In the ever-evolving landscape of cyber threats, understanding the profiles of individual threat actors is crucial for both governments and private organizations to take action before major incidents happen. One such actor that has recently come into the spotlight is Bjorka, a mysterious figure responsible for a series of high-profile attacks on the Indonesian government and private sectors. This blog post aims to delve into Bjorka and get to know the actor itself. By understanding the nature of Bjorka’s activities, we can better prepare and defend against similar threats in the future.
Who is Bjorka?
Bjorka is a cyber threat actor whose activities have sent shockwaves through the cybersecurity community. Emerging in the last few years, Bjorka has become synonymous with high-profile hacks, leaks, and cyber-espionage, particularly targeting the Indonesian government.
According to our research, Bjorka first appeared in Raidforums in November 2022. Bjorka continued to operate on Breach Forums after Raidforums was seized.
 Figure 1. Profile picture of Bjorka
Figure 1. Profile picture of Bjorka
- Alias and Identity: Operating under the alias “Bjorka,” the true identity of this threat actor remains shrouded in mystery. Whether an individual or a group, Bjorka’s anonymity has added to the intrigue and complexity of understanding their motives and operations.
- Motivations: While the exact motivations behind Bjorka’s actions are unclear, the targeted nature of the attacks suggests political, financial, and possibly ideological drivers. The leaks of sensitive political information and the sale of passports on the dark web indicate a multifaceted approach to cyber warfare.
- Public Statements: Bjorka has occasionally released public statements, providing insights into their stance on certain issues. These communications, though rare, offer a glimpse into the mindset of this elusive threat actor.
- Creating Its Own Backups: The fact that Bjorka has more than one Telegram and Twitter account, and that the accounts are related to each other, may be intended to prevent possible bans.
Profile Picture of Bjorka
Bjorka has a single profile picture on all his accounts. When looking at this picture, it is understood that it is a profile made up of a combination of two album covers:
 Figure 2. Album covers used by Bjorka in its profile image; “Björk – Utopia” album cover image on the left, “Fever Ray – Plunge” album cover image on the right
Figure 2. Album covers used by Bjorka in its profile image; “Björk – Utopia” album cover image on the left, “Fever Ray – Plunge” album cover image on the right
The only point that draws our attention under this title is that both albums were released in 2017.
How does Bjorka attack?
Bjorka’s attacks are characterized by sophistication, precision, and adaptability. Here’s a list of how Bjorka operates:
- Data Leaks: One of Bjorka’s signature moves is leaking sensitive information. Whether government documents or private data, Bjorka has demonstrated the ability to infiltrate systems and expose confidential material, often with political or financial implications.
- Selling Data on the Dark Web: Bjorka’s activities extend to the dark web, where they have been involved in selling valuable data, such as passports. This not only generates revenue but also amplifies the impact of the attack by putting sensitive information in the hands of other malicious actors.
- Social Engineering: There are indications that Bjorka may also utilize social engineering tactics, manipulating individuals to gain access to restricted information or systems. This human-centric approach adds another layer of complexity to their operations.
- Collaboration with Other Threat Actors: While not fully confirmed, there are hints that Bjorka may collaborate or have connections with other threat actors. This potential network could enhance their capabilities and reach, making them an even more formidable adversary.
- Adaptation and Evolution: Bjorka’s attacks are not static; they evolve and adapt to new challenges and opportunities. This ability to change tactics and learn from previous engagements makes Bjorka a dynamic and unpredictable threat.
Bjorka’s attack methods are a blend of technical prowess and strategic thinking. By employing a diverse array of tactics, Bjorka has managed to stay ahead of defenses and continue to pose a significant threat to its targets. The multifaceted nature of Bjorka’s attacks highlights the need for a comprehensive and adaptable defense strategy.
But do all of its attacks belong to Bjorka?
In the Breach Forums, another actor named “RRR” offered 34 million passports and 6.94 million visa data from the Indonesia Directorate General of Immigration for sale; the same data had previously been shared by Bjorka. However, RRR also offered additional Visa data.
