A new plant has grown in the desert of cyber threats, wielding its thorns to pierce through organizations and individuals alike. The Cactus Ransomware Group, a name recently whispered with curiosity across the cybersecurity realm, has emerged from the shadows, sowing seeds of chaos and disruption in its wake. With a prickly demeanor, this threat actor has meticulously crafted its ransomware to not only encrypt but also entangle itself within the fabric of digital security, evading detection with a finesse that demands a closer look.
 Threat actor card of Cactus Ransomware
Threat actor card of Cactus Ransomware
Much like its namesake in the natural world, the Cactus Ransomware does not merely sit idly; it poses a latent threat, waiting for the opportune moment to strike. Employing a unique encryption technique that encrypts the ransomware binary itself, Cactus ensures its malicious endeavors go unnoticed by antivirus solutions, allowing it to propagate and establish a stronghold within the compromised system.
In this exploration, we delve into the intricate layers of Cactus Ransomware, unraveling its mechanisms, targets, and the prickly path it treads upon in the vast landscape of cyber espionage and malicious activities. Through our analysis, we aim to shed light on the dark corners where Cactus Ransomware blossoms, providing insights and recommendations to safely navigate through its thorny presence.
Who is Cactus Ransomware?
The Cactus Ransomware Group, first identified in March 2023, has rapidly spread its spines across the digital domain, exploiting vulnerabilities, particularly within VPNs, to gain unauthorized access and establish a foothold within compromised infrastructures. The group has demonstrated a sophisticated understanding of evasion techniques, employing a dynamic approach to encryption and utilizing many tools and techniques to ensure its malicious payload is delivered effectively and covertly.
 Fig. 1. Illustration of Cactus Ransomware, generated using DALL-E 3
Fig. 1. Illustration of Cactus Ransomware, generated using DALL-E 3
Cactus does not just stop at encryption. The threat actor ensures its presence is deeply rooted within the compromised system, employing a complex infection chain and utilizing multiple layers of obfuscation to conceal its activities. From using UPX packing and leveraging encryption algorithms like OpenSSL, AES OCB, and ChaCha20_Poly1305 to organizing restart executions and enumerating network shares, Cactus demonstrates a multifaceted approach to its attacks, ensuring that its activities are not only successful but also remain surrounded in secretiveness.
How does the Cactus Ransomware Attack?
The group has demonstrated an ability to hit stealthily, ensuring its malicious attempts remain concealed beneath a cover of sophistication and complexity. Here are the phases cactus ransomware follows when it is operating:
The Initial Access
Cactus Ransomware exploits vulnerabilities in VPN devices, paving a secret path into the target’s infrastructure. The initial access is indicated by the exploitation of VPN vulnerabilities, followed by the creation of an SSH backdoor, which not only facilitates unauthorized access but also ensures a persistent presence within the compromised network.
The Infection Chain
The infection chain of Cactus is a complicated journey through multiple layers of obfuscation and evasion. Employing a batch script to execute the ransomware sample using 7-Zip, Cactus encrypts itself, evading detection mechanisms and embedding itself within the system. The attack chain is multifaceted, involving a series of steps that include exploiting VPN vulnerabilities, utilizing remote access tools like Splashtop or AnyDesk, managing operations with SuperOps RMM software, simulating attacks with Cobalt Strike, establishing encrypted communication channels with Chisel, and exfiltrating credentials.
Encryption Phase
Once embedded, Cactus Ransomware follows a path of encryption. The ransomware employs AES-256-GCM and RSA-4096 encryption algorithms, ensuring the victim’s files are securely encrypted, amplifying the attack’s impact. The ransom note, named “cAcTuS.readme.txt“, is then released, planting seeds of panic and urgency within the victim.
 Fig. 2. Ransom note of Cactus Ransomware
Fig. 2. Ransom note of Cactus Ransomware
Data Exfiltration and Leaks
Cactus does not merely stop at encryption. The threat actor ensures that its venomous spines reach far and wide, threatening to publish the victim’s data on its data leak portal if the ransom is not paid, which is called the double extortion method. The data leak portal, a dark web domain, becomes a threat to the victims, ensuring that the attack’s implications extend beyond encryption, permeating into data integrity and reputation damage.
