting South Korea: Major incidents and Statistics
1. Hacking Forum: South Korea statistics and samples
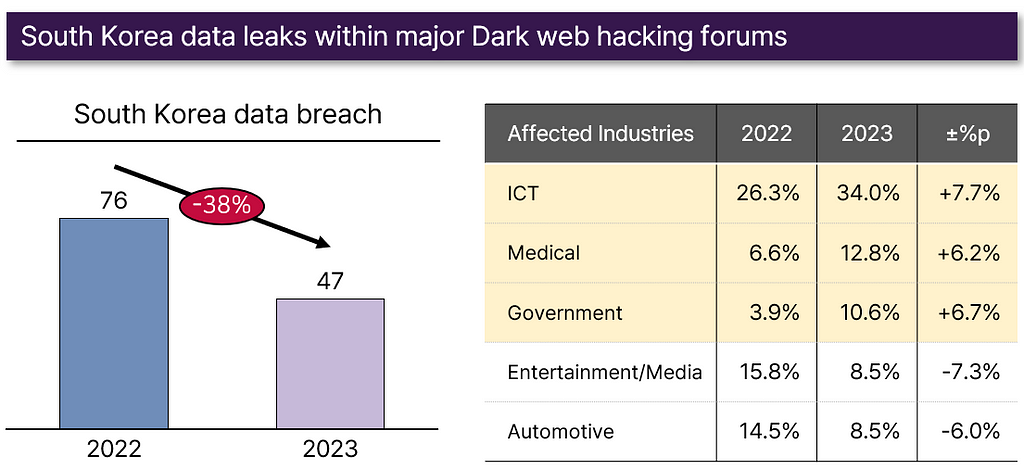
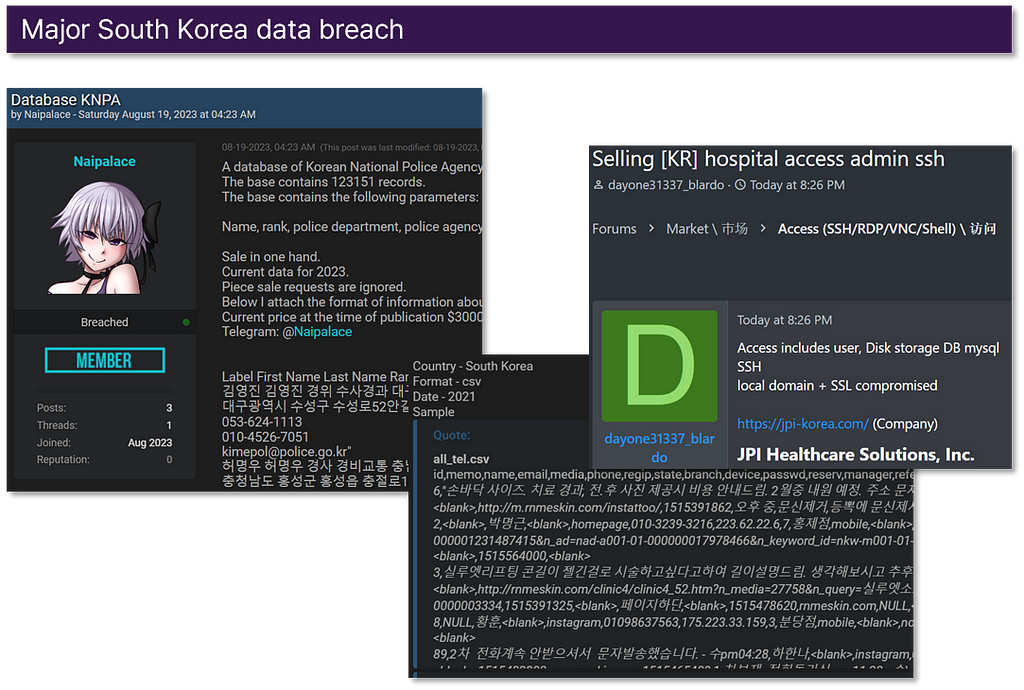
- Within deep/dark web hacking forums, incidents related to South Korea’s data breaches have generally decreased compared to last year. However, some sensitive data breaches have occurred across diverse industries.
- Examples: Internal data leaks from the police agency, patient information breaches from hospitals, selling of network access credentials within hospitals, and data breaches from multiple ICT companies.