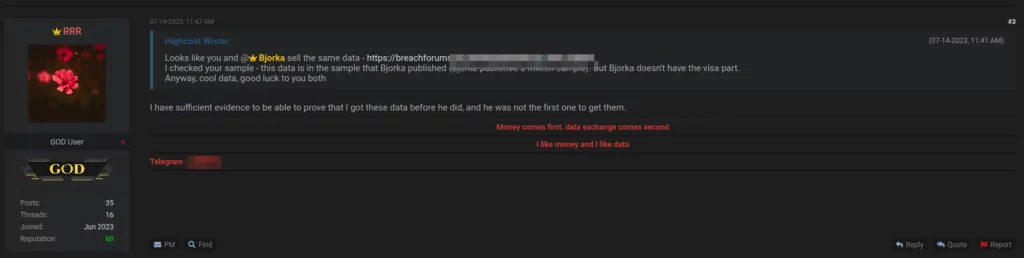 Figure 3. A post advertising the sale of data from the Indonesia Directorate General of Immigration on Breach Forums.
Figure 3. A post advertising the sale of data from the Indonesia Directorate General of Immigration on Breach Forums.
This situation raises two questions:
- Bjorka has all of the data mentioned but thought to separate it and sell it under two separate posts (we could not confirm)
- Bjorka only has the passport part of the data, and the data does not belong to him.
What are the Targets of Bjorka?
Bjorka’s cyber-attacks have been primarily focused on specific sectors and nations, revealing a pattern that may offer insights into their objectives and motivations. Here’s a list of Bjorka’s main targets:
- Indonesian Government: Bjorka has repeatedly targeted various agencies within the Indonesian government. These attacks have included hacking, leaking documents, and even selling sensitive information on the dark web. The focus on governmental bodies suggests a political dimension to Bjorka’s activities.
- Private Sector in Indonesia: Beyond governmental targets, Bjorka has also attacked private companies and organizations within Indonesia. These attacks have ranged from data breaches to financial theft, impacting both the economy and individual privacy.
- Critical Infrastructure: Some of Bjorka’s attacks have targeted critical infrastructure, such as databases containing millions of records. These attacks not only cause immediate damage but also have long-term implications for security and trust in essential services.
- International Reach: While the primary focus has been on Indonesia, there may be indications of Bjorka’s activities extending beyond national borders. This international reach, if confirmed, would signify a broader agenda and potential collaboration with other threat actors.
- Specific Sectors: Bjorka’s attacks have not been random; they have targeted specific sectors such as healthcare, finance, and immigration. This targeted approach allows for maximum impact and may reflect a strategic alignment with broader political or financial goals.
- Individuals and Personal Data: Bjorka’s sale of personal data, such as passports, highlights a willingness to target individuals as part of a broader strategy. This personal targeting adds a layer of complexity and raises ethical concerns about privacy and individual rights.
Bjorka’s choice of targets is both strategic and symbolic, reflecting a calculated approach to cyber warfare. By focusing on specific sectors and nations, Bjorka is able to maximize the impact of their attacks and potentially advance specific agendas. The pattern of targeting also offers clues to Bjorka’s motivations and may provide a roadmap for anticipating and defending against future attacks.
What are Bjorka’s social media habits?
Earlier in the article, we mentioned that Bjorka has multiple social media accounts. There are multiple accounts under the name Bjorka, it is a bit of a question mark as to which of them are real and which are fake, or if they all belong to the same actor.
- We know that Bjorka used to spend time on Raidforums and now on Breach Forums.