Persistence
Cactus Ransomware ensures its persistent presence within the compromised system by creating a scheduled task named “Updates Check Task” that runs every 5 minutes, thereby running the ransomware as SYSTEM and ensuring that its malicious activities continue without a problem.
Structure of Cactus Ransomware
Now, if we move on to the structure of the Cactus:
The sample we can access from the internet is the GNU linker. Looking at the details, we can observe that the language it was developed in is C/C++.
Our sample’s hash is:
SHA256: 78c16de9fc07f1d0375a093903f86583a4e32037a7da8aa2f90ecb15c4862c17
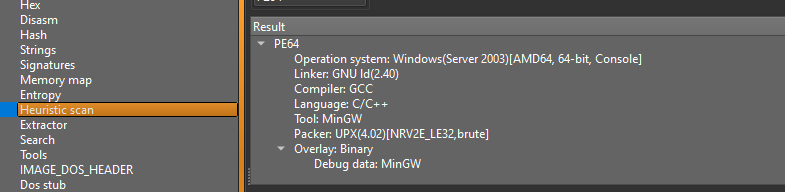 Fig. 3. Detect It Easy output showing that Cactus ransomware is developed in C/C++
Fig. 3. Detect It Easy output showing that Cactus ransomware is developed in C/C++
A Quick Look at Cactus Ransomware’s TOR site
When we access Cactus Ransomware’s TOR site, we are greeted by the main page listing victim shares.
 Fig. 4. Main page of Cactus Ransomware TOR site
Fig. 4. Main page of Cactus Ransomware TOR site
When we access Cactus Ransomware’s TOR site, we are greeted by the main page listing victim shares. At the top, a search box and buttons take you to the “Home” and “Contact” sections.
Clicking on any victim on the main page opens the victim detail page, which includes information about Cactus’ victim, a download link to the data leaked by Cactus, and evidentiary images:
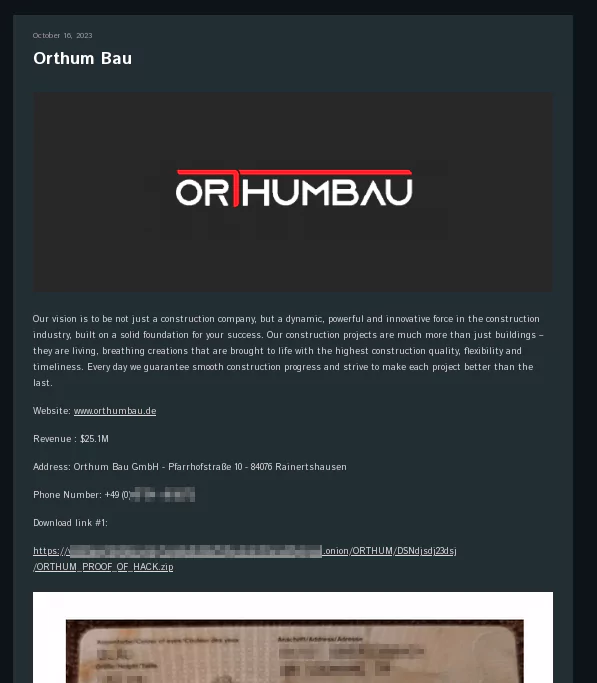 Fig. 5. Victim details page of one of the Cactus Ransomware’s victims
Fig. 5. Victim details page of one of the Cactus Ransomware’s victims
As we click on the Contact page above, we are greeted with a link to the sonar message platform to access “Cactus Support”.
 Fig. 6. Contact page of Cactus Ransomware TOR site
Fig. 6. Contact page of Cactus Ransomware TOR site
When we follow the Sonar message link, there are message boxes for us to reach Cactus:
 Fig. 7. Sonar Message TOR page set for Cactus Support
Fig. 7. Sonar Message TOR page set for Cactus Support
What are the targets of Cactus Ransomware?