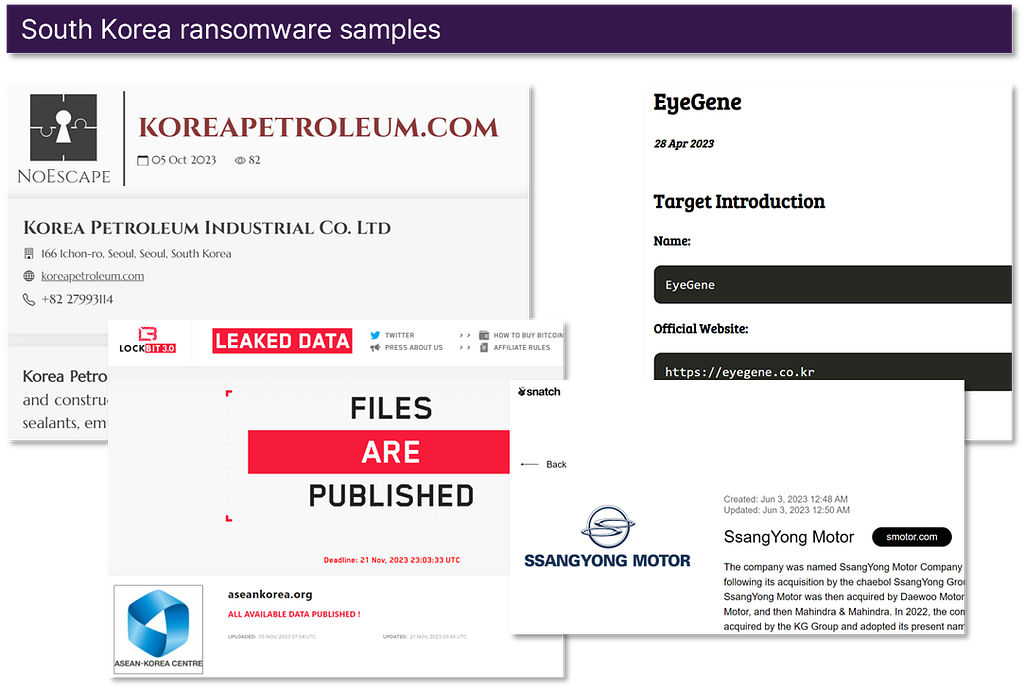
2. Ransomware: South Korea statistics and samples
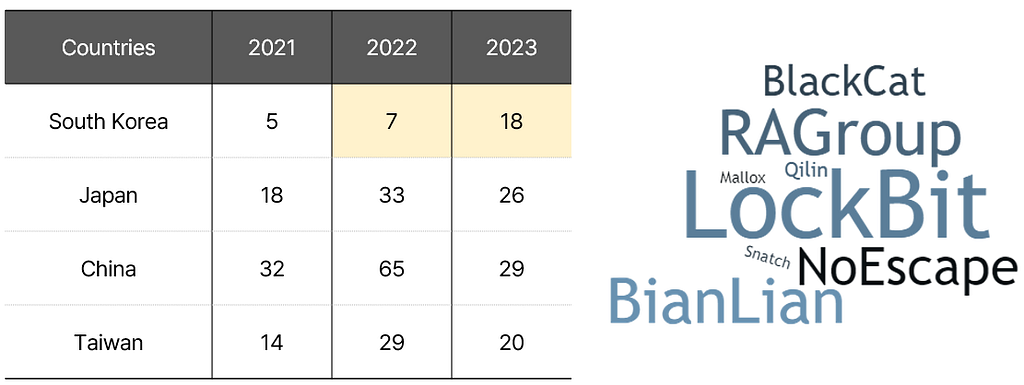
- While the absolute number of ransomware incidents in South Korea is lower compared to neighboring countries, there has been more than a twofold increase from the previous year.
- The top three affected industries are Manufacturing, Government, and Retail, accounting for 35.3%, 11.8%, and 11.8% respectively.
- While the ‘LockBit’ group inflicted the most ransomware damage in South Korea, the activities of newly emerged ransomware groups like ‘NoEscape,’ ‘RA Group,’ and ‘BianLian’ have also had significant impacts.