 Figure 4. Bjorka’s Breach Forums Information Card
Figure 4. Bjorka’s Breach Forums Information Card
Bjorka shares data sales on “Breach Forums”:
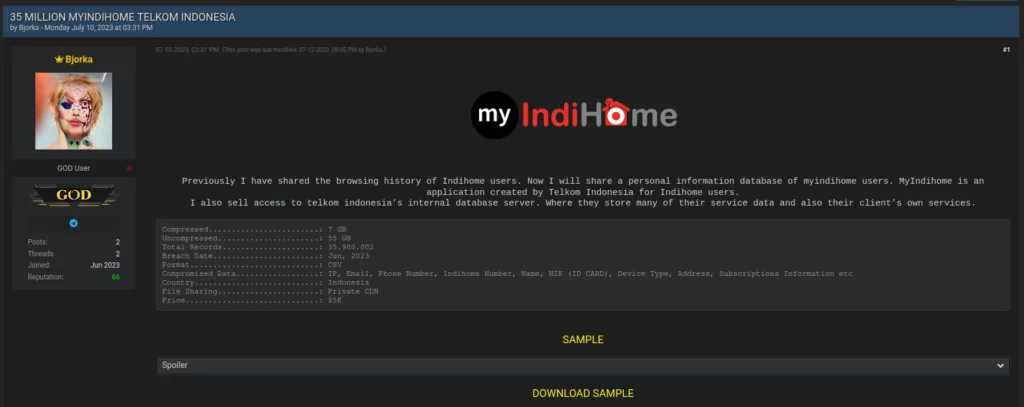 Figure 5. Database of Indihome, one of Bjoka’s data selling posts on Breach Forums
Figure 5. Database of Indihome, one of Bjoka’s data selling posts on Breach Forums
From time to time, Bjorka opened various pages such as bjork[.]ai and leak[.]sh, but none of them are currently accessible. Recently, following the closure of bjork[.]ai, we have noticed the existence of a blog called bjorkanesia, but we have doubts as to whether it belongs to Bjorka itself.
 Figure 6. Bjorkanesia blog’s manifest
Figure 6. Bjorkanesia blog’s manifest
We have observed that Bjorka has started to use Twitter and Telegram frequently, but it has multiple Telegrams and multiple Twitter pages. Most of them share similar posts at similar times, but there are significant differences in the number of followers. This raises the question of whether Bjorka has opened these pages as a backup and repeats the same posts to keep them active or whether Bjorka’s fake accounts have started to form.
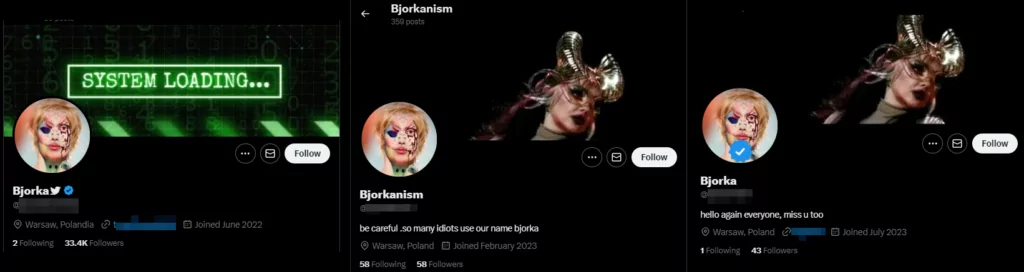 Figure 7. Some of the Bjorka-related Twitter accounts
Figure 7. Some of the Bjorka-related Twitter accounts
When we looked at its Breach Forums profile, we found that the following Telegram profile belongs to Bjorka:
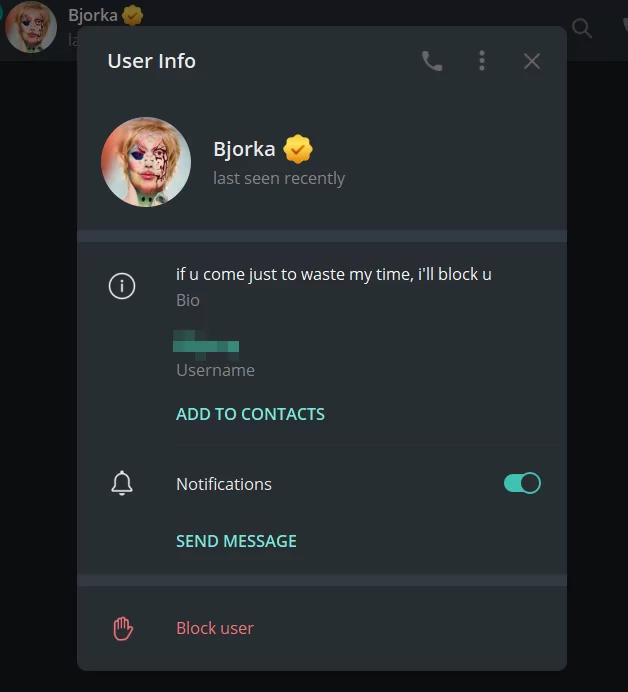 Figure 8. Telegram user card from Bjorka’s Breach Forums profile
Figure 8. Telegram user card from Bjorka’s Breach Forums profile
There are multiple Bjorka channels on Telegram, but some have relatively more followers than others, raising the possibility that they belong to Bjorka:
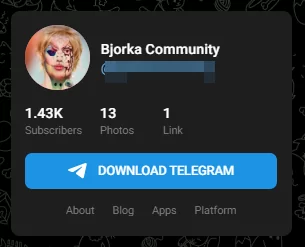 Figure 9. One of the Bjorka Telegram channels with a relatively high number of followers
Figure 9. One of the Bjorka Telegram channels with a relatively high number of followers
However, when we do detailed research, we see that Bjorka actively uses a Telegram page with close to 250 followers:
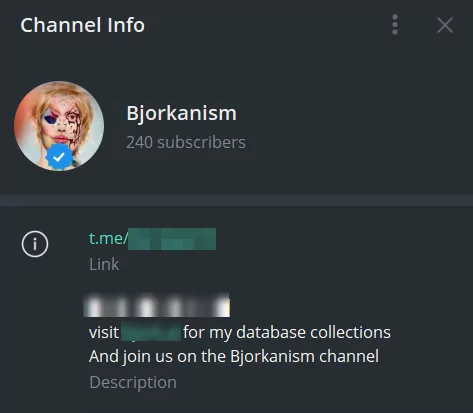 Figure 10. Bjorka’s Telegram channel which is actively used by the threat actor itself
Figure 10. Bjorka’s Telegram channel which is actively used by the threat actor itself
Another thing we noticed about Bjorka is that most of its profiles (Breach Forums and Twitter accounts) state that Bjorka is living in Poland and its gender is Female.
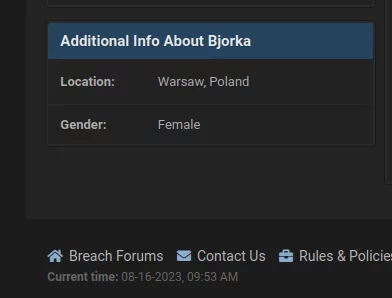 Figure 11. Additional information section of Bjorka’s Breach Forums profile
Figure 11. Additional information section of Bjorka’s Breach Forums profile
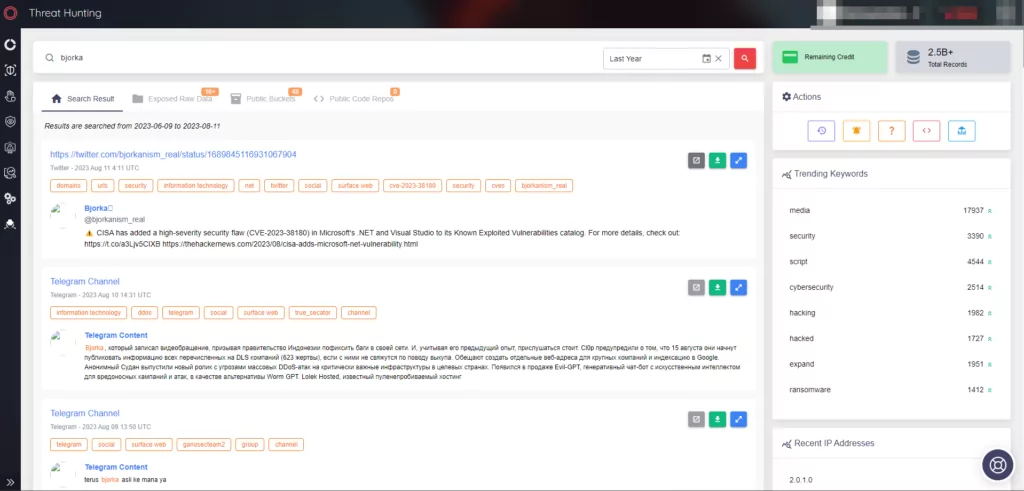 Figure 12. Threat Hunting page under the CTI Module of SOCRadar (Source: SOCRadar)
Figure 12. Threat Hunting page under the CTI Module of SOCRadar (Source: SOCRadar)
What are the Latest Activities of Bjorka?