Navigating through the dry landscapes sculpted by the Cactus Ransomware Group, we encounter many targets. The targets paint a picture of a threat actor that is not bound by geographical or sectoral limitations but rather one that spreads its spines far and wide.
Target Sectors:
The sectors targeted by the Cactus Ransomware Group are as diverse as they are numerous. From financial entities to law firms, Cactus has ensured that its thorns prick through various sectors of our digital world. But mostly, the group targeted organizations that operate in Manufacturing and Professional Services.
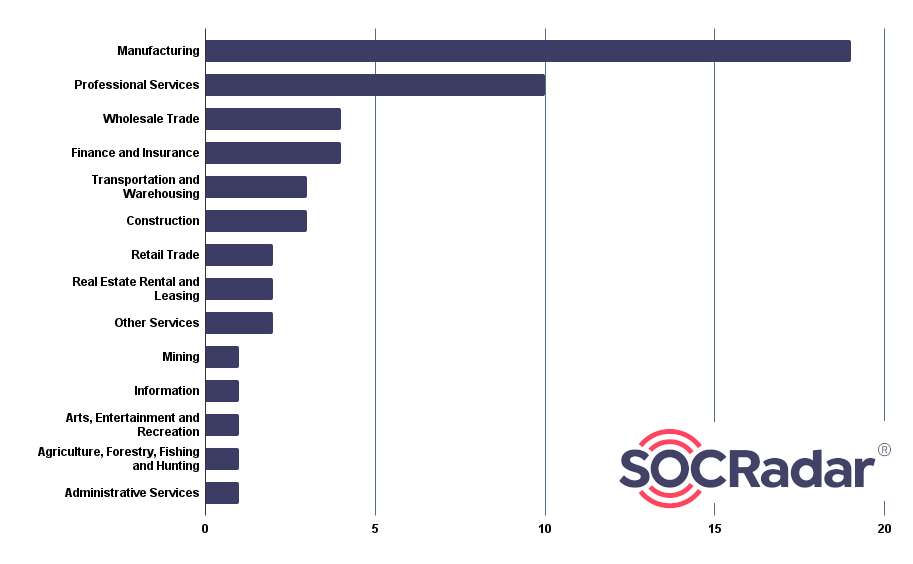 Fig. 8. Distribution of Industries Affected by Cactus Ransomware
Fig. 8. Distribution of Industries Affected by Cactus Ransomware
Target Countries:
With its global attribute, Cactus Ransomware does not confine its malicious endeavors to a specific geographical locale. Its spines have pierced through various countries.
 Fig. 9. Countries Affected by Cactus Ransomware (Source: SOCRadar)
Fig. 9. Countries Affected by Cactus Ransomware (Source: SOCRadar)
Looking at the distribution of the victim countries, the United States is targeted mostly (51.9%) by the Cactus Ransomware.