#4. Targeting North Korea: Major incidents and Statistics
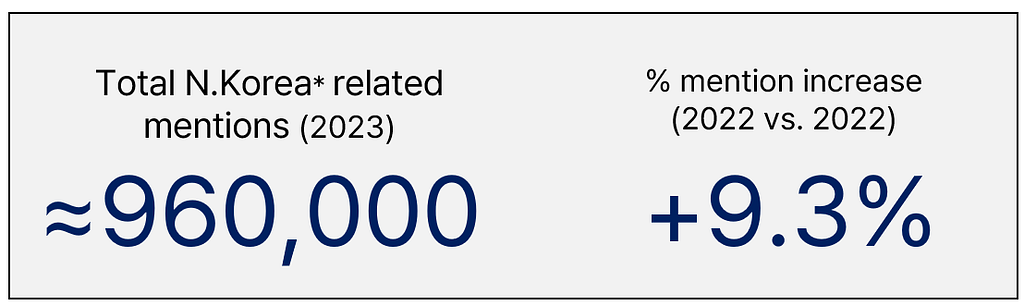 *Example of North Korea keywords: ‘North Korea’, ‘n_korea’, ‘Pyongyang’, ‘Kim Jong Un’, ‘DPRK’, etc.
*Example of North Korea keywords: ‘North Korea’, ‘n_korea’, ‘Pyongyang’, ‘Kim Jong Un’, ‘DPRK’, etc.- The number of pages mentioning North Korea on the dark web has nearly reached one million this year, showing an increase compared to the previous year.
- Upon examining pages where North Korea is mentioned, the overwhelming majority contain content that ridicules North Korea or Kim Jong-un. It appears that most of these are not authored by actual North Koreans, North Korean threat actors, or discussing developments within North Korea.
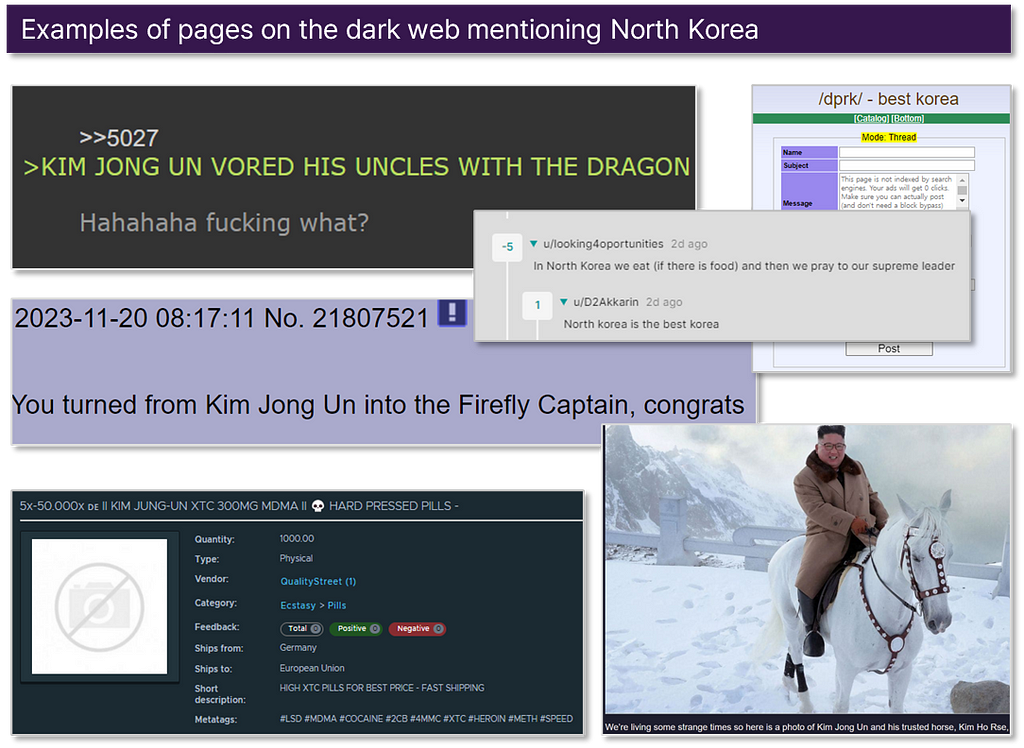
Cases of cyber incidents related to North Korea within the dark web
- Some content actually appears on pages associated with North Korea. This includes actions such as leaking data related to North Korea and attempting hacking attacks against North Korea, as well as conducting hacking attacks against various countries, including South Korea.