The leak of Indonesian hospital database:
In a post on August 16, Bjorka claimed to have leaked Indonesian Hospital data. Bjorka also said that the data also included data from House of Representatives (DPR-RI) members.
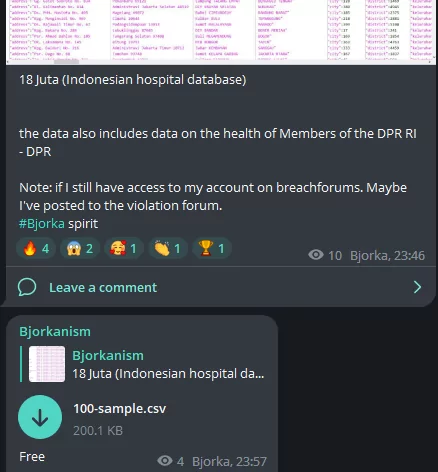 Figure 13. Bjorka’s Telegram post of leaked Indonesian hospital database
Figure 13. Bjorka’s Telegram post of leaked Indonesian hospital database
The data contains the name, gender, marriage status, place of birth, date of birth, address, job, city and district information of patients.
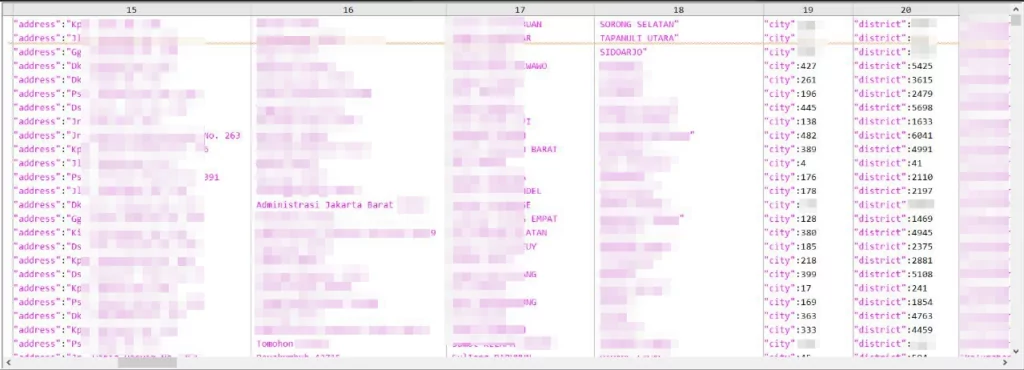 Figure 14. Leaked information sample of Indonesian hospital database
Figure 14. Leaked information sample of Indonesian hospital database
Database leak of Bank Syariah Indonesia:
One of the noteworthy recent posts is the Bank Syariah IndonesiaDatabase leak, on August 13, which shows that Bjorka is also targeting the Finance sector in Indonesia:
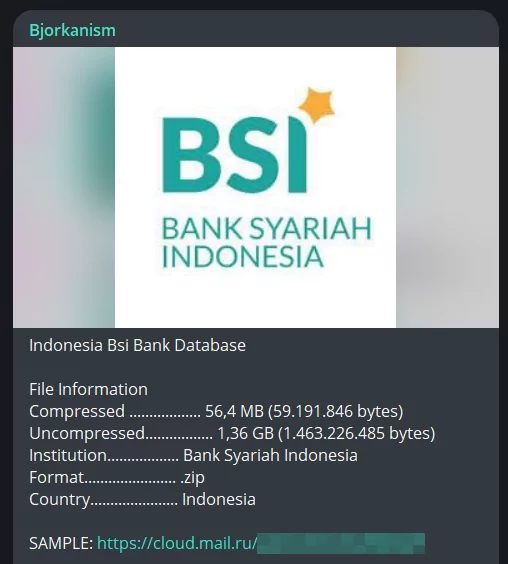 Figure 15. Bank Syariah Indonesia Database leak post made by Bjorka
Figure 15. Bank Syariah Indonesia Database leak post made by Bjorka
Money giveaway:
Recently, Bjorka announced on her Twitter account that it will be doing a 5,000 Dollar giveaway and stated that the conditions for participation are to Like, Share, and Commenting under the tweet.