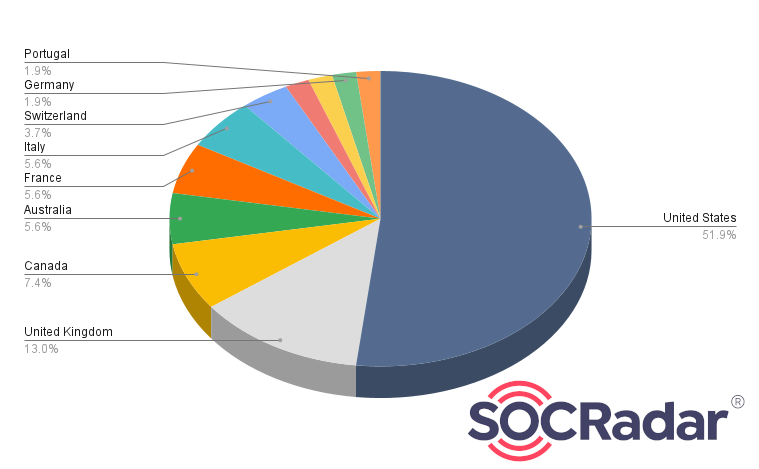 Fig. 10. Distribution of countries affected by Cactus Ransomware (Source: SOCRadar)
Fig. 10. Distribution of countries affected by Cactus Ransomware (Source: SOCRadar)
Latest Activities of Cactus Ransomware
The Hurley Group:
 Fig. 11. The Hurley Group’s Victim post of Cactus Ransomware
Fig. 11. The Hurley Group’s Victim post of Cactus Ransomware
RICOR Global Limited:
 Fig. 12. RICOR’s victim post of Cactus Ransomware
Fig. 12. RICOR’s victim post of Cactus Ransomware
Conclusion
The Cactus Ransomware Group poses a significant threat in the cyber landscape. They have established themselves as a major cyber adversary using advanced encryption techniques, evasion strategies, and diverse attack methods. They have successfully attacked various sectors globally, demonstrating their ability to penetrate and remain within systems, causing chaos and disruption. Victims face encryption challenges and the potential public exposure of their data on Cactus’s leak portal, jeopardizing data integrity, confidentiality, and organizational reputation. It is crucial to understand Cactus Ransomware’s tactics to combat this threat and equip ourselves with the necessary knowledge and tools to protect against it. The next section will provide security recommendations to defend against Cactus Ransomware’s malicious activities.
 Fig. 13. Threat Actor/Malware page of Cactus Ransomware (Source: SOCRadar)
Fig. 13. Threat Actor/Malware page of Cactus Ransomware (Source: SOCRadar)
Security Recommendations Against Cactus Ransomware
Navigating through the dangerous desert sculpted by the Cactus Ransomware Group necessitates not only an understanding of its prickly paths but also the armament of robust defenses to safeguard against its venomous spines. As we tread cautiously through the thorny terrains, let’s explore various security recommendations to shield against the multifaceted threats posed by Cactus Ransomware.
Patching and Updating: A Shield Against Vulnerabilities
Prioritize VPN Security: Ensure that all VPN softwares/devices are patched and updated to shield against vulnerabilities exploited by Cactus.
Regular Updates: Consistently update all software, systems, and applications to fortify defenses against potential breaches.
Enhanced Detection Mechanisms: Unveiling the Concealed Threat
Antivirus Solutions: Employ robust antivirus and EDR/EPP solutions capable of detecting and mitigating threats posed by self-encrypting ransomware binaries.
Behavioral Analysis: Utilize tools, including EDR (Endpoint Detection and Response) and EPP (Endpoint Protection Platform), that perform behavioral analysis to detect anomalous activities indicative of a ransomware attack.
Data Protection: Safeguarding the Lifeblood of Operations
Regular Backups: Ensure that data is backed up regularly and that backup systems are isolated from the network to safeguard against encryption.
Data Encryption: Employ data encryption to protect sensitive information from potential leaks and unauthorized access.
User Awareness and Training: Armoring the Human Element
Phishing Awareness: Conduct training sessions to enhance user awareness regarding phishing emails, which are often utilized by Cactus for initial access.
Safe Practices: Educate users on safe online practices to mitigate the risk of inadvertently facilitating a breach.
Network Security: Fortifying the Digital Perimeter
Network Segmentation: Employ network segmentation to contain the spread of ransomware in the event of a breach.
Secure Configurations: Ensure that systems and networks are securely configured to shield against potential infiltrations.
Incident Response Plan: Navigating Through the Crisis
Develop and Test: Formulate an incident response plan and ensure that it is tested and updated regularly to effectively navigate through a crisis.
Communication Channels: Establish secure communication channels to coordinate response efforts in the event of a ransomware attack.
Legal and Regulatory Compliance: Navigating Through the Repercussions
Data Breach Protocols: Ensure that data breach protocols are in place and comply with legal and regulatory requirements pertaining to data exposure and leaks.
Notification Procedures: Establish procedures to notify affected parties and relevant authorities in the event of a data breach.