1. Leakage of information related to North Korean ships
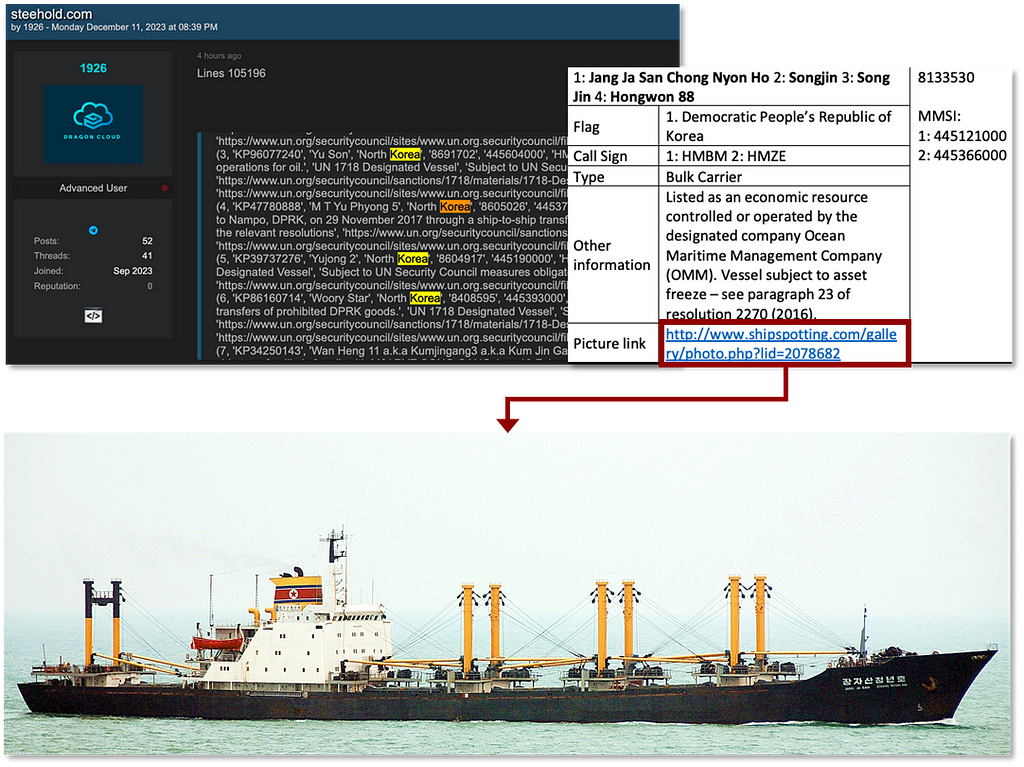
- Internal documents and SQL files of the Ghana-based company ‘Steehold’ have been leaked to the global dark web hacking forum ‘BreachForums’.
- Upon examination of the SQL file, content related to ‘North Korean ships’ was identified.
- The content includes ship MMSI numbers (Maritime Mobile Service Identity, composed of 9 digits) and ship names.
- The threat actor responsible for the leak goes by the ID ‘1926’. This threat actor is active on ‘BreachForums’ and is identified primarily as a user who steals numerous accounts to sell on hacking forums.
2. A print attack campaign utilizing photos of North Korean leaders
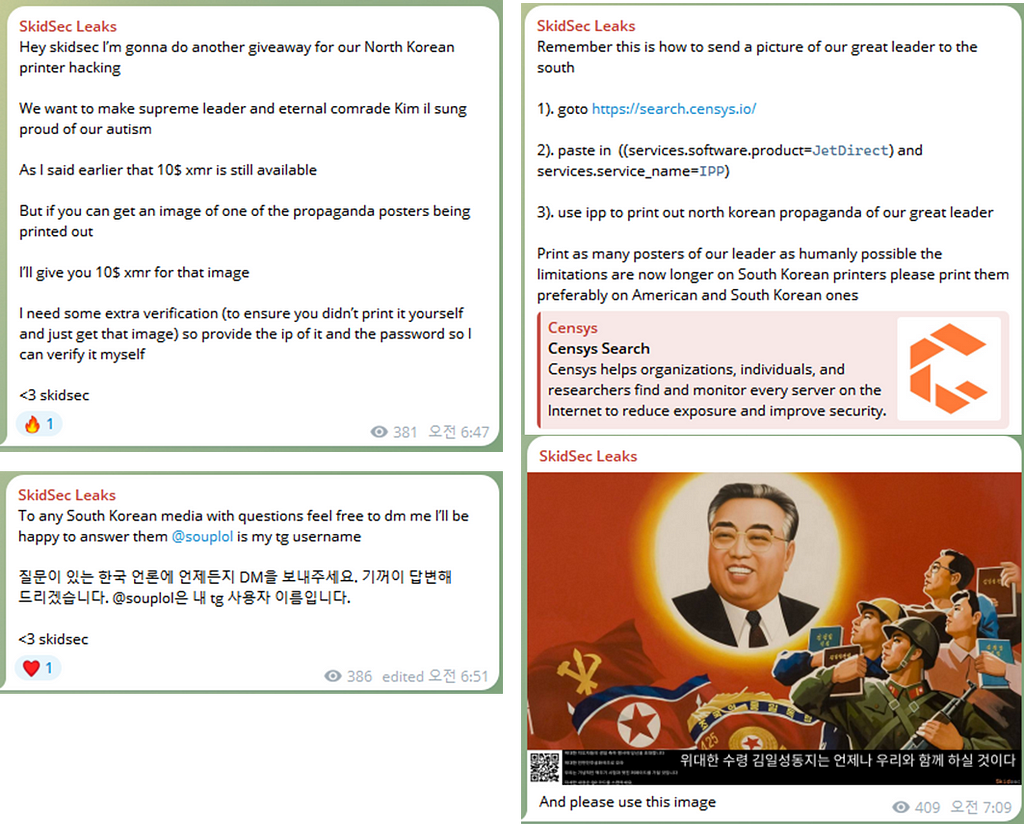
- A post stating that they are conducting a “print attack campaign using photos of North Korean leaders targeting South Korean printers” was uploaded to the Telegram channel ‘SkidSec Leaks’.
- ’SkidSec’ has been conducting hacking attacks targeting various countries and leaking databases since October 18, 2023.
- They are also active on BreachForums, and as of now, only one post has been identified (Post title: Crypto.com Crypto Stadium Leaks).