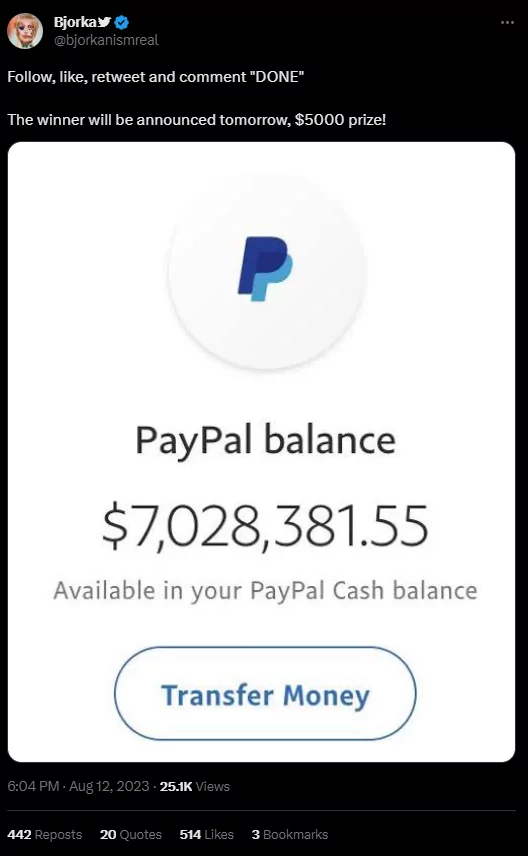 Figure 16. Money Giveaway event run by Bjorka
Figure 16. Money Giveaway event run by Bjorka
We understand from this post that Bjorka wants to show her power by showing the large amount in her account, and whether this giveaway event is real or not, she aims to spread to a wider audience by increasing its interaction.
Whether this post is Bjorka’s own or not is a matter of debate. It is possible that other actors are using Bjorka’s reputation to carry out a scam; who knows?
Selling a stolen credit card with a high limit:
On August 11, 2023, Bjorka announced on both Telegram and Twitter that it had put up for sale a credit card with a limit of $85,000,000 at Scotia Bank.
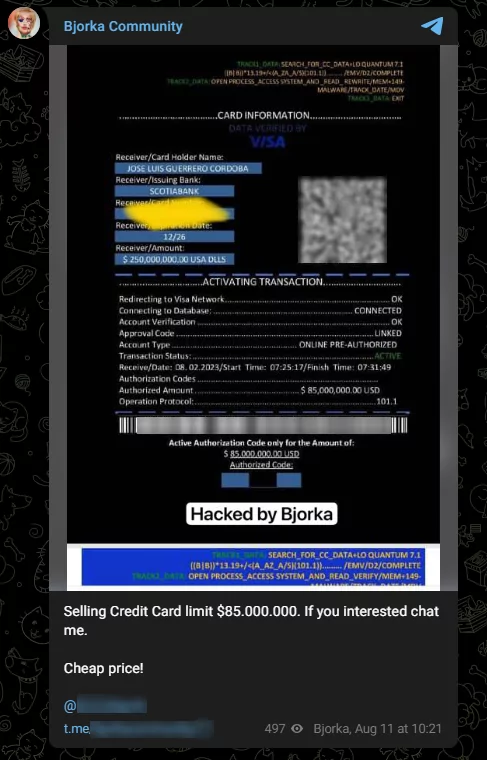 Figure 17. Bjorka’s post about selling a stolen credit card with a high limit
Figure 17. Bjorka’s post about selling a stolen credit card with a high limit
The SIAK Database of Dukcapil Ministry of Home Affairs of Indonesia:
One post on the Bjorkanesia blog that caught our attention was the 131 GB data leak of Ministry of Home Affairs of Indonesia published on July 17:
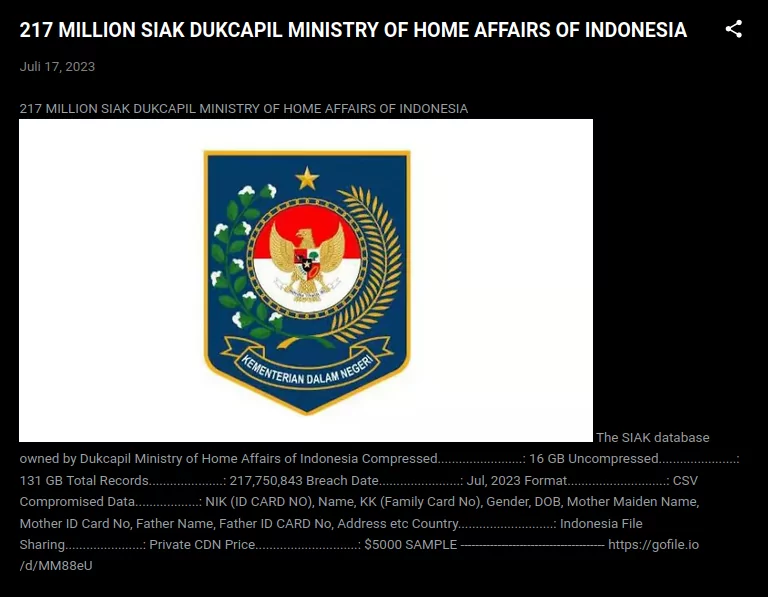 Figure 18. Bjorka’s bjorkanesia post about database leak of Ministry of Home Affairs
Figure 18. Bjorka’s bjorkanesia post about database leak of Ministry of Home Affairs
To learn about dark web news about Indonesia and/or Bjorka, you can use the Dark Web News page under the SOCRadar’s CTI module:
 Figure 19. SOCRadar’s Dark Web News section under the CTI module (Source: SOCRadar)
Figure 19. SOCRadar’s Dark Web News section under the CTI module (Source: SOCRadar)
Harbinger of More to Come
In a Telegram post on August 13, Bjorka stated that there will be a lot of Indonesian Private leaks on August 17:
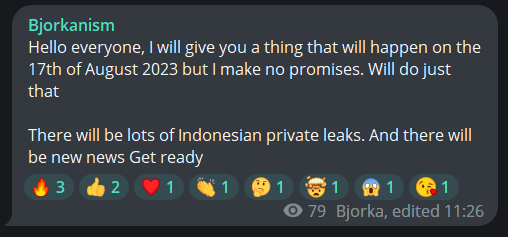 Figure 20. Bjorka’s Telegram post about it will make lots of leaks on August 17
Figure 20. Bjorka’s Telegram post about it will make lots of leaks on August 17
We will see whether Bjorka did this post to get interaction or to announce that will actually share something.
The Unraveling: Connection to Anonymous