Leveraging Cyber Threat Intelligence: A Beacon in the Desert
Utilize Threat Intelligence: Leverage cyber threat intelligence to gain insights into the tactics, techniques, and procedures (TTPs) employed by Cactus Ransomware.
SOCRadar’s Insights: Utilize SOCRadar to stay abreast of the latest developments and threats posed by threat actors like the Cactus Ransomware Group, ensuring that defenses are continually updated and fortified against emerging threats.
MITRE ATT&CK TTPs of Cactus Ransomware
|
Technique |
ID |
|
Initial Access |
|
|
Exploit Public-Facing Application |
T1190 |
|
Execution |
|
|
Command and Scripting Interpreter |
T1059 |
|
Windows Management Instrumentation |
T1047 |
|
Shared Modules |
T1129 |
|
Software Deployment Tools |
T1072 |
|
Persistence |
|
|
DLL Side-Loading |
T1574.002 |
|
Scheduled Task/Job |
T1053 |
|
Scheduled Task |
T1053.005 |
|
Create Account |
T1136 |
|
Privilege Escalation |
|
|
Process Injection |
T1055 |
|
DLL Side-Loading |
T1574.002 |
|
Defense Evasion |
|
|
Process Injection |
T1055 |
|
Obfuscated Files or Information |
T1027 |
|
Masquerading |
T1036 |
|
Virtualization/Sandbox Evasion |
T1497 |
|
Hidden Files and Directories |
T1564.001 |
|
DLL Side-Loading |
T1574.002 |
|
Impair Defenses |
T1562 |
|
Disable or Modify Tools |
T1562.001 |
|
Obfuscated Files or Information |
T1027 |
|
Software Packing |
T1027.002 |
|
Credential Access |
|
|
Input Capture |
T1056 |
|
Credentials from Password Stores |
T1555 |
|
Credentials from Web Browsers |
T1555.003 |
|
OS Credential Dumping |
T1003 |
|
Discovery |
|
|
System Information Discovery |
T1082 |
|
Security Software Discovery |
T1518.001 |
|
Remote System Discovery |
T1018 |
|
Process Discovery |
T1057 |
|
File and Directory Discovery |
T1083 |
|
Virtualization/Sandbox Evasion |
T1497 |
|
System Network Connections Discovery |
T1049 |
|
Account Discovery |
T1087 |
|
Domain Account |
T1087.002 |
|
Lateral Movement |
|
|
Remote Services |
T1021 |
|
Remote Services: Remote Desktop Protocol |
T1021.001 |
|
Lateral Tool Transfer |
T1570 |
|
Collection |
|
|
Input Capture |
T1056 |
|
Automated Collection |
T1119 |
|
Command and Control |
|
|
Application Layer Protocol |
T1071 |
|
Non-Application Layer Protocol |
T1095 |
|
Non-Standard Port |
T1571 |
|
Encrypted Channel |
T1573 |
|
Remote Access Software |
T1219 |
|
Proxy |
T1090 |
|
Exfiltration |
|
|
Exfiltration Over Web Service |
T1567 |
|
Exfiltration Over Web Service: Exfiltration to Cloud Storage |
T1567.002 |
|
Impact |
|
|
Data Encrypted for Impact |
T1486 |
Cactus Ransomware IoCs
|
IP |
163.123.142[.]213 |
|
HASH |
b9ef2e948a9b49a6930fc190b22cbdb3571579d37a4de56564e41a2ef736767b |
|
HASH |
5b70972c72bf8af098350f8a53ec830ddbd5c2c7809c71649c93f32a8a3f1371 |
|
HASH |
78c16de9fc07f1d0375a093903f86583a4e32037a7da8aa2f90ecb15c4862c17 |
|
HASH |
248795453ceb95e39db633285651f7204813ea3a |
|
HASH |
6715b888a280d54de9a8482e40444087fd4d5fe8 |
|
HASH |
78aea93137be5f10e9281dd578a3ba73 |
The post Dark Web Profile: Cactus Ransomware appeared first on SOCRadar® Cyber Intelligence Inc..
Article Link: Dark Web Profile: Cactus Ransomware