- The details of the campaign are as follows:
1) Visit the URL: https://search.censys.io/
2) Enter the search term ((services.software.product=JetDirect) and services.service_name=IPP) and location.country=South Korea
3) Identify IPP devices from the search results and print photos of North Korean leaders on them.
3. Leakage of account information from subscribers of ‘Uriminzokkiri’ website
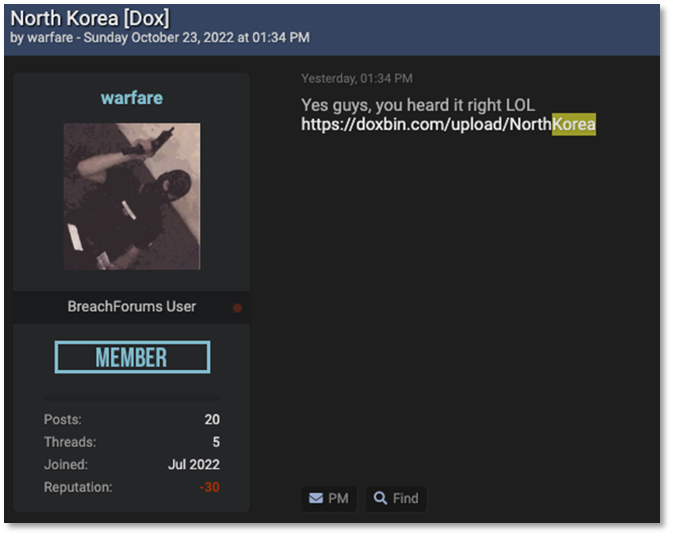

- Account information (email addresses and passwords) allowing access to websites like ‘Uriminzokkiri’ (a North Korean internet propaganda and agitation medium) was being freely shared on prominent hacking forum.
- Furthermore, the threat actor was also leaking account information that could access multiple North Korean government agencies and departments.
- Additionally, the threat actor describes a method to temporarily disrupt services by exploiting a vulnerability (CVE-2017–3881) in a Cisco Router (175.45.178.161) used by North Korea.
4. Leakage of North Korea Spy List
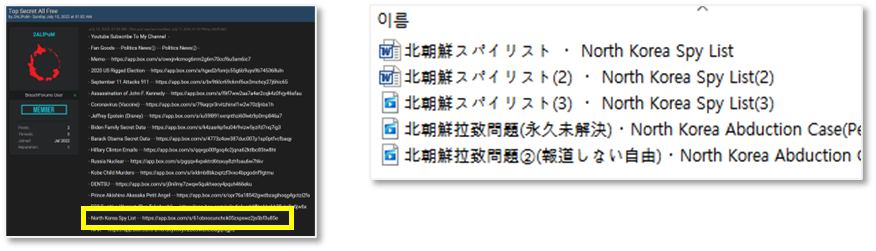
- A post claiming to leak a list of ‘North Korean spies’ was posted on a well-known dark web hacking forum.