On YouTube, Bjorka shared a mysterious monologue. The actor started with the phrase “But we won’t sell the data” and then touched upon various topics, including data privacy and socio-political matters. This move towards commentary reveals a more thoughtful side of Bjorka, inspiring viewers to take an active role in these difficult times rather than being passive observers.
 Figure 21. Bjorka’s post about its latest monologue
Figure 21. Bjorka’s post about its latest monologueInterestingly, the video concludes, echoing Anonymous’s motto: “We are Anonymous. We are Legion. We do not forgive. We do not forget. Expect us.”
Bjorka’s Relation with Other Threat Actors
The cyber threat landscape is often interconnected, with various actors collaborating, competing, or operating in parallel. Bjorka’s relation with other threat actors is an area of interest that may shed light on their capabilities, objectives, and broader context within the cyber underworld. Here’s what we know and what remains speculative:
- Potential Collaborations: While concrete evidence is scarce, there are hints that Bjorka may have connections or collaborations with other threat actors. Such alliances could enhance their capabilities, share resources, and coordinate attacks for maximum impact.
- Shared Techniques and Tools: Bjorka’s use of certain hacking techniques and tools may align with those used by other known threat actors. This overlap could suggest shared knowledge, collaboration, or simply a convergence of methods within the cybercriminal community.
- Competing Interests: Conversely, Bjorka may also have competing interests with other threat actors. The complex dynamics of the cyber underworld often lead to rivalries and conflicts, and understanding these relationships can provide insights into Bjorka’s positioning and strategy.
- Influence and Inspiration: Bjorka’s actions may be influenced or inspired by other prominent threat actors. Studying these potential influences can help in understanding Bjorka’s evolution as a threat actor and their alignment with broader trends in cyber warfare.
- Unconfirmed Connections: It’s important to note that much of the information regarding Bjorka’s relations with other threat actors remains speculative and unconfirmed. The secretive nature of cyber criminal activities often makes it challenging to definitively map connections and collaborations.
Bjorka’s potential relations with other threat actors add another layer of complexity to their profile. Whether through collaboration, competition, or influence, these connections provide a broader context for understanding Bjorka’s actions and positioning within the cyber threat landscape. However, the elusive nature of these connections also serves as a reminder of the challenges in fully unraveling the web of relationships that define the cyber underworld.
Conclusion
Bjorka’s emergence as a prominent threat actor in the cyber landscape represents a complex and multifaceted challenge. With a focus on targeted attacks against the Indonesian government, private sectors, and critical infrastructure, Bjorka has demonstrated a sophisticated blend of technical prowess, strategic thinking, and adaptability.
The profile of Bjorka is a testament to the evolving nature of cyber threats, where motivations, methods, and targets are continually shifting. Whether driven by political agendas, financial gains, or ideological beliefs, Bjorka’s actions have had far-reaching impacts, both within Indonesia and potentially beyond.
While some connections with other threat actors remain speculative, the possibility of collaboration or influence adds to the intrigue and complexity of understanding Bjorka’s full scope and intentions.
In the face of such a dynamic and unpredictable threat, continuous vigilance, comprehensive analysis, and adaptable defense strategies are paramount. Bjorka’s activities serve as a stark reminder that cyberspace and cybercrime are ever-changing, and understanding the profiles of individual threat actors is crucial in staying one step ahead.
Security Recommendations Against Bjorka
In light of Bjorka’s sophisticated and targeted attacks, organizations, governments, and individuals must take proactive measures to defend against this threat actor. Here are some security recommendations to consider:
- Regular Security Assessments: Conducting regular security assessments to identify vulnerabilities and weaknesses in systems can help in early detection and mitigation of potential threats from actors like Bjorka.
- Implement Multi-Factor Authentication: Utilizing multi-factor authentication adds an additional layer of security, making it more challenging for threat actors to gain unauthorized access to sensitive information. Coupled with the practice of using strong passwords, ensuring a unique password for every platform, and employing password management tools, users can significantly enhance their defense against potential breaches.
- Educate and Train Staff: Since social engineering may be one of Bjorka’s tactics, educating and training staff on recognizing and responding to phishing attempts and other manipulative techniques is essential.
- Monitor and Analyze Network Activity: Continuous monitoring and analysis of network activity can help in detecting unusual patterns or behaviors that may indicate an intrusion or attack by Bjorka.
- Collaborate with Cybersecurity Experts: Collaborating with cybersecurity experts and agencies can provide specialized insights and support in defending against complex threats like Bjorka.
- Utilize Threat Intelligence and Cyber Threat Intelligence (CTI): Leveraging threat intelligence and Cyber Threat Intelligence (CTI) to stay informed about Bjorka’s latest tactics, techniques, and procedures (TTPs) can enable a more targeted and effective defense strategy. CTI provides actionable insights based on the analysis of global cyber threats, allowing for a more nuanced understanding of Bjorka’s methods and potential countermeasures.
- Implement Data Encryption: Encrypting sensitive data adds an extra layer of protection, ensuring that even if data is breached, it remains inaccessible to unauthorized parties.
- Develop an Incident Response Plan: Having a well-defined incident response plan ensures that in the event of an attack by Bjorka or similiar threat actors, the organization can respond quickly and effectively to minimize damage and recover.
- Consider Legal and Ethical Implications: Understanding and complying with legal and ethical obligations related to data protection and privacy is vital, especially considering Bjorka’s focus on personal data.
- Stay Informed and Adaptable: The dynamic nature of Bjorka’s attacks requires continuous learning and adaptation. Staying informed about the latest developments and being ready to adjust security measures as needed is key to a robust defense.
Bjorka’s activities have underscored the importance of a comprehensive and multifaceted approach to cybersecurity. By understanding the profile of this threat actor and implementing targeted security measures, including the utilization of Cyber Threat Intelligence, we can build a resilient defense against Bjorka and similar threats in the future.
The post Dark Web Profile: Bjorka appeared first on SOCRadar® Cyber Intelligence Inc..
Article Link: Dark Web Profile: Bjorka