- The leaked files contained email addresses and passwords of members who had registered with ‘KANCC’ (Association of North Korean Residents in the U.S.) and ‘Chongryon’ (General Association of Korean Residents in Japan). Additionally, it was confirmed that the data also included self-introductions provided by members during their registration.
5. Request for access permission to North Korean domain
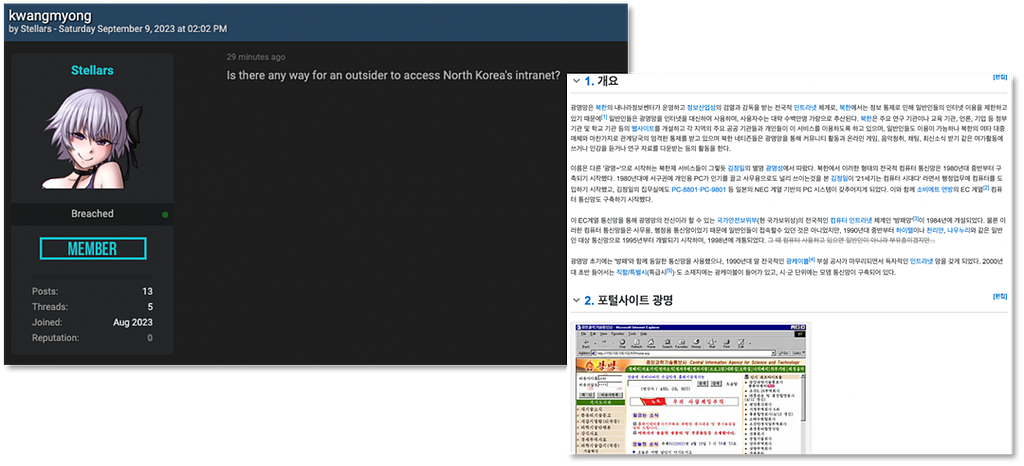
- A post inquiring about methods to access the internal network of North Korea’s internet portal site, ‘Kwangmyong’ was detected on a dark web hacking forum.
6. Purchasing personal information of North Korea citizens
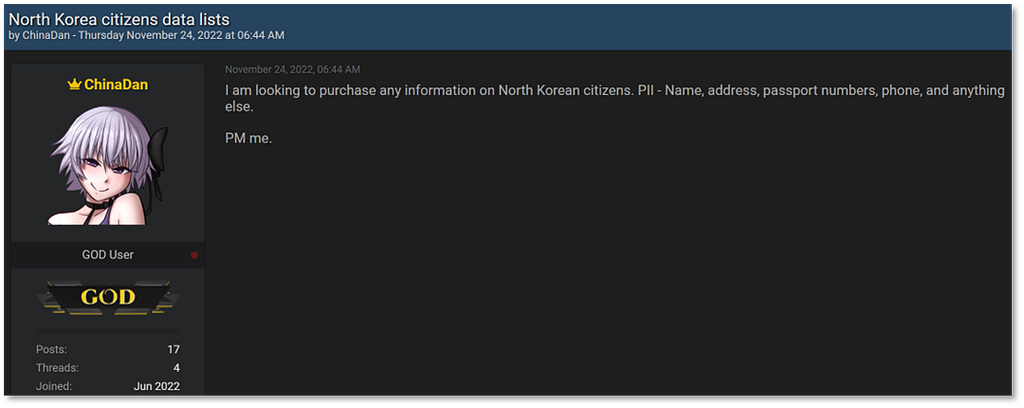
- A post on a dark web hacking forum was captured, indicating an inquiry about purchasing personal information of North Korean citizens. The title of the inquiry post was “North Korea citizens data lists.”
- The threat actor goes by the ID ‘ChinaDan.’ This individual is known as a ‘personal information specialist broker’ who previously stole and sold the personal information of hundreds of millions of Chinese citizens by hacking into China’s public security database.
Dark Web Trends Report: Key Content Trends and Statistical Information (English ver.) was originally published in S2W BLOG on Medium, where people are continuing the conversation by highlighting and responding to this story.
Article Link: Dark Web Trends Report: Key Content Trends and Statistical Information (English ver.) | by S2W | S2W BLOG | Medium